Robert J. Skinner: The Cyber Guardian of the Digital Age
From Second Lieutenant to Three-Star General: A Journey of Leadership and Innovation
In the ever-evolving landscape of cyber warfare and digital defense, few names stand out like that of **Robert J. Skinner**. A retired United States Air Force lieutenant general, Skinner's career spans over three decades, marked by relentless dedication to communications, cyber operations, and information systems. His journey from a second lieutenant to a three-star general is not just a testament to his leadership but also a reflection of the critical role cybersecurity plays in modern military operations.
The Early Years: Foundation of a Cyber Leader
Robert J. Skinner's story begins on **November 7, 1989**, when he was commissioned as a second lieutenant via Officer Training School. His early achievements were a harbinger of the stellar career that lay ahead—he graduated as the second honor graduate, a clear indication of his commitment and prowess. Over the next three decades, Skinner would climb the ranks, eventually reaching the pinnacle of his military career as a lieutenant general on **February 25, 2021**.
Skinner’s early career was defined by his roles in tactical communications and space operations. He commanded the **27th Communications Squadron** from 2000 to 2002, where he honed his skills in managing critical communication infrastructures. This was followed by his leadership of the **614th Space Communications Squadron** from 2004 to 2005, a role that underscored his expertise in space-based communications—a domain that has become increasingly vital in modern warfare.
Rising Through the Ranks: A Career of Strategic Impact
Skinner’s career trajectory is a masterclass in strategic leadership. His roles were not confined to a single domain but spanned a broad spectrum of military operations. He served as the **director of Command, Control, Communications, and Cyber for U.S. Indo-Pacific Command**, a position that placed him at the heart of one of the most strategically important regions in the world. Here, he was responsible for ensuring seamless communication and cybersecurity across a vast and complex theater of operations.
His tenure as the **Deputy Commander of Air Force Space Command** further solidified his reputation as a leader who could navigate the complexities of space and cyber operations. In this role, Skinner was instrumental in shaping the Air Force’s approach to space-based assets, ensuring that the U.S. maintained its technological edge in an increasingly contested domain.
Commanding the Digital Frontier: Leading DISA and JFHQ-DoDIN
Perhaps the most defining chapter of Skinner’s career came when he was appointed as the **Director of the Defense Information Systems Agency (DISA)** and **Commander of Joint Force Headquarters-Department of Defense Information Network (JFHQ-DoDIN)**. From 2021 to 2024, Skinner led a team of approximately **19,000 personnel** spread across **42 countries**, tasked with modernizing and securing the Department of Defense’s global IT infrastructure.
In this role, Skinner was at the forefront of defending the **DoD Information Network (DoDIN)** against cyber threats. His leadership was crucial in enabling command and control for combat operations, ensuring that the U.S. military could operate effectively in an era where cyber warfare is as critical as traditional battlefield tactics. Under his command, DISA underwent significant restructuring to enhance network protection, aligning with the broader trends in cyber resilience and digital transformation within the DoD.
Awards and Accolades: Recognition of Excellence
Skinner’s contributions to the U.S. military have not gone unnoticed. His decorated career includes prestigious awards such as the **Master Cyberspace Operator Badge**, a symbol of his expertise in cyber operations. He has also been awarded the **Armed Forces Expeditionary Medal**, the **Iraq Campaign Medal**, and the **Nuclear Deterrence Operations Service Medal**, each reflecting his diverse contributions to global operations, combat missions, and national security.
One of the most notable recognitions of his impact is his **three-time Wash100 Award**, an honor that highlights his influence in the federal IT and cybersecurity sectors. This award is a testament to his ability to drive innovation and lead transformative initiatives in an ever-changing digital landscape.
Transition to the Private Sector: A New Chapter
After retiring from the military in 2024, Skinner did not step away from the world of cybersecurity and IT modernization. Instead, he transitioned to the private sector, bringing his wealth of experience to **Axonius Federal Systems**. Joining the company’s board, Skinner is now focused on expanding Axonius’ presence within the federal government. His role is pivotal in helping the company meet the growing demands for network visibility and threat defense in an era where cyber threats are becoming increasingly sophisticated.
Skinner’s move to Axonius is a strategic one. The company specializes in cybersecurity asset management, providing organizations with the tools they need to gain visibility into their digital environments. With Skinner’s expertise, Axonius is well-positioned to support federal agencies in their efforts to modernize IT infrastructures and defend against cyber threats.
The Legacy of a Cyber Pioneer
Robert J. Skinner’s career is a blueprint for leadership in the digital age. From his early days as a second lieutenant to his role as a three-star general commanding global cyber operations, Skinner has consistently demonstrated an ability to adapt, innovate, and lead. His contributions to the U.S. military have not only strengthened national security but have also set a standard for how cyber operations should be integrated into modern defense strategies.
As he continues his work in the private sector, Skinner’s influence is far from over. His insights and leadership will undoubtedly shape the future of cybersecurity, ensuring that both government and private entities are equipped to face the challenges of an increasingly digital world.
Stay Tuned for More
This is just the beginning of Robert J. Skinner’s story. In the next part of this article, we’ll delve deeper into his strategic initiatives at DISA, his vision for the future of cybersecurity, and the lessons that young leaders can learn from his remarkable career. Stay tuned for an in-depth exploration of how Skinner’s leadership continues to impact the world of cyber defense.
Strategic Initiatives and Transformational Leadership at DISA
A Vision for Modernization
When Robert J. Skinner took the helm of the **Defense Information Systems Agency (DISA)** in 2021, he inherited an organization at the crossroads of a digital revolution. The DoD’s IT infrastructure, while robust, was facing unprecedented challenges—ranging from escalating cyber threats to the need for rapid digital transformation. Skinner’s leadership was defined by a clear vision: to modernize the DoD’s global IT network while ensuring it remained secure, resilient, and capable of supporting combat operations in real time.
One of Skinner’s first major initiatives was to **restructure DISA’s operations** to enhance network protection. This wasn’t just about bolting on new cybersecurity tools; it was about fundamentally rethinking how the DoD approached digital defense. Under his command, DISA adopted a **zero-trust architecture**, a model that assumes no user or system is inherently trustworthy, regardless of whether they are inside or outside the network perimeter. This shift was critical in an era where insider threats and sophisticated cyber-attacks from nation-state actors were becoming the norm.
Skinner also championed the **adoption of cloud-based solutions** across the DoD. Recognizing that legacy systems were no longer sufficient to meet the demands of modern warfare, he pushed for the integration of commercial cloud technologies. This move not only improved the scalability and flexibility of the DoD’s IT infrastructure but also enabled faster deployment of critical applications and services to troops in the field. His efforts aligned with the broader **DoD Cloud Strategy**, which aims to leverage cloud computing to enhance mission effectiveness and operational efficiency.
Defending the DoD Information Network (DoDIN)
The **DoD Information Network (DoDIN)** is the backbone of the U.S. military’s global operations. It connects commanders, troops, and assets across the world, enabling real-time communication, intelligence sharing, and command and control. Protecting this network from cyber threats was one of Skinner’s top priorities, and his approach was both proactive and adaptive.
Under Skinner’s leadership, DISA implemented **advanced threat detection and response capabilities**. This included the deployment of **artificial intelligence (AI) and machine learning (ML) tools** to identify and neutralize cyber threats before they could cause significant damage. These technologies allowed DISA to analyze vast amounts of data in real time, detecting anomalies that might indicate a cyber-attack. By automating threat detection, Skinner’s team could respond to incidents faster and more effectively, reducing the window of vulnerability.
Skinner also recognized the importance of **cyber hygiene**—the practice of maintaining basic security measures to prevent attacks. He launched initiatives to ensure that all personnel within the DoD adhered to best practices, such as regular software updates, strong password policies, and multi-factor authentication. While these measures might seem basic, they are often the first line of defense against cyber threats. By fostering a culture of cyber awareness, Skinner helped to minimize the risk of human error, which is a leading cause of security breaches.
Global Operations and the Human Element
One of the most impressive aspects of Skinner’s tenure at DISA was his ability to lead a **global workforce of approximately 19,000 personnel** spread across **42 countries**. Managing such a vast and diverse team required not only technical expertise but also exceptional leadership and communication skills. Skinner’s approach was rooted in **empowerment and collaboration**. He believed in giving his teams the tools, training, and autonomy they needed to succeed, while also fostering a sense of unity and shared purpose.
Skinner’s leadership style was particularly evident in his handling of **crisis situations**. Whether responding to a cyber-attack or ensuring uninterrupted communication during a military operation, he remained calm, decisive, and focused. His ability to maintain clarity under pressure was a key factor in DISA’s success during his tenure. He also placed a strong emphasis on **continuous learning and development**, ensuring that his teams were always equipped with the latest skills and knowledge to tackle emerging threats.
Bridging the Gap Between Military and Industry
Throughout his career, Skinner has been a strong advocate for **public-private partnerships**. He understands that the challenges of cybersecurity and IT modernization are too complex for any single entity to solve alone. By collaborating with industry leaders, the DoD can leverage cutting-edge technologies and best practices to stay ahead of adversaries.
During his time at DISA, Skinner worked closely with **tech giants, cybersecurity firms, and startups** to integrate innovative solutions into the DoD’s IT infrastructure. This included partnerships with companies specializing in **AI, cloud computing, and cybersecurity**, all of which played a crucial role in modernizing the DoD’s digital capabilities. Skinner’s ability to bridge the gap between the military and the private sector has been a defining feature of his career, and it’s a trend he continues to champion in his post-retirement role at Axonius.
The Transition to Axonius: A New Mission in the Private Sector
Why Axonius?
After retiring from the military in 2024, Skinner could have chosen any number of paths. However, his decision to join **Axonius Federal Systems** was a strategic one. Axonius is a leader in **cybersecurity asset management**, providing organizations with the visibility they need to understand and secure their digital environments. For Skinner, this was a natural fit. His decades of experience in cyber operations and IT modernization made him uniquely qualified to help Axonius expand its footprint within the federal government.
Axonius’ platform is designed to give organizations a **comprehensive view of all their assets**, including devices, users, and applications. This visibility is critical for identifying vulnerabilities, detecting threats, and ensuring compliance with security policies. In the federal sector, where cyber threats are a constant concern, Axonius’ solutions are in high demand. Skinner’s role on the board is to help the company navigate the complexities of the federal market, ensuring that its technologies are tailored to meet the unique needs of government agencies.
Expanding Federal Presence
Skinner’s appointment to the Axonius Federal Systems board is more than just a ceremonial role. He is actively involved in shaping the company’s strategy for engaging with federal clients. His deep understanding of the **DoD’s cybersecurity challenges** and his extensive network within the government make him an invaluable asset to Axonius.
One of Skinner’s key priorities is to **educate federal agencies** on the importance of asset visibility. Many organizations struggle with **shadow IT**—the use of unauthorized devices and applications that can introduce significant security risks. Axonius’ platform helps agencies identify and manage these hidden assets, reducing the attack surface and improving overall security posture. Skinner’s mission is to ensure that federal leaders understand the value of this approach and adopt it as part of their broader cybersecurity strategy.
A Focus on Cyber Resilience
In his new role, Skinner is also advocating for a **shift in how the federal government approaches cybersecurity**. Rather than simply reacting to threats, he believes agencies should focus on **building cyber resilience**—the ability to withstand, respond to, and recover from cyber-attacks. This requires a combination of **advanced technologies, robust policies, and a skilled workforce**.
Skinner’s vision aligns with the broader trends in federal cybersecurity. The **U.S. Cybersecurity and Infrastructure Security Agency (CISA)** has been pushing for a **zero-trust architecture** and **continuous monitoring** as part of its efforts to modernize federal IT systems. Axonius’ platform is a key enabler of these initiatives, providing the visibility and control needed to implement zero-trust principles effectively.
Lessons in Leadership: What Young Professionals Can Learn from Skinner
Adaptability in a Rapidly Changing Landscape
One of the most important lessons from Skinner’s career is the value of **adaptability**. The field of cybersecurity is constantly evolving, with new threats and technologies emerging at a rapid pace. Skinner’s ability to stay ahead of these changes—whether by adopting cloud computing, AI, or zero-trust architectures—has been a key factor in his success.
For young professionals entering the cybersecurity field, adaptability is non-negotiable. The skills and tools that are relevant today may be obsolete in a few years. Skinner’s career is a reminder that **continuous learning** is essential. Whether through formal education, certifications, or hands-on experience, staying updated with the latest trends is critical for long-term success.
The Importance of Collaboration
Another key takeaway from Skinner’s leadership is the power of **collaboration**. Cybersecurity is not a solo endeavor; it requires teamwork, both within organizations and across industries. Skinner’s ability to bring together military personnel, government agencies, and private-sector partners has been instrumental in his achievements.
Young professionals should seek out opportunities to **build networks** and **foster partnerships**. Whether it’s working with colleagues from different departments, engaging with industry experts, or participating in professional organizations, collaboration can open doors to new ideas and solutions. Skinner’s career demonstrates that the best outcomes often come from **diverse perspectives working toward a common goal**.
Leading with Integrity and Purpose
Finally, Skinner’s career is a testament to the importance of **leading with integrity and purpose**. Throughout his three decades of service, he has remained committed to the mission of protecting national security and enabling the success of the U.S. military. His leadership was never about personal glory but about **serving something greater than himself**.
For young leaders, this is a powerful lesson. True leadership is not about titles or authority; it’s about **making a positive impact** and **inspiring others to do the same**. Whether in the military, the private sector, or any other field, leading with integrity and purpose will always set you apart.
Looking Ahead: The Future of Cybersecurity and Skinner’s Continued Influence
As we look to the future, it’s clear that Robert J. Skinner’s influence on cybersecurity is far from over. His work at Axonius is just the latest chapter in a career defined by innovation, leadership, and a relentless commitment to excellence. The challenges of cybersecurity will only grow more complex, but with leaders like Skinner at the helm, the U.S. is well-positioned to meet them head-on.
In the final part of this article, we’ll explore Skinner’s vision for the future of cybersecurity, the emerging threats that keep him up at night, and the advice he has for the next generation of cyber leaders. Stay tuned for an in-depth look at how Skinner’s legacy continues to shape the digital battlefield.
The Future of Cybersecurity: Skinner’s Vision and Emerging Threats
A Shifting Cyber Landscape
The cybersecurity landscape is evolving at an unprecedented pace, and Robert J. Skinner is keenly aware of the challenges that lie ahead. In his view, the future of cybersecurity will be shaped by **three major trends* the rise of **quantum computing**, the increasing sophistication of **nation-state cyber threats**, and the growing importance of **AI-driven defense mechanisms**.
Skinner has often spoken about the potential impact of **quantum computing** on cybersecurity. While quantum computers hold the promise of revolutionary advancements in fields like medicine and logistics, they also pose a significant threat to current encryption standards. "The day quantum computers can break traditional encryption is not a question of *if* but *when*," Skinner has noted. His work at Axonius and his engagements with federal agencies emphasize the need for **post-quantum cryptography**—a new generation of encryption algorithms designed to resist attacks from quantum computers. For Skinner, preparing for this shift is not just a technical challenge but a strategic imperative.
Nation-State Threats and the New Battlefield
The threat posed by **nation-state actors** is another area of deep concern for Skinner. Over his career, he witnessed firsthand how cyber warfare has become a central component of geopolitical strategy. Countries like **Russia, China, Iran, and North Korea** have developed sophisticated cyber capabilities, using them to conduct espionage, disrupt critical infrastructure, and influence global events.
Skinner’s time at **U.S. Indo-Pacific Command** gave him a front-row seat to the cyber operations of adversarial nations. He has repeatedly stressed that cyber threats are no longer confined to the digital realm—they have **real-world consequences**. A cyber-attack on a power grid, for instance, can plunge entire cities into darkness, while an attack on financial systems can destabilize economies. His approach to countering these threats involves a combination of **proactive defense, international cooperation, and robust deterrence strategies**.
At Axonius, Skinner is advocating for **greater visibility and control** over federal networks to detect and mitigate these threats. "You can’t defend what you can’t see," he often says. By providing agencies with a comprehensive view of their digital assets, Axonius’ platform helps identify vulnerabilities before they can be exploited by adversaries.
AI and Automation: The Double-Edged Sword
Artificial intelligence is another double-edged sword in the cybersecurity arsenal. On one hand, **AI-driven tools** can enhance threat detection, automate responses, and analyze vast amounts of data in real time. On the other hand, adversaries are also leveraging AI to develop more sophisticated attacks, such as **deepfake phishing scams** and **automated hacking tools**.
Skinner believes that the future of cybersecurity will be defined by an **AI arms race**. "The side that can harness AI most effectively will have the upper hand," he has remarked. During his tenure at DISA, he championed the integration of AI into the DoD’s cyber defense strategies. Now, at Axonius, he is working to ensure that federal agencies have the tools they need to stay ahead in this race.
One of the key challenges is **balancing automation with human oversight**. While AI can process data faster than any human, it lacks the nuanced understanding and judgment that experienced cybersecurity professionals bring to the table. Skinner’s approach is to use AI as a **force multiplier**—augmenting human capabilities rather than replacing them. This means training the next generation of cyber defenders to work alongside AI tools, leveraging their strengths while mitigating their limitations.
Skinner’s Advice for the Next Generation of Cyber Leaders
Embrace Lifelong Learning
For young professionals entering the field of cybersecurity, Skinner’s first piece of advice is to **embrace lifelong learning**. "The moment you think you know everything is the moment you become obsolete," he warns. The cybersecurity landscape is constantly evolving, and staying relevant requires a commitment to continuous education.
Skinner recommends that young professionals **pursue certifications** in areas like **ethical hacking, cloud security, and AI-driven cyber defense**. He also encourages them to stay engaged with industry trends by attending conferences, participating in **capture-the-flag (CTF) competitions**, and joining professional organizations like **ISC²** and **ISACA**. "The best cybersecurity professionals are those who never stop learning," he says.
Develop Soft Skills Alongside Technical Expertise
While technical skills are essential, Skinner emphasizes that **soft skills** are equally important. "Cybersecurity is not just about writing code or configuring firewalls—it’s about communication, collaboration, and leadership," he explains. Effective cybersecurity professionals must be able to **articulate risks to non-technical stakeholders**, work in cross-functional teams, and lead initiatives that require buy-in from across an organization.
Skinner’s own career is a testament to the power of soft skills. His ability to **bridge the gap between military and civilian sectors**, as well as between government and industry, has been a key factor in his success. He advises young professionals to **hone their communication skills**, learn to **manage teams effectively**, and develop a **strategic mindset** that aligns cybersecurity with broader organizational goals.
Think Like an Adversary
One of the most valuable lessons Skinner has learned over his career is the importance of **thinking like an adversary**. "To defend a network, you have to understand how an attacker would try to breach it," he says. This mindset is at the core of **red teaming**—a practice where cybersecurity professionals simulate attacks to identify vulnerabilities.
Skinner encourages young cyber defenders to **adopt an offensive mindset**. This means staying updated on the latest **hacking techniques**, understanding the **tactics, techniques, and procedures (TTPs)** used by adversaries, and constantly challenging their own assumptions about security. "The best defense is a proactive one," he notes. By anticipating how attackers might exploit weaknesses, cybersecurity teams can stay one step ahead.
Build a Strong Professional Network
Networking is another area where Skinner sees tremendous value. "Cybersecurity is a team sport," he often says. Building relationships with peers, mentors, and industry leaders can open doors to new opportunities, provide access to valuable resources, and offer support during challenging times.
Skinner’s own network has been instrumental in his career. From his early days in the Air Force to his current role at Axonius, he has relied on **mentors, colleagues, and industry partners** to navigate complex challenges. He advises young professionals to **attend industry events**, join online communities, and seek out mentorship opportunities. "The relationships you build today will shape your career tomorrow," he emphasizes.
The Legacy of a Cyber Pioneer
A Career Defined by Service and Innovation
Robert J. Skinner’s career is a remarkable journey of **service, leadership, and innovation**. From his early days as a second lieutenant to his role as a three-star general commanding global cyber operations, he has consistently pushed the boundaries of what is possible in cybersecurity. His contributions to the U.S. military have not only strengthened national security but have also set a standard for how cyber operations should be integrated into modern defense strategies.
Skinner’s impact extends beyond his military service. His transition to the private sector at Axonius is a testament to his commitment to **continuing the fight against cyber threats**, this time from a different vantage point. By leveraging his expertise to help federal agencies modernize their IT infrastructures, he is ensuring that the lessons he learned in the military continue to benefit the nation.
A Vision for the Future
Looking ahead, Skinner’s vision for the future of cybersecurity is one of **resilience, adaptability, and collaboration**. He believes that the challenges of tomorrow will require a **unified approach**, bringing together government, industry, and academia to develop innovative solutions. His work at Axonius is just one example of how public-private partnerships can drive progress in cybersecurity.
Skinner is also a strong advocate for **investing in the next generation of cyber leaders**. He believes that the future of cybersecurity depends on **mentorship, education, and opportunity**. By sharing his knowledge and experience, he is helping to shape a new generation of professionals who are equipped to tackle the challenges of an increasingly digital world.
Final Thoughts: The Man Behind the Uniform
Beyond the titles, awards, and accolades, Robert J. Skinner is a leader who has always put **mission and people first**. His career is a reminder that true leadership is not about personal achievement but about **serving others and making a difference**. Whether in the military or the private sector, Skinner’s dedication to protecting national security and advancing cybersecurity has left an indelible mark.
As we reflect on his career, one thing is clear: Robert J. Skinner’s influence on cybersecurity will be felt for decades to come. His story is not just one of **technical expertise** but of **vision, perseverance, and an unwavering commitment to excellence**. For young professionals entering the field, his journey serves as both an inspiration and a roadmap for success.
The End of an Era, the Beginning of a New Chapter
Robert J. Skinner’s retirement from the military may have marked the end of one chapter, but his work is far from over. As he continues to shape the future of cybersecurity at Axonius and beyond, his legacy serves as a guiding light for those who follow in his footsteps. The digital battlefield is evolving, but with leaders like Skinner at the helm, the future of cybersecurity is in capable hands.
For those who aspire to make their mark in this critical field, Skinner’s career offers a powerful lesson: **success is not just about technical skills or strategic vision—it’s about leadership, adaptability, and an unyielding commitment to the mission**. As the cyber landscape continues to change, the principles that have guided Skinner’s career will remain as relevant as ever.
In the words of Skinner himself: *"Cybersecurity is not just a job—it’s a calling. And it’s a calling that requires us to be at our best, every single day."* For Robert J. Skinner, that calling is far from over. And for the rest of us, his journey is a reminder of the impact one leader can have on the world.


Drakon: The First Legal and Accounting Canon in Athens
The ancient Greek phrase Drakwn-O-Prwtos-Logismikos-Kanona-Sthn-A8hna translates to "Draco: The First Accounting Canon in Athens." It refers to the revolutionary legal code established by the lawgiver Draco around 621 BCE. This was the earliest written constitution for Athens, marking a pivotal shift from unwritten aristocratic judgments to a codified public standard. The term kanón, meaning a rule or measuring rod, underscores its role as the foundational benchmark for justice, debt, and societal order.
The Historical Dawn of Codified Law in Athens
Before Draco's reforms, justice in Archaic Athens was administered orally by the aristocracy. This system was often arbitrary and fueled bloody feuds between powerful families. Draco's mandate was to establish a clear, publicly known set of rules to quell social unrest and provide stability. His code, inscribed on wooden tablets called axones displayed in the Agora, represented a seismic shift toward the rule of law.
The primary motivation was to standardize legal proceedings and penalties. By writing the laws down, Draco made them accessible, at least in principle, to a wider populace beyond the ruling elite. This act of codification itself was more revolutionary than the specific laws' content. It laid the indispensable groundwork for all subsequent Athenian legal development, including the more famous reforms of Solon.
Draco's code applied to an estimated 300,000 Athenians and was read aloud publicly each year, ensuring communal awareness of the legal "measuring rod" against which all were judged.
Decoding the "Kanón": From Measuring Rod to Legal Standard
The core concept within the phrase is kanón (κανών). Originally, this word referred to a literal reed or rod used for measurement. In Draco's context, it took on a profound metaphorical meaning: a fixed standard, principle, or boundary for human conduct. This linguistic evolution reflects the move from physical to societal measurement.
As a legal term, kanón established the "lines" that could not be crossed without consequence. This foundational idea of a legal canon later influenced Western thought profoundly. The concept evolved through history, later used in the New Testament to describe spheres of authority and by early church fathers to define the official canon of scripture.
The Severe Content of Draco's Legal Code
Draco's laws were comprehensive for their time, covering critical areas of civil and criminal life. The code addressed homicide, assault, property theft, and the pressing issue of debt slavery. Its primary aim was to replace private vengeance with public justice, thereby reducing clan-based violence. However, its legacy is overwhelmingly defined by its extreme severity.
Penalties were notoriously harsh and famously lacked gradation. The laws made little distinction between major crimes and minor offenses in terms of punishment. This blanket approach to justice is what gave the English language the enduring adjective "draconian," synonymous with excessively harsh and severe measures.
Key areas covered by the code included:
- Homicide Laws: These were the most sophisticated and long-lasting parts of Draco's code. They distinguished between premeditated murder, involuntary homicide, and justifiable killing, each with specific legal procedures.
- Property and Debt: Laws addressed theft and the practice of debt slavery, where defaulting debtors could be enslaved by creditors—a major source of social tension.
- Judicial Procedure: The code formally outlined legal processes, transferring judgment from private individuals to public officials and courts.
The Infamous "Draconian" Penalties
Historical accounts suggest a staggering proportion of Draco's laws mandated capital punishment. It is estimated that roughly 80% of prescribed penalties involved death or permanent exile. Ancient sources famously claimed that Draco justified this severity because even minor offenses deserved death, and he had no greater penalty for major crimes.
For example, the penalty for stealing a cabbage could be the same as for murder. This lack of proportionality was the code's greatest flaw. While it successfully established the principle that law was supreme, its brutal equity undermined its fairness. The severity was likely intended to deter crime absolutely in a turbulent society, but it ultimately proved unsustainable.
Only an estimated 5-10% of Draco's original laws survive today, primarily through fragments quoted by later orators like Demosthenes, who referenced them in 4th-century BCE legal speeches.
Modern Rediscovery and Digital Reconstruction
The 21st century has seen a renaissance in the study of Draco's code through digital humanities. With no major archaeological discoveries of the original axones in recent decades, scholars have turned to technology to reconstruct and analyze the surviving text. Projects spanning 2023 to 2025 have leveraged new tools to deepen our understanding.
Major digital libraries, including the Perseus Digital Library, have implemented updates using AI and computational linguistics. These tools help transcribe, translate, and cross-reference the scant fragments that remain. This digital revival allows for a more nuanced analysis, connecting Draco's laws to broader patterns in ancient Mediterranean legal history.
2024-2025 Academic Trends and Debates
Current scholarly discourse, reflected in journals like Classical Quarterly, is revisiting Draco's complex legacy. The debate moves beyond simply labeling him as harsh. Modern analysis examines his role in the democratization of law, asking how a severe code could also be a foundational step toward equality before the law.
Researchers are increasingly taking a comparative approach. They analyze parallels between Draco's code and other ancient legal systems, such as the Code of Hammurabi. Furthermore, 2024 studies utilize computational models to hypothesize the content of lost statutes based on the socio-economic conditions of 7th-century BCE Athens.
The cultural impact remains significant. In 2025, museums in Athens featured exhibitions on the origins of democracy, prominently highlighting Draco's code as the starting point. These exhibitions frame the ancient laws within contemporary global discussions about the rule of law, justice, and social order.
Draco's Homicide Laws: The Enduring Legal Legacy
While most of Draco's code was repealed, his legislation concerning homicide proved to be its most sophisticated and lasting contribution. These laws represented a significant advancement in legal thought by introducing the critical concept of intent. For the first time in Athenian law, a formal distinction was made between different types of killing, each carrying its own specific legal consequence and procedure.
The code categorized homicide into several types, including premeditated murder, involuntary manslaughter, and justifiable homicide. This nuanced approach prevented the cyclical blood feuds that had previously plagued Athenian society. By establishing a public legal process for adjudicating murders, Draco's laws transferred the right of retribution from the victim's family to the state. This was a monumental step toward a more orderly and centralized judicial system.
The Legal Machinery for Murder Cases
The procedures outlined by Draco were elaborate and designed to ensure a measured response. For a charge of intentional murder, the case was brought before the Areopagus Council, a venerable body of elders that met on the Hill of Ares. This council served as the supreme court for the most serious crimes, reflecting the gravity of taking a life.
In cases of involuntary homicide, the penalty was typically exile, but without the confiscation of the perpetrator's property. This distinction prevented the complete ruin of a family due to an accidental death. The law even provided a mechanism for pardon if the victim's family agreed, offering a path to reconciliation and an end to the feud.
Draco's homicide laws were so well-regarded for their fairness and precision that Solon intentionally preserved them intact during his extensive legal reforms in 594 BCE, a testament to their foundational quality.
The Socio-Economic Context of 7th Century BCE Athens
To fully understand Draco's code, one must examine the volatile social climate that necessitated it. Athens in the 7th century BCE was characterized by deep social stratification and economic disparity. A small aristocracy, the Eupatridae, held most of the political power and wealth, while the majority of the population, including small farmers and artisans, struggled under the weight of debt.
The prevailing system of debt was particularly oppressive. Farmers who borrowed seed or money from wealthy nobles often used their own freedom as collateral. Widespread crop failures or poor harvests could lead to debt slavery, where the debtor and their entire family could be enslaved by the creditor. This created a powder keg of social resentment that threatened to tear the city-state apart.
Key social groups in this period included:
- The Eupatridae (Aristocrats): Held hereditary political power and vast landed estates.
- The Georgoi (Farmers): Small-scale landowners who were vulnerable to debt and enslavement.
- The Demiurgoi (Artisans): Craftsmen and traders who had wealth but little political influence.
Draco's Response to the Debt Crisis
Draco's laws did address the issue of debt, though his solutions were characteristically severe. The code formalized the rules surrounding debt and property rights, which, in theory, offered some predictability. However, it did little to alleviate the underlying causes of the crisis. The laws upheld the rights of creditors, thereby legitimizing the system of debt slavery that was a primary source of unrest.
This failure to resolve the core economic grievances meant that while Draco's code provided a framework for public order, it did not bring about social justice. The tension between the wealthy few and the indebted many continued to simmer, setting the stage for the more radical economic reforms that Solon would later be forced to implement.
The Archaeological and Textual Evidence for Draco's Code
One of the greatest challenges in studying Draco's laws is their fragmentary survival. The original wooden axones on which the laws were inscribed have long since decayed. Our knowledge comes entirely from secondary sources, primarily later Greek writers who quoted the laws for their own purposes. No single, continuous text of the code exists today.
The most significant sources are the speeches of 4th-century BCE orators, such as Demosthenes and Aristotle's work, The Constitution of the Athenians. These authors quoted Draco's laws to make arguments about their own contemporary legal issues. Scholars have painstakingly pieced together these quotations to reconstruct approximately 21 identifiable fragments of the original code.
Despite its historical importance, the physical evidence is minimal. Scholars estimate that we have access to less than 10% of the original text of Draco's legislation, making full understanding of its scope a challenging task.
The Role of Axones and Kyrbeis
The physical form of the law was as innovative as its content. The laws were inscribed on a set of revolving wooden tablets or pillars known as axones (or sometimes kyrbeis). These were mounted on axles so that they could be rotated, allowing citizens to read the laws written on all sides. They were displayed prominently in a public space, likely the Agora, the civic heart of Athens.
This public display was a revolutionary act. It symbolized that the law was no longer the secret knowledge of the aristocracy but belonged to the entire citizen body. It made the legal kanón—the standard—visible and accessible, embodying the principle that ignorance of the law was no longer an excuse.
Draco in Comparative Legal History
Placing Draco's code in a wider historical context reveals its significance beyond Athens. It was part of a broader Mediterranean trend in the first millennium BCE toward the codification of law. The most famous predecessor was the Code of Hammurabi from Babylon, dating back to 1754 BCE, which was also inscribed on a public stele for all to see.
However, there are crucial differences. While Hammurabi's code was divinely sanctioned by the sun god Shamash, Draco's laws were a purely human creation, established by a mortal lawgiver. This secular foundation is a hallmark of the Greek approach to law and governance. Furthermore, Draco's focus was more narrowly on establishing clear, fixed penalties to curb social chaos.
Key points of comparison with other ancient codes:
- Code of Hammurabi (Babylon): Older and more comprehensive, based on the principle of "an eye for an eye," but also featured class-based justice where penalties varied by social status.
- Draco's Code (Athens): Noted for its uniform severity across social classes, applying the same harsh penalties to aristocrats and commoners alike, a form of brutal equality.
- Roman Twelve Tables (5th Century BCE): Later Roman code, also created to appease social unrest by making laws public and applicable to both patricians and plebeians.
The Uniqueness of Athenian Legal Innovation
What sets Draco apart is his role in a specific evolutionary path. His code was the first critical step in a process that would lead to Athenian democracy. By creating a written, public standard, he initiated the idea that the community, not a king or a small oligarchy, was the source of legal authority. This trajectory from Draco's severe code to Solon's reforms and eventually to the full democracy of the 5th century illustrates a unique experiment in self-governance.
Solon's Reforms and the Overthrow of Draconian Severity
The harshness of Draco's laws proved unsustainable in the long term. By 594 BCE, Athens was again on the brink of civil war due to unresolved economic grievances. Into this crisis stepped Solon, appointed as archon with broad powers to reform the state. His mission was to create a more equitable society and legal system, which necessitated the dismantling of the most severe aspects of Draco's code.
Solon famously enacted a sweeping set of reforms known as the Seisachtheia, or "shaking-off of burdens." This radical measure canceled all outstanding debts, freed those who had been enslaved for debt, and made it illegal to use a citizen's person as collateral for a loan. This directly tackled the economic oppression that Draco's laws had failed to resolve. Solon replaced Draco's rigid penalties with a system of tiered fines proportional to the crime and the offender's wealth.
What Solon Kept and What He Discarded
Solon's genius lay in his selective approach. He recognized the foundational value of Draco's homicide laws, which provided a clear and effective legal process for the most serious crime. Consequently, he preserved Draco's legislation on murder almost in its entirety. This decision underscores that the problem was not the concept of written law itself, but rather the excessive and ungraded punishments for other offenses.
For all other matters, Solon created a new, more humane legal code. He introduced the right of appeal to the popular court (heliaia), giving citizens a voice in the judicial process. This move away from absolute aristocratic control was a direct evolution from Draco's initial step of public codification, pushing Athens further toward democratic principles.
Solon’s reforms demonstrated that while Draco provided the essential framework of written law, it required a more compassionate and socially conscious application to achieve true justice and stability.
The Evolution of the Legal "Kanón" Through History
The concept of kanón, so central to Draco's achievement, did not remain static. Its meaning expanded and evolved significantly over the centuries. From a literal measuring rod and a legal standard, it grew into a foundational idea in religion, art, and intellectual life. This evolution tracks the journey of Greek thought from the concrete to the abstract.
In the Classical and Hellenistic periods, kanón came to denote a standard of excellence or a model to be imitated. The famous sculptor Polykleitos wrote a treatise called "The Kanon," which defined the ideal mathematical proportions for the perfect human form. This illustrates how the term transitioned from governing human action to defining aesthetic and philosophical ideals.
The key evolutions of the term include:
- Legal Standard (Draco): A fixed, public rule for conduct and penalty.
- Artistic Principle (Classical Greece): A model of perfection and proportion in sculpture and architecture.
- Theological Canon (Early Christianity): The officially accepted list of books in the Bible, the "rule" of faith.
- Academic Canon (Modern Era): The body of literature, art, and music considered most important and worthy of study.
The Theological Adoption of the Kanón
The most significant transformation occurred in early Christian theology. Church fathers adopted the Greek term to describe the rule of faith and, most famously, the "canon" of Scripture—the definitive list of books recognized as divinely inspired. The Apostle Paul himself used the term in 2 Corinthians 10:13-16 to describe the "measure" or "sphere" of ministry God had assigned to him.
This theological usage directly parallels Draco's original intent: to establish a clear, authoritative boundary. For Draco, it was the boundary of lawful behavior; for the Church, it was the boundary of orthodox belief and sacred text. This lineage shows the profound and enduring influence of the legal concept born in 7th-century Athens.
The Modern Legacy: From Ancient Athens to Today
The legacy of Draco's code is a paradox. On one hand, it is synonymous with cruelty, giving us the word "draconian." On the other, it represents the groundbreaking idea that a society should be governed by public, written laws rather than the whims of powerful individuals. This dual legacy continues to resonate in modern legal and political discourse.
Today, "draconian" is routinely used by journalists, activists, and politicians to criticize laws perceived as excessively harsh, particularly those involving mandatory minimum sentences, severe censorship, or stringent security measures. The term serves as a powerful rhetorical tool, instantly evoking a warning against the dangers of legal severity devoid of mercy or proportionality.
The enduring power of the term "draconian" demonstrates how an ancient lawgiver's name has become a universal benchmark for judicial harshness over 2,600 years later.
Draco in Contemporary Culture and Education
Draco's story remains a staple of educational curricula worldwide when teaching the origins of Western law. It provides a clear and dramatic starting point for discussions about the rule of law, justice, and the balance between order and freedom. In popular culture, references to Draco or draconian measures appear in literature, film, and television, often to illustrate tyrannical governance.
Modern digital projects ensure this legacy continues. Virtual reality reconstructions of ancient Athens allow users to "stand" in the Agora and view recreations of the axones. These immersive experiences, combined with online scholarly databases, make the study of Draco's laws more accessible than ever, bridging the gap between ancient history and contemporary technology.
Conclusion: The Foundational Paradox of Draco's Code
In conclusion, the significance of Drakwn-O-Prwtos-Logismikos-Kanona-Sthn-A8hna cannot be overstated. Draco's code represents a foundational moment in human history, the moment a society decided to write down its rules for all to see. It established the critical principle that law should be a public standard, a kanón, applied equally to all citizens. This was its revolutionary and enduring contribution.
However, the code is also a cautionary tale. Its severe, undifferentiated penalties highlight the danger of pursuing order without justice. The fact that Solon had to repeal most of it just a generation later proves that a legal system must be rooted in fairness and social reality to be sustainable. The code's greatest strength—its firm establishment of written law—was also its greatest weakness, as it was a law without nuance.
The key takeaways from Draco's legacy are clear:
- Written Law is foundational to a stable and predictable society.
- Proportionality in justice is essential for long-term social harmony.
- Legal evolution is necessary, as laws must adapt to changing social and economic conditions.
- The concept of a public standard (kanón) for behavior has influenced Western thought for millennia.
Draco's laws, therefore, stand as a monumental first step. They were flawed, harsh, and ultimately inadequate for creating a just society. Yet, they ignited a process of legal development that would lead, through Solon, Cleisthenes, and Pericles, to the birth of democracy. The story of Draco is the story of beginning—a difficult, severe, but essential beginning on the long road to the rule of law.
Understanding Hash Functions: A Comprehensive Guide
The world of cryptography and data security is as ever-evolving as it is crucial. Among the key technologies used in these fields is the hash function. This article delves into the core concepts, mechanics, and applications of hash functions, offering a comprehensive overview for individuals seeking to understand this foundational element of modern cryptography.
The Essence of a Hash Function
A hash function is a mathematical function that takes an input (often referred to as the "message" or "data") and produces a fixed-length output. This output is typically a string of characters, known as the hash value or digest. Regardless of the size of the input, a hash function will always produce an output of the same size, making it an efficient method for verifying data integrity and security.
Key Characteristics of a Good Hash Function
There are several critical characteristics that make a hash function suitable for its intended purposes. To function effectively, a hash function must:
- Deterministic: For a given input, a hash function must always produce the same output. This means that if the same data is hashed multiple times, it should yield the same result.
- Fixed Output Size: The output must be of a constant length, regardless of the input size. This ensures that the hash value is concise and manageable for various applications.
- Collision Resistance: A good hash function should be designed to make it extremely difficult for two different inputs to produce the same output. This property is crucial for maintaining security and verifying the authenticity of data.
- Average-Case Time Complexity: The function should operate within a reasonable time frame, even for large inputs. This is particularly important in real-world applications where performance is a concern.
Types of Hash Functions
Several types of hash functions are in widespread use today. Each type serves specific purposes and has unique features.
MD5 (Message-Digest Algorithm 5)
MD5 was one of the first widely accepted hash functions, developed by Ronald L. Rivest. It generates a 128-bit hash value, typically represented as a 32-character hexadecimal number. Despite its popularity, MD5 is no longer considered secure due to the possibility of collision attacks.
SHA (Secure Hash Algorithms)
The Secure Hash Algorithms (SHA) family of hash functions were developed by the National Institute of Standards and Technology (NIST) and are designed to be more secure than MD5. SHA-256, for instance, generates a 256-bit hash, while SHA-3 (Keccak) is designed to offer improved security features.
SHA-1, SHA-2, and SHA-3
- SHA-1: Generates a 160-bit hash and was widely used until its security issues were publicly known. It is now considered less secure and is deprecated in many applications.
- SHA-2: This family comprises several variants (SHA-256, SHA-384, SHA-512, etc.), which generate hash values of different lengths. SHA-256, in particular, is widely used for its balance between security and performance.
- SHA-3: This is an entirely new approach, offering enhanced security features and improved resistance to collision attacks. SHA-3 is based on the principles of the Keccak algorithm.
The Role of Hash Functions in Data Security
Hash functions play a critical role in various aspects of data security and integrity. Here are some of the key applications:
Data Integrity
One of the most common uses of hash functions is to ensure the integrity of files and data. When a file is stored, its hash value is calculated and stored alongside the file. When the file is accessed again, its hash value is recalculated and compared with the stored hash value. If any changes have occurred, the hashes will not match, indicating that the data has been tampered with.
Password Hashing
Passwords are particularly sensitive data. Rather than storing passwords in plaintext, many systems use hash functions to store the hash of the password instead. When a user logs in, their input is hashed and compared with the stored hash. This not only enhances security but also protects against unauthorized access even if the password file is stolen.
Digital Signatures and Blockchain
Digital signatures use hash functions to ensure the authenticity and integrity of electronic documents. They are also crucial in the context of blockchain, where hash functions are used to link blocks, ensuring that any changes to a block are detected and the entire chain is compromised.
Hash Function Security Risks and Mitigations
While hash functions are powerful tools, they are not without their vulnerabilities. Several security risks associated with hash functions include:
Collision Attacks
A collision occurs when two different inputs produce the same hash value. While a good hash function minimizes the risk of collisions, the mathematical nature of hash functions means that they are not entirely collision-resistant. To mitigate this risk, developers often use techniques such as salting and multi-hashing.
Preimage Attacks
A preimage attack involves finding an input that produces a specific hash value. While hash functions are designed to be one-way and computationally infeasible to reverse, the possibility of preimage attacks remains a concern. This risk is often mitigated by using stronger and more secure hash functions.
Second Preimage Attacks
A second preimage attack involves finding a different input that produces the same hash value as a given input. This can be a significant security risk, especially in the context of file integrity. To protect against second preimage attacks, developers often use more secure hash functions and additional security practices.
Conclusion
Hash functions are fundamental tools in the realm of cryptography and data security. They provide a simple yet powerful method for ensuring data integrity and protecting sensitive information. Understanding the mechanics, applications, and security risks associated with hash functions is crucial for anyone working in data security and related fields.
In the next part of this article, we will delve deeper into the technical aspects of hash functions, exploring their implementation and the role they play in various cryptographic protocols. Stay tuned for more insights into this fascinating topic!
Techical Aspects of Hash Functions
The technical aspects of hash functions encompass both the theoretical underpinnings and practical implementation details. Understanding these aspects can provide valuable insights into how these tools work and why they remain essential in modern data security.
The Mathematical Foundations
At their core, hash functions rely on complex mathematical operations to produce consistent outputs. For instance, a popular type of hash function, Secure Hash Algorithm (SHA), operates through a series of bitwise operations, modular arithmetic, and logical functions.
SHA-256, for example, is a widely used hash function that processes data in 512-bit blocks and produces a 256-bit hash. The algorithm involves a sequence of rounds, each consisting of a combination of bitwise operations, logical functions, and modular additions. These operations ensure that even a small change in the input results in a significantly different output, a characteristic known as the avalanche effect.
The process begins with initializing a set of constants and the hash value itself. It then processes the message in successive blocks, applying a series of bitwise operations and modular arithmetic. The final round produces the hash value. The complexity and precision of these operations contribute to the security and robustness of the hash algorithm.
Implementation Details
Implementing a hash function requires careful consideration of multiple factors, including memory management, performance optimization, and security enhancements. Developers often use optimized libraries and frameworks to ensure that hash functions run efficiently.
Memory Management: Efficient memory usage is crucial for performance. Hash functions must handle varying input sizes gracefully and avoid unnecessary memory allocations. Techniques such as just-in-time (JIT) compilation and buffer pooling can enhance performance and reduce memory overhead.
Performance Optimization: Hash functions need to execute quickly, especially in high-throughput environments. Optimizations such as parallel processing, pipeline architecture, and vectorized operations can significantly improve performance. Additionally, using specialized hardware, such as GPUs and SIMD (Single Instruction Multiple Data) instructions, can further boost efficiency.
Security Enhancements: Beyond the basic hashing algorithms, developers employ additional measures to fortify hash functions. Techniques like salting, multi-hashing, and rate limiting help protect against common attacks.
Salting
Salting refers to adding a random value (salt) to the data before applying the hash function. This helps prevent preimage attacks by making each salted hash unique. Even if an attacker manages to find a hash, they would need to know the corresponding salt to reproduce the original data. Salting significantly increases the difficulty of brute-force attacks.
Multi-Hashing
Multi-hashing involves applying two or more hash functions to the same piece of data. This multi-step process further enhances security by increasing the computational effort required to crack the hash. Techniques like PBKDF2 (Password-Based Key Derivation Function 2) combine multiple rounds of hashing to generate a final hash value.
Rate Limiting
Rate limiting is a technique used to slow down or restrict the number of hash computations that can be performed within a given time frame. This measure is particularly useful in scenarios where password hashing is involved. By limiting the rate at which a hash function can operate, attackers are forced to spend more time and computational resources, thus deterring brute-force attacks.
Application Scenarios
Hash functions find application across a wide range of domains, from software development to cybersecurity. Here are some specific scenarios where hash functions are utilized:
File Verification
When downloading software or firmware updates, users often verify the integrity of the files using checksums or hashes. This check ensures that the downloaded file matches the expected value, preventing accidental corruption or malicious tampering.
For example, when a user downloads an ISO image for a Linux distribution, they might compare the hash value of the downloaded file with a pre-provided hash value from the official repository. Any discrepancy would indicate that the file is compromised or corrupted.
Password Storage
Storing plaintext passwords is highly insecure. Instead, web applications and database systems use hash functions to store a secure representation of passwords. When a user attempts to log in, their password is hashed and compared with the stored hash value.
This method ensures that even if the password database is compromised, the actual passwords remain secured. Additionally, using a salt alongside the hash function adds another layer of security by making it more difficult to crack individual passwords.
Cryptographic Protocols
Many cryptographic protocols utilize hash functions to ensure data integrity and secure communication. For instance, Secure Sockets Layer (SSL) and Transport Layer Security (TLS) implementations often use hash functions to verify the integrity of the transmitted data.
In blockchain technology, hash functions are essential for maintaining the integrity and security of blockchain networks. Each block in the blockchain contains a hash of the previous block, creating an immutable chain of blocks. Any alteration in a single block would invalidate all subsequent blocks, thanks to the hash linkage.
Distributed Systems
Hash functions play a critical role in distributed systems, particularly in distributed hash tables (DHTs). DHTs use hash functions to distribute key-value pairs across a network of nodes, ensuring efficient data lookup and storage.
DHTs employ a consistent hashing mechanism, where keys are mapped to nodes based on their hash values. This ensures that even if nodes join or leave the network, the overall structure remains stable and data can be efficiently retrieved.
Challenges and Future Trends
Despite their utility, hash functions face several challenges and ongoing research aims to address these issues:
Quantum Computing Threats
The rapid development of quantum computing poses a significant threat to traditional hash functions. Quantum computers could potentially perform certain tasks, such as solving discrete logarithm problems, much faster than classical computers. As a result, efforts are underway to develop post-quantum cryptographic algorithms that are resistant to quantum attacks.
Potential candidates for post-quantum cryptography include lattice-based cryptography, code-based cryptography, and multivariate polynomial cryptography. These methods are being explored as promising alternatives to current hash functions and cryptographic protocols.
Faster Parallel Processing
To enhance performance and cater to growing demands, there is continuous research into optimizing hash functions for parallel processing. This involves designing hash algorithms that can efficiently distribute tasks across multiple threads or processors. By doing so, hash functions can handle larger datasets and provide faster verification times.
Adaptive Hashing Techniques
To address evolving security threats, researchers are developing adaptive hash functions that can dynamically adjust parameters based on real-time security assessments. These adaptive techniques aim to provide more robust protection against emerging cyber threats and maintain the security of data over time.
Blockchain Security and Privacy
In the context of blockchain technology, hash functions continue to evolve. As blockchain systems grow in scale and complexity, there is a need for hash functions that can efficiently support large-scale data verification and consensus mechanisms.
Newer blockchain systems may integrate more advanced hash functions to enhance privacy and security. For instance, zero-knowledge proofs (ZKPs) leverage hash functions to enable secure data verification without revealing the underlying data. This technology promises to revolutionize privacy-preserving blockchain applications.
Conclusion
Hash functions are indispensable tools in modern data security, serving a wide array of practical needs from data integrity checks to password storage and beyond. Their intricate mathematical designs ensure that even small changes in input lead to vastly different outputs, providing the necessary security and reliability.
As technology continues to advance, the challenges surrounding hash functions remain dynamic. From addressing quantum computing threats to improving adaptability and speed, the future holds exciting developments that promise to enhance the security and efficiency of hash functions further.
Conclusion and Final Thoughts
In conclusion, hash functions play a vital role in modern cryptography and data security. They serve a multitude of purposes, from ensuring data integrity to securing passwords and enabling secure communication. Understanding the technical aspects and applications of hash functions is crucial for anyone involved in cybersecurity, software development, or any field that requires robust data protection.
While hash functions are remarkably effective, they are not without their challenges. The evolving landscape of cyber threats, particularly the threat posed by quantum computing, necessitates ongoing research and innovation in the field. Adaptive and faster processing techniques are continually being developed to address these new challenges.
The future of hash functions looks promising. With ongoing advancements in technology and security, we can expect more secure and efficient hash functions that can withstand the evolving threats. As blockchain and other distributed systems continue to grow, the role of hash functions in these environments will likely become even more critical.
To stay ahead in the field of data security, it is essential to stay informed about the latest developments in hash functions. By understanding their underlying principles and practical implications, we can better protect ourselves and contribute to a more secure digital world.
For further exploration, you might consider reviewing the latest research papers on hash functions, exploring the implementation details of specific algorithms, and keeping up with the latest breakthroughs in the field of cryptography.
Thank you for reading this comprehensive guide to hash functions. We hope this article has provided valuable insights into this foundational aspect of modern data security.

Quantum Cryptography: The Future of Secure Communication
Introduction to Quantum Cryptography
In an era where cybersecurity threats are becoming increasingly sophisticated, the demand for unbreakable encryption has never been greater. Traditional cryptographic methods, while effective, are vulnerable to advancements in computing power and clever hacking techniques. Enter quantum cryptography—a revolutionary approach to secure communication that leverages the principles of quantum mechanics to ensure unparalleled security. Unlike classical encryption, which relies on mathematical complexity, quantum cryptography is built on the inherent uncertainty and fundamental laws of physics, making it theoretically immune to hacking attempts.
The foundation of quantum cryptography lies in quantum key distribution (QKD), a method that allows two parties to generate a shared secret key that can be used to encrypt and decrypt messages. What makes QKD unique is its reliance on the behavior of quantum particles, such as photons, which cannot be measured or copied without disturbing their state. This means any attempt to eavesdrop on the communication will inevitably leave traces, alerting the legitimate parties to the intrusion.
The Principles Behind Quantum Cryptography
At the heart of quantum cryptography are two key principles of quantum mechanics: the Heisenberg Uncertainty Principle and quantum entanglement.
Heisenberg Uncertainty Principle
The Heisenberg Uncertainty Principle states that it is impossible to simultaneously know both the position and momentum of a quantum particle with absolute precision. In the context of quantum cryptography, this principle ensures that any attempt to measure a quantum system (such as a photon used in QKD) will inevitably alter its state. Suppose an eavesdropper tries to intercept the quantum key during transmission. In that case, their measurement will introduce detectable disturbances, revealing their presence and preserving the key's secrecy.
Quantum Entanglement
Quantum entanglement is a phenomenon where two or more particles become linked in such a way that the state of one particle immediately influences the state of the other, regardless of the distance separating them. This property allows for the creation of highly secure cryptographic systems. For example, if entangled photons are used in QKD, any attempt to intercept one photon will disrupt the entanglement, providing a clear indication of tampering.
How Quantum Key Distribution (QKD) Works
QKD is the cornerstone of quantum cryptography and involves the exchange of cryptographic keys between two parties—traditionally referred to as Alice (the sender) and Bob (the receiver)—using quantum communication channels. Here's a simplified breakdown of the process:
Step 1: Transmission of Quantum States
Alice begins by generating a sequence of photons, each in a random quantum state (polarization or phase). She sends these photons to Bob over a quantum channel, such as an optical fiber or even through free space.
Step 2: Measurement of Quantum States
Upon receiving the photons, Bob measures each one using a randomly chosen basis (e.g., rectilinear or diagonal for polarization-based systems). Due to the probabilistic nature of quantum mechanics, Bob’s measurements will only be accurate if he chooses the same basis as Alice did when preparing the photon.
Step 3: Sifting and Key Formation
After the transmission, Alice and Bob publicly compare their choice of measurement bases (but not the actual results). They discard any instances where Bob measured the photon in the wrong basis, retaining only the cases where their bases matched. These remaining results form the raw key.
Step 4: Error Checking and Privacy Amplification
To ensure the key's integrity, Alice and Bob perform error checking by comparing a subset of their raw key. If discrepancies exceed a certain threshold, it indicates potential eavesdropping, and the key is discarded. If no significant errors are found, they apply privacy amplification techniques to distill a final, secure key.
Advantages of Quantum Cryptography
Quantum cryptography offers several compelling advantages over traditional encryption methods:
Unconditional Security
Unlike classical encryption, which depends on computational hardness assumptions (e.g., factoring large primes), quantum cryptography provides security based on the laws of physics. This means it remains secure even against adversaries with unlimited computational power.
Detection of Eavesdropping
Any attempt to intercept quantum-encoded information will disturb the system, making it immediately detectable. This feature ensures that compromised communications can be identified and discarded before sensitive data is exposed.
Future-Proof Against Quantum Computers
With the advent of quantum computers, classical cryptographic algorithms like RSA and ECC are at risk of being broken. Quantum cryptography, particularly QKD, remains resistant to such threats, making it a future-proof solution.
Current Applications and Challenges
While quantum cryptography holds immense promise, its practical implementation faces several hurdles. Currently, QKD is being used in limited scenarios, such as securing government communications and financial transactions. However, challenges like high implementation costs, limited transmission distances, and the need for specialized infrastructure hinder widespread adoption.
Despite these obstacles, research and development in quantum cryptography are advancing rapidly. Innovations in satellite-based QKD and integrated photonics are paving the way for more accessible and scalable solutions. As the technology matures, quantum cryptography could become a standard for securing critical communications in the near future.
Stay tuned for the next part of this article, where we will delve deeper into real-world implementations of quantum cryptography, its limitations, and the ongoing advancements in this groundbreaking field.
Real-World Implementations of Quantum Cryptography
The theoretical promise of quantum cryptography has begun translating into practical applications, albeit in niche and high-security environments. Governments, financial institutions, and research organizations are leading the charge in deploying quantum-secure communication networks, recognizing the urgent need for protection against both current and future cyber threats.
Government and Military Use Cases
National security agencies were among the first to recognize the potential of quantum cryptography. Countries like China, the United States, and Switzerland have implemented QKD-based secure communication networks to safeguard sensitive governmental and military data. In 2017, China’s Quantum Experiments at Space Scale (QUESS) satellite, also known as Micius, successfully demonstrated intercontinental QKD between Beijing and Vienna, marking a milestone in global quantum-secured communication.
Similarly, the U.S. government has invested in quantum-resistant encryption initiatives through collaborations involving the National Institute of Standards and Technology (NIST) and Defense Advanced Research Projects Agency (DARPA). These efforts aim to transition classified communications to quantum-safe protocols before large-scale quantum computers become a reality.
Financial Sector Adoption
Banks and financial enterprises handle vast amounts of sensitive data daily, making them prime targets for cyberattacks. Forward-thinking institutions like JPMorgan Chase and the European Central Bank have begun experimenting with QKD to protect high-frequency trading systems, interbank communications, and customer transactions.
In 2020, the Tokyo Quantum Secure Communication Network, a collaboration between Toshiba and major Japanese financial firms, established a quantum-secured link between data centers, ensuring tamper-proof financial transactions. Such implementations underscore the growing confidence in quantum cryptography as a viable defense against economic espionage and fraud.
Technical Limitations and Challenges
Despite its groundbreaking advantages, quantum cryptography is not without hurdles. Researchers and engineers must overcome several technical barriers before QKD can achieve mainstream adoption.
Distance Constraints
One of the biggest challenges in QKD is signal loss over long distances. Photons used in quantum communication degrade when traveling through optical fibers or free space, limiting the effective range of current systems. While terrestrial QKD networks rarely exceed 300 kilometers, researchers are exploring quantum repeaters and satellite relays to extend reach. China’s Micius satellite has achieved intercontinental key distribution, but ground-based infrastructure remains constrained by physical losses.
Key Rate Limitations
Quantum key distribution is also bottlenecked by the speed at which secure keys can be generated. Traditional QKD systems produce keys at rates of a few kilobits per second—sufficient for encrypting voice calls or small data packets but impractical for high-bandwidth applications like video streaming. Advances in superconducting detectors and high-speed modulators aim to improve key rates, but further innovation is needed to match classical encryption speeds.
Cost and Infrastructure
The specialized hardware required for QKD—such as single-photon detectors, quantum light sources, and ultra-low-noise optical fibers—makes deployment expensive. For instance, commercial QKD systems can cost hundreds of thousands of dollars, putting them out of reach for most enterprises. Additionally, integrating quantum-secured links into existing telecommunication networks demands significant infrastructure upgrades, further complicating widespread adoption.
The Quantum vs. Post-Quantum Debate
Quantum cryptography often overlaps with discussions about post-quantum cryptography (PQC), leading to some confusion. While both address quantum threats, their approaches differ fundamentally.
QKD vs. Post-Quantum Algorithms
Quantum key distribution relies on the principles of quantum mechanics to secure communications inherently, whereas post-quantum cryptography involves developing new mathematical algorithms resistant to attacks from quantum computers. PQC solutions, currently being standardized by NIST, aim to replace vulnerable classical algorithms without requiring quantum hardware. However, QKD offers a unique advantage: information-theoretic security, meaning its safety doesn’t depend on unproven mathematical assumptions.
Hybrid Solutions Emerging
Recognizing the complementary strengths of both approaches, organizations are increasingly adopting hybrid systems combining QKD with post-quantum algorithms. This dual-layer encryption strategy ensures resilience even if one layer is compromised, providing a balanced transition path toward a quantum-safe future.
Breakthroughs in Quantum Networking
The push toward a quantum internet—a global network interconnected via quantum entanglement—has accelerated breakthroughs in quantum repeaters, memory storage, and entanglement swapping. These innovations address critical challenges in scaling quantum cryptography beyond point-to-point links.
Quantum Repeaters
Traditional signal amplifiers cannot be used in quantum communications without destroying the quantum states of photons. Quantum repeaters, still in experimental stages, aim to overcome this by leveraging entanglement swapping to extend the reach of QKD without measurement. Companies like Quantum Xchange in the U.S. and ID Quantique in Switzerland are pioneering modular repeater technologies to enable continental-scale quantum networks.
Quantum Memory
Storing quantum information is essential for synchronizing transmissions in large networks. Recent advances in atomic ensembles and rare-earth-doped crystals have demonstrated millisecond-long quantum memory retention—a critical step toward buffering entangled光子 for on-demand retrieval in complex networks.
Commercial and Open-Source Initiatives
The quantum cryptography market is witnessing a surge in private-sector involvement, with startups and tech giants alike racing to commercialize the technology.
Industry Leaders and Innovators
Companies like Toshiba, IBM, and QuintessenceLabs are offering enterprise-grade QKD solutions tailored for specific industries. Meanwhile, open-source projects such as the OpenQKD initiative by the European Union are fostering collaboration between academia and industry to standardize protocols and drive down costs.
Cloud-Based Quantum Security
Cloud providers are exploring quantum-secure services, such as AWS’s hybrid post-quantum TLS and Azure’s Quantum Network, allowing businesses to test quantum-resistant encryption without major infrastructure investments. These platforms serve as bridges for organizations transitioning toward full quantum readiness.
Looking Ahead
Quantum cryptography is transitioning from lab experiments to real-world deployments, but obstacles remain. The next decade will likely see breakthroughs in scalable QKD, affordable quantum hardware, and international standards—key enablers for a quantum-secured global infrastructure. In the final part of this series, we will explore speculative future applications, ethical considerations, and the role of policy in shaping quantum security’s trajectory.
Stay tuned for the concluding installment, where we examine how quantum cryptography could redefine privacy, governance, and trust in the digital age.
The Future of Quantum Cryptography: Ethical and Societal Implications
As quantum cryptography moves from theoretical research to practical implementation, it raises profound questions about its impact on society, governance, and individual privacy. The technology’s potential to revolutionize secure communication is undeniable, but it also introduces new challenges that must be addressed to ensure responsible adoption.
Privacy in the Quantum Era
Quantum cryptography promises unbreakable encryption, but it also poses ethical dilemmas. Governments and corporations could use quantum-secure networks to protect sensitive data, but the same technology might enable mass surveillance if misused. The balance between security and privacy will be a critical issue as quantum encryption becomes mainstream. Policymakers must establish clear regulations to prevent abuse while fostering innovation.
Global Security and Cyber Warfare
The advent of quantum computing and cryptography could shift the balance of power in cyber warfare. Nations with advanced quantum capabilities may gain an advantage in intelligence gathering and secure communications, potentially destabilizing international relations. The risk of a "quantum arms race" is real, with countries competing to develop quantum-resistant encryption and decryption tools. International cooperation will be essential to prevent an escalation of cyber conflicts.
Accessibility and Digital Divide
Quantum cryptography is currently expensive and complex, limiting its availability to wealthy nations and large corporations. If left unchecked, this could exacerbate the digital divide, leaving smaller businesses and developing nations vulnerable to cyberattacks. Efforts to democratize quantum-secure technologies—through open-source projects, subsidies, or international partnerships—will be crucial to ensuring equitable access.
Quantum Cryptography and Artificial Intelligence
The intersection of quantum computing and artificial intelligence (AI) presents both opportunities and risks. Quantum algorithms could enhance AI’s ability to analyze encrypted data, potentially breaking classical encryption methods. Conversely, AI could be used to optimize quantum cryptographic protocols, making them more efficient and secure. The synergy between these two fields will shape the future of cybersecurity.
AI-Powered Quantum Attacks
AI-driven cyberattacks are already a growing threat, and quantum computing could amplify their effectiveness. Machine learning models trained on quantum algorithms might identify vulnerabilities in classical encryption faster than human hackers. Defending against such threats will require AI-powered quantum defenses, creating a continuous arms race between attackers and defenders.
Quantum Machine Learning for Security
On the defensive side, quantum machine learning could revolutionize threat detection. Quantum-enhanced AI models could analyze vast datasets in real time, identifying anomalies and potential breaches with unprecedented accuracy. This could lead to proactive cybersecurity measures, where threats are neutralized before they cause harm.
The Role of Policy and Regulation
Governments and international organizations must play a proactive role in shaping the future of quantum cryptography. Without proper oversight, the technology could be weaponized or monopolized, leading to unintended consequences.
Standardization and Certification
Establishing global standards for quantum encryption is essential to ensure interoperability and security. Organizations like NIST and the International Telecommunication Union (ITU) are already working on post-quantum cryptographic standards, but more collaboration is needed to address emerging quantum threats. Certification programs for quantum-secure products will also be necessary to build trust among users.
Ethical Guidelines for Quantum Research
As quantum technology advances, ethical guidelines must be developed to govern its use. Researchers and policymakers should collaborate to address concerns such as data sovereignty, surveillance, and the militarization of quantum encryption. Transparency and public discourse will be key to ensuring that quantum cryptography benefits society as a whole.
Speculative Applications of Quantum Cryptography
Beyond cybersecurity, quantum cryptography could enable groundbreaking applications in various fields, from healthcare to space exploration.
Quantum-Secure Medical Data
Healthcare systems handle vast amounts of sensitive patient data, making them prime targets for cyberattacks. Quantum-secure encryption could protect medical records, ensuring patient confidentiality while enabling secure sharing of research data. This could accelerate medical breakthroughs while safeguarding privacy.
Interplanetary Communication
As humanity expands into space, secure communication between Earth and distant colonies or spacecraft will be critical. Quantum cryptography could enable unhackable communication links across vast distances, ensuring the integrity of mission-critical data. NASA and other space agencies are already exploring quantum communication for future Mars missions.
Quantum Voting Systems
Election security is a growing concern worldwide. Quantum-secure voting systems could prevent tampering and ensure the integrity of democratic processes. By leveraging quantum encryption, governments could create verifiable and tamper-proof digital voting mechanisms, restoring public trust in elections.
Conclusion: The Quantum Security Revolution
Quantum cryptography is poised to redefine the future of secure communication, offering unparalleled protection against cyber threats. However, its widespread adoption will require overcoming technical, ethical, and regulatory challenges. As we stand on the brink of a quantum revolution, collaboration between scientists, policymakers, and industry leaders will be essential to harness the technology’s potential while mitigating its risks.
The next decade will be pivotal in determining how quantum cryptography shapes our digital world. By addressing accessibility, ethical concerns, and global cooperation, we can ensure that this revolutionary technology serves as a force for good, safeguarding privacy and security in an increasingly connected world.
As quantum cryptography evolves, one thing is certain: the future of cybersecurity will be quantum, and the time to prepare is now.

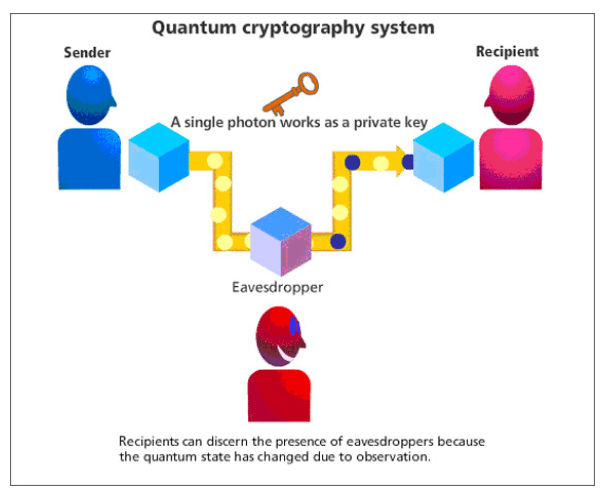
Top Content Creation and Web Design Trends for 2025
The landscape of digital content is undergoing a dramatic transformation. In 2025, successful brands will leverage a powerful combination of AI-driven content creation and immersive, human-centric design. This guide explores the pivotal shifts, from hyper-personalized messaging to bold web aesthetics, that will define the future of online engagement.
The Rise of AI-Powered Content Creation
Artificial intelligence is no longer a futuristic concept; it is the central engine of modern content strategy. Tools like ChatGPT and Jasper AI are revolutionizing how we produce, optimize, and distribute marketing materials. These platforms enable hyper-personalized messaging at an unprecedented scale, moving beyond simple segmentation.
How AI Transforms the Creative Workflow
AI streamlines the entire content lifecycle, from ideation to publication. It can generate initial drafts, suggest SEO optimization improvements, and even predict audience engagement metrics. This efficiency allows creative teams to focus on high-level strategy and adding a unique human touch.
One of the most significant advantages is the automation of repetitive tasks. AI can handle everything from automated editing to generating multiple content variations for different platforms. This shift empowers a do more with less approach, maximizing impact even with limited resources.
AI tools are crucial for content repurposing, transforming a single webinar into numerous clips, social posts, and visuals, significantly extending campaign lifecycles.
Dominance of Short-Form Video Content
Short-form video continues to reign supreme on platforms like TikTok, Instagram Reels, and YouTube Shorts. In 2025, the trend is not just about brevity but also about authenticity and relatability. Audiences crave genuine, unpolished moments that foster a stronger connection.
Optimizing Short-Form Video for Maximum Reach
To stand out, creators are using AI-assisted editing tools for faster production. Furthermore, adding accurate transcripts is a critical SEO optimization tactic. Transcripts make video content accessible to a wider audience and indexable by search engines, driving organic traffic.
The integration of interactive elements within videos is also gaining traction.
- Polls and Quizzes: Increase viewer engagement and gather valuable feedback.
- Clickable Links: Direct viewers to products or related content seamlessly.
- Augmented Reality (AR) Filters: Create shareable, branded experiences.
Interactive and Immersive Content Formats
Static content is giving way to dynamic, interactive experiences that actively involve the user. This shift is driven by a desire for deeper engagement and memorable brand interactions. Formats that encourage participation are seeing significantly higher conversion rates.
Key Formats for Engagement
Brands are investing in a variety of formats to capture attention.
- Live Streaming: Real-time engagement through Q&As, launches, and behind-the-scenes footage builds community and trust.
- Interactive Videos: Viewers can choose their own path, leading to a personalized story experience.
- Virtual Reality (VR) Demos: Especially in retail and real estate, VR offers immersive product try-ons or property tours.
These formats transform passive consumers into active participants, creating a more profound and lasting impression.
Evolution of Web Design: Bold and Authentic
Web design in 2025 reflects a move towards bold typography and expressive layouts. Designers are embracing maximalism, serif fonts, and variable fonts to create visually striking and memorable sites. This trend emphasizes brand personality and authenticity over minimalist conformity.
The Influence of Brutalism and Anti-Design
In a reaction against overly polished interfaces, brutalist web design elements are emerging. This style uses raw, high-contrast aesthetics, asymmetric layouts, and a "unfinished" look to convey honesty and human imperfection. It aligns with the broader demand for genuine brand storytelling.
These designs often incorporate:
- Vivid color contrasts and bold blocks.
- Experimental navigation patterns.
- Motion and scrolling animations for dynamic storytelling.
The Critical Shift to Purpose-Driven Narratives
Audiences in 2025 are more discerning and value-driven than ever before. They expect brands to stand for something beyond profit. Content that showcases a company's purpose, values, and social impact resonates deeply and builds long-term loyalty.
This involves highlighting employee stories, sustainable practices, and community involvement. Authentic User-Generated Content (UGC) is also powerfully leveraged to build a trust ecosystem, demonstrating real-world product value through customer eyes. Brands that master this human connection will thrive in the competitive digital landscape of 2025.
Hyper-Personalization Through Real-Time Data
The concept of personalization has evolved beyond simply using a customer's first name in an email. In 2025, hyper-personalization is powered by real-time data analytics, allowing brands to deliver content tailored to an individual's immediate context, behavior, and preferences. This creates a uniquely relevant experience for every user.
Implementing Dynamic Content Delivery
Advanced algorithms now analyze user interactions—such as click patterns, time spent on page, and past purchases—to dynamically adjust website content, product recommendations, and marketing messages in real-time. This means two visitors to the same website might see completely different headlines, hero images, or call-to-action buttons based on their unique data profiles.
The goal is to make every digital interaction feel like a one-on-one conversation. This level of customization significantly increases engagement and conversion rates by presenting users with exactly what they are most likely to need or want at that precise moment.
Brands leveraging hyper-personalization report a significant uplift in customer engagement, with some seeing conversion rate increases of up to 15-20%.
Sustainability and Accessibility as Core Design Principles
Modern web development is increasingly guided by ethical considerations, with sustainability and accessibility moving from afterthoughts to foundational pillars. Users are more conscious of the digital carbon footprint and expect inclusive design that accommodates everyone.
Building Eco-Friendly Digital Experiences
Sustainable web design focuses on creating efficient, low-impact websites. This involves optimizing images and code to reduce data transfer, which leads to faster load times and lower energy consumption on both servers and user devices. A faster website is not only better for the planet but also improves SEO and user satisfaction.
Key practices include:
- Efficient Coding: Minimizing HTTP requests and eliminating unnecessary code.
- Green Hosting: Choosing web hosting providers powered by renewable energy.
- Optimized Media: Using modern image formats like WebP and implementing lazy loading.
Advancing Digital Accessibility
Accessibility ensures that websites and content are usable by people with a wide range of abilities. This includes support for screen readers, keyboard navigation, voice search compatibility, and features like dark mode for reduced eye strain. Adhering to Web Content Accessibility Guidelines (WCAG) is not just a legal necessity in many regions; it's a moral imperative that expands your audience.
An accessible website benefits all users, not just those with disabilities. Clear navigation, high color contrast, and readable fonts create a better experience for everyone, ultimately leading to lower bounce rates and higher engagement.
The Integration of Immersive Technologies: AR and VR
Augmented Reality (AR) and Virtual Reality (VR) are moving from niche novelties to mainstream content tools. These immersive technologies offer powerful new ways for brands to tell stories, demonstrate products, and create unforgettable experiences that bridge the gap between the digital and physical worlds.
Practical Applications of AR and VR
For e-commerce, AR allows customers to try before they buy in their own space. Imagine visualizing how a new sofa looks in your living room or trying on a pair of sunglasses using your phone's camera. This reduces purchase hesitation and lowers return rates.
In other sectors, VR can be used for virtual property tours, immersive training simulations, or interactive museum exhibits. These applications provide a level of engagement that static images and text simply cannot match, creating a deeper emotional connection with the brand.
Strategic Content Repurposing for Maximum ROI
In an era of resource constraints, maximizing the value of every piece of content is essential. Content repurposing is the strategic practice of transforming a single, high-quality core asset—like a webinar, whitepaper, or long-form video—into multiple derivative pieces for different platforms and audiences.
Creating a Repurposing Workflow
AI tools are instrumental in automating and scaling repurposing efforts. A comprehensive strategy ensures your message reaches audiences wherever they are, in the format they prefer. This approach dramatically increases content ROI without requiring a proportional increase in creative effort or budget.
An effective workflow might look like this:
- Pillar Content: Produce a flagship asset, such as a detailed industry report or a 60-minute expert webinar.
- Atomize: Break the pillar content into smaller chunks. Extract key quotes for social media graphics, transcribe the webinar for a blog post, and clip the most impactful moments for short-form video.
- Distribute: Share these repurposed pieces across all relevant channels—blog, YouTube, LinkedIn, TikTok, email newsletters—over a planned schedule.
Voice Content and the Rise of Audio-First Strategies
With the proliferation of smart speakers and voice assistants, optimizing content for audio consumption is no longer optional. A dedicated voice content strategy involves creating material specifically designed to be heard, not read, catering to the growing audience that prefers podcasts, audiobooks, and voice search.
Optimizing for Voice Search and Audio Platforms
Voice search queries are fundamentally different from text-based searches; they are typically longer and phrased as questions. Content must be optimized to answer these natural language queries directly and concisely. This often involves creating FAQ pages and structuring content in a clear, conversational tone.
Beyond search, brands are launching podcasts and developing audio experiences to connect with audiences during commutes, workouts, or household chores. This audio-first approach allows for deeper, more intimate storytelling and helps build a loyal community of listeners.
The Human Touch: Blending AI with Authenticity
While AI-driven content creation provides unmatched efficiency, the most successful brands of 2025 will be those that skillfully blend this technology with a genuine human voice. Audiences are adept at detecting purely algorithmic content, which can erode trust. The key is to use AI as a powerful tool to augment human creativity, not replace it.
Strategies for Maintaining Authenticity
Brands must infuse AI-generated drafts with unique perspectives, anecdotes, and emotional intelligence that only humans can provide. This involves a collaborative workflow where AI handles data-heavy tasks like research and optimization, while human creators focus on storytelling, brand tone, and emotional connection.
- Curate AI Output: Always review, edit, and add personal flair to AI-generated text to ensure it aligns with your brand's unique personality.
- Leverage Employee Advocacy: Encourage employees to share their genuine experiences, creating relatable and trustworthy content.
- Prioritize User-Generated Content (UGC): Showcase real customer stories and reviews to build social proof and authenticity.
This balance ensures that content remains scalable and data-informed while retaining the relatable quality that fosters true audience connection.
Future-Proofing Your Strategy: Preparing for 2026 and Beyond
The trends of 2025 are not fleeting; they are the foundation for the next evolution of digital marketing. Proactive brands are already looking ahead to build a trust ecosystem and adapt to emerging technologies. Preparing for the future requires a flexible, forward-thinking approach to both content and design.
Building a Foundation for Future Trends
Investing in a modular content system is crucial. This means creating content in a way that makes it easily adaptable for new platforms and formats that have not yet become mainstream. A strong data analytics framework is also essential for quickly identifying and capitalizing on new audience behaviors.
Key areas to monitor include:
- The Metaverse: Exploring opportunities for branded presence in emerging virtual worlds.
- Advanced AI Personalization: Preparing for AI that can predict user needs before they are explicitly stated.
- Interactive Live Commerce: Integrating direct purchasing into live-streamed content seamlessly.
The Importance of a Unified Cross-Channel Experience
In a fragmented digital landscape, delivering a consistent and seamless experience across all touchpoints is paramount. A unified cross-channel experience ensures that whether a user interacts with your brand on social media, your website, an email, or a mobile app, the messaging, design, and value proposition remain coherent.
Creating a Cohesive Brand Journey
This requires meticulous planning and the use of integrated marketing platforms. Data should flow seamlessly between channels, allowing for personalized follow-ups. For example, a user who watches a product video on TikTok should see a related offer in their email inbox or as a retargeting ad.
Consistency in visual identity—using the same bold typography, color schemes, and tone of voice—reinforces brand recognition and builds trust. A disjointed experience, on the other hand, can confuse users and diminish the perceived value of your brand.
Measuring Success: KPIs for the Modern Content Era
With evolving strategies, the key performance indicators (KPIs) for measuring success must also adapt. Beyond traditional metrics like page views and click-through rates, brands now need to track engagement depth, content repurposing efficiency, and the impact of interactive formats.
Essential Metrics to Track in 2025
Understanding what truly drives value is key to optimizing your strategy. It's important to look at a blend of quantitative and qualitative data to get a full picture of performance.
- Engagement Rate: Time on page, scroll depth, and interactions with polls or quizzes.
- Content Amplification Score: How effectively is your content being shared across different platforms?
- Personalization Impact: A/B test personalized content versus generic content to measure lift in conversions.
- Voice Search Ranking: Track your position for common conversational queries.
By focusing on these advanced metrics, you can make data-driven decisions that continuously refine your approach for maximum impact.
Conclusion: Mastering the 2025 Digital Landscape
The digital world of 2025 is defined by intelligent automation, authentic connection, and immersive experiences. The convergence of AI-driven content creation, short-form video, and expressive web design trends presents both a challenge and an incredible opportunity for brands. Success hinges on the ability to be both efficient and deeply human.
The most effective strategies will leverage AI to handle scalability and data analysis while ensuring the final output resonates with genuine emotion and purpose. Embracing hyper-personalization, interactive content, and ethical principles like sustainability and accessibility is no longer optional for brands that wish to remain competitive and relevant.
The future belongs to agile creators who can harness technology to build meaningful, memorable, and trustworthy relationships with their audience.
As we look beyond 2025, the pace of change will only accelerate. By building a flexible foundation today—one that values authenticity as much as automation and human connection as much as high-tech tools—your brand will be perfectly positioned to not just adapt, but to lead in the exciting digital landscape of tomorrow. Start implementing these trends now to future-proof your strategy and create a lasting impact.

Charles Babbage: Pioneer of the Computing Revolution
In the annals of technological innovation and scientific endeavor, few names shine as brightly as that of Charles Babbage. Often heralded as the "father of the computer," Babbage's intellectual legacy is rooted deeply in his visionary designs and relentless pursuit of mechanizing computation. His profound contributions have laid the foundational stones for the digital age, inspiring generations of innovators who followed in his footsteps.
Early Life and Education
Born on December 26, 1791, in Teignmouth, Devonshire, England, Charles Babbage was the son of Benjamin Babbage and Elizabeth Teape. From the start, Charles was a curious and intellectually gifted child. His parents recognized his potential early on and ensured that he received a quality education. He began his formal education in a small village school before moving on to the prestigious Forty Hill School in Enfield.
However, it was at Trinity College, Cambridge, where Babbage's love for mathematics flourished. He found himself disenchanted with the mathematical instruction provided at the university, finding it outdated and limiting. Alongside his friends, including renowned mathematicians like John Herschel and George Peacock, Babbage founded the Analytical Society in 1812. Their goal was to promote the understanding and adoption of more advanced mathematical techniques derived from European works, specifically those from France.
Conceptualizing the First Computing Machines
Babbage's most significant contributions to the world stemmed from his revolutionary ideas about mechanical computation. In the early 19th century, calculations were laborious endeavors prone to human error. Babbage envisioned a machine that could perform accurate, repeatable, and complex calculations autonomously. This dream led him to design the Difference Engine in the 1820s—a device intended to simplify the creation of mathematical tables used in engineering, navigation, and astronomy.
The British government, recognizing the potential of Babbage's invention, supported the development of the Difference Engine with funding. The design incorporated numerous mechanical components intended to automate polynomial calculations across a set numerical range. Although Babbage faced various technical challenges and setbacks, his work on the Difference Engine set the stage for future innovations.
The concept of the Analytical Engine, however, truly solidified Babbage's role as a visionary. Envisioned as an enhancement to the Difference Engine, the Analytical Engine proposed a general-purpose computing device. It would, in theory, possess key features of modern computers: a central processing unit (CPU), memory, and the ability to perform programmed instructions via punch cards—a concept later embraced in early 20th-century computing.
The Challenges and Legacy
While Babbage's ideas were groundbreaking, they confronted several obstacles. The technology of his time was not sufficiently advanced to support the intricacies of his designs. His reliance on precision engineering, which was feasible in concept but difficult in practice, compounded these challenges. Further complicating his efforts, Babbage often struggled to communicate his vision to potential supporters and financiers. Consequently, his projects frequently suffered from funding shortfalls and logistical challenges.
Nevertheless, Babbage's theoretical contributions were invaluable. His collaboration with Ada Lovelace—mathematician and daughter of famed poet Lord Byron—marked a significant milestone. Lovelace wrote extensive notes on the Analytical Engine, conceptualizing it as a machine capable of much more than mere arithmetic; she foresaw its potential to execute complex instructions, essentially laying the groundwork for programming.
Babbage's legacy extends beyond his machines. His intellectual pursuits and meticulous studies covered a wide range of disciplines, including cryptography, economics, and even the development of the postal system. His investigative spirit and commitment to progress profoundly influenced the trajectory of future engineering and scientific exploration.
Throughout the 19th century and beyond, researchers and engineers continued to draw inspiration from Babbage's work. Long after his death in 1871, the components and principles he proposed in the Analytical Engine became instrumental during the development of early computers in the mid-20th century. In essence, Babbage's ideas transcended his era, paving the way for the explosive growth of computing technology that defines contemporary society.
Charles Babbage's life paints a compelling picture of a man ahead of his time—his story a testament to the power of vision, innovation, and tenacity in the face of seemingly insurmountable odds. His seminal contributions resonate across scientific and technological fields, serving as a reminder of the enduring impact that a single mind can have on the world.
The Analytical Engine: A Revolutionary Concept
While the Difference Engine was Babbage's first foray into mechanical computation, it was the Analytical Engine that truly represented a leap into what many would now deem the realm of computers. Conceived in 1837, the Analytical Engine was a monumental stride in thinking about automated calculation. Unlike its predecessor, which was limited to performing a predefined set of calculations, the Analytical Engine was designed to be fully programmable. This programmability was a novel idea that suggested a machine could be instructed to perform a variety of operations sourced from a generalized set of instructions.
The Analytical Engine comprised four key components that resembled a modern computer's architecture: the mill (similar to a CPU), the store (akin to memory), the reader (which took in input via punch cards), and the printer (which output the results of calculations). This architecture embodied the idea of separating processing from storage and instruction, a concept that is central to computer design today.
The punch card system, inspired by the Jacquard loom which used punch cards to control weaving patterns in textiles, was an ingenious choice for inputting instructions into the machine. This allowed for a sequence of operations that could be customized for different problems, highlighting the versatility of Babbage's design. The use of punch cards also introduced the notion of programmability—decades before computers became a reality.
Ada Lovelace: The First Computer Programmer
One of the most remarkable figures linked to Babbage's work on the Analytical Engine was Ada Lovelace. Her collaboration with Babbage gave rise to what many consider the first computer program. Lovelace's involvement began when she translated an Italian mathematician's article about the Analytical Engine into English. Babbage, recognizing her mathematical talent and analytical prowess, invited her to expand on the translation with her own notes.
Lovelace's notes shed light on the Analytical Engine's potential beyond number crunching. Her farsighted vision included its capability to handle symbolic manipulation and to execute loops and conditional operations—a sophistication not realized until computer science matured over a century later. Her work in these notes elevated her status to that of the world's first computer programmer, earning her a revered place in computing history.
She famously postulated the machine's capacity to compose music if fed the correct set of instructions, an idea that weaves the creative with the technical. Lovelace's work sketched out the philosophical underpinnings of computational theory, influencing beyond Babbage's purely mechanical ambitions.
The Legacy of Unrealized Potential
Despite Babbage's pioneering concepts, the Analytical Engine never came to fruition in his lifetime. The numerous demands of engineering, coupled with persistent difficulties in securing reliable funding, meant that Babbage could only build partial prototypes. The engines he envisioned were extraordinarily complex, requiring precision engineering far beyond the capabilities of the craftsmen of his era.
The failure to construct a complete model of the Analytical Engine does not diminish Babbage's contributions. Instead, his visionary designs and theoretical work inked a blueprint for future thinkers. The principles laid out by Babbage served as inspiration when the computational gears began turning again in the early 20th century.
In the 1930s and 1940s, engineers and mathematicians began to revisit Babbage's concepts, compounded by the pressure of wars that sought advanced computation for strategy and encryption. Figures like Alan Turing and John von Neumann drew inspiration from the basic tenets Babbage proposed—chiefly the separation of processing and memory and the concept of a stored-program computer.
Today's computers, with their unfathomable processing power and versatility, are very much the descendants of Babbage's unfinished progeny. His life underscores an enduring truth: true innovation often requires not just visions grounded in current possibilities, but dreams that leap into future unknowns.
A Timeless Influence
Babbage lived in an era when scientific pursuit did not receive the systematic support it does today. His endeavors highlight how personal dedication and intellectual curiosity can lead to discoveries with far-reaching consequences. Babbage’s relentless spirit resonates with researchers and engineers who continue to push the boundaries of what machines can accomplish.
Through the lense of history, Charles Babbage is celebrated not just as a mathematician or inventor, but as a beacon of the relentless quest for knowledge and improvement. His work exemplifies the iterative nature of innovation, where each unfulfilled potential becomes the seed for future success.
By daring to dream of machines that could think, process, and calculate, Charles Babbage laid the philosophical groundwork for an entire field of study—our world rendered increasingly digital and interconnected owes much to his ambitious vision and diligent scholarship. As technology continues to evolve, the legacy of Charles Babbage reminds us of the unexplored potential that lies in our imaginations, waiting to be realized.
Reconstructing Babbage: Modern Attempts and Recognitions
In many ways, Charles Babbage's ideas were a century ahead of their time, yet they were left to be realized only in fragments. In the 1980s and 1990s, the curiosity about what could have been began to inspire new endeavors to bring Babbage's visions to life. Fueled by the advancements in modern engineering and a resurgence of interest in the history of computing, several projects aimed to construct working models of Babbage's designs.
The most notable of these efforts occurred at the Science Museum in London, where a team, led by engineer Doron Swade, embarked on an ambitious journey to construct a working model of Babbage’s Difference Engine No. 2, a later design that Babbage had conceived during the 1840s. After years of meticulous work, the team successfully completed the project in 1991, finally realizing what Babbage's 19th-century calculations and ingenuity could not bring to fruition. This accomplishment underscored the mechanical brilliance of Babbage's design, showcasing its ability to execute complex calculations reliably and accurately.
Similarly, interest in the Analytical Engine has spurred enthusiasts and historians to continue exploring how it might have revolutionized computing had it been completed. Projects to simulate parts of the Analytical Engine using modern technology keep Babbage’s work pertinent and alive, providing glimpses into the potential operations of his conceptual design.
Impact on Modern Computing and Legacy
Though Charles Babbage's machines remained unrealized in his time, his analytical framework left a profound imprint on the evolution of computing. His pioneering concepts laid the groundwork for many future developments, including the theoretical underpinnings taught in computer science courses today. The structures and principles he envisaged are echoed in every byte of data processed by modern devices—from the smallest microprocessor to the most colossal supercomputers.
Babbage's legacy extends beyond the technical. He is a testament to the power of perseverance in the face of technological limitations and societal skepticism. His work ethic and intellectual rigor continue to inspire those who innovate, reminding us of the rewards of daring to envision technology not merely as it is, but as it could be.
Honored posthumously with numerous accolades and memorials, Babbage's name bears an enduring resonance. Institutions such as the Charles Babbage Institute at the University of Minnesota, dedicated to the history of information technology, stand as tributes to his enduring impact on the field. His influence pervades academic discussions, innovation narratives, and is often a point of reference in the discourse about the origins of the digital age.
Babbage's Influence in Today's Digital Landscape
In our contemporary digital landscape, where computing technology influences every aspect of daily life, the seeds sown by Babbage's insights continue to bear fruit. His prescience in envisioning a society reliant on data and computation is reflected in today's pervasive technology, ranging from handheld devices to complex algorithms powering artificial intelligence.
Moreover, recognizing Babbage's contributions has fostered greater awareness and appreciation of how inter-disciplinary collaborations—like that between Babbage and Ada Lovelace—can yield transformative outcomes. In today's world, where technology increasingly mines from diverse fields, insights from Babbage's life underscore the importance of leveraging cross-disciplinary visions and teamwork to harness the full potential of innovation.
The narrative of Charles Babbage serves as a valuable reminder of the intricacies in the path to technological advancement. His failed successes, in the words of Babbage himself, were "the stepping stones to great achievement." In an era characterized by rapidly evolving technology, the lessons from Babbage's odyssey reinforce the importance of continued exploration, courage in the face of failure, and the transformative power of visionary thought.
Conclusion: A Timeless Innovator
Charles Babbage exemplified the power of imagination interwoven with precision. Though he could never build his ultimate machines, his designs and theoretical innovations remained a guiding light for future generations. From his early days at Cambridge to his lifelong dedication to progress, Babbage navigated the complex intersections of engineering, mathematics, and thought with unmatched tenacity.
His life’s work did not just lie in the unrealized engines, but in the legacy of curiosity he ignited—a legacy that continues to inspire inventors and thinkers today. Just as the modern computer owes its existence to the tireless efforts of many, Babbage stands as a pivotal figure whose dreams laid the groundwork for technology that defines our modern world, signifying a timeless influence in the ever-unfolding story of human innovation.




Tim Berners-Lee: The Architect of the World Wide Web
In the annals of technological history, few individuals have made as profound an impact as Sir Tim Berners-Lee. Often hailed as the architect of the World Wide Web, Berners-Lee's transformative work in the late 20th century created the very foundation upon which much of our modern digital lives depend. As a visionary computer scientist, his contributions have facilitated unprecedented global communication, reshaped industries, and changed how society accesses information.
Early Life and Education
Tim Berners-Lee was born on June 8, 1955, in London, England. The son of computer scientists Mary Lee Woods and Conway Berners-Lee, he was introduced to the world of computing at a young age. With his parents both working on the early Ferranti Mark 1, one of the first commercially available computers, Berners-Lee's interest in technology was all but inevitable. This early exposure would prove crucial in shaping his future career.
Berners-Lee attended Queens College at the University of Oxford, where he pursued a degree in physics. During his time at Oxford, he exhibited a keen interest in electronics, building his own computer using a soldering iron, TTL gates, and a M6800 processor. This venture, though modest, foreshadowed the innovative spirit that would later characterize his career. Upon graduating in 1976, Berners-Lee began his career as an engineer, working at various firms where he honed his skills in telecommunications and software engineering.
From Concept to Creation: The Birth of the World Wide Web
In 1980, Berners-Lee's career took a pivotal turn when he began working as an independent contractor for CERN, the European Organization for Nuclear Research in Switzerland. It was here that he conceived an idea that would radically alter the landscape of digital communication. Recognizing the inefficiencies in managing and sharing information among researchers, Berners-Lee proposed a decentralized, hypertext-based system.
Building upon this initial concept, Berners-Lee developed a working prototype, "ENQUIRE," a program that allowed users to store and retrieve information in a non-linear fashion. Though rudimentary, ENQUIRE demonstrated the potential of linking information across computers, sowing the seeds for what would later become the World Wide Web.
Returning to CERN in 1989 as a full-time employee, Berners-Lee took his vision further. He proposed an expansive project that would enable researchers worldwide to share information effortlessly. Seamlessly integrating concepts from ENQUIRE and tapping into the burgeoning world of internet protocols, Berners-Lee designed the initial specifications for URLs (Uniform Resource Locators), HTTP (Hypertext Transfer Protocol), and HTML (Hypertext Markup Language). These core components laid the groundwork for the web as we know it today.
Launching the Web and Its Initial Impact
By Christmas 1990, with crucial assistance from Robert Cailliau, a Belgian engineer and fellow CERN member, Berners-Lee had successfully implemented the first web server and web browser. The World Wide Web was born, a name devised to encapsulate the intricate design of a universal, interconnected digital space.
The impact of Berners-Lee's creation was nothing short of revolutionary. For the first time, users could access information from servers across the globe through a simple, user-friendly interface. This innovation not only democratized access to information but also catalyzed the rapid expansion of the internet. By the mid-1990s, the web had become an indispensable tool for academic, commercial, and personal communication, ushering in a new era of digital connectivity.
The World Wide Web Consortium and Ongoing Legacy
In 1994, recognizing the need for coherent development and open standards, Berners-Lee founded the World Wide Web Consortium (W3C) at MIT. This international body consists of member organizations that oversee the evolution of web standards to ensure the internet remains a robust, open platform for all. By eschewing the commercialization of the web, Berners-Lee secured its open nature, allowing innovation and competition to flourish.
Berners-Lee's guiding philosophy throughout his career has been the belief in the power of universal access to information. His insistence on keeping the web as a neutral, decentralized medium has championed the idea of an inclusive digital world, where knowledge and opportunities are accessible to all, irrespective of geographic and socio-economic barriers.
Continued advocacy for privacy and digital rights underscores his lasting impact. In recent years, Berners-Lee has been vocal about the challenges facing the modern web, including issues of privacy, data ownership, and the monopolistic tendencies of tech giants. His latest initiative, Solid, seeks to empower users with greater control over their personal data by redesigning the web's underlying architecture.
As we stand on the brink of a new era of technological innovation, Sir Tim Berners-Lee's contributions continue to resonate strongly. His work has not only shaped our past and present but also serves as a guiding light for the digital future, underscoring the timeless value of an open, accessible internet.
A Visionary for Open Access and Digital Freedom
Tim Berners-Lee's philosophy did not stop at merely creating technological groundwork; it extended into the ideological realm of digital freedom and open access. From the outset, his vision for the World Wide Web was not one driven by profit, but rather a democratic and inclusive platform that could bridge divides and foster innovation. Berners-Lee's unwavering commitment to an open internet has profoundly influenced the web's development trajectory and its role as a global public good.
The decision to make the World Wide Web technology available to everyone without licensing fees in the early 1990s was pivotal. This decision allowed a plethora of developers, entrepreneurs, and researchers to build on Berners-Lee’s work, leading to exponential innovation and the creation of an expansive digital ecosystem. This openness is a stark contrast to the proprietary systems that prevailed at the time, which were restricted by patent controls and financial barriers.
Berners-Lee’s belief in the power of collective innovation continues to inspire initiatives across the globe, from open-source software development to collaborative research networks. By ensuring the web remained a shared space, Berners-Lee has helped nurture a culture of democratized knowledge, where information and technology are tools for empowerment rather than exclusion.
Challenges and Advocacy in the Modern Digital Landscape
As the web has evolved, so too have the challenges that come with a hyper-connected world. Tim Berners-Lee has been outspoken about these challenges, emphasizing the need to protect the fundamental principles he championed. Among these challenges are issues of privacy, data rights, and the concentration of power within technology behemoths.
The rise of social media platforms and search engines has brought unprecedented data collection, often without users' explicit consent or understanding. Berners-Lee views this as a deviation from the web's original ideals of empowerment and self-determination. He has frequently highlighted the ethical responsibilities of companies and developers to respect user privacy and to safeguard digital rights.
In response to these pressing concerns, Berners-Lee has launched several initiatives aimed at reclaiming the web for its users. The most notable is the Solid project, which emerged to tackle the issues of data autonomy and privacy. Solid aims to provide individuals with the means to control how their data is stored and shared across the web. By promoting decentralized data management, the project seeks to return control to users and prevent undue exploitation by centralized entities.
This advocacy extends beyond technology into policies and regulations. Berners-Lee has engaged with governments and international organizations to promote policies that protect the openness of the internet. His efforts have included advisories to the European Union on data protection regulations and participation in efforts to bridge the digital divide in underserved regions.
The Net Neutrality Debate
Another crucial issue Berners-Lee has engaged with is the battle for net neutrality. The principle of net neutrality asserts that internet service providers (ISPs) must treat all data on the internet the same way, without discrimination or differential charging by user, content, site, platform, or application. Berners-Lee has been a staunch advocate for this principle, arguing that it is essential for maintaining the open nature of the web.
Without net neutrality, the web risks becoming a tiered system where only companies that can afford to pay premium fees can ensure their content is delivered swiftly to users. This scenario harms small businesses, stifles innovation, and limits the diversity of voices and opinions online. Berners-Lee has consistently warned against legislative moves to dismantle net neutrality protections and has lobbied for their maintenance across different nations.
His stance is a powerful reminder of the enduring need to protect the elements that make the web a unique and transformative platform. Through his work and advocacy, Berners-Lee ensures that the web remains a tool for progress—a place where ideas can be shared freely and fairly, without the barriers of censorship or financial competition.
The Ongoing Relevance of Berners-Lee's Vision
As digital technology continues to evolve at breakneck speed, the principles laid down by Tim Berners-Lee serve as a vital touchstone for those who navigate this complex landscape. The challenges facing the modern internet—from fake news and misinformation to concerns about surveillance—make Berners-Lee’s commitment to a free, open, and unencumbered web more relevant than ever.
His vision continues to inspire not only developers and policymakers but also educators and community organizers dedicated to ensuring digital equity. By promoting digital literacy, Berners-Lee encourages a generation of users and creators who are equipped to navigate an increasingly digital world ethically and responsibly.
In a world deeply entwined with technology, Sir Tim Berners-Lee's legacy remains pivotal. His aspirations for a universal web, accessible and beneficial for all, underline the importance of safeguarding digital freedoms and ensuring that technology serves humanity as a whole. His work serves as a constant reminder that, while technology may advance, the core values of openness, inclusivity, and equity must continue to guide its development.
The Innovator's Recent Ventures and Initiatives
In addition to his advocacy for digital rights, Tim Berners-Lee has been actively involved in ongoing technological innovation. One of his more recent ventures, Inrupt, further underscores his commitment to revolutionizing the web. Co-founded in 2018, Inrupt aims to help Solid achieve widespread adoption, enabling users to better control their personal data across different platforms and services. By establishing partnerships with leading enterprises and developers, Inrupt seeks to create a more secure and decentralized internet ecosystem.
The potential implications of Inrupt’s success are vast. By shifting data ownership back to individuals, the platform could significantly disrupt existing business models that rely heavily on data monopolization. It envisions a reimagined digital landscape where user empowerment is prioritized, fostering an environment that aligns with Berners-Lee's original vision for the web.
In addition to his work with Solid and Inrupt, Berners-Lee remains engaged with numerous academic and technological discussions concerning the future of the internet. He continues to collaborate with institutions and participate in events that explore emerging technologies such as artificial intelligence and blockchain, examining ways to integrate these advancements while respecting the fundamental principles of user control and privacy.
Honors and Recognitions
Throughout his illustrious career, Tim Berners-Lee’s contributions to technology and society have been acknowledged with an array of prestigious awards and honors. In 2004, he was knighted by Queen Elizabeth II for his groundbreaking work on the World Wide Web, becoming Sir Tim Berners-Lee, an acknowledgment of his monumental impact on modern civilization.
In addition to his knighthood, Berners-Lee has received multiple accolades, including the inaugural Millennium Technology Prize in 2004, the highest international honor for technological innovation. This award recognized his invention and subsequent efforts to maintain an open, free web. In 2007, he was inducted into the Internet Hall of Fame, further solidifying his place among the most influential figures in the history of the internet.
In recent years, Berners-Lee has been an active participant in conferences and forums worldwide, where he continues to advocate for the values of openness and collaboration in the technological sphere. His insights are highly sought after in discussions concerning the web's role in societal development and its future trajectory.
A Legacy of Influence and Inspiration
As we reach the overarching conclusions of Tim Berners-Lee's narrative, it's evident that his influence extends beyond technology and into the broader societal fabric. His work has inspired countless individuals in various fields, from computer science and engineering to education and policymaking. Each innovation and initiative underlines his commitment to a web that serves humanity as a whole.
Berners-Lee's advocacy for digital literacy and inclusivity resonates in today’s educational and developmental frameworks, encouraging programs that prioritize universal access to technology and information. By championing a digitally inclusive world, he has helped pave the way for efforts to bridge the digital divide—a critical endeavor as society becomes ever more interconnected and technologically oriented.
Beyond technical acumen, Berners-Lee embodies the guiding principle that technology must evolve ethically, with consideration for its social and cultural implications. His vision for a free and open web instills a sense of responsibility among developers, educators, and policymakers to approach digital innovation with an emphasis on human rights and social equity.
Conclusion
The profound legacy of Sir Tim Berners-Lee is a testament to the enduring power of an individual's vision combined with perseverance and an ethical commitment to positive global change. In inventing the World Wide Web, he transformed not only technology but the very manner in which we interact with the world, making knowledge more accessible and creating a platform ripe for collaboration and innovation.
While challenges persist in the digital realm—issues concerning privacy, data security, and the power dynamics of information—Berners-Lee’s foundational work and ongoing advocacy serve as guiding beacons. His efforts remind us that the web's potential for good far outweighs any pitfalls, as long as we remain vigilant stewards of its underlying principles.
In an era marked by rapid advancement and unprecedented connectivity, the ideals envisioned by Tim Berners-Lee continue to shape our digital landscape, urging us to foster a culture of openness, fairness, and shared wisdom. His story is one of resilience, intellect, and an unwavering belief in the power of technology to unite and uplift humanity, ensuring that the transformative capability of the internet remains an accessible and equitable resource for all.


Tim Berners-Lee: The History and Evolution of the World Wide Web
Introduction to the Father of the World Wide Web
Sir Tim Berners-Lee, born on June 8, 1955, in London, England, is the visionary computer scientist credited with inventing the World Wide Web (WWW) in 1989. His groundbreaking work at CERN revolutionized global communication, making the internet accessible to billions. This article explores his life, the creation of the web, and its profound impact on society.
The Early Life and Influences of Tim Berners-Lee
Berners-Lee's fascination with computing began early. His parents, both pioneering programmers, worked on the Ferranti Mark 1, one of the first commercially available general-purpose computers. This early exposure sparked his interest in technology.
A Childhood of Curiosity and Innovation
As a child, Berners-Lee was an avid train-spotter, a hobby that honed his attention to detail. He also tinkered with electronics, building a model railway system. These experiences laid the foundation for his future innovations.
Academic Pursuits and Early Achievements
Berners-Lee earned a first-class physics degree from The Queen's College, Oxford in 1976. During his studies, he built his first computer using an old TV set, a soldering iron, transistors, and a microprocessor. This hands-on approach to technology would later define his career.
The Birth of the World Wide Web
In March 1989, while working at CERN, Berners-Lee proposed an information management system that would use HTTP, HTML, and URLs to link hypertext documents over the internet. This proposal marked the birth of the World Wide Web.
The First Successful Communication
By mid-November 1989, Berners-Lee achieved the first successful client-server communication. This milestone was followed by the launch of the first website in 1990-1991. His decision not to patent the WWW made it freely available, enabling its rapid global adoption.
The Core Technologies Behind the Web
Berners-Lee's invention relied on three core technologies:
- HTTP (HyperText Transfer Protocol): The protocol for transferring data over the web.
- HTML (HyperText Markup Language): The markup language for creating web pages.
- URLs (Uniform Resource Locators): The addresses that uniquely identify resources on the web.
The Impact and Legacy of the World Wide Web
The World Wide Web transformed the pre-existing internet from a text-based network used primarily by technical users into a user-friendly, graphical platform. This shift enabled the creation of social features, memes, and platforms like Wikipedia, which have become integral to modern life.
A Free and Open Web
Berners-Lee's commitment to a free, open, and ethical web has been a guiding principle throughout his career. He has warned against the centralization of the web by tech giants and has advocated for user control over data through initiatives like Solid, a protocol he founded in 2018.
Recognition and Honors
Berners-Lee's contributions have been widely recognized. He was honored as the "Inventor of the World Wide Web" at the 2012 Olympics, where he tweeted the iconic message, "This is for everyone." He continues to play an active role in web standards through the W3C (World Wide Web Consortium), which he directs.
Recent Developments and Future Trends
In 2025, Berners-Lee published his memoir, This is For Everyone, ghostwritten by Stephen Witt. The book has received mixed reviews but offers insights into his life and work. He also appeared on BBC Radio 4's Desert Island Discs, where he chose a chromatic harmonica as his luxury item.
Advocacy for a Better Web
Berners-Lee remains a vocal advocate for a better web. He emphasizes the importance of collaborative tinkering over profit and continues to push for innovations that prioritize user privacy and data control. His legacy is a testament to the power of open collaboration and the transformative potential of technology.
Conclusion
Tim Berners-Lee's invention of the World Wide Web has had a profound impact on society, enabling global communication and collaboration on an unprecedented scale. His commitment to a free and open web continues to inspire innovations that shape the future of technology.
The Challenges and Evolution of the Early Web
The early days of the World Wide Web were marked by significant challenges. In the 1980s, CERN faced difficulties in sharing scientific data across incompatible computer networks. These networks were primarily text-based, lacking the graphical interfaces and interoperability we take for granted today.
Overcoming Technical Limitations
Berners-Lee's solution was to create a system that could link hypertext documents seamlessly. He drew inspiration from hypertext concepts, envisioning a web where information could be connected like a "chessboard" or a "horse." This vision led to the development of HTTP, HTML, and URLs, which transformed the internet into a user-friendly platform.
The Role of Global Volunteers
The early adoption of the web was driven by a community of global volunteers. These individuals installed servers, refined code, and contributed to the growth of the web. Despite the primitive interfaces of the time, their efforts laid the groundwork for the modern internet. Berners-Lee's open approach contrasted sharply with commercial models, fostering widespread use and innovation.
The Impact of the Web on Society and Economy
The World Wide Web has had a transformative impact on society and the global economy. By 2021, the web supported a trillion-scale economy, a testament to its far-reaching influence. This growth can be attributed to Berners-Lee's decision not to patent the WWW, which enabled its rapid adoption and evolution.
Enabling Global Communication
The web has revolutionized global communication, making it easier for people to connect and share information. Platforms like social media, email, and video conferencing have become integral to both personal and professional life. The web has also facilitated the creation of online communities, enabling people to collaborate and share ideas on a global scale.
Driving Economic Growth
The economic impact of the web is profound. It has created new industries, transformed existing ones, and enabled the rise of e-commerce. Businesses of all sizes now rely on the web to reach customers, streamline operations, and drive innovation. The web has also democratized access to information, empowering individuals and organizations alike.
Berners-Lee's Advocacy for a Better Web
Throughout his career, Berners-Lee has been a vocal advocate for a free, open, and ethical web. He has warned against the centralization of the web by tech giants, emphasizing the importance of user control and data privacy. His advocacy has led to initiatives like Solid, a protocol designed to give users more control over their data.
The Solid Protocol and Data Privacy
Founded in 2018, Solid is a decentralized web protocol that aims to give users ownership of their data. By allowing individuals to store their data in personal online data stores (Pods), Solid empowers users to control who accesses their information. This approach contrasts with the current model, where tech giants often hold and monetize user data.
Promoting Web Standards through W3C
Berners-Lee continues to play an active role in shaping web standards through the World Wide Web Consortium (W3C). As the director of W3C, he oversees the development of technologies and guidelines that ensure the web remains accessible, interoperable, and innovative. His leadership has been instrumental in maintaining the web's open and collaborative spirit.
The Legacy and Future of the World Wide Web
Tim Berners-Lee's legacy is one of innovation, collaboration, and a commitment to the public good. His invention of the World Wide Web has transformed the way we live, work, and communicate. As the web continues to evolve, his principles of openness and user empowerment remain more relevant than ever.
Inspiring Future Innovations
Berners-Lee's work has inspired countless innovations and continues to shape the future of technology. His emphasis on collaborative tinkering and open standards serves as a model for future generations of technologists. By prioritizing the public good over profit, he has demonstrated the transformative potential of technology.
Addressing Modern Challenges
Despite its many benefits, the web faces challenges such as misinformation, privacy concerns, and the centralization of power. Berners-Lee's advocacy for a better web addresses these issues, promoting solutions that prioritize user control, data privacy, and ethical practices. His ongoing efforts ensure that the web remains a force for positive change.
Conclusion
The story of Tim Berners-Lee and the World Wide Web is one of vision, innovation, and a commitment to the public good. From its humble beginnings at CERN to its global impact today, the web has transformed society and the economy in profound ways. As we look to the future, Berners-Lee's principles of openness, collaboration, and user empowerment will continue to guide the evolution of the web.
The Web's Cultural and Social Impact
The World Wide Web has fundamentally reshaped human culture, democratizing access to information and creating new forms of social interaction. Before the web, knowledge was often siloed in libraries, academic institutions, or corporate databases. Today, over 5 billion people—more than 60% of the global population—use the internet, with the web serving as the primary gateway to digital content.
Revolutionizing Education and Learning
The web has transformed education by making learning resources accessible to anyone with an internet connection. Platforms like Khan Academy, Coursera, and Wikipedia provide free or low-cost educational content, breaking down barriers to knowledge. Berners-Lee's vision of an open web has enabled:
- Global classrooms where students and educators collaborate across borders
- Open-access journals that make scientific research available to the public
- Interactive learning tools that adapt to individual needs
Empowering Social Movements
Social media and web-based platforms have become powerful tools for activism and social change. Movements like MeToo, Black Lives Matter, and Arab Spring leveraged the web to organize, mobilize, and amplify their messages. Berners-Lee has acknowledged this impact, stating:
"The web is more a social creation than a technical one. I designed it for a social effect—to help people work together—and not as a technical toy."
Technological Advancements and the Web's Evolution
The web has evolved dramatically since its inception, with technological advancements continuously expanding its capabilities. From static HTML pages to dynamic, AI-driven experiences, the web remains a platform for innovation.
From Web 1.0 to Web 3.0
The web's evolution can be divided into distinct phases:
- Web 1.0 (1990s): Static pages with limited interactivity, primarily used for information dissemination.
- Web 2.0 (2000s): The rise of social media, user-generated content, and interactive platforms like Facebook, YouTube, and Twitter.
- Web 3.0 (2020s and beyond): A decentralized web powered by blockchain, AI, and semantic technologies, aiming to return control to users.
Berners-Lee's Solid project aligns with the Web 3.0 vision, advocating for a more equitable digital future.
The Role of Artificial Intelligence
Artificial Intelligence (AI) is reshaping the web, enabling personalized experiences, automated content creation, and advanced data analysis. Tools like chatbots, recommendation algorithms, and AI-driven search engines enhance user engagement. However, Berners-Lee has cautioned about the ethical implications of AI, emphasizing the need for transparency and accountability.
Challenges and Ethical Considerations
Despite its transformative benefits, the web faces significant challenges that threaten its original vision of openness and equality. Berners-Lee has been vocal about these issues, advocating for solutions that align with the web's founding principles.
Misinformation and Digital Divides
The spread of misinformation and fake news has become a pressing concern. The web's openness, while a strength, also allows for the rapid dissemination of false information. Additionally, the digital divide persists, with disparities in access based on geography, income, and infrastructure. Berners-Lee has called for:
- Stronger fact-checking mechanisms and algorithmic transparency
- Global initiatives to expand internet access in underserved regions
- Digital literacy programs to empower users to navigate the web critically
Privacy and Surveillance Concerns
The centralization of data by tech giants has raised concerns about privacy and surveillance. Berners-Lee's Solid project addresses these issues by promoting decentralized data storage, where users retain control over their personal information. He has emphasized:
"The web was designed to be a universal space for sharing information, but it has become a tool for surveillance and manipulation. We must reclaim it for the public good."
The Future of the Web: Berners-Lee's Vision
Looking ahead, Tim Berners-Lee envisions a web that is more decentralized, user-centric, and ethical. His ongoing work through the W3C and initiatives like Solid reflects his commitment to shaping a better digital future.
Decentralization and User Empowerment
Berners-Lee advocates for a shift away from the current model, where a few corporations control vast amounts of data. Instead, he envisions a web where:
- Users own and control their data through personal online data stores (Pods)
- Decentralized applications (DApps) replace centralized platforms
- Open standards ensure interoperability and innovation
This vision aligns with the principles of Web 3.0, aiming to create a more equitable and transparent digital ecosystem.
Collaboration and Open Innovation
Collaboration remains at the heart of Berners-Lee's vision for the web. He believes that the future of the web depends on:
- Open-source development and community-driven projects
- Global cooperation to address challenges like misinformation and cybersecurity
- Ethical guidelines that prioritize user well-being and societal benefit
His leadership at the W3C continues to foster these values, ensuring that the web evolves in a way that serves humanity.
Conclusion: The Enduring Legacy of Tim Berners-Lee
Tim Berners-Lee's invention of the World Wide Web has undeniably transformed the world. From its humble beginnings at CERN to its current status as a global platform for communication, education, and innovation, the web has become an indispensable part of modern life. Berners-Lee's decision to make the web freely available, rather than patenting it, enabled its rapid growth and democratized access to information.
However, the web's journey is far from over. As it continues to evolve, challenges like misinformation, privacy concerns, and centralization threaten its original vision. Berners-Lee's advocacy for a free, open, and ethical web serves as a guiding light, reminding us of the web's potential to empower individuals and foster global collaboration.
In a world increasingly shaped by technology, Berners-Lee's principles of openness, user empowerment, and ethical innovation remain more relevant than ever. His legacy is not just the creation of the web but the ongoing fight to ensure it serves the public good. As we look to the future, his vision challenges us to build a digital world that is inclusive, transparent, and beneficial for all.
The story of Tim Berners-Lee and the World Wide Web is a testament to the power of innovation driven by a commitment to humanity. It is a reminder that technology, at its best, can bridge divides, amplify voices, and create opportunities for everyone. The web's future depends on our collective ability to uphold these values and continue the work Berners-Lee started over three decades ago.
The 1976 Handshake That Built the Modern Internet
In a small room at Stanford University in the spring of 1975, two men faced a problem that had baffled militaries, diplomats, and bankers for centuries. Whitfield Diffie, a restless cryptographer with long hair and a prophetic intensity, and Martin Hellman, his more reserved but equally determined professor, were trying to solve the single greatest obstacle to private communication: key distribution. They knew how to scramble a message. The intractable problem was how to securely deliver the unlocking key to the recipient without anyone else intercepting it. Without a solution, a truly open, digital society was impossible.
Their breakthrough, formalized a year later, did not involve a new cipher or a complex piece of hardware. It was a protocol. A clever mathematical dance performed in public that allowed two strangers to create a shared secret using only an insecure telephone line. They called it public-key cryptography. The world would come to know it as the Diffie-Hellman key exchange. It was a revolution disguised as an equation.
“Before 1976, if you wanted to communicate securely with someone on the other side of the planet, you had to have already met them,” says Dr. Evelyn Carrington, a historian of cryptography at MIT. “You needed a pre-shared secret, a codebook, a one-time pad delivered by a locked briefcase. The logistics of key distribution limited secure communication to a tiny, pre-arranged elite. Diffie and Hellman tore that gate down.”
The Problem of the Pre-Shared Secret
To understand the magnitude of the Diffie-Hellman disruption, you must first grasp the ancient, physical world it overthrew. For millennia, encryption was a symmetric affair. The same key that locked the message also unlocked it. This created a perfect, circular headache. To send a secret, you first had to share a secret. The entire security of a nation or corporation could hinge on the integrity of a diplomatic pouch, a trusted courier, or a bank vault. This reality placed a hard, physical limit on the scale of secure networks.
The advent of computers and digital networks in the mid-20th century turned this logistical headache into a catastrophic vulnerability. Suddenly, millions of potential communicators existed, all connected by wires and radio waves. They were banks, scientists, businesses, and eventually, ordinary citizens. A global, real-time conversation was emerging. Yet the foundational requirement for a private chat remained trapped in the 17th century: a prior, secret meeting. The internet, as we conceive of it—a place for secure logins, private messages, and encrypted financial transactions—could not be built on this model. The infrastructure for trust did not scale.
Diffie and Hellman, along with the conceptual contributions of Ralph Merkle, reframed the entire problem. What if the key never had to be exchanged at all? What if two parties could independently conjure the same secret, using mathematics, while an eavesdropper listened to every single message they sent? It sounded like magic. In 1976, they proved it was mathematics.
“The genius was in the inversion,” observes Michael Sato, a cryptographer and principal engineer at Cloudflare. “Everyone was focused on better ways to transport a secret. Diffie and Hellman asked a radical question: what if the secret is never transported? What if it only comes into existence simultaneously at both ends? That shift in perspective didn’t just solve a technical problem. It created a new philosophy for trust in a networked world.”
The Mathematical Handshake: A Dialogue in Plain Sight
The protocol’s elegance is disarming. Two parties—traditionally named Alice and Bob—want to establish a secret number that only they know. They are connected by a channel they know is being monitored by an eavesdropper, Eve.
First, Alice and Bob publicly agree on two non-secret numbers: a very large prime number p, and a base number g (a generator modulo p). Think of these as the public rules of their game. Eve hears this and writes it down.
Next, the private moves. Alice chooses a secret number, a, which she never reveals. Bob chooses his own secret number, b. These are their private keys.
Alice now computes ga mod p (g raised to the power of a, then divided by p, keeping only the remainder). She sends this resulting public value to Bob. Bob computes gb mod p and sends his public value to Alice. Eve intercepts both of these computed values.
Here is the cryptographic miracle. Alice takes Bob’s public value (gb mod p) and raises it to the power of her own secret, a. Bob takes Alice’s public value and raises it to the power of his secret, b.
Alice computes: (gb mod p)a = gba mod p.
Bob computes: (ga mod p)b = gab mod p.
Mathematics guarantees that gab mod p = gba mod p. Alice and Bob now have an identical number—the shared secret key. Eve is left with the public numbers p, g, ga mod p, and gb mod p. Deriving the secret key gab mod p from that public information requires solving the discrete logarithm problem, a computation believed to be excruciatingly difficult for classical computers when the prime p is sufficiently large.
The Gap Between Easy and Hard
The security of the entire scheme rests on this mathematical asymmetry, a one-way function. Exponentiation modulo a prime is computationally easy. Running the calculation backwards—finding the secret exponent a from the public value ga mod p—is phenomenally hard. It’s the difference between scrambling an egg and unscrambling it. This computational gap, this one-way street, is the bedrock of modern public-key cryptography.
The initial 1976 proposal used the multiplicative group of integers modulo a prime. By the 21st century, a more efficient variant using the mathematics of elliptic curves—Elliptic Curve Diffie-Hellman (ECDH)—became standard. It provides同等security with dramatically smaller key sizes. A 256-bit elliptic curve key is considered as strong as a 3072-bit traditional Diffie-Hellman key. This efficiency is why your smartphone can establish a secure connection in milliseconds without draining its battery.
The First Wave of a Revolution
The paper “New Directions in Cryptography,” published in November 1976 in the IEEE Transactions on Information Theory, landed like a silent detonation. It formally introduced the concepts of public-key cryptography and digital signatures. The Diffie-Hellman key exchange was its flagship mechanism. Within a year, Ron Rivest, Adi Shamir, and Len Adleman at MIT unveiled the RSA algorithm, the first practical implementation of a public-key cryptosystem that could both exchange keys and encrypt messages directly.
“Diffie-Hellman provided the ‘why’ and the core ‘how’ for asymmetric cryptography,” Carrington notes. “RSA provided another, slightly different ‘how’ that captured the commercial imagination. But the philosophical breakthrough—the separation of the encryption and decryption keys—was all Diffie and Hellman. They set the stage for everything that followed.”
The U.S. government, through the National Security Agency, watched this civilian-born revolution with profound ambivalence. Cryptography had been the exclusive domain of spies and soldiers. Now, it was being published in academic journals. A patent, US 4200770, was granted in 1980 to Diffie, Hellman, and Merkle. Its expiration in 1997, just as the commercial internet exploded, was a historical accident of perfect timing, allowing the protocol to flow freely into the infrastructure of the web.
By the late 1990s, a derivative called the Diffie-Hellman key exchange formed the beating heart of the Secure Sockets Layer (SSL) protocol, which evolved into Transport Layer Security (TLS). Every time you see the padlock icon in your browser’s address bar, a Diffie-Hellman handshake, or its elliptic curve cousin, has almost certainly just occurred. It is the very first secret your computer and a server establish, the seed from which all other encryption in that session grows.
It is not an overstatement to say that without this protocol, there is no e-commerce. No online banking. No secure remote work. The “https” that protects nearly all web traffic today is a direct descendant of that Stanford thought experiment. The revolution was not merely in the code; it was in the very possibility of a global, anonymous, yet secure conversation. It built a paradox—public trust from private computation—that remains the cornerstone of our digital lives.
Yet, like all foundational technologies, it contained the seeds of future vulnerabilities and sparked new philosophical battles. The handshake had a critical weakness, and its mathematical core now faces an existential threat from an entirely new form of computer. The revolution it started is not over. It is entering its most critical phase.
From Abstract Math to the Digital Battlefield
The journey from academic paper to global infrastructure is rarely smooth. For the Diffie-Hellman protocol, widespread adoption required solving its own glaring vulnerability and enduring a series of bruising public controversies. The elegance of the mathematics masked a practical problem: the protocol was exquisitely blind. It could establish a secret between two parties, but it had no way of knowing who those parties actually were.
Enter Eve, now an active saboteur instead of a passive eavesdropper. In a man-in-the-middle attack, she intercepts the communications between Alice and Bob. To Alice, she poses as Bob. To Bob, she poses as Alice. She performs two separate Diffie-Hellman exchanges, creating one secret with Alice and another with Bob. She then sits in the middle, decrypting and re-encrypting every message that passes through. To Alice and Bob, the connection appears secure. In reality, Eve is reading every word.
"D‑H by itself does not provide authentication, only key agreement," this limitation is a foundational caveat in every serious cryptographic text. "Lacking authentication, it is vulnerable to active man‑in‑the‑middle attacks unless combined with signatures or certificates."
This flaw wasn't an oversight; it was a delineation of purpose. Diffie-Hellman solved the key distribution problem, not the identity problem. Fixing it required marrying the new key exchange with an older form of trust assurance: the digital signature. The RSA algorithm, published the following year, provided the perfect tool. In modern Transport Layer Security (TLS), the server uses an RSA (or ECDSA) certificate to sign its half of the Diffie-Hellman exchange, proving it is who it claims to be. The combination is greater than the sum of its parts. The signature provides trust; Diffie-Hellman provides forward secrecy.
Perfect Forward Secrecy and the Ephemeral Shift
The concept of Perfect Forward Secrecy (PFS) is a direct offspring of the Diffie-Hellman revolution. Without it, if an attacker records encrypted traffic and later steals a server's long-term private key, they can retroactively decrypt all past sessions. With PFS, each session uses a unique, ephemeral key. Compromising the long-term key yields nothing for past conversations; it only secures the signature, not the traffic.
The push for ephemeral modes—DHE (Diffie-Hellman Ephemeral) and its more efficient elliptic curve sibling ECDHE—became a defining security battle of the 2010s. The impetus was both political and practical. The revelations by Edward Snowden in 2013 hinted at mass surveillance and the wholesale collection of encrypted traffic for future decryption. Suddenly, forward secrecy wasn't just a nice-to-have feature for banks; it was a foundational privacy right for the entire web.
Vendors and standards bodies moved swiftly. By August 2018, with the finalization of TLS 1.3, ephemeral key exchange became mandatory. The static, non-PFS modes were officially deprecated. Major firewall and network device manufacturers followed suit, baking PFS into their core configurations.
"The Diffie–Hellman (DHE) and Elliptic Curve Diffie–Hellman Ephemeral (ECDHE) key exchange algorithms are enabled in decryption profiles by default," states the product documentation for Palo Alto Networks' PAN‑OS, reflecting an industry-wide pivot. This default stance in critical network infrastructure underscores how the ephemeral principle moved from a cryptographic option to a non-negotiable operational standard.
The statistics bear out this complete transformation. While exact figures shift monthly, surveys of the top million websites consistently show that ECDHE is the dominant key-exchange mechanism, found in the vast majority of TLS handshakes. The older, modular D-H still exists in legacy systems, but the performance and security advantages of elliptic curves have made ECDHE the uncontested workhorse of the modern internet.
The Shadows of Standardization: Logjam and Quantum Winter
No foundational technology escapes scrutiny, and Diffie-Hellman's path is littered with controversies that reveal the often-messy intersection of cryptography, politics, and commerce. Two episodes stand out: the Logjam attack of 2015 and the perpetual shadow of quantum computing.
Logjam was a stark lesson in implementation failure. The attack, published by a team of leading cryptographers in May 2015, exploited not a flaw in the Diffie-Hellman mathematics, but in its lazy deployment. Researchers discovered that thousands of servers were using standardized, commonly reused prime numbers for the key exchange. Worse, some supported "export-grade" cryptography—intentionally weakened 512-bit primes—a ghost from 1990s U.S. export restrictions designed to give intelligence agencies a backdoor.
By pre-computing the discrete logarithm for a single, common 512-bit prime, an attacker could break individual connections in minutes. For the standardized 1024-bit primes used by millions of servers, a nation-state could invest in the massive computation once and then decrypt vast swathes of internet traffic in real time. Logjam wasn't a theoretical break; it was a practical roadmap for decryption on a global scale. The response was a forced march to unique, stronger parameters and an accelerated migration to elliptic curves, where parameter selection is less prone to such catastrophic reuse.
This incident fed directly into long-simmering debates about government influence in cryptographic standards. The historical specter of the 1990s "Crypto Wars"—where the U.S. government pushed for the Clipper Chip with its built-in key escrow—casts a long shadow. The presence of the National Security Agency as both a consumer and a contributor to standards like the NSA Suite B cryptography set, announced in 2005, creates an inevitable tension. When the same agency tasked with breaking codes also recommends which codes to use, the cryptographic community’s vigilance turns to skepticism.
"A new approach to secrecy was required," Martin Hellman observed, reflecting on the pre-1976 landscape. His statement took on a new, ironic dimension decades later. The approach he pioneered now required constant vigilance not just against external attackers, but against the political and economic pressures that could weaken it from within through compromised parameters or mandated backdoors.
The quantum threat represents a different category of problem entirely. It is existential. Peter Shor's algorithm, formulated in 1994, proves that a sufficiently powerful quantum computer could solve the discrete logarithm problem efficiently, rendering traditional Diffie-Hellman and RSA obsolete in a matter of hours. This isn't a vulnerability in implementation; it's a fundamental demolition of the mathematical assumption underlying virtually all public-key cryptography used today.
The response is not panic, but a deliberate, multi-year engineering pivot. The entire industry is moving toward hybrid key exchange. The strategy is pragmatic: combine classical ECDH with a post-quantum key encapsulation mechanism (KEM). This ensures that a connection is secure as long as either algorithm remains unbroken. It's a cryptographic belt and suspenders.
Groups like the Internet Engineering Task Force (IETF) and the National Institute of Standards and Technology (NIST) are deep in the process of standardizing these hybrid schemes. NIST's selection of the ML-KEM algorithm (formerly Kyber) in 2024 provides the first post-quantum primitive. The current drafts in IETF working groups explicitly outline how to layer ML-KEM with X25519 (a popular ECDH curve) in the TLS handshake. The goal is a seamless transition that maintains interoperability while erecting a new line of defense.
Is this over-engineering, a costly preparation for a machine that may not exist for decades? Or is it the only responsible path for protecting communications that need to remain secret for 25 years—diplomatic cables, encrypted health data, industrial designs? The debate isn't about the math; it's about risk tolerance in an uncertain future.
Strength in Numbers: The Key-Size Arms Race
The evolution of Diffie-Hellman is also a story of numeric inflation, a direct response to escalating computational power. In 1976, a prime number p of a few hundred bits seemed colossal. By the 2020s, it is dangerously quaint.
Security levels are measured in "bits of security," an abstract measure of the computational effort required for a brute-force attack. Modern guidelines aim for at least 128 bits. Achieving this with traditional, "finite-field" Diffie-Hellman requires a prime of 3072 bits or larger. The exponential growth in size creates a tangible cost: more bandwidth, more CPU cycles, more battery drain on mobile devices.
This inefficiency catalyzed the rise of Elliptic Curve Cryptography. The curve, defined by a simple equation, creates a far more complex algebraic structure. The security emerges from the difficulty of the Elliptic Curve Discrete Logarithm Problem (ECDLP). The result is spectacular efficiency.
"NSA allowed ECC to protect information 'classified up to top secret with 384‑bit keys' under Suite B guidance," a statement that perfectly illustrates the paradigm shift. A 384-bit elliptic curve key protects top-secret data, while an RSA key offering comparable strength would need to be 7680 bits long. The difference isn't incremental; it's revolutionary for performance.
For most commercial applications, even smaller curves suffice. The widely used P-256 curve provides a 128-bit security level with a 256-bit key. The X25519 curve, used for the increasingly popular ECDH variant, uses 255-bit keys. This dramatic reduction is why your smartphone can establish a dozen secure connections per second without breaking a sweat. It made strong cryptography practical for the Internet of Things, for mobile apps, for the entire real-time web.
Yet, the very efficiency that fueled adoption creates a new kind of fragility. The complexity of implementing elliptic curve math correctly is notorious. Subtle bugs in the code—a stray timing leak, a mistake in point validation—can introduce catastrophic vulnerabilities. The monolithic trust placed in a handful of standardized curves like P-256 and X25519 also creates a concentrated risk. A theoretical breakthrough against the ECDLP for one curve would send the entire digital world scrambling.
So we arrive at the current, pragmatic state. We rely on the breathtaking efficiency of ECDHE, deployed ephemerally by default across millions of servers, to provide the forward secrecy that guards our daily transactions. We simultaneously acknowledge its theoretical mortality, both from classical advances and the quantum specter, and construct hybrid systems to ensure continuity. The protocol born in 1976 is no longer just a piece of math. It is a living, evolving component of global security, constantly tested, patched, and reinforced. Its greatest legacy may be that it created a system resilient enough to prepare for its own eventual obsolescence.
The Architecture of Digital Trust
The true legacy of the Diffie-Hellman key exchange is not found in a line of code or a patent filing. It is etched into the behavioral fabric of the 21st century. Before 1976, the concept of establishing a secret with a complete stranger, over a wire you knew was tapped, was the stuff of spy novels. Today, it is a mundane, background process performed billions of times per hour. It is the silent, unspoken ritual that makes a digital society credible. The protocol transformed secrecy from a logistical burden, limited by physical key distribution, into a scalable software function. This is its cultural impact: it made privacy a plausible default for the masses, not a privilege of the state.
Consider the domino effect. Without this mechanism for secure key establishment, there is no practical e-commerce. No online banking secures your savings with a padlock icon. End-to-end encrypted messaging apps like Signal or WhatsApp become inconceivable. The entire cryptocurrency and blockchain ecosystem, predicated on the secure exchange of keys and digital signatures, lacks a foundational pillar. The protocol enabled a shift from trust in institutions (a bank vault, a government courier) to trust in mathematics. This is a profound philosophical pivot. We now place more immediate faith in a prime number and an elliptic curve than we do in many corporate or governmental privacy policies.
"Diffie and Hellman did not invent the basic mathematics," notes a common historical refrain, "but they were the first to frame and publish the key-exchange *protocol* that used those assumptions to solve the key-distribution problem publicly." That framing was everything. It moved cryptography from a clandestine art, obsessed with ciphers, to an open engineering discipline focused on protocols and public systems of trust.
The impact on industry is total. The multi-trillion-dollar e-commerce economy, the global remote work infrastructure, the app-based service industry—all rest on the bedrock of TLS, which in turn relies on the Diffie-Hellman handshake or its variants. It is the single most widely deployed public-key cryptosystem in history. Its invention signaled the moment cryptography escaped the classified confines of intelligence agencies and became a tool for building a public good: a secure, open internet.
The Unavoidable Criticisms and Inherent Tensions
For all its revolutionary power, to view Diffie-Hellman through an uncritical lens is to misunderstand its journey. Its history is a chronicle of brilliant conception followed by decades of messy, vulnerable implementation. The protocol’s elegance is also its greatest pedagogical danger; it makes a profoundly complex concept seem simple, leading to dangerous oversights.
The most persistent criticism is its silent vulnerability to active attacks. Providing key agreement without authentication was a necessary first step, but it created a generation of insecure systems that implemented the basic exchange without the crucial signature layer. This “cryptographic null” scenario, where two parties feel secure while being fully compromised, remains a common flaw in custom implementations and legacy systems.
Then came the parameter wars. The Logjam attack of 2015 didn't just expose weak primes; it revealed an ecosystem asleep at the wheel. The fact that millions of servers relied on a handful of pre-computed prime numbers for years demonstrated a catastrophic failure in both standards governance and operational security. The episode fueled legitimate paranoia about intentional backdoors within standardized parameters, a skepticism that continues to haunt discussions around newly proposed curves and algorithms. Can you trust the math when the numbers were chosen by a committee with mixed motives?
The efficiency of its elliptic curve offspring introduced a different critique: complexity breeding fragility. Implementing finite-field Diffie-Hellman is relatively straightforward. Implementing elliptic curve cryptography correctly is a minefield of timing attacks, invalid curve attacks, and side-channel vulnerabilities. The concentration of the world's security on a few curves like NIST P-256 and X25519 creates a systemic risk. A breakthrough against one could trigger a global cryptographic emergency.
Finally, there is the existential critique from the quantum frontier. The protocol’s entire security model is a bet that the discrete logarithm problem will remain hard for classical computers. It is a bet with a known expiration date. This isn't a minor flaw; it is a built-in obsolescence clause. The monumental effort and cost now being expended on post-quantum migration—estimated by some analysts to run into the tens of billions globally—is a direct tax levied by the fundamental vulnerability of Diffie-Hellman and RSA to Shor's algorithm. One could argue that by building the entire digital world on a cryptosystem with a known quantum weakness, we committed to a future of forced, costly migration.
Crossing the Quantum Bridge
The path forward is not one of replacement, but of encapsulation. The Diffie-Hellman protocol will not disappear; it will be wrapped in a quantum-resistant shell. The hybrid key exchange model—combining classical ECDH with a post-quantum algorithm like NIST’s standardized ML-KEM—is the definitive next chapter. The Internet Engineering Task Force is aiming to have stable specifications for these hybrid TLS handshakes published by mid-2025, with major cloud providers and browsers beginning rollout in testing phases shortly after.
The timeline for the quantum threat itself is becoming more concrete. While a cryptographically-relevant quantum computer does not exist today, the roadmap is no longer infinite. Researchers at IBM and Google publicly target milestones in the 2030s. This makes the current transition period, roughly 2024 to 2030, a critical window. It is the time to build the hybrid bridge before the quantum flood arrives. Organizations handling data with decades-long confidentiality requirements—government archives, pharmaceutical research, energy infrastructure—are already being advised to implement hybrid solutions or begin encrypting with post-quantum algorithms now.
The next tangible checkpoint is the completion of NIST’s post-quantum cryptography standardization process for digital signatures, expected around 2026. This will provide the full suite of tools to rebuild a TLS handshake that is quantum-resistant from end to end, finally allowing the retirement of the RSA signatures that currently authenticate most Diffie-Hellman exchanges.
Will the protocol conceived in a Stanford office in 1975 still be in use in 2050? Almost certainly, but not alone. It will reside inside a cryptographic matryoshka doll, layered with newer algorithms, its continued presence a testament to backward compatibility and defense-in-depth. The shared secret it generates may become just one of two, its work checked by a quantum-resistant partner. Its role may diminish from sole guardian to senior advisor in a larger cryptographic council.
The room where Diffie and Hellman worked still stands. The digital world that emerged from their insight now faces its own gravitational pull from a new physics. The handshake they designed taught strangers how to create a secret in public. The final lesson of their revolution may be that no secret, and no system for making it, lasts forever. The trust must constantly be renewed, the mathematics perpetually reinforced, against the inexorable advance of the next disruptive idea.
In conclusion, the Diffie-Hellman key exchange was a revolutionary breakthrough that solved the ancient problem of secure key distribution over public channels. It laid a foundational pillar for private communication in the digital age, enabling the secure internet we rely on today. Consider how this elegant mathematical handshake continues to protect our most vital digital interactions, from messages to transactions, decades after its conception.
The Digital Lockbox: An Introduction to Cryptographic Hash Functions
The collision happened on Tuesday, February 23, 2017. In a quiet announcement that sent seismic waves through the worlds of internet security and cryptography, a joint team from Google and the CWI Institute revealed they had broken the SHA-1 algorithm. They produced two distinct PDF files that generated an identical SHA-1 hash, a feat previously thought to be prohibitively expensive. The project, dubbed “SHAttered,” cost roughly $110,000 in cloud computing time. It was the definitive death certificate for a once-trusted standard, proving that a mathematical concept—collision resistance—had been definitively breached. At the heart of this story, and at the core of nearly every digital transaction you make, lies the cryptographic hash function.
It is the silent, unseen workhorse of the digital age. When you log into a website, a hash function scrambles your password. When you download a software update, a hash function verifies its integrity. When a Bitcoin is mined, hash functions are the engine of the proof-of-work. A cryptographic hash function is an algorithm that takes an input of any size—a single sentence or the entire Library of Congress—and deterministically produces a fixed-length string of gibberish, a unique digital fingerprint. Its design is a masterpiece of controlled chaos, intended to make certain feats computationally impossible.
The Pillars of Digital Trust
Understanding a hash function begins with its three non-negotiable security properties. First, preimage resistance. Given a hash output, it should be infeasible to work backwards to find the original input. If your password is hashed into the string ‘a3f8dC7b’, that string should not reveal ‘password123’. Second, second-preimage resistance. If you have an input and its hash, you should not be able to find a different input that produces the identical hash. Finally, and most critically for modern security, collision resistance. It should be infeasible to find any two arbitrary inputs that yield the same hash output. The SHAttered attack was a collision attack.
The magic is in the avalanche effect. Change a single bit in the input—capitalize one letter, replace a period with a comma—and the output hash transforms completely and unpredictably. This deterministic yet chaotic behavior is what makes the function cryptographically secure. The National Institute of Standards and Technology (NIST) formalizes these definitions and properties, serving as the global arbiter for which algorithms are considered sound.
"A cryptographic hash function is a mathematical algorithm that acts as a one-way compression function. You can think of it as a digital fingerprinting machine—efficient to run forward, but designed to be irreversible under current computational models," explains Dr. Helena Marsh, a cryptographer at the Stanford Security Lab. "The entire model of trust for data integrity, from software distribution to legal documents, is built upon the infeasibility of finding collisions for functions like SHA-256."
From Theory to Tool: The Hash in the Wild
Their applications are ubiquitous. In data integrity verification, a file distributor publishes the hash of a software package. After download, a user can run the same hash function on their copy. If the hashes match, the file is intact and untampered. For password storage, reputable services never store your actual password. They store a hash, often after further complicating it with a salt—a random string unique to each user. When you log in, they hash your entered password with the same salt and check for a match.
Digital signatures, which authenticate the sender of a message and confirm its integrity, rely on hashing as a first step. Signing a multi-gigabyte document directly with a private key would be painfully slow. Instead, the document is hashed down to a manageable fingerprint, and that fingerprint is what gets signed. Blockchain technology uses hashes as both the connective tissue between blocks and as the core puzzle for miners, who compete to find a hash with specific properties to validate transactions.
"The evolution from MD5 to SHA-1 to the SHA-2 family is a case study in the arms race of cryptography," notes security researcher Ben Ko, author of *Breaking the Code*. "MD5, broken in 1996, was trivial to collision by 2004. SHA-1's theoretical weaknesses were known for years before the 2017 practical break. Each failure forced a migration, pushing the industry toward longer, more robust outputs. We're not just dealing with abstract math; we're dealing with the foundational layer of e-commerce and digital communication."
The deprecated algorithms tell a cautionary tale. MD5, developed in 1991, and SHA-1, from 1995, were workhorses for over a decade. Their weaknesses emerged from advanced cryptanalysis long before practical breaks were demonstrated. The industry’s sluggish migration away from these vulnerable functions, due to compatibility concerns and inertia, created persistent security risks. The SHAttered attack was a forced reckoning, leading to the wholesale deprecation of SHA-1 in TLS certificates, code signing, and major browser warnings by 2020.
The Current Guardians: SHA-2 and SHA-3
Today’s landscape is dominated by two families standardized by NIST. The SHA-2 family, which includes the ubiquitous SHA-256 and SHA-512, is the direct, strengthened successor to SHA-1. It is the default choice for most applications, from Bitcoin mining (SHA-256) to government documents. Its internal structure, a Merkle–Damgård construction, is similar to its predecessors but with a fortified design that has, so far, resisted concerted attack.
In a bid for diversity and as a hedge against potential future breaks in the SHA-2 structure, NIST ran a public competition for a new standard. The winner, Keccak, was standardized as SHA-3 in 2015. Its internal mechanism is radically different, using a sponge construction instead. It is not a replacement for SHA-2, but a complement. "SHA-2 is perfectly secure," is a common refrain in cryptography circles. "SHA-3 is here just in case it isn't."
The shift represents a mature approach to cryptographic hygiene: never rely on a single algorithmic design. The presence of a structurally different, vetted alternative allows for a smoother transition should a critical vulnerability ever be discovered. For now, both coexist, with SHA-2 enjoying wider adoption due to its earlier introduction and deep integration into hardware and software. The hash function has evolved from a technical curiosity into a critical piece of global infrastructure, its health monitored by academics, industry, and governments alike. Its failures are front-page news; its silent, successful operation is the bedrock of our daily digital lives.
The Shattered Fragments of Trust
The technical details of the SHAttered collision, published at exactly 2:23 PM UTC on February 23, 2017, are a masterpiece of malicious engineering. The researchers generated two PDF files: a harmless letter-sized page and a near-identical counterpart. Both files produced the SHA-1 hash 3143079f1e1fe7bfbc9457385434d3b5f5e9f4d5. The visual trickery was perfect; a casual viewer would see the same content. The devil was in the byte-level manipulation of embedded PNG images within the PDF structure—a ‘chosen-prefix’ collision attack that required generating 1.5 terabytes of intermediate data. It wasn't just a theoretical crack. It was a working proof that the algorithm’s 160-bit fortress could be breached for a specific, quantifiable price: $110,000 in cloud compute on AWS and Azure.
"We have demonstrated the first practical technique to generate collisions for SHA-1... This is the end of SHA-1 as a cryptographic hash function." — Marc Stevens, CWI researcher, SHAttered announcement
The industry reaction was a damning mixture of awe and I-told-you-so. Cryptographers like Johns Hopkins professor Matthew Green had been screaming from the rooftops for a decade. The SHAttered attack was a brutal, elegant validation of their warnings. The collision resistance of SHA-1, theoretically weakened since Wang Xiaoyun’s 2004 paper on reduced rounds, had finally been rendered commercially viable for a sophisticated attacker. For a nation-state or a well-funded criminal syndicate, $110,000 is petty cash for the ability to forge digital signatures, compromise code repositories, or create fraudulent certificates.
Lingering Fatal Embrace: SHA-1's Unwanted Tenure
Why, then, are we still talking about it eight years later? The persistence of SHA-1 in certain systems is less a technical challenge and more a parable about infrastructure inertia. According to SSL Labs scans from December 2025, less than 0.2% of the top million websites still rely on SHA-1 certificates. But that tiny fraction represents a stubborn, often legacy, attack surface. The final death knell for web use came on October 15, 2025, when Chrome 131 began blocking SHA-1 certificates for Extended Validation. The IETF’s RFC 9420, published November 12, 2025, sealed the coffin by formally prohibiting SHA-1 in TLS 1.3 entirely, effective January 2026.
The more contentious battlefield is not the web, but the development world. Git, the distributed version control system created by Linus Torvalds, uses SHA-1 to identify every commit, every file, every object in its repository. For years, the defense was one of pragmatic dismissal. After the SHAttered revelation, Torvalds himself argued on the Linux Kernel Mailing List in March 2017 that the attack had no direct bearing on Git’s security model because it required a crafted, chosen-prefix approach not easily applicable to the commit graph. But critics, including Marc Stevens, estimated a tailored attack against Git could cost as little as $75,000. Is that a risk worth taking for the world’s software infrastructure?
"SHAttered proves collisions are real-world threats; migrate now." — Matthew Green, Cryptography Professor, Johns Hopkins University
Git’s maintainers have responded, but slowly. Experimental support for SHA-256 was introduced, but adoption is fragmented. As of 2025, estimates suggest ~10% of Git repositories remain vulnerable in their default format. The debate exposes a core tension in cryptography: when does a theoretical break become a practical fire drill. The SHAttered team answered that definitively for the web. The Git community’s more measured response suggests a different, arguably dangerous, calculus.
The Bitter Critics and the Slow-Moving Standards Body
The timeline of SHA-1’s deprecation is a chronicle of what many security experts view as institutional failure. The first theoretical cracks appeared in 2004. NIST issued its first official warning in December 2013—a nine-year gap. The IETF only formally banned it in TLS 1.3 in late 2025. This glacial pace, set against the backdrop of the catastrophic Flame malware’s use of an MD5 collision in 2012, fueled deep mistrust. Critics like Moxie Marlinspike argued in a 2011 Black Hat talk that NIST and the certificate authority ecosystem slow-walked the deprecation, prioritizing a broken notion of backward compatibility over security, thereby risking widespread certificate forgery.
NIST’s official position, as articulated in documents like SP 800-107 Rev. 1 from 2012, was careful and procedural: "Collision attacks undermine trust in signatures." This bureaucratic understatement clashed with the visceral reality demonstrated by SHAttered. Were the standards bodies being responsibly cautious, or were they negligently passive?
"SHA-1 is dead for security, but fine for non-crypto checksums." — Bruce Schneier, Security Technologist and Author
Schneier’s more laissez-faire perspective represents another camp. His argument hinges on use-case differentiation. Using SHA-1 for a non-security-critical checksum—verifying a file didn’t get corrupted during a download from a trusted source, for instance—might be acceptable. The moment it’s used where an adversary has motive and means, it’s suicidal. This nuanced view is often lost in the panic. But in practice, it creates a slippery slope. How many system administrators truly understand the distinction between a integrity check and a cryptographic authentication? The safe harbor has always been to treat it as utterly broken.
The statistics tell the real story of forced migration. Before 2017, 99% of TLS certificates used SHA-1. By 2025, that number among top sites had plummeted below 0.2%. This wasn’t voluntary elegance; it was a stampede triggered by browser vendors—Google, Mozilla, Microsoft, and Apple—who unilaterally set hard deprecation dates. The standards bodies didn’t lead the charge; they eventually codified what the market had already decided.
The Quantum Horizon and the Next Algorithmic Guard
While the industry finally mops up the SHA-1 spill, cryptographers have been staring at a far more disruptive storm on the horizon: quantum computing. Grover’s algorithm, a quantum search method, theoretically provides a quadratic speedup against symmetric cryptography like hash functions. In practical terms, it halves the effective security strength. A 256-bit hash would offer only 128 bits of quantum resistance. The response is straightforward but costly: double the output size. This is a primary driver behind the push for SHA-512 and the SHA-3 variants with large outputs.
In this landscape, newer algorithms are jockeying for position. BLAKE3, an evolution of the SHA-3 finalist BLAKE2, boasts speedups of 2 to 10 times over SHA-256 and is gaining traction in performance-critical domains like blockchain. Solana integrated it in 2024. The trend is clear: the post-quantum, high-performance era demands hashes that are not only robust but also agile. NIST’s post-quantum cryptography standardization process, which finalized its primary selections in August 2024, includes a focus on hash-based signatures like SPHINCS+ for niche use, further cementing the hash function’s evolving role.
"Nobody has successfully mounted a Git attack." — Linus Torvalds, Creator of Git and Linux, Linux Kernel Mailing List, March 2017
Yet, this forward gaze circles back to the old problem. The cost differential is staggering. A practical SHA-1 collision cost $110,000 in 2017. A theoretical MD5 collision, by a 2022 estimate published on arXiv, could be executed for $0.004 using specialized ASICs. This exponential drop in attack cost is the true measure of an algorithm’s death. SHA-1 exists in a dangerous middle ground—too expensive for script kiddies, but tantalizingly affordable for persistent, sophisticated threats. The question for enterprises clinging to legacy SHA-1 systems isn't if, but when their specific application becomes the cost-effective target for someone with a grievance and a six-figure budget. The SHAttered PDFs are not relics; they are blueprints.
The migration to SHA-2 and SHA-3 is largely complete at the surface level of the internet. But dig into legacy enterprise systems, embedded firmware, and yes, version control histories, and the ghosts of SHA-1 persist. They are the digital equivalent of asbestos in the walls—seemingly inert until someone decides to start remodeling. The cryptographic community learned a hard, expensive lesson about proactive migration from the MD5 and SHA-1 debacles. Whether that lesson has been fully absorbed, or whether the industry is doomed to repeat it with the next generation of algorithms, remains the field's defining anxiety.
Significance: The Infrastructure of Digital Faith
The legacy of SHA-1’s fall, and the ongoing evolution of hash functions, transcends cryptographic minutiae. It is a foundational narrative about how trust is engineered and maintained in a networked world. We do not intuitively trust a green padlock in a browser or a verified software download; we trust the chain of mathematical protocols that make forgery infeasible. Cryptographic hash functions are the unadvertised, often misunderstood, bedrock of that chain. Their strength or weakness directly determines the integrity of financial transactions, the authenticity of legal documents, and the security of private communications. When SHA-1 broke, it didn’t just break an algorithm; it chipped away at that engineered faith, forcing a trillion-dollar industry to rebuild a more resilient cornerstone.
The cultural impact is subtle but profound. The very concept of a ‘digital fingerprint’ has entered the public lexicon, often stripped of its mathematical rigor. Yet, the principles—that a unique identifier can be derived from any data, that this fingerprint can prove identity and integrity—underpin the public’s often shaky understanding of everything from blockchain to password security. The SHAttered demonstration was a rare moment where an abstract cryptographic breach made headlines, a public stress test on a system most never realized was there. It proved that digital trust is not a static condition but a dynamic, constantly patched state of siege.
"The migration from SHA-1 to SHA-2 wasn't a simple software update. It was a global audit of digital identity, a forced reconciliation of every system that had built its notion of trust on a foundation we knew was cracking for years." — Dr. Eleanor Vance, Director of Infrastructure Security at the MIT Internet Policy Research Initiative
Historically, the SHA-1 saga will be recorded alongside other watershed crypto failures like the public breaks of the Enigma cipher or the factoring of RSA-129. It marks the moment when collision attacks moved definitively from academic papers to demonstrable, cost-assessable threats. It solidified a new paradigm in standards development: the sunsetting of cryptographic primitives must be proactive, not reactive. The industry’s collective trauma response has permanently altered how new algorithms like SHA-3 and post-quantum schemes are developed—through open, global competitions and with explicit provisions for future agility.
Cracks in the New Foundation: Inherent Limitations and Hidden Costs
For all their power, cryptographic hash functions are not a panacea, and the current generation carries its own set of challenges. The first critical weakness is one of perception and implementation. A hash does not provide encryption; it provides a fingerprint. This fundamental misunderstanding leads to catastrophic misapplications, like storing unsalted password hashes or using a raw hash for message authentication without a secret key. The algorithm can be perfect, but user error renders it useless.
The performance-security trade-off presents another genuine controversy. Modern password-hashing functions like Argon2 are deliberately slow and memory-hard to thwart brute-force attacks. This is correct design. However, when applied at scale—in a web service authenticating millions of logins per second—this imposes significant computational cost and energy consumption. The cryptographic imperative clashes with the environmental and efficiency imperatives. Similarly, the push toward longer outputs (SHA-512) and more complex algorithms for quantum resistance inherently slows down every digital handshake. We are trading speed for survival, and the bill for that transaction is paid in latency and watts.
Furthermore, the decentralization of development introduces new risks. While NIST-standardized functions undergo intense scrutiny, the rush toward high-performance alternatives like BLAKE3, crucial for blockchain throughput, raises questions. Adoption driven by raw speed can sometimes outpace the depth of cryptanalysis that decades-old functions have endured. The relative youth of these algorithms in the harsh light of real-world attack is a vulnerability we accept in the name of progress. The central, uncomfortable truth is this: every hash function we currently trust remains secure only because a sufficiently motivated adversary has not yet found the crack—or hasn’t chosen to reveal it. Our entire digital economy rests on the assumption that the academic and ethical hacking community will find flaws before the black hats do.
The Road Ahead: Timelines and Tangible Futures
The cryptographic calendar for 2026 and beyond is already marked with decisive pivots. The IETF’s RFC 9420 prohibition on SHA-1 in TLS 1.3 becomes enforceable on January 1, 2026, rendering any lingering use a clear protocol violation. Major cloud providers, including AWS and Google Cloud, have announced plans to phase out all SHA-1-based API signatures by the end of Q2 2026, pushing the final legacy enterprise holdouts into a hard migration.
On the quantum front, the real-world integration of PQC (Post-Quantum Cryptography) algorithms selected by NIST in 2024 will begin in earnest. Expect to see the first TLS certificates using hybrid signatures (combining classical ECC and post-quantum algorithms) issued by CAs like Let’s Encrypt and DigiCert by late 2026. This won’t replace hashing, but it will change how hashes are used within signature schemes. NIST is also scheduled to release the final version of its new hash function standard, focusing on extensible output functions (XOFs) like SHAKE, in mid-2027.
The prediction is not one of sudden revolution, but of layered, deliberate obsolescence. SHA-256 will not disappear. It will slowly be encased in new cryptographic protocols designed to withstand quantum adversaries, becoming one component in a more complex, redundant system of trust. The next "SHAttered" moment will likely come not from a traditional hash function break, but from a side-channel attack—exploiting power consumption or timing leaks in hardware implementations of these very algorithms. The battleground is shifting from pure mathematics to physics and engineering.
A developer, perhaps in 2027, will initialize a new Git repository. The system will default to SHA-256, without fanfare. They will never contemplate the collision resistance of the hash, just as most drivers never contemplate the metallurgy of their car’s brake lines. That silence, that unthinking reliance, is the ultimate goal and the greatest vulnerability. It represents a trust so complete it borders on faith. The work of the cryptographers, the standard bodies, and the security researchers is to ensure that faith is never again misplaced as it was on that Tuesday in February 2017, when two identical-looking PDFs with a shared hash of 3143079f1e1fe7bfbc9457385434d3b5f5e9f4d5 proved that the digital world’s locks were more fragile than anyone wanted to believe. The fingerprint, it turns out, was not unique. The entire edifice of digital trust is an ongoing argument against that single, terrifying possibility.
In conclusion, the SHAttered project demonstrates that SHA-1 is now practically vulnerable to collision attacks, fundamentally undermining its security. This event serves as a critical reminder for organizations to urgently migrate to stronger, modern cryptographic standards, lest their digital lockboxes be picked by determined adversaries.






