Explore Any Narratives
Discover and contribute to detailed historical accounts and cultural stories. Share your knowledge and engage with enthusiasts worldwide.
The Roman Empire, known for its military might, architectural grandeur, and influential governance, also left a less conspicuous but equally intriguing legacy in the field of cryptography. While cryptographic techniques are often associated with modern warfare and espionage, the Romans implemented sophisticated methods to protect sensitive information from prying eyes. These techniques, although primitive by today's standards, laid foundational work for the art and science of cryptography, influencing the way encrypted communication developed through the centuries.
Roman cryptographic practices primarily evolved out of necessity during military campaigns. The need for secure communication was paramount, especially when relaying strategic orders that, if intercepted, could spell disaster. In an era before electronic communication, Romans relied on written messages. These messages had to be protected from enemies and any unintended recipients.
Cryptography during this period was less about complex algorithms and more about inventive ciphers. The most notable and widely used cipher was the Caesar Cipher, named after Julius Caesar himself. This technique involved a straightforward method of shifting letters in the alphabet to hide the true message. Although seemingly simple, it was effective enough to maintain secrecy among those who were unaware of the shift pattern used in the ciphertext.
Julius Caesar is often credited with pioneering one of the earliest forms of encryption known to the Western world. The Caesar Cipher operated on a simple principle: each letter in a plaintext message was shifted a certain number of places down the alphabet. For instance, with a shift of three, 'A' would become 'D', 'B' would become 'E', and so on.
This cipher offered a rudimentary level of security. Despite its simplicity, it was effective because it assumed that interceptors lacked knowledge of both the specific character shift and the concept of shifting altogether. The effort of decoding such scrambled text without this understanding would have been daunting and time-consuming for enemies who were not privy to cryptographic principles.
Though the Caesar Cipher showcased an early attempt to obscure communications, it was not impervious to decryption. The limited number of possible shifts (twenty-five in a Latin alphabet) meant that any determined interceptor, by systematically trying each shift, could eventually decipher the message. This vulnerability soon led to the development of more complex methods.
Rome also experimented with additional layers to their cryptography through the use of different substitutive elements and physical encryption tools. Among these were the 'scytale', a cryptographic tool believed to have been borrowed from the Spartans. This device utilized a physical rod upon which a message was inscribed in a strip of parchment wound spirally around it. The message was unreadable unless the parchment was unwound on a scytale of the same diameter. Such innovations demonstrated an early understanding of more advanced secure communication practices, extending beyond simple letter shifting.
While primarily used for military purposes, cryptography in ancient Rome was not strictly confined to the battlefield. Bears of political and personal significance also leveraged these techniques. Intriguingly, as literacy rates increased among Roman citizens, the use of cryptography extended to personal correspondence for safeguarding private information.
Cryptographic practices, therefore, played a subtle yet vital role in the societal and political fabric of Roman life. They were employed by statesmen looking to preserve confidentiality in political machinations, as well as lovers wishing to keep their romantic exchanges hidden from watchful eyes. This versatility hints at the broader understanding and adaptability of cryptographic applications beyond tactile military strategies.
The rich tapestry of Roman cryptographic history thus provides a fascinating insight into the early evolution of encrypted communication. As we continue to delve into the methods employed, it is crucial to appreciate how these ancient techniques not only addressed the needs of their time but also laid the groundwork for future developments in cryptography. In the next segment, we will explore more about how these techniques were refined and adapted, influencing the world of cryptography well beyond the fall of the Roman Empire.
As the Roman Empire expanded, the need for more complex and secure communication methods grew exponentially. The Caesar Cipher, while a cornerstone in Roman cryptography, eventually required enhancements to meet these heightened demands for secrecy. This necessity led to the exploration and adaptation of more intricate encryption methods that attempted to address the vulnerabilities present in simpler ciphers.
The evolution of Roman cryptographic techniques saw the incorporation of polyalphabetic ciphers, where multiple alphabets were used to encode a message. Unlike Julius Caesar’s single-shift approach, polyalphabetic ciphers introduced varying shifts during the message encryption. This technique provided a much-stronger deterrent against interception as it dramatically increased the complexity of decrypting the code without specific knowledge of the keys.
A noteworthy development in Roman cryptography was the introduction of mechanical devices that facilitated the encryption process. Historical records suggest the usage of various tools that were precursors to more sophisticated machinery for cryptography found in later centuries. Among these innovative devices was the Roman wheel cipher, also known as the 'quadrant', which allowed for multiple layers of encryption by rearranging different elements of text through mechanical rotation.
This innovation showcased an early understanding of mechanizing the encryption process, not only improving security but also easing the complexity involved in encoding and decoding messages manually. Combined with the use of complex keys, the cipher wheels remained a staple in cryptographic circles until the Middle Ages, illustrating the lasting influence of Roman ingenuity on secret communication tools.
The cryptographic systems developed by the Romans left a legacy that transcended the empire itself. As subsequent societies and military groups valued the importance of secure communication, Roman methods provided a blueprint for improvements and adaptations that echoed through medieval and modern cryptography.
With fallen seekers continually adapting and evolving these methods, it highlighted a significant progression from basic ciphers to more sophisticated systems utilized in various historical epochs. Among these was the Vigenère cipher, often referred to as an evolution of the principles first explored through Roman cryptographs. This cipher introduced a repeated polyalphabetic shift, influenced by the complex patterns the Roman cryptographers had begun exploring.
Furthermore, Roman efforts in cryptography influenced educational practices, such as the establishment of cryptography-studying schools among the medieval Italian city-states. These institutions fostered the development of cryptographic techniques used in diplomatic and managerial roles outside the military, broadening the horizons of encryption usage established during Roman times.
While our modern cryptographic methodologies overshadow Roman techniques in complexity and technological advancement, the basis of secret communication established during the Roman era remains undeniably essential. The Roman emphasis on simplicity yet effectivity in securing messages resonates with today’s cryptographic principles aimed at balancing accessibility and impenetrability.
In a cyber world dominated by algorithms and digital encryption keys, the Roman legacy demonstrates how even the most rudimentary techniques could provide robust security in communication scenarios particular to their era. As contemporary cryptographers innovate new pathways to secure digital information, acknowledging the historical frameworks laid down by Roman practices becomes instrumental in appreciating how far the science has come and where it may advance in the future.
The story of Roman cryptographic techniques is one of innovation born out of necessity, shaping the trajectory of secure communication for centuries to follow. From the Caesar Cipher's straightforward letter shifts to the complex wheel ciphers that inspired future mechanical encryption devices, the Romans endeavored to adapt and protect their messages beyond their immediate era.
By examining these ancient techniques, it becomes clear that cryptography's journey through history is more than just technological evolution—it's a testament to human ingenuity in overcoming challenges of secrecy and confidentiality. As we continue to push the boundaries of cryptographic science, the Roman ingenuity remains a profound reminder of our enduring quest to communicate securely across time and space.
Your personal space to curate, organize, and share knowledge with the world.
Discover and contribute to detailed historical accounts and cultural stories. Share your knowledge and engage with enthusiasts worldwide.
Connect with others who share your interests. Create and participate in themed boards about any topic you have in mind.
Contribute your knowledge and insights. Create engaging content and participate in meaningful discussions across multiple languages.
Already have an account? Sign in here

Delve into the captivating history of medieval cryptographic techniques, uncovering the clever innovations that paved th...
View Board
Explore the captivating history of polyalphabetic ciphers, a cornerstone of cryptography that revolutionized secure comm...
View Board
Unlock the intricacies of the Advanced Encryption Standard (AES) in our comprehensive guide. Explore its key mechanisms,...
View Board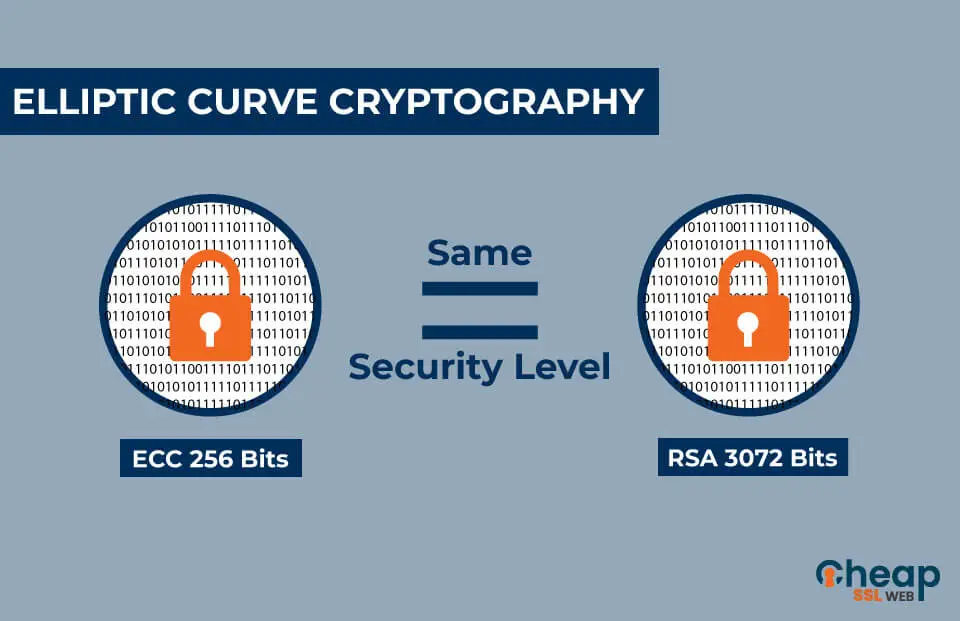
Discover the power of Elliptic Curve Cryptography (ECC) in "Understanding Elliptic Curve Cryptography: A Modern Approach...
View Board
Discover the pivotal role of the Diffie-Hellman Key Exchange in secure communications. Learn how this foundational crypt...
View Board
Explore the fascinating journey of the monoalphabetic cipher, from its historical roots in ancient civilizations to its ...
View Board
Encryption in 2025: Trends, Standards, and Future-Proofing Encryption is the cornerstone of modern data security, trans...
View Board
Explore the essentials of Public Key Infrastructure (PKI) as the foundation of secure digital communication. Discover ho...
View Board
Explore the fascinating evolution of cryptography, from ancient methods to modern breakthroughs, in our insightful artic...
View Board
Discover the essentials of encryption and decryption, the backbone of data security, in this comprehensive guide. Learn ...
View Board
Explore the secretive world of Cold War cryptography, where the U.S. and Soviet Union waged a cryptographic arms race wi...
View Board
Discover how the SHA-256 hashing algorithm secures digital data, powers blockchain, and ensures integrity. Learn its key...
View Board
Explore how digital signatures are revolutionizing data security by verifying identity and ensuring data integrity in th...
View Board
Discover the mysterious history of the Death Machine cipher, the WWII Enigma machine. Explore its origins, wartime role,...
View Board
Descubra a cifra monoalfabética, um clássico da criptografia que ensina fundamentos essenciais de segurança da informaçã...
View Board
Explore the fascinating journey of cryptography from ancient times to modern day in "The Evolution of Early Cryptographi...
View Board
Descubra como o algoritmo SHA-256 garante segurança digital, desde blockchain até proteção de senhas. Entenda seu funcio...
View Board
AES एन्क्रिप्शन: डिजिटल सुरक्षा का सबसे विश्वसनीय मानक। जानें कैसे AES-256 आपके डेटा को हैकर्स से सुरक्षित रखता है।
View Board
Descubra como a criptografia de chave assimétrica protege dados sem compartilhar segredos, revolucionando a segurança di...
View Board
Comments