Explore Any Narratives
Discover and contribute to detailed historical accounts and cultural stories. Share your knowledge and engage with enthusiasts worldwide.
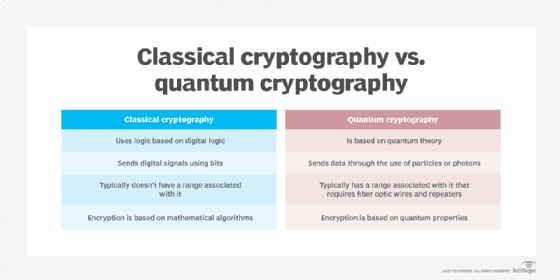
In an era where cybersecurity threats are becoming increasingly sophisticated, the demand for unbreakable encryption has never been greater. Traditional cryptographic methods, while effective, are vulnerable to advancements in computing power and clever hacking techniques. Enter quantum cryptography—a revolutionary approach to secure communication that leverages the principles of quantum mechanics to ensure unparalleled security. Unlike classical encryption, which relies on mathematical complexity, quantum cryptography is built on the inherent uncertainty and fundamental laws of physics, making it theoretically immune to hacking attempts.
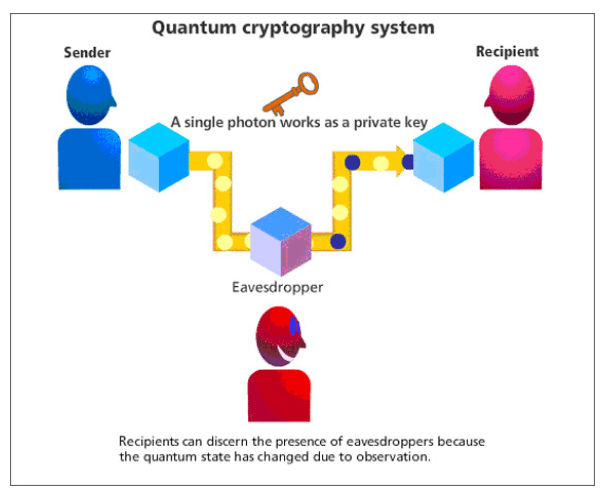
The foundation of quantum cryptography lies in quantum key distribution (QKD), a method that allows two parties to generate a shared secret key that can be used to encrypt and decrypt messages. What makes QKD unique is its reliance on the behavior of quantum particles, such as photons, which cannot be measured or copied without disturbing their state. This means any attempt to eavesdrop on the communication will inevitably leave traces, alerting the legitimate parties to the intrusion.
At the heart of quantum cryptography are two key principles of quantum mechanics: the Heisenberg Uncertainty Principle and quantum entanglement.
The Heisenberg Uncertainty Principle states that it is impossible to simultaneously know both the position and momentum of a quantum particle with absolute precision. In the context of quantum cryptography, this principle ensures that any attempt to measure a quantum system (such as a photon used in QKD) will inevitably alter its state. Suppose an eavesdropper tries to intercept the quantum key during transmission. In that case, their measurement will introduce detectable disturbances, revealing their presence and preserving the key's secrecy.
Quantum entanglement is a phenomenon where two or more particles become linked in such a way that the state of one particle immediately influences the state of the other, regardless of the distance separating them. This property allows for the creation of highly secure cryptographic systems. For example, if entangled photons are used in QKD, any attempt to intercept one photon will disrupt the entanglement, providing a clear indication of tampering.
QKD is the cornerstone of quantum cryptography and involves the exchange of cryptographic keys between two parties—traditionally referred to as Alice (the sender) and Bob (the receiver)—using quantum communication channels. Here's a simplified breakdown of the process:
Alice begins by generating a sequence of photons, each in a random quantum state (polarization or phase). She sends these photons to Bob over a quantum channel, such as an optical fiber or even through free space.
Upon receiving the photons, Bob measures each one using a randomly chosen basis (e.g., rectilinear or diagonal for polarization-based systems). Due to the probabilistic nature of quantum mechanics, Bob’s measurements will only be accurate if he chooses the same basis as Alice did when preparing the photon.
After the transmission, Alice and Bob publicly compare their choice of measurement bases (but not the actual results). They discard any instances where Bob measured the photon in the wrong basis, retaining only the cases where their bases matched. These remaining results form the raw key.
To ensure the key's integrity, Alice and Bob perform error checking by comparing a subset of their raw key. If discrepancies exceed a certain threshold, it indicates potential eavesdropping, and the key is discarded. If no significant errors are found, they apply privacy amplification techniques to distill a final, secure key.
Quantum cryptography offers several compelling advantages over traditional encryption methods:
Unlike classical encryption, which depends on computational hardness assumptions (e.g., factoring large primes), quantum cryptography provides security based on the laws of physics. This means it remains secure even against adversaries with unlimited computational power.
Any attempt to intercept quantum-encoded information will disturb the system, making it immediately detectable. This feature ensures that compromised communications can be identified and discarded before sensitive data is exposed.
With the advent of quantum computers, classical cryptographic algorithms like RSA and ECC are at risk of being broken. Quantum cryptography, particularly QKD, remains resistant to such threats, making it a future-proof solution.
While quantum cryptography holds immense promise, its practical implementation faces several hurdles. Currently, QKD is being used in limited scenarios, such as securing government communications and financial transactions. However, challenges like high implementation costs, limited transmission distances, and the need for specialized infrastructure hinder widespread adoption.
Despite these obstacles, research and development in quantum cryptography are advancing rapidly. Innovations in satellite-based QKD and integrated photonics are paving the way for more accessible and scalable solutions. As the technology matures, quantum cryptography could become a standard for securing critical communications in the near future.
Stay tuned for the next part of this article, where we will delve deeper into real-world implementations of quantum cryptography, its limitations, and the ongoing advancements in this groundbreaking field.
The theoretical promise of quantum cryptography has begun translating into practical applications, albeit in niche and high-security environments. Governments, financial institutions, and research organizations are leading the charge in deploying quantum-secure communication networks, recognizing the urgent need for protection against both current and future cyber threats.
National security agencies were among the first to recognize the potential of quantum cryptography. Countries like China, the United States, and Switzerland have implemented QKD-based secure communication networks to safeguard sensitive governmental and military data. In 2017, China’s Quantum Experiments at Space Scale (QUESS) satellite, also known as Micius, successfully demonstrated intercontinental QKD between Beijing and Vienna, marking a milestone in global quantum-secured communication.
Similarly, the U.S. government has invested in quantum-resistant encryption initiatives through collaborations involving the National Institute of Standards and Technology (NIST) and Defense Advanced Research Projects Agency (DARPA). These efforts aim to transition classified communications to quantum-safe protocols before large-scale quantum computers become a reality.
Banks and financial enterprises handle vast amounts of sensitive data daily, making them prime targets for cyberattacks. Forward-thinking institutions like JPMorgan Chase and the European Central Bank have begun experimenting with QKD to protect high-frequency trading systems, interbank communications, and customer transactions.
In 2020, the Tokyo Quantum Secure Communication Network, a collaboration between Toshiba and major Japanese financial firms, established a quantum-secured link between data centers, ensuring tamper-proof financial transactions. Such implementations underscore the growing confidence in quantum cryptography as a viable defense against economic espionage and fraud.
Despite its groundbreaking advantages, quantum cryptography is not without hurdles. Researchers and engineers must overcome several technical barriers before QKD can achieve mainstream adoption.
One of the biggest challenges in QKD is signal loss over long distances. Photons used in quantum communication degrade when traveling through optical fibers or free space, limiting the effective range of current systems. While terrestrial QKD networks rarely exceed 300 kilometers, researchers are exploring quantum repeaters and satellite relays to extend reach. China’s Micius satellite has achieved intercontinental key distribution, but ground-based infrastructure remains constrained by physical losses.
Quantum key distribution is also bottlenecked by the speed at which secure keys can be generated. Traditional QKD systems produce keys at rates of a few kilobits per second—sufficient for encrypting voice calls or small data packets but impractical for high-bandwidth applications like video streaming. Advances in superconducting detectors and high-speed modulators aim to improve key rates, but further innovation is needed to match classical encryption speeds.
The specialized hardware required for QKD—such as single-photon detectors, quantum light sources, and ultra-low-noise optical fibers—makes deployment expensive. For instance, commercial QKD systems can cost hundreds of thousands of dollars, putting them out of reach for most enterprises. Additionally, integrating quantum-secured links into existing telecommunication networks demands significant infrastructure upgrades, further complicating widespread adoption.
Quantum cryptography often overlaps with discussions about post-quantum cryptography (PQC), leading to some confusion. While both address quantum threats, their approaches differ fundamentally.
Quantum key distribution relies on the principles of quantum mechanics to secure communications inherently, whereas post-quantum cryptography involves developing new mathematical algorithms resistant to attacks from quantum computers. PQC solutions, currently being standardized by NIST, aim to replace vulnerable classical algorithms without requiring quantum hardware. However, QKD offers a unique advantage: information-theoretic security, meaning its safety doesn’t depend on unproven mathematical assumptions.
Recognizing the complementary strengths of both approaches, organizations are increasingly adopting hybrid systems combining QKD with post-quantum algorithms. This dual-layer encryption strategy ensures resilience even if one layer is compromised, providing a balanced transition path toward a quantum-safe future.
The push toward a quantum internet—a global network interconnected via quantum entanglement—has accelerated breakthroughs in quantum repeaters, memory storage, and entanglement swapping. These innovations address critical challenges in scaling quantum cryptography beyond point-to-point links.
Traditional signal amplifiers cannot be used in quantum communications without destroying the quantum states of photons. Quantum repeaters, still in experimental stages, aim to overcome this by leveraging entanglement swapping to extend the reach of QKD without measurement. Companies like Quantum Xchange in the U.S. and ID Quantique in Switzerland are pioneering modular repeater technologies to enable continental-scale quantum networks.
Storing quantum information is essential for synchronizing transmissions in large networks. Recent advances in atomic ensembles and rare-earth-doped crystals have demonstrated millisecond-long quantum memory retention—a critical step toward buffering entangled光子 for on-demand retrieval in complex networks.
The quantum cryptography market is witnessing a surge in private-sector involvement, with startups and tech giants alike racing to commercialize the technology.
Companies like Toshiba, IBM, and QuintessenceLabs are offering enterprise-grade QKD solutions tailored for specific industries. Meanwhile, open-source projects such as the OpenQKD initiative by the European Union are fostering collaboration between academia and industry to standardize protocols and drive down costs.
Cloud providers are exploring quantum-secure services, such as AWS’s hybrid post-quantum TLS and Azure’s Quantum Network, allowing businesses to test quantum-resistant encryption without major infrastructure investments. These platforms serve as bridges for organizations transitioning toward full quantum readiness.
Quantum cryptography is transitioning from lab experiments to real-world deployments, but obstacles remain. The next decade will likely see breakthroughs in scalable QKD, affordable quantum hardware, and international standards—key enablers for a quantum-secured global infrastructure. In the final part of this series, we will explore speculative future applications, ethical considerations, and the role of policy in shaping quantum security’s trajectory.
Stay tuned for the concluding installment, where we examine how quantum cryptography could redefine privacy, governance, and trust in the digital age.
As quantum cryptography moves from theoretical research to practical implementation, it raises profound questions about its impact on society, governance, and individual privacy. The technology’s potential to revolutionize secure communication is undeniable, but it also introduces new challenges that must be addressed to ensure responsible adoption.
Quantum cryptography promises unbreakable encryption, but it also poses ethical dilemmas. Governments and corporations could use quantum-secure networks to protect sensitive data, but the same technology might enable mass surveillance if misused. The balance between security and privacy will be a critical issue as quantum encryption becomes mainstream. Policymakers must establish clear regulations to prevent abuse while fostering innovation.
The advent of quantum computing and cryptography could shift the balance of power in cyber warfare. Nations with advanced quantum capabilities may gain an advantage in intelligence gathering and secure communications, potentially destabilizing international relations. The risk of a "quantum arms race" is real, with countries competing to develop quantum-resistant encryption and decryption tools. International cooperation will be essential to prevent an escalation of cyber conflicts.
Quantum cryptography is currently expensive and complex, limiting its availability to wealthy nations and large corporations. If left unchecked, this could exacerbate the digital divide, leaving smaller businesses and developing nations vulnerable to cyberattacks. Efforts to democratize quantum-secure technologies—through open-source projects, subsidies, or international partnerships—will be crucial to ensuring equitable access.
The intersection of quantum computing and artificial intelligence (AI) presents both opportunities and risks. Quantum algorithms could enhance AI’s ability to analyze encrypted data, potentially breaking classical encryption methods. Conversely, AI could be used to optimize quantum cryptographic protocols, making them more efficient and secure. The synergy between these two fields will shape the future of cybersecurity.
AI-driven cyberattacks are already a growing threat, and quantum computing could amplify their effectiveness. Machine learning models trained on quantum algorithms might identify vulnerabilities in classical encryption faster than human hackers. Defending against such threats will require AI-powered quantum defenses, creating a continuous arms race between attackers and defenders.
On the defensive side, quantum machine learning could revolutionize threat detection. Quantum-enhanced AI models could analyze vast datasets in real time, identifying anomalies and potential breaches with unprecedented accuracy. This could lead to proactive cybersecurity measures, where threats are neutralized before they cause harm.
Governments and international organizations must play a proactive role in shaping the future of quantum cryptography. Without proper oversight, the technology could be weaponized or monopolized, leading to unintended consequences.
Establishing global standards for quantum encryption is essential to ensure interoperability and security. Organizations like NIST and the International Telecommunication Union (ITU) are already working on post-quantum cryptographic standards, but more collaboration is needed to address emerging quantum threats. Certification programs for quantum-secure products will also be necessary to build trust among users.
As quantum technology advances, ethical guidelines must be developed to govern its use. Researchers and policymakers should collaborate to address concerns such as data sovereignty, surveillance, and the militarization of quantum encryption. Transparency and public discourse will be key to ensuring that quantum cryptography benefits society as a whole.
Beyond cybersecurity, quantum cryptography could enable groundbreaking applications in various fields, from healthcare to space exploration.
Healthcare systems handle vast amounts of sensitive patient data, making them prime targets for cyberattacks. Quantum-secure encryption could protect medical records, ensuring patient confidentiality while enabling secure sharing of research data. This could accelerate medical breakthroughs while safeguarding privacy.
As humanity expands into space, secure communication between Earth and distant colonies or spacecraft will be critical. Quantum cryptography could enable unhackable communication links across vast distances, ensuring the integrity of mission-critical data. NASA and other space agencies are already exploring quantum communication for future Mars missions.
Election security is a growing concern worldwide. Quantum-secure voting systems could prevent tampering and ensure the integrity of democratic processes. By leveraging quantum encryption, governments could create verifiable and tamper-proof digital voting mechanisms, restoring public trust in elections.
Quantum cryptography is poised to redefine the future of secure communication, offering unparalleled protection against cyber threats. However, its widespread adoption will require overcoming technical, ethical, and regulatory challenges. As we stand on the brink of a quantum revolution, collaboration between scientists, policymakers, and industry leaders will be essential to harness the technology’s potential while mitigating its risks.
The next decade will be pivotal in determining how quantum cryptography shapes our digital world. By addressing accessibility, ethical concerns, and global cooperation, we can ensure that this revolutionary technology serves as a force for good, safeguarding privacy and security in an increasingly connected world.
As quantum cryptography evolves, one thing is certain: the future of cybersecurity will be quantum, and the time to prepare is now.


Your personal space to curate, organize, and share knowledge with the world.
Discover and contribute to detailed historical accounts and cultural stories. Share your knowledge and engage with enthusiasts worldwide.
Connect with others who share your interests. Create and participate in themed boards about any topic you have in mind.
Contribute your knowledge and insights. Create engaging content and participate in meaningful discussions across multiple languages.
Already have an account? Sign in here
Understanding hash functions is crucial for data security. Learn about their mechanics, types, applications, and securit...
View Board
Explore hash functions' core uses, security & future challenges in blockchain/data. Master algorithm selection & digital...
View Board
Discover how the SHA-256 hashing algorithm secures digital data, powers blockchain, and ensures integrity. Learn its key...
View Board
A 1976 handshake at Stanford unlocked the modern internet—how Diffie-Hellman’s public-key cryptography revolutionized se...
View Board
Unlock the intricacies of the Advanced Encryption Standard (AES) in our comprehensive guide. Explore its key mechanisms,...
View Board
Encryption in 2025: Trends, Standards, and Future-Proofing Encryption is the cornerstone of modern data security, trans...
View Board
Discover the mysterious history of the Death Machine cipher, the WWII Enigma machine. Explore its origins, wartime role,...
View Board
Descubra como o algoritmo SHA-256 garante segurança digital, desde blockchain até proteção de senhas. Entenda seu funcio...
View Board
Explore the secretive world of Cold War cryptography, where the U.S. and Soviet Union waged a cryptographic arms race wi...
View Board
The open AI accelerator exchange in 2025 breaks NVIDIA's CUDA dominance, enabling seamless model deployment across diver...
View Board
Experience the thrill of live music's post-pandemic resurgence with our dive into the industry's booming return. Discove...
View Board
Descubra como a criptografia de chave assimétrica protege dados sem compartilhar segredos, revolucionando a segurança di...
View Board
Discover the top content creation and web design trends for 2025, from AI-driven personalization to immersive AR/VR expe...
View Board
Robert J Skinner, a retired US Air Force lieutenant general, has had a distinguished career in cybersecurity and IT mode...
View Board
Explore the pioneering legacy of Charles Babbage, the visionary often regarded as the "father of the computer." From his...
View Board
Descubra a cifra monoalfabética, um clássico da criptografia que ensina fundamentos essenciais de segurança da informaçã...
View Board
Explore the revolutionary journey of Sir Tim Berners-Lee, the pioneering architect behind the World Wide Web. Discover h...
View Board
Descubra como a Troca de Chaves Diffie-Hellman protege HTTPS, VPNs e mensagens. Domine este pilar essencial da segurança...
View Board
Discover how Moore's Law has driven computing evolution for decades, its challenges, and future innovations like quantum...
View Board
Discover how Tim Berners-Lee invented the World Wide Web in 1989, revolutionizing global communication. Explore his life...
View Board
Comments