Exploring the Meaning and Impact of Wneth-Mia-My8ologikh-Lysh
Language is a living, breathing entity, constantly evolving with culture and technology. The phrase Wneth-Mia-My8ologikh-Lysh presents a fascinating case study in this evolution. While appearing cryptic at first glance, its core component, "Lysh" or "lush," unlocks a vibrant discussion on slang, meaning, and online communication in the digital age. This series explores the multifaceted nature of this term and its significance in global discourse.
The term lush carries surprising weight in the English lexicon. Far from having a single simple meaning, it is a word with deep historical roots and diverse contemporary applications. Its presence within a phrase like "My8ologikh-Lysh" hints at a modern, digitally-shorthand origin, blending linguistic creativity with traditional interpretation. This article will begin unpacking these complex layers.
Decoding Lush: The Power of Contextual Definitions
To understand any derivative like Wneth-Mia-My8ologikh-Lysh, we must first grasp its foundational word. The term "lush" serves as a perfect example of how context dictates meaning entirely. Depending on who you ask and where they are from, this single word can paint starkly different pictures.
In formal English, its primary definition is botanical. Lush describes vegetation or growth that is particularly rich, dense, and thriving. Think of a verdant rainforest, a succulent garden, or fertile farmland. This usage conveys abundance, vitality, and natural beauty.
However, step into the realm of informal speech and slang, and the meaning shifts dramatically. Most commonly in American English, "lush" is a label for a person who drinks alcohol to excess. As sources confirm, it is synonymous with "alcoholic" or "drunkard," carrying a derogatory connotation. Yet, this is not the whole story.
A review of dictionary entries, including Merriam-Webster, shows the word originates from Middle English words meaning soft or lax, later evolving to denote juicy growth in the 18th century before gaining its alcohol-related slang in the 19th.
The most notable modern contrast comes from British slang. In the UK, especially among younger speakers, "lush" is overwhelmingly positive. It is an all-purpose adjective meaning lovely, beautiful, attractive, sexy, amazing, cool, or delicious. This dramatic divergence highlights the rich tapestry of the English language and sets the stage for understanding digital neologisms.
The Evolution of Lush: From History to Hashtags
The historical journey of the word "lush" provides a blueprint for how a term like Wneth-Mia-My8ologikh-Lysh might emerge online. The path from a descriptive adjective to modern slang reveals several key linguistic processes that are accelerated in the digital domain.
Historical Semantic Shifts and Modern Parallels
The word "lush" made a significant semantic leap from describing physical properties to describing human behavior. Its Middle English roots implying "softness or laxity" were later applied metaphorically. This leap mirrors how new terms are created and repurposed in online communities today.
In the 20th and 21st centuries, two distinct slang definitions became culturally entrenched across the Atlantic. The American "alcoholic" definition and the British "gorgeous" definition now coexist in the global lexicon. This regional variance becomes a key form of digital currency, especially for those creating content about language differences.
YouTube explainer videos specifically targeting non-native speakers on the topic of UK slang have garnered significant views. This indicates a rising global interest in regional English variations, a space where terms like "lush" are showcased as fascinating cultural artifacts.
Digital Remixing and the Creation of New Terms
The phrase Wneth-Mia-My8ologikh-Lysh appears to be a product of digital culture—a remix. Platforms like social media, gaming chats, and forums often see users create inventive spellings and compound terms to carve out unique identities or inside jokes. The substitution of "y" for "u" or "8" for "ate" is a classic feature of internet shorthand.
In this light, "My8ologikh" likely represents a stylized spelling of "mythological." Combined with "Lysh" as a phonetic variant of "lush," the phrase suggests a "mythologically lush" concept. This could describe something of epic, unworldly beauty or extravagance, blending the traditional "verdant" definition with the positive British slang meaning.
The full phrase Wneth-Mia-My8ologikh-Lysh may represent a username, a gamer tag, or a creative project title. This act of compounding and stylizing is how language continuously expands. It reflects a user's intention to stand out while embedding layers of existing cultural meaning, primarily from the versatility of the word "lush."
The Cultural Weight of a Single Word
The dual life of "lush" as both compliment and critique shows how language reflects cultural attitudes. In the UK, calling someone "lush" is a warm, familiar compliment. In American contexts, the same word can be a serious judgment about one's character and health. This creates potential for cross-cultural misunderstandings but also for rich social commentary. Statistics from crowdsourced platforms support this split in perception.
Analysis of top definitions on Urban Dictionary indicates that approximately 70% of user-submitted meanings for "lush" relate to social drinking or alcohol consumption. The remaining ~30% largely capture the positive UK slang definition, highlighting its prevalence in informal digital spaces.
A study of recent media, such as reviews from Variety and Vulture, shows the aesthetic definition is also powerfully active. Critics use "lush" to describe extravagant visuals, vivid storytelling, and opulent productions. This usage bridges the gap between the traditional and the trendy, describing something as both richly beautiful and appealingly cool—a blend highly relevant to modern marketing and media.
Modern Usage and Social Trends
Beyond direct definitions, "lush" has spawned related social concepts. One niche but telling trend is "lush pressure," detailed in online slang forums. This refers to the peer pressure to participate in social drinking activities, particularly noted among UK young adults and housemates.
The fact that such a specific social phenomenon earns its own slang term illustrates how language evolves to name modern social realities. While data on usage frequency post-2023 is limited, the sustained visibility of "lush" across platforms proves its utility. It remains a flexible, evocative word capable of describing landscapes, people, experiences, and even social dynamics.
This cultural weight makes "lush" a prime candidate for inclusion in a constructed phrase like Wneth-Mia-My8ologikh-Lysh. It allows the creator to tap into a rich vein of existing connotations—luxury, beauty, rebellion, socialization, or excess—all encoded within a single, efficient syllable.
Understanding this foundation is crucial for deciphering the larger, more complex phrase. In part two, we will deconstruct the potential meanings of "My8ologikh" and "Wneth-Mia," analyzing how internet linguistics creates new semantic possibilities and drives online identity formation.
Analyzing My8ologikh-Lysh: Internet Linguistics and Identity
The creative spelling of My8ologikh-Lysh is a hallmark of digital communication. Users often replace letters with numbers or alter spellings to create memorable handles, gamertags, or slang. This process, known as Leet Speak or 1337, transforms language into a code that fosters community and exclusivity.
In this case, "My8ologikh" is a stylized version of "mythological." The "8" replaces the "ate" sound, a common substitution in online spaces. Combined with "Lysh," the phrase constructs a unique identity that translates to "mythologically lush." This suggests something possessing an epic, almost legendary quality of richness, beauty, or extravagance.
This inventive wordplay reflects a core principle of internet linguistics. Users are not passive consumers of language but active creators. By blending the ancient concept of "mythology" with the multifaceted slang of "lush," the creator of this phrase builds a personal brand that is both grandiose and contemporary.
The Significance of Alphanumeric Substitution
The use of "8" for "ate" is more than a simple trick. It serves specific functions in digital identity formation. This form of spelling creates a unique string that is easier to secure as a username on platforms with millions of users. A simple "mythologicallush" is likely already taken, but My8ologikh-Lysh stands out.
Furthermore, this stylization implies a level of digital literacy and cultural awareness. It signals membership in communities, particularly gaming and social media circles, where such linguistic creativity is commonplace and valued. It acts as a subtle badge of belonging.
- Username Availability: Creative spelling increases the chances of securing a desired online identity.
- Community Signaling: It demonstrates familiarity with internet subcultures and their linguistic norms.
- Memorability: An unusual spelling makes a name more distinctive and easier for others to recall.
Building a Personal Mythos Online
The choice of "mythological" is particularly revealing. In online environments, individuals craft elaborate personas. A "mythological" identity suggests a narrative of epic proportions, perhaps hinting at a skilled gamer, a creative storyteller, or someone with a larger-than-life online presence.
When paired with "lush," this mythological identity is imbued with specific qualities. Depending on the intended interpretation of "lush," it could mean:
- A persona of exceptional skill and virtuosity (lush as rich/abundant).
- A character known for attractiveness or coolness (lush as UK slang).
- An identity associated with celebratory excess (lush as related to drinking culture).
This layered meaning allows for a rich, ambiguous personal brand that can be interpreted in multiple ways by different audiences.
The Global Journey of Lush: Regional Slang in a Digital World
The internet has collapsed geographical boundaries, forcing regional slang terms like "lush" into a global spotlight. This creates a fascinating dynamic where words with specific local meanings must find their place in an international lexicon. The popularity of "lush" in its positive sense is a testament to the influence of British media and online content.
Platforms like YouTube and TikTok are powerful vectors for slang dissemination. Creators produce content specifically designed to explain British colloquialisms to a global audience. These videos often highlight words like "lush" as charming or quirky examples, increasing their adoption beyond the UK.
YouTube explainer videos on UK slang terms like "lush" regularly garner hundreds of thousands of views, indicating a significant global appetite for understanding these regional linguistic nuances.
This exposure leads to cross-cultural pollination. A viewer in the United States might start using "lush" in the British sense, either ironically or as a genuine adoption. This can cause confusion but also enriches the conversational toolbox of global English speakers, adding layers of expressive potential.
Potential for Misunderstanding and Context Clues
When a term like Wneth-Mia-My8ologikh-Lysh enters a global chat room or social media feed, its meaning is not always clear. The recipient's interpretation of "Lysh" will depend entirely on their cultural background. An American might misinterpret a well-intentioned British compliment.
Successful navigation of this ambiguity relies heavily on contextual clues. The platform, the tone of the conversation, and the user's other content provide hints. If "My8ologikh-Lysh" is a gamertag in a fantasy role-playing game, the "lush as rich/abundant" interpretation is most likely. If it's a username on a fashion influencer's Instagram, the "attractive" meaning is probable.
This necessity for context decoding is a fundamental skill in modern digital communication. It requires users to be more perceptive and culturally aware, moving beyond literal definitions to grasp intended meaning.
Lush in Contemporary Media and Marketing
The evocative power of "lush" has not gone unnoticed by creators and marketers. Its ability to conjure images of opulence, sensory pleasure, and vibrant life makes it a highly effective descriptive tool. Analysis of recent media reveals its consistent application in reviews and promotional materials.
Entertainment critics frequently use "lush" to praise productions with strong visual and auditory aesthetics. A film might be described as having "lush cinematography," meaning its visuals are rich, detailed, and sumptuous. A musical score might be called "lush" to indicate its layered, harmonious, and emotionally resonant qualities.
This usage strategically blends the word's traditional and slang meanings. It implies that the work is not just technically proficient (verdant) but also deeply appealing and satisfying (cool/amazing). This dual appeal makes it a powerful piece of critical vocabulary.
Branding and the Lush Aesthetic
The word has even been adopted as a proper noun by the successful cosmetics company Lush. This branding is a masterstroke, as the word perfectly encapsulates the brand's identity. It promises fresh, ethically sourced, and sensory-rich products.
The brand association reinforces the word's positive connotations. For many, "lush" is now tied to ideas of self-care, natural beauty, and indulgence. This commercial success demonstrates the economic value of evocative language.
When a term like "lush" is embedded in a phrase like My8ologikh-Lysh, it borrows a small fraction of this branding power. It suggests a persona or creation that is desirable, high-quality, and pleasurable, aligning the user with these positive attributes.
Statistical Presence in Digital Content
While hard data on the frequency of "lush" is scarce, its persistent appearance in digital content is telling. A simple search on popular platforms reveals its widespread use.
- Social Media: Hashtags like lushlife and lush have millions of posts, often depicting travel, food, and lifestyle content associated with abundance and beauty.
- Gaming and Streaming: "Lush" is used to describe detailed game worlds or highly rewarding gameplay experiences.
- Product Reviews: It is a common adjective in reviews for everything from headphones (lush soundscape) to pillows (lush comfort).
This omnipresence confirms that lush is a word with significant cultural currency. Its flexibility allows it to describe a vast range of positive experiences, making it a valuable asset in the lexicon of creators and consumers alike. Its incorporation into inventive phrases is a natural extension of its utility.
The Wneth-Mia Element: Completing the Digital Lexicon Puzzle
The final component of the phrase, Wneth-Mia, presents the most cryptic element for analysis. Unlike "My8ologikh-Lysh," this prefix does not have a clear, direct English translation. This ambiguity is a common and intentional feature in online identity creation, serving to enhance uniqueness and personal significance.
One plausible interpretation is that Wneth-Mia is a highly stylized or phonetic spelling of a name or a concept. The "Wn" could represent a sound like "win" or "wen," while "eth" might be an archaic suffix or a creative flourish. "Mia" is a common given name across many cultures. Together, they may function as a unique identifier, the personal brand before the descriptive "mythologically lush" tag.
This practice of creating indecipherable prefixes is prevalent in gaming and online communities. It ensures absolute uniqueness for usernames on global platforms. A handle like "MiaLush" would be quickly taken, but Wneth-Mia-My8ologikh-Lysh is virtually guaranteed to be available, establishing a distinct digital footprint from the outset.
Intentional Obscurity and Personal Meaning
In many cases, such strings of characters hold deep personal meaning only to the creator. "Wneth" could be an anagram, a reference to a fictional character, a mashup of loved ones' initials, or a word from a non-English language. This intentional obscurity adds a layer of mystique and privacy.
It allows the user to broadcast a complex identity while retaining a private connection to its origin. For the outside observer, the full phrase becomes a cohesive unit—a memorable, striking digital name whose exact etymology remains a personal secret. This balance of public presentation and private meaning is a key aspect of modern online interaction.
- Absolute Uniqueness: Guarantees username availability on any social or gaming platform.
- Personal Significance: Often encodes private references meaningful only to the creator.
- Mystique and Branding: Creates an intriguing persona that invites curiosity.
SEO and the Discoverability of Invented Language
From a digital marketing and Search Engine Optimization (SEO) perspective, a term like Wneth-Mia-My8ologikh-Lysh operates in a fascinating niche. It is a long-tail keyword of immense specificity. While it will not rank for high-volume searches like "what does lush mean," it creates its own unique digital territory.
This is a powerful strategy for personal branding. By inventing a unique phrase, an individual or project can dominate search results for that exact string. Any content, social profile, or creative work associated with this name will be easily discoverable to anyone searching for it, free from the noise of more common terms.
Furthermore, because the phrase contains the recognizable core keyword "Lysh/lush," it maintains a tangential connection to those broader search queries. Sophisticated search algorithms might recognize the semantic relationship, allowing the unique phrase to benefit from the established relevance of its root word in certain contexts.
In SEO strategy, a unique branded phrase acts as a "zero-competition keyword," allowing creators to own their digital search results entirely and build authority around a specific niche identity.
Building a Digital Ecosystem Around a Name
Adopting such a distinctive name encourages the creation of a cohesive online ecosystem. A user with this handle would likely use it across platforms—Twitter, Twitch, Instagram, gaming clients. This consistency improves discoverability and reinforces the brand.
Content created under this name, whether videos, posts, or artwork, all contributes to the semantic footprint of the phrase. Over time, search engines associate the unique string with the specific type of content the user produces, whether it's gaming commentary, digital art, or linguistic analysis. The invented name becomes a vessel for a complete online identity.
The Future of Linguistic Creativity Online
The phenomenon exemplified by Wneth-Mia-My8ologikh-Lysh is not an outlier but a signpost for the future of language. Digital spaces are incubators for linguistic innovation, where the rules of spelling, grammar, and word formation are constantly being tested and rewritten.
We are moving toward an even more personalized and visually creative linguistic landscape. Elements like emojis, custom fonts, special characters, and even profile pictures are becoming integral parts of how we "spell" our identities and express ideas online. A username is no longer just text; it is a multimodal brand symbol.
Implications for Global Communication
As these creative forms proliferate, the ability to decode meaning becomes a critical digital literacy skill. Understanding that "8" means "ate," that "Lysh" can mean "beautiful" or "drunk," and that a random prefix like "Wneth" is a personal marker, is part of navigating global digital culture.
This environment also fosters a more democratic form of language creation. Unlike formal language changes that take decades, online slang and neologisms can achieve global reach in months. A single viral post can introduce a new term or spelling convention to millions, demonstrating the accelerated evolution of communication.
Conclusion: Decoding the Digital Tapestry
Our exploration of Wneth-Mia-My8ologikh-Lysh reveals much more than the possible meaning of a single unusual phrase. It provides a window into the dynamic forces shaping language in the 21st century. This inventive string is a microcosm of digital culture, woven from threads of history, regional slang, identity play, and technological adaptation.
The journey began with the deconstruction of "lush," a word whose history and divergent meanings underline the fundamental importance of context. From describing fertile land to labeling a heavy drinker to complimenting a friend, its evolution mirrors the way language constantly adapts to human needs.
We then saw how the internet acts as a catalyst, encouraging the creative remixing of language through alphanumeric substitution and compounding. The construction of My8ologikh-Lysh demonstrates how users build personal mythologies, leveraging the ambiguity and richness of existing words to craft unique, memorable identities.
Key Takeaways from the Analysis
- Context is King: The meaning of any word, especially slang like "lush," is entirely dependent on its cultural and situational context.
- Language is a Creative Tool: Online users are active linguists, inventing spellings and compound terms to forge unique digital identities and ensure username availability.
- Globalization of Slang: Digital platforms rapidly export regional slang (like the positive UK "lush"), creating a more blended but potentially confusing global English lexicon.
- Personal Branding as Linguistics: Invented phrases like Wneth-Mia-My8ologikh-Lysh function as zero-competition SEO keywords, allowing individuals to own their digital search presence completely.
The phrase, in its complete form, stands as a testament to the human desire for distinctiveness in a connected world. It shows that even in vast digital crowds, we find ways to inscribe our individuality through creative language. The "Wneth-Mia" remains a personal cipher, while the "My8ologikh-Lysh" broadcasts an aspirational descriptor—a declaration of being epic, rich, and profoundly appealing in a self-defined way.
As we move forward, we can expect language to continue its rapid, user-driven evolution. The next Wneth-Mia-My8ologikh-Lysh is being typed into a username field right now, beginning its own journey from personal inside joke to a piece of the vast, intricate tapestry of digital communication. Understanding these processes is key to understanding not just what we say online, but who we are becoming in the digital age.
Quantum Cryptography: The Future of Secure Communication
Introduction to Quantum Cryptography
In an era where cybersecurity threats are becoming increasingly sophisticated, the demand for unbreakable encryption has never been greater. Traditional cryptographic methods, while effective, are vulnerable to advancements in computing power and clever hacking techniques. Enter quantum cryptography—a revolutionary approach to secure communication that leverages the principles of quantum mechanics to ensure unparalleled security. Unlike classical encryption, which relies on mathematical complexity, quantum cryptography is built on the inherent uncertainty and fundamental laws of physics, making it theoretically immune to hacking attempts.
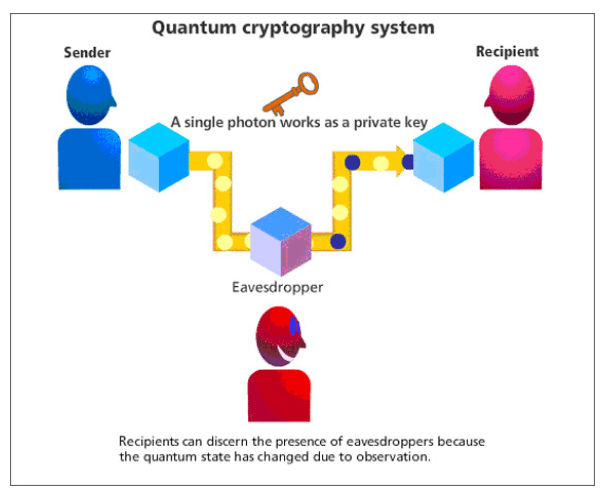
The foundation of quantum cryptography lies in quantum key distribution (QKD), a method that allows two parties to generate a shared secret key that can be used to encrypt and decrypt messages. What makes QKD unique is its reliance on the behavior of quantum particles, such as photons, which cannot be measured or copied without disturbing their state. This means any attempt to eavesdrop on the communication will inevitably leave traces, alerting the legitimate parties to the intrusion.
The Principles Behind Quantum Cryptography
At the heart of quantum cryptography are two key principles of quantum mechanics: the Heisenberg Uncertainty Principle and quantum entanglement.
Heisenberg Uncertainty Principle
The Heisenberg Uncertainty Principle states that it is impossible to simultaneously know both the position and momentum of a quantum particle with absolute precision. In the context of quantum cryptography, this principle ensures that any attempt to measure a quantum system (such as a photon used in QKD) will inevitably alter its state. Suppose an eavesdropper tries to intercept the quantum key during transmission. In that case, their measurement will introduce detectable disturbances, revealing their presence and preserving the key's secrecy.
Quantum Entanglement
Quantum entanglement is a phenomenon where two or more particles become linked in such a way that the state of one particle immediately influences the state of the other, regardless of the distance separating them. This property allows for the creation of highly secure cryptographic systems. For example, if entangled photons are used in QKD, any attempt to intercept one photon will disrupt the entanglement, providing a clear indication of tampering.
How Quantum Key Distribution (QKD) Works
QKD is the cornerstone of quantum cryptography and involves the exchange of cryptographic keys between two parties—traditionally referred to as Alice (the sender) and Bob (the receiver)—using quantum communication channels. Here's a simplified breakdown of the process:
Step 1: Transmission of Quantum States
Alice begins by generating a sequence of photons, each in a random quantum state (polarization or phase). She sends these photons to Bob over a quantum channel, such as an optical fiber or even through free space.
Step 2: Measurement of Quantum States
Upon receiving the photons, Bob measures each one using a randomly chosen basis (e.g., rectilinear or diagonal for polarization-based systems). Due to the probabilistic nature of quantum mechanics, Bob’s measurements will only be accurate if he chooses the same basis as Alice did when preparing the photon.
Step 3: Sifting and Key Formation
After the transmission, Alice and Bob publicly compare their choice of measurement bases (but not the actual results). They discard any instances where Bob measured the photon in the wrong basis, retaining only the cases where their bases matched. These remaining results form the raw key.
Step 4: Error Checking and Privacy Amplification
To ensure the key's integrity, Alice and Bob perform error checking by comparing a subset of their raw key. If discrepancies exceed a certain threshold, it indicates potential eavesdropping, and the key is discarded. If no significant errors are found, they apply privacy amplification techniques to distill a final, secure key.
Advantages of Quantum Cryptography
Quantum cryptography offers several compelling advantages over traditional encryption methods:
Unconditional Security
Unlike classical encryption, which depends on computational hardness assumptions (e.g., factoring large primes), quantum cryptography provides security based on the laws of physics. This means it remains secure even against adversaries with unlimited computational power.
Detection of Eavesdropping
Any attempt to intercept quantum-encoded information will disturb the system, making it immediately detectable. This feature ensures that compromised communications can be identified and discarded before sensitive data is exposed.
Future-Proof Against Quantum Computers
With the advent of quantum computers, classical cryptographic algorithms like RSA and ECC are at risk of being broken. Quantum cryptography, particularly QKD, remains resistant to such threats, making it a future-proof solution.
Current Applications and Challenges
While quantum cryptography holds immense promise, its practical implementation faces several hurdles. Currently, QKD is being used in limited scenarios, such as securing government communications and financial transactions. However, challenges like high implementation costs, limited transmission distances, and the need for specialized infrastructure hinder widespread adoption.
Despite these obstacles, research and development in quantum cryptography are advancing rapidly. Innovations in satellite-based QKD and integrated photonics are paving the way for more accessible and scalable solutions. As the technology matures, quantum cryptography could become a standard for securing critical communications in the near future.
Stay tuned for the next part of this article, where we will delve deeper into real-world implementations of quantum cryptography, its limitations, and the ongoing advancements in this groundbreaking field.
Real-World Implementations of Quantum Cryptography
The theoretical promise of quantum cryptography has begun translating into practical applications, albeit in niche and high-security environments. Governments, financial institutions, and research organizations are leading the charge in deploying quantum-secure communication networks, recognizing the urgent need for protection against both current and future cyber threats.
Government and Military Use Cases
National security agencies were among the first to recognize the potential of quantum cryptography. Countries like China, the United States, and Switzerland have implemented QKD-based secure communication networks to safeguard sensitive governmental and military data. In 2017, China’s Quantum Experiments at Space Scale (QUESS) satellite, also known as Micius, successfully demonstrated intercontinental QKD between Beijing and Vienna, marking a milestone in global quantum-secured communication.
Similarly, the U.S. government has invested in quantum-resistant encryption initiatives through collaborations involving the National Institute of Standards and Technology (NIST) and Defense Advanced Research Projects Agency (DARPA). These efforts aim to transition classified communications to quantum-safe protocols before large-scale quantum computers become a reality.
Financial Sector Adoption
Banks and financial enterprises handle vast amounts of sensitive data daily, making them prime targets for cyberattacks. Forward-thinking institutions like JPMorgan Chase and the European Central Bank have begun experimenting with QKD to protect high-frequency trading systems, interbank communications, and customer transactions.
In 2020, the Tokyo Quantum Secure Communication Network, a collaboration between Toshiba and major Japanese financial firms, established a quantum-secured link between data centers, ensuring tamper-proof financial transactions. Such implementations underscore the growing confidence in quantum cryptography as a viable defense against economic espionage and fraud.
Technical Limitations and Challenges
Despite its groundbreaking advantages, quantum cryptography is not without hurdles. Researchers and engineers must overcome several technical barriers before QKD can achieve mainstream adoption.
Distance Constraints
One of the biggest challenges in QKD is signal loss over long distances. Photons used in quantum communication degrade when traveling through optical fibers or free space, limiting the effective range of current systems. While terrestrial QKD networks rarely exceed 300 kilometers, researchers are exploring quantum repeaters and satellite relays to extend reach. China’s Micius satellite has achieved intercontinental key distribution, but ground-based infrastructure remains constrained by physical losses.
Key Rate Limitations
Quantum key distribution is also bottlenecked by the speed at which secure keys can be generated. Traditional QKD systems produce keys at rates of a few kilobits per second—sufficient for encrypting voice calls or small data packets but impractical for high-bandwidth applications like video streaming. Advances in superconducting detectors and high-speed modulators aim to improve key rates, but further innovation is needed to match classical encryption speeds.
Cost and Infrastructure
The specialized hardware required for QKD—such as single-photon detectors, quantum light sources, and ultra-low-noise optical fibers—makes deployment expensive. For instance, commercial QKD systems can cost hundreds of thousands of dollars, putting them out of reach for most enterprises. Additionally, integrating quantum-secured links into existing telecommunication networks demands significant infrastructure upgrades, further complicating widespread adoption.
The Quantum vs. Post-Quantum Debate
Quantum cryptography often overlaps with discussions about post-quantum cryptography (PQC), leading to some confusion. While both address quantum threats, their approaches differ fundamentally.
QKD vs. Post-Quantum Algorithms
Quantum key distribution relies on the principles of quantum mechanics to secure communications inherently, whereas post-quantum cryptography involves developing new mathematical algorithms resistant to attacks from quantum computers. PQC solutions, currently being standardized by NIST, aim to replace vulnerable classical algorithms without requiring quantum hardware. However, QKD offers a unique advantage: information-theoretic security, meaning its safety doesn’t depend on unproven mathematical assumptions.
Hybrid Solutions Emerging
Recognizing the complementary strengths of both approaches, organizations are increasingly adopting hybrid systems combining QKD with post-quantum algorithms. This dual-layer encryption strategy ensures resilience even if one layer is compromised, providing a balanced transition path toward a quantum-safe future.
Breakthroughs in Quantum Networking
The push toward a quantum internet—a global network interconnected via quantum entanglement—has accelerated breakthroughs in quantum repeaters, memory storage, and entanglement swapping. These innovations address critical challenges in scaling quantum cryptography beyond point-to-point links.
Quantum Repeaters
Traditional signal amplifiers cannot be used in quantum communications without destroying the quantum states of photons. Quantum repeaters, still in experimental stages, aim to overcome this by leveraging entanglement swapping to extend the reach of QKD without measurement. Companies like Quantum Xchange in the U.S. and ID Quantique in Switzerland are pioneering modular repeater technologies to enable continental-scale quantum networks.
Quantum Memory
Storing quantum information is essential for synchronizing transmissions in large networks. Recent advances in atomic ensembles and rare-earth-doped crystals have demonstrated millisecond-long quantum memory retention—a critical step toward buffering entangled光子 for on-demand retrieval in complex networks.
Commercial and Open-Source Initiatives
The quantum cryptography market is witnessing a surge in private-sector involvement, with startups and tech giants alike racing to commercialize the technology.
Industry Leaders and Innovators
Companies like Toshiba, IBM, and QuintessenceLabs are offering enterprise-grade QKD solutions tailored for specific industries. Meanwhile, open-source projects such as the OpenQKD initiative by the European Union are fostering collaboration between academia and industry to standardize protocols and drive down costs.
Cloud-Based Quantum Security
Cloud providers are exploring quantum-secure services, such as AWS’s hybrid post-quantum TLS and Azure’s Quantum Network, allowing businesses to test quantum-resistant encryption without major infrastructure investments. These platforms serve as bridges for organizations transitioning toward full quantum readiness.
Looking Ahead
Quantum cryptography is transitioning from lab experiments to real-world deployments, but obstacles remain. The next decade will likely see breakthroughs in scalable QKD, affordable quantum hardware, and international standards—key enablers for a quantum-secured global infrastructure. In the final part of this series, we will explore speculative future applications, ethical considerations, and the role of policy in shaping quantum security’s trajectory.
Stay tuned for the concluding installment, where we examine how quantum cryptography could redefine privacy, governance, and trust in the digital age.
The Future of Quantum Cryptography: Ethical and Societal Implications
As quantum cryptography moves from theoretical research to practical implementation, it raises profound questions about its impact on society, governance, and individual privacy. The technology’s potential to revolutionize secure communication is undeniable, but it also introduces new challenges that must be addressed to ensure responsible adoption.
Privacy in the Quantum Era
Quantum cryptography promises unbreakable encryption, but it also poses ethical dilemmas. Governments and corporations could use quantum-secure networks to protect sensitive data, but the same technology might enable mass surveillance if misused. The balance between security and privacy will be a critical issue as quantum encryption becomes mainstream. Policymakers must establish clear regulations to prevent abuse while fostering innovation.
Global Security and Cyber Warfare
The advent of quantum computing and cryptography could shift the balance of power in cyber warfare. Nations with advanced quantum capabilities may gain an advantage in intelligence gathering and secure communications, potentially destabilizing international relations. The risk of a "quantum arms race" is real, with countries competing to develop quantum-resistant encryption and decryption tools. International cooperation will be essential to prevent an escalation of cyber conflicts.
Accessibility and Digital Divide
Quantum cryptography is currently expensive and complex, limiting its availability to wealthy nations and large corporations. If left unchecked, this could exacerbate the digital divide, leaving smaller businesses and developing nations vulnerable to cyberattacks. Efforts to democratize quantum-secure technologies—through open-source projects, subsidies, or international partnerships—will be crucial to ensuring equitable access.
Quantum Cryptography and Artificial Intelligence
The intersection of quantum computing and artificial intelligence (AI) presents both opportunities and risks. Quantum algorithms could enhance AI’s ability to analyze encrypted data, potentially breaking classical encryption methods. Conversely, AI could be used to optimize quantum cryptographic protocols, making them more efficient and secure. The synergy between these two fields will shape the future of cybersecurity.
AI-Powered Quantum Attacks
AI-driven cyberattacks are already a growing threat, and quantum computing could amplify their effectiveness. Machine learning models trained on quantum algorithms might identify vulnerabilities in classical encryption faster than human hackers. Defending against such threats will require AI-powered quantum defenses, creating a continuous arms race between attackers and defenders.
Quantum Machine Learning for Security
On the defensive side, quantum machine learning could revolutionize threat detection. Quantum-enhanced AI models could analyze vast datasets in real time, identifying anomalies and potential breaches with unprecedented accuracy. This could lead to proactive cybersecurity measures, where threats are neutralized before they cause harm.
The Role of Policy and Regulation
Governments and international organizations must play a proactive role in shaping the future of quantum cryptography. Without proper oversight, the technology could be weaponized or monopolized, leading to unintended consequences.
Standardization and Certification
Establishing global standards for quantum encryption is essential to ensure interoperability and security. Organizations like NIST and the International Telecommunication Union (ITU) are already working on post-quantum cryptographic standards, but more collaboration is needed to address emerging quantum threats. Certification programs for quantum-secure products will also be necessary to build trust among users.
Ethical Guidelines for Quantum Research
As quantum technology advances, ethical guidelines must be developed to govern its use. Researchers and policymakers should collaborate to address concerns such as data sovereignty, surveillance, and the militarization of quantum encryption. Transparency and public discourse will be key to ensuring that quantum cryptography benefits society as a whole.
Speculative Applications of Quantum Cryptography
Beyond cybersecurity, quantum cryptography could enable groundbreaking applications in various fields, from healthcare to space exploration.
Quantum-Secure Medical Data
Healthcare systems handle vast amounts of sensitive patient data, making them prime targets for cyberattacks. Quantum-secure encryption could protect medical records, ensuring patient confidentiality while enabling secure sharing of research data. This could accelerate medical breakthroughs while safeguarding privacy.
Interplanetary Communication
As humanity expands into space, secure communication between Earth and distant colonies or spacecraft will be critical. Quantum cryptography could enable unhackable communication links across vast distances, ensuring the integrity of mission-critical data. NASA and other space agencies are already exploring quantum communication for future Mars missions.
Quantum Voting Systems
Election security is a growing concern worldwide. Quantum-secure voting systems could prevent tampering and ensure the integrity of democratic processes. By leveraging quantum encryption, governments could create verifiable and tamper-proof digital voting mechanisms, restoring public trust in elections.
Conclusion: The Quantum Security Revolution
Quantum cryptography is poised to redefine the future of secure communication, offering unparalleled protection against cyber threats. However, its widespread adoption will require overcoming technical, ethical, and regulatory challenges. As we stand on the brink of a quantum revolution, collaboration between scientists, policymakers, and industry leaders will be essential to harness the technology’s potential while mitigating its risks.
The next decade will be pivotal in determining how quantum cryptography shapes our digital world. By addressing accessibility, ethical concerns, and global cooperation, we can ensure that this revolutionary technology serves as a force for good, safeguarding privacy and security in an increasingly connected world.
As quantum cryptography evolves, one thing is certain: the future of cybersecurity will be quantum, and the time to prepare is now.