Explore Any Narratives
Discover and contribute to detailed historical accounts and cultural stories. Share your knowledge and engage with enthusiasts worldwide.
The world of cryptography and data security is as ever-evolving as it is crucial. Among the key technologies used in these fields is the hash function. This article delves into the core concepts, mechanics, and applications of hash functions, offering a comprehensive overview for individuals seeking to understand this foundational element of modern cryptography.
A hash function is a mathematical function that takes an input (often referred to as the "message" or "data") and produces a fixed-length output. This output is typically a string of characters, known as the hash value or digest. Regardless of the size of the input, a hash function will always produce an output of the same size, making it an efficient method for verifying data integrity and security.
There are several critical characteristics that make a hash function suitable for its intended purposes. To function effectively, a hash function must:
Several types of hash functions are in widespread use today. Each type serves specific purposes and has unique features.
MD5 was one of the first widely accepted hash functions, developed by Ronald L. Rivest. It generates a 128-bit hash value, typically represented as a 32-character hexadecimal number. Despite its popularity, MD5 is no longer considered secure due to the possibility of collision attacks.
The Secure Hash Algorithms (SHA) family of hash functions were developed by the National Institute of Standards and Technology (NIST) and are designed to be more secure than MD5. SHA-256, for instance, generates a 256-bit hash, while SHA-3 (Keccak) is designed to offer improved security features.
Hash functions play a critical role in various aspects of data security and integrity. Here are some of the key applications:
One of the most common uses of hash functions is to ensure the integrity of files and data. When a file is stored, its hash value is calculated and stored alongside the file. When the file is accessed again, its hash value is recalculated and compared with the stored hash value. If any changes have occurred, the hashes will not match, indicating that the data has been tampered with.
Passwords are particularly sensitive data. Rather than storing passwords in plaintext, many systems use hash functions to store the hash of the password instead. When a user logs in, their input is hashed and compared with the stored hash. This not only enhances security but also protects against unauthorized access even if the password file is stolen.
Digital signatures use hash functions to ensure the authenticity and integrity of electronic documents. They are also crucial in the context of blockchain, where hash functions are used to link blocks, ensuring that any changes to a block are detected and the entire chain is compromised.
While hash functions are powerful tools, they are not without their vulnerabilities. Several security risks associated with hash functions include:
A collision occurs when two different inputs produce the same hash value. While a good hash function minimizes the risk of collisions, the mathematical nature of hash functions means that they are not entirely collision-resistant. To mitigate this risk, developers often use techniques such as salting and multi-hashing.
A preimage attack involves finding an input that produces a specific hash value. While hash functions are designed to be one-way and computationally infeasible to reverse, the possibility of preimage attacks remains a concern. This risk is often mitigated by using stronger and more secure hash functions.
A second preimage attack involves finding a different input that produces the same hash value as a given input. This can be a significant security risk, especially in the context of file integrity. To protect against second preimage attacks, developers often use more secure hash functions and additional security practices.
Hash functions are fundamental tools in the realm of cryptography and data security. They provide a simple yet powerful method for ensuring data integrity and protecting sensitive information. Understanding the mechanics, applications, and security risks associated with hash functions is crucial for anyone working in data security and related fields.
In the next part of this article, we will delve deeper into the technical aspects of hash functions, exploring their implementation and the role they play in various cryptographic protocols. Stay tuned for more insights into this fascinating topic!
The technical aspects of hash functions encompass both the theoretical underpinnings and practical implementation details. Understanding these aspects can provide valuable insights into how these tools work and why they remain essential in modern data security.
At their core, hash functions rely on complex mathematical operations to produce consistent outputs. For instance, a popular type of hash function, Secure Hash Algorithm (SHA), operates through a series of bitwise operations, modular arithmetic, and logical functions.
SHA-256, for example, is a widely used hash function that processes data in 512-bit blocks and produces a 256-bit hash. The algorithm involves a sequence of rounds, each consisting of a combination of bitwise operations, logical functions, and modular additions. These operations ensure that even a small change in the input results in a significantly different output, a characteristic known as the avalanche effect.
The process begins with initializing a set of constants and the hash value itself. It then processes the message in successive blocks, applying a series of bitwise operations and modular arithmetic. The final round produces the hash value. The complexity and precision of these operations contribute to the security and robustness of the hash algorithm.
Implementing a hash function requires careful consideration of multiple factors, including memory management, performance optimization, and security enhancements. Developers often use optimized libraries and frameworks to ensure that hash functions run efficiently.
Memory Management: Efficient memory usage is crucial for performance. Hash functions must handle varying input sizes gracefully and avoid unnecessary memory allocations. Techniques such as just-in-time (JIT) compilation and buffer pooling can enhance performance and reduce memory overhead.
Performance Optimization: Hash functions need to execute quickly, especially in high-throughput environments. Optimizations such as parallel processing, pipeline architecture, and vectorized operations can significantly improve performance. Additionally, using specialized hardware, such as GPUs and SIMD (Single Instruction Multiple Data) instructions, can further boost efficiency.
Security Enhancements: Beyond the basic hashing algorithms, developers employ additional measures to fortify hash functions. Techniques like salting, multi-hashing, and rate limiting help protect against common attacks.
Salting refers to adding a random value (salt) to the data before applying the hash function. This helps prevent preimage attacks by making each salted hash unique. Even if an attacker manages to find a hash, they would need to know the corresponding salt to reproduce the original data. Salting significantly increases the difficulty of brute-force attacks.
Multi-hashing involves applying two or more hash functions to the same piece of data. This multi-step process further enhances security by increasing the computational effort required to crack the hash. Techniques like PBKDF2 (Password-Based Key Derivation Function 2) combine multiple rounds of hashing to generate a final hash value.
Rate limiting is a technique used to slow down or restrict the number of hash computations that can be performed within a given time frame. This measure is particularly useful in scenarios where password hashing is involved. By limiting the rate at which a hash function can operate, attackers are forced to spend more time and computational resources, thus deterring brute-force attacks.
Hash functions find application across a wide range of domains, from software development to cybersecurity. Here are some specific scenarios where hash functions are utilized:
When downloading software or firmware updates, users often verify the integrity of the files using checksums or hashes. This check ensures that the downloaded file matches the expected value, preventing accidental corruption or malicious tampering.
For example, when a user downloads an ISO image for a Linux distribution, they might compare the hash value of the downloaded file with a pre-provided hash value from the official repository. Any discrepancy would indicate that the file is compromised or corrupted.
Storing plaintext passwords is highly insecure. Instead, web applications and database systems use hash functions to store a secure representation of passwords. When a user attempts to log in, their password is hashed and compared with the stored hash value.
This method ensures that even if the password database is compromised, the actual passwords remain secured. Additionally, using a salt alongside the hash function adds another layer of security by making it more difficult to crack individual passwords.
Many cryptographic protocols utilize hash functions to ensure data integrity and secure communication. For instance, Secure Sockets Layer (SSL) and Transport Layer Security (TLS) implementations often use hash functions to verify the integrity of the transmitted data.
In blockchain technology, hash functions are essential for maintaining the integrity and security of blockchain networks. Each block in the blockchain contains a hash of the previous block, creating an immutable chain of blocks. Any alteration in a single block would invalidate all subsequent blocks, thanks to the hash linkage.
Hash functions play a critical role in distributed systems, particularly in distributed hash tables (DHTs). DHTs use hash functions to distribute key-value pairs across a network of nodes, ensuring efficient data lookup and storage.
DHTs employ a consistent hashing mechanism, where keys are mapped to nodes based on their hash values. This ensures that even if nodes join or leave the network, the overall structure remains stable and data can be efficiently retrieved.
Despite their utility, hash functions face several challenges and ongoing research aims to address these issues:
The rapid development of quantum computing poses a significant threat to traditional hash functions. Quantum computers could potentially perform certain tasks, such as solving discrete logarithm problems, much faster than classical computers. As a result, efforts are underway to develop post-quantum cryptographic algorithms that are resistant to quantum attacks.
Potential candidates for post-quantum cryptography include lattice-based cryptography, code-based cryptography, and multivariate polynomial cryptography. These methods are being explored as promising alternatives to current hash functions and cryptographic protocols.
To enhance performance and cater to growing demands, there is continuous research into optimizing hash functions for parallel processing. This involves designing hash algorithms that can efficiently distribute tasks across multiple threads or processors. By doing so, hash functions can handle larger datasets and provide faster verification times.
To address evolving security threats, researchers are developing adaptive hash functions that can dynamically adjust parameters based on real-time security assessments. These adaptive techniques aim to provide more robust protection against emerging cyber threats and maintain the security of data over time.
In the context of blockchain technology, hash functions continue to evolve. As blockchain systems grow in scale and complexity, there is a need for hash functions that can efficiently support large-scale data verification and consensus mechanisms.
Newer blockchain systems may integrate more advanced hash functions to enhance privacy and security. For instance, zero-knowledge proofs (ZKPs) leverage hash functions to enable secure data verification without revealing the underlying data. This technology promises to revolutionize privacy-preserving blockchain applications.
Hash functions are indispensable tools in modern data security, serving a wide array of practical needs from data integrity checks to password storage and beyond. Their intricate mathematical designs ensure that even small changes in input lead to vastly different outputs, providing the necessary security and reliability.
As technology continues to advance, the challenges surrounding hash functions remain dynamic. From addressing quantum computing threats to improving adaptability and speed, the future holds exciting developments that promise to enhance the security and efficiency of hash functions further.
In conclusion, hash functions play a vital role in modern cryptography and data security. They serve a multitude of purposes, from ensuring data integrity to securing passwords and enabling secure communication. Understanding the technical aspects and applications of hash functions is crucial for anyone involved in cybersecurity, software development, or any field that requires robust data protection.
While hash functions are remarkably effective, they are not without their challenges. The evolving landscape of cyber threats, particularly the threat posed by quantum computing, necessitates ongoing research and innovation in the field. Adaptive and faster processing techniques are continually being developed to address these new challenges.
The future of hash functions looks promising. With ongoing advancements in technology and security, we can expect more secure and efficient hash functions that can withstand the evolving threats. As blockchain and other distributed systems continue to grow, the role of hash functions in these environments will likely become even more critical.
To stay ahead in the field of data security, it is essential to stay informed about the latest developments in hash functions. By understanding their underlying principles and practical implications, we can better protect ourselves and contribute to a more secure digital world.
For further exploration, you might consider reviewing the latest research papers on hash functions, exploring the implementation details of specific algorithms, and keeping up with the latest breakthroughs in the field of cryptography.
Thank you for reading this comprehensive guide to hash functions. We hope this article has provided valuable insights into this foundational aspect of modern data security.



Your personal space to curate, organize, and share knowledge with the world.
Discover and contribute to detailed historical accounts and cultural stories. Share your knowledge and engage with enthusiasts worldwide.
Connect with others who share your interests. Create and participate in themed boards about any topic you have in mind.
Contribute your knowledge and insights. Create engaging content and participate in meaningful discussions across multiple languages.
Already have an account? Sign in here

Discover how the SHA-256 hashing algorithm secures digital data, powers blockchain, and ensures integrity. Learn its key...
View Board
Explore the fascinating evolution of cryptography, from ancient methods to modern breakthroughs, in our insightful artic...
View Board
**Meta Description:** "Discover how quantum cryptography revolutionizes secure communication with unbreakable encrypti...
View Board
Unlock the intricacies of the Advanced Encryption Standard (AES) in our comprehensive guide. Explore its key mechanisms,...
View Board
Explore the fascinating journey of the monoalphabetic cipher, from its historical roots in ancient civilizations to its ...
View Board
Explore how digital signatures are revolutionizing data security by verifying identity and ensuring data integrity in th...
View Board
Discover the pivotal role of the Diffie-Hellman Key Exchange in secure communications. Learn how this foundational crypt...
View Board
Explore the essentials of Public Key Infrastructure (PKI) as the foundation of secure digital communication. Discover ho...
View Board
Discover the essentials of encryption and decryption, the backbone of data security, in this comprehensive guide. Learn ...
View Board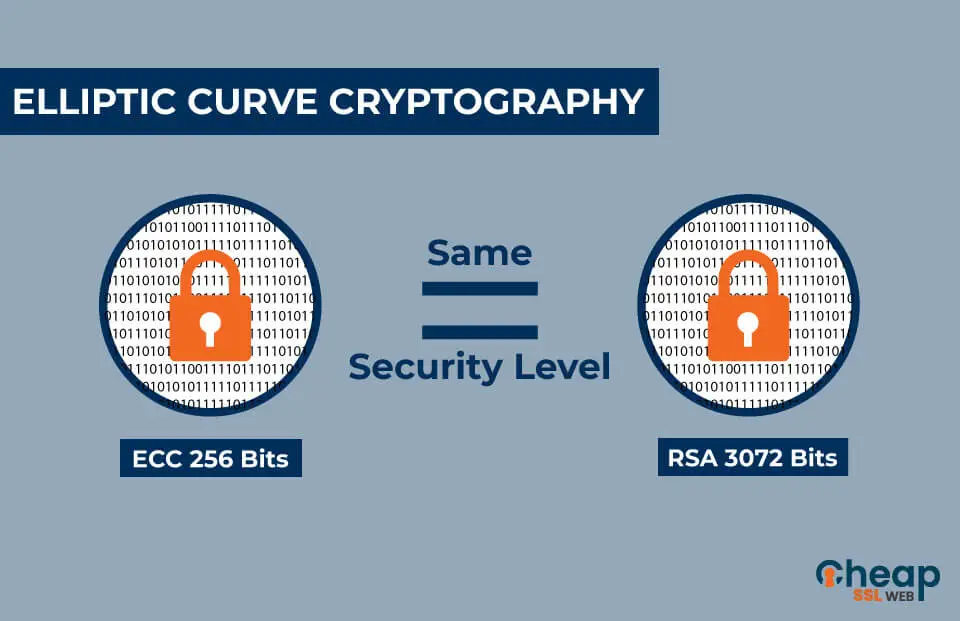
Discover the power of Elliptic Curve Cryptography (ECC) in "Understanding Elliptic Curve Cryptography: A Modern Approach...
View Board
Explore the profound legacy of Donald Knuth, the visionary architect of algorithms and a luminary in computer science. D...
View Board
Descubra como o algoritmo SHA-256 garante segurança digital, desde blockchain até proteção de senhas. Entenda seu funcio...
View Board
Explore the captivating history of polyalphabetic ciphers, a cornerstone of cryptography that revolutionized secure comm...
View Board
Explore the fascinating journey of cryptography from ancient times to modern day in "The Evolution of Early Cryptographi...
View Board
Encryption in 2025: Trends, Standards, and Future-Proofing Encryption is the cornerstone of modern data security, trans...
View BoardExplore the transformative potential of quantum computing in our in-depth article, revealing how its advanced processing...
View Board
आधुनिक क्रिप्टोग्राफी को समझें हिंदी वर्णमाला के माध्यम से। जानें कैसे स्वर-व्यंजन पब्लिक-प्राइवेट कीज़ की तरह क
View Board
AES एन्क्रिप्शन: डिजिटल सुरक्षा का सबसे विश्वसनीय मानक। जानें कैसे AES-256 आपके डेटा को हैकर्स से सुरक्षित रखता है।
View Board
Descubra como a criptografia de chave assimétrica protege dados sem compartilhar segredos, revolucionando a segurança di...
View Board
Comments