Explore Any Narratives
Discover and contribute to detailed historical accounts and cultural stories. Share your knowledge and engage with enthusiasts worldwide.
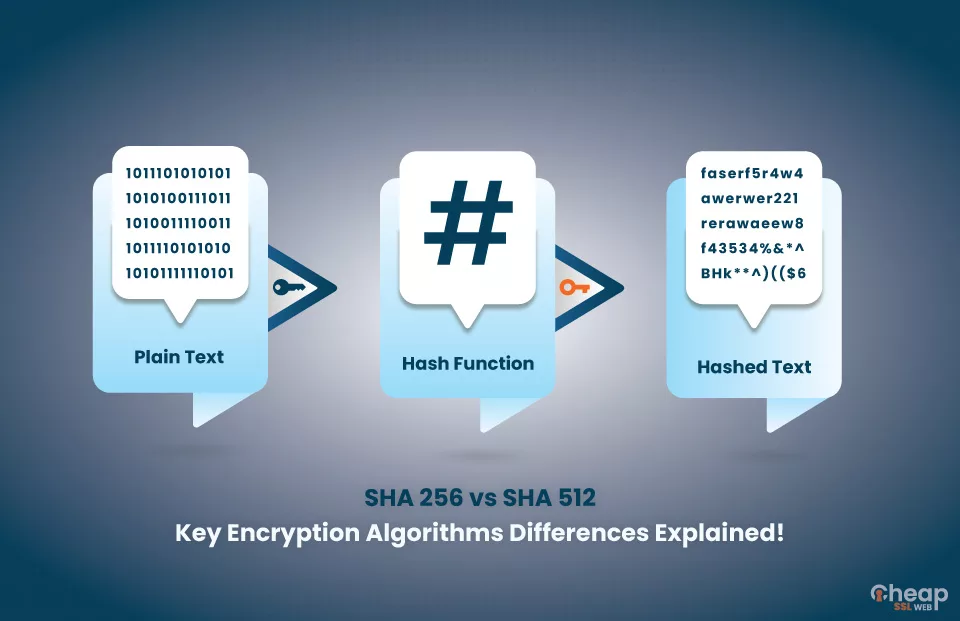
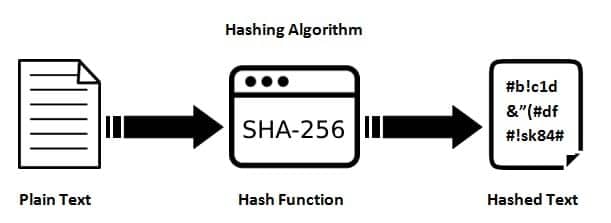
The SHA-256 hashing algorithm is a fundamental pillar of modern cybersecurity and digital trust. As a member of the SHA-2 family, this cryptographic function transforms any input into a fixed, unique 256-bit digest. Securing everything from digital signatures to blockchain transactions, SHA-256 is the unseen guardian of data integrity across the internet.
SHA-256 stands for Secure Hash Algorithm 256-bit. It is a one-way cryptographic hash function published in 2001 by the National Institute of Standards and Technology (NIST). Its primary purpose is to create a digital fingerprint of data for verification and tamper detection. This technology powers critical systems like blockchain, secure communications, and software distribution.
SHA-256 is a cornerstone of security protocols, including TLS/SSL, PGP, and is famously integral to Bitcoin's proof-of-work consensus mechanism.
Unlike encryption, hashing is not designed to be reversible. The process takes an input (or 'message') and returns a fixed-size string of bytes. The output, called a hash digest, appears random. Even a tiny change in the input creates a completely different hash. This property is essential for validating data authenticity without exposing the original content.
The SHA-256 algorithm is engineered with specific mathematical properties that ensure its reliability and security. These foundational characteristics make it suitable for high-stakes applications like financial transactions and secure logging.
The algorithm is deterministic. This means the same input will always produce the identical 256-bit (32-byte) output. Regardless of whether you hash a single word or a massive file, the resulting digest is always the same fixed length: 64 hexadecimal characters.
SHA-256 is designed to be computationally irreversible. It is infeasible to reverse-engineer the original input from its hash output, a property known as preimage resistance. It also boasts strong collision resistance, making it extremely unlikely for two different inputs to produce the same hash output.
A defining feature of SHA-256 is the avalanche effect. If you modify just one bit of the input data, approximately 50% of the output bits will change. This ensures that the new hash is completely uncorrelated to the original hash, making it impossible to infer relationships between inputs and outputs.
For example, the Bitcoin network leverages this effect. A minor change in a block's transaction data completely alters its cryptographic hash, securing the entire chain from tampering.
The internal mechanics of the SHA-256 hashing algorithm involve a sophisticated yet elegant process. It processes data in a series of structured rounds to generate the final secure digest. Let's break down the core steps.
The algorithm first prepares the input message. It encodes the message (typically in UTF-8) and then pads it so its length in bits becomes a multiple of 512. Padding always adds a single '1' bit, followed by a series of '0' bits. Finally, it appends a 64-bit integer representing the original message length.
The padded message is then divided into N number of 512-bit blocks. Each of these 512-bit blocks will be processed sequentially by the algorithm's compression function. This modular design allows SHA-256 to handle data of virtually any size.
The algorithm begins with eight initial 32-bit hash values. These initial hash values are constants derived from the first 32 bits of the fractional parts of the square roots of the first eight prime numbers (2, 3, 5, 7, 11, 13, 17, 19). These values are often denoted as H0(0) through H7(0).
This is the heart of the SHA-256 algorithm. For each 512-bit block, the data is expanded and mixed in 64 rounds of computation. Each round uses:
The compression function updates the eight working hash variables with the result of each round. After all rounds for a block are complete, the result is added to the intermediate hash value, and the process repeats for the next block.
SHA-256 is part of the broader SHA-2 family of hash functions. Understanding its place in this family clarifies its strengths relative to predecessors and successors.
SHA-256 was developed as the successor to the vulnerable SHA-1 algorithm. While SHA-1 produces a 160-bit hash, its cryptographic weaknesses were exposed, making it susceptible to collision attacks. SHA-256 provides a significantly longer 256-bit digest and a more robust internal structure, addressing the brute-force vulnerabilities of its predecessor.
The SHA-2 family includes several variants: SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224, and SHA-512/256. The key differences lie in:
SHA-256 forms the basis for standards like FIPS 180-4 and is currently the most widely adopted SHA-2 variant due to its balance of security and performance.
Delving deeper into the SHA-256 algorithm reveals a foundation built on elegant mathematics. The internal state management and constant values are not arbitrary. They are carefully chosen to ensure a uniform, unpredictable, and secure distribution of the final hash output.
The eight initial hash values provide a standardized starting point for the computation. These 32-bit numbers are the first 32 bits of the fractional parts of the square roots of the first eight prime numbers. This method of generation ensures they are free from hidden backdoors and are statistically random.
Similarly, the 64 round constants used in the compression function are derived from the fractional parts of the cube roots of the first 64 prime numbers. These constants introduce asymmetry into each round of processing. This helps break any patterns in the input data, further strengthening the algorithm's collision resistance.
The core of SHA-256's security lies in its compression function. It works on a 512-bit message block and the current 256-bit intermediate hash value. The function compresses these 768 bits down into a new 256-bit value. This is achieved through 64 rounds of bitwise operations.
The intricate sequence of these operations ensures that every bit of the input influences every bit of the final output. This design enforces the critical avalanche effect.
The theoretical strength of SHA-256 is validated by its ubiquitous adoption in critical systems. Its balance of performance and security has made it the de facto standard for numerous applications that underpin the digital world.
SHA-256 is famously the backbone of Bitcoin's proof-of-work consensus mechanism. Miners compete to find a hash for a new block that meets a certain target (starting with a specific number of zeros). This process secures the network and validates transactions.
The Bitcoin network's hashrate, estimated at ~2^65 hashes per second in 2025, illustrates the immense computational scale dedicated to SHA-256 processing.
Every Bitcoin transaction is hashed, and those hashes are themselves hashed in a Merkle tree structure. The resulting Merkle root is stored in the block header. This allows for efficient and secure verification of any transaction within a massive block.
Digital signature schemes like RSA and DSA rely heavily on cryptographic hash functions. To sign a document, the software first generates a SHA-256 hash of the document's contents. The signature algorithm then encrypts this hash with the signer's private key.
Verification involves decrypting the signature with the public key to get the hash and comparing it to a freshly computed hash of the document. This proves the document's integrity and the signer's authenticity. SSL/TLS certificates securing HTTPS connections use this same principle.
Software distributors often provide a SHA-256 checksum alongside file downloads. After downloading, a user can generate a hash of the file. If it matches the published checksum, the file is intact and unaltered. This prevents corruption and malicious tampering.
For password storage, secure systems never store plaintext passwords. Instead, they store a salted SHA-256 hash of the password. When a user logs in, the system hashes the entered password with the same salt and compares the hashes. A match grants access without ever storing the actual password.
As of 2025, SHA-256 remains cryptographically secure against practical attacks. No feasible method exists to break its preimage or collision resistance within a realistic timeframe, given current technology. Its design has withstood nearly 25 years of intense public scrutiny.
The primary security metric for a hash function is its collision resistance. For SHA-256, finding two different inputs that produce the same output requires, on average, 2^128 operations due to the birthday paradox. This is an astronomically large number.
No collisions have ever been found for SHA-256. This stands in stark contrast to SHA-1, where practical collision attacks were demonstrated. The computational power needed to brute-force a SHA-256 hash is far beyond the capabilities of any existing or foreseeable classical computer system.
The total number of possible SHA-256 outputs is 2^256, approximately 1.16 x 10^77. This number vastly exceeds the estimated number of atoms in the observable universe (~10^80), putting the probability of an accidental collision effectively at zero.
The rise of quantum computing introduces new theoretical considerations. Grover's quantum algorithm can speed up the search for a preimage (reversing a hash). For SHA-256, Grover's algorithm could theoretically reduce the effective security from 2^256 to 2^128 operations.
While 2^128 is still an immense security margin, this potential reduction is driving cryptographic research into post-quantum algorithms.
It is crucial to note that practical, large-scale quantum computers capable of running Grover's algorithm on this scale do not exist today. However, the long-term viability of cryptographic systems demands proactive planning. This is a key reason NIST is standardizing post-quantum cryptography.
In response to potential long-term risks, NIST selected Keccak as the winner of the SHA-3 competition in 2012. SHA-3 uses a completely different internal structure (sponge construction) than the SHA-2 family. NIST recommends SHA-3 for future applications, especially those requiring long-term security.
However, SHA-256 is not deprecated. The transition is cautious due to SHA-256's immense ecosystem, proven track record, and hardware acceleration support. Many experts believe it will remain secure for years, if not decades, to come. The choice often depends on the specific risk profile and lifetime of the system being secured.
The widespread adoption of SHA-256 is not due to security alone. Its design allows for efficient implementation in both software and hardware, making it practical for high-speed applications from database indexing to blockchain mining.
Modern processors include dedicated instructions to accelerate SHA-256 computations. For example, Intel's SHA Extensions (part of the Intel SHA-NI instruction set) provide a significant performance boost. These instructions perform the core compression function steps directly in hardware, reducing the number of CPU cycles required.
This hardware support is a major factor in its continued dominance. It enables efficient, low-power hashing on everything from servers to mobile devices. This performance efficiency is critical for applications like TLS handshakes, where every millisecond counts.
In software, optimized SHA-256 libraries use techniques like loop unrolling and efficient scheduling of the message words to maximize throughput. Performance is typically measured in megabytes or gigabytes per second on a given processor.
These characteristics make SHA-256 a versatile tool suitable for a vast array of computing environments.
The security properties of the SHA-256 algorithm are best understood by examining its resistance to various attack vectors. Its robustness against mathematical and computational attacks is why it remains a trusted standard.
A preimage attack seeks to find an input that produces a specific hash output. Due to the deterministic yet unpredictable nature of the algorithm, the only known method is a brute-force search. SHA-256's 2^256 possible outputs make this completely infeasible. Even with the most powerful supercomputers, such an attack would require timeframes exceeding the age of the universe.
Finding two distinct inputs that produce the same hash is significantly harder for SHA-256 than for its predecessor, SHA-1. The birthday paradox suggests a collision attack would require about 2^128 operations. No successful collision attacks on SHA-256 have been demonstrated, and the computational power required remains firmly in the realm of theoretical impossibility with current technology.
Understanding where SHA-256 fits within the cryptographic landscape helps in appreciating its strengths and identifying appropriate use cases.
The SHA-256 algorithm was designed to overcome the vulnerabilities found in older algorithms like MD5 and SHA-1. Both MD5 (128-bit) and SHA-1 (160-bit) have been successfully attacked, with practical collisions demonstrated. SHA-256's longer digest size and more complex compression function provide a vastly superior security margin.
SHA-3 (Keccak) represents a different architectural approach using a sponge construction. While SHA-3 offers an alternative with different security properties, SHA-256 is not obsolete. The widespread adoption, hardware acceleration, and extensive real-world testing of SHA-256 ensure its continued relevance for the foreseeable future.
The cryptographic community continuously evaluates hash functions against emerging threats and technological advancements.
The potential advent of large-scale quantum computers presents a theoretical challenge to current cryptographic systems. Grover's algorithm could potentially square root the search space for preimage attacks on hash functions. However, even with this theoretical advantage, SHA-256 would retain 128 bits of security against quantum attacks, which most experts consider sufficient for many applications.
NIST's post-quantum cryptography standardization effort focuses primarily on asymmetric encryption and digital signatures, while noting that SHA-256 and SHA-3 are expected to remain secure with increased output lengths.
Cryptographers continually analyze SHA-256 for potential weaknesses. To date, no significant vulnerabilities have been found that would compromise its use in practice. The algorithm's transparent design and extensive peer review contribute to its strong security assurances.
Proper implementation is crucial for maintaining the security guarantees of the SHA-256 hashing algorithm.
When using SHA-256 for password hashing, always incorporate a unique salt for each password. This practice prevents rainbow table attacks and ensures that identical passwords result in different hash values.
For applications requiring key derivation from passwords, use iterated hashing (such as PBKDF2 with SHA-256) to intentionally slow down the computation. This increases the cost of brute-force attacks.
The SHA-256 algorithm represents a remarkable achievement in cryptographic engineering. Its elegant mathematical foundation, combined with practical efficiency and robust security properties, has made it an indispensable tool for modern computing.
From securing financial transactions on blockchain networks to verifying software downloads and authenticating digital communications, SHA-256 provides the bedrock of trust that enables our digital world to function. While new algorithms like SHA-3 offer alternative approaches, SHA-256's combination of security, performance, and widespread adoption ensures its continued importance for years to come.
As technology evolves and new threats emerge, the cryptographic community will continue to monitor and strengthen our tools. However, the fundamental principles embodied in SHA-256 – careful design, transparent analysis, and conservative security margins – will remain essential for developing the trustworthy systems of tomorrow.
Your personal space to curate, organize, and share knowledge with the world.
Discover and contribute to detailed historical accounts and cultural stories. Share your knowledge and engage with enthusiasts worldwide.
Connect with others who share your interests. Create and participate in themed boards about any topic you have in mind.
Contribute your knowledge and insights. Create engaging content and participate in meaningful discussions across multiple languages.
Already have an account? Sign in here

Learn about AES (Advanced Encryption Standard), the global standard for data encryption. Discover how AES works, key len...
View Board
Explore Filecoin, the blockchain-based decentralized storage network. Learn how it leverages IPFS, FIL tokens, and crypt...
View Board
In 2026, AI agents like Aria design, code, and test software autonomously, reshaping development from manual craft to st...
View Board
Discover how new privacy laws in 2025 impact age-gating, data security, and compliance. Stay ahead with expert insights ...
View Board
Explore the career of Robert J. Skinner, a retired USAF Lieutenant General and cybersecurity leader. Discover his impact...
View Board
Μάθετε για τον Πολ Μίλερ, τον Ελβετό χημικό που ανακάλυψε το DDT και έλαβε Νόμπελ. Η ιστορία του, η ανακάλυψη και η συμβ...
View Board
The open AI accelerator exchange in 2025 breaks NVIDIA's CUDA dominance, enabling seamless model deployment across diver...
View Board
Explore the vital role film critics play in shaping audience perceptions and influencing the film industry. Discover the...
View Board
SethBling: The Redstone King Who Rewrote Minecraft The blocky world of Minecraft is a universe of infinite possibility, ...
View Board
Autonomous AI agents quietly reshape work in 2026, slashing claim processing times by 38% overnight, shifting roles from...
View Board
Depthfirst's $40M Series A fuels AI-native defense against autonomous AI threats, reshaping enterprise security with con...
View Board
Explore the devastating global impact of film piracy. Understand the economic losses, geographical hotspots, and latest ...
View Board
Microsoft's Copilot+ PC debuts a new computing era with dedicated NPUs delivering 40+ TOPS, enabling instant, private AI...
View Board
Discover Charles Babbage, the visionary behind the Difference Engine & Analytical Engine! Explore his life, inventions, ...
View Board
Quantinuum files for $20B IPO, betting trapped-ion quantum tech can outpace rivals despite minimal revenue.
View Board
Next-gen dark matter detectors like LZ and TESSERACT push sensitivity limits, probing WIMPs with quantum tech and massiv...
View Board
The Architects of 2026: The Human Faces Behind Five Tech Revolutions On the morning of February 3, 2026, in a sprawling...
View Board
Discover Michael Faraday, the 'father of electromagnetism'! Learn about his groundbreaking discoveries in electricity, e...
View Board
AI stock picks for 2026 focus on companies building infrastructure, monetizing AI at scale, and supplying critical tools...
View Board
Uniswap’s code‑driven AMM turned a trillion‑dollar market into a permissionless engine, burning UNI as fees surge across...
View Board
Comments