Quantinuum's Quantum Leap: The $20 Billion IPO Filing Explained
The filing landed with the weight of a prophecy. On Wednesday, January 14, 2026, in a move telegraphed to the U.S. Securities and Exchange Commission before dawn touched the trading floors of Wall Street, a new contender for the future of computation took its first formal step into the public arena. Honeywell International, the 138-year-old industrial conglomerate, announced its majority-owned quantum computing subsidiary, Quantinuum, had confidentially submitted a draft registration for an initial public offering. The potential valuation whispered by sources close to the deal? Over $20 billion.
For a company with minimal revenue, nestled in a field where practical applications are still measured in laboratory breakthroughs, that number is either an act of supreme confidence or a spectacular gamble. It represents a doubling of the firm's worth in just four months. It would instantly crown Quantinuum as the largest pure-play quantum computing company by market cap. And it signals, more clearly than any press release ever could, that the era of quantum computing as a speculative science project is over. The build-out has begun, and the market is being asked to fund it.
"This isn't just another tech IPO. It's a bet on the underlying fabric of computation itself," said Dr. Elara Vance, a quantum information analyst at the Boston Consulting Group. "Honeywell isn't selling gadgets; they're selling a stake in a new physical paradigm. A $20 billion valuation tells you institutional investors are starting to believe the paradigm is real."
The Architect and the Engine: A Union Forged in Ambition
To understand Quantinuum's audacious move, you must rewind to November 2021. The quantum landscape was a fragmented mosaic of startups, tech giants, and national labs. In a decisive stroke, Honeywell Quantum Solutions—the group that had quietly developed what many experts considered the world's highest-fidelity trapped-ion quantum hardware—merged with Cambridge Quantum, a UK-based powerhouse in quantum software and algorithms. The new entity was christened Quantinuum. Honeywell contributed its exquisite machinery; Cambridge Quantum brought the intricate code to make it sing. It was a full-stack marriage of necessity and ambition.
The heart of Quantinuum's technical claim is the trapped-ion approach. While competitors like IBM and Google pursue superconducting loops that require temperatures colder than deep space, Quantinuum's processors use individual ytterbium atoms, suspended in a vacuum by electromagnetic fields and manipulated with lasers. The method is notoriously difficult to scale but offers unparalleled stability and precision. Qubits, the fundamental units of quantum information, are not created equal. Quantinuum bets that quality, for now, trumps sheer quantity.
By January 2026, the company was commercially offering its 32-qubit H2 processor through a platform named Helios. More telling than the qubit count was the software stack blossoming around it: open-source tools like the Guppy compiler and the Selene project. This was the Cambridge Quantum legacy in action, building the roads and traffic signals for a machine that operates on the bizarre rules of quantum mechanics.
The company operates globally, with several hundred employees split between the United States, the United Kingdom, Germany, and Japan. It is, in essence, a pre-revenue scientific juggernaut. Its customers are enterprises like JPMorgan Chase and Airbus, running early experiments on optimization and materials science problems that would choke a classical supercomputer. Revenue is a trickle. Belief is the currency.
"The confidential S-1 filing is a masterclass in optionality," notes financial journalist Mark Chen, who covers advanced technology markets for MarketWatch. "Honeywell gets to test the waters without showing its cards. The 1.4% to 2.07% pop in Honeywell's stock that day tells you the street views this as value-unlocking, not a distraction. They see Quantinuum as a crown jewel they never knew Honeywell had."
A Conglomerate Unravels, A Future Spins Out
Quantinuum's IPO path is inextricably linked to the radical transformation of its corporate parent. Honeywell, under CEO Vimal Kapur, is executing a deliberate and dramatic breakup. In October 2025, it spun off its Solstice Advanced Materials unit. In the second half of 2026, it plans to separate its massive aerospace business. Quantinuum's proposed public offering is the third act in this strategic trilogy.
The message is stark: the age of the sprawling industrial conglomerate is fading. The future belongs to focused, agile, and publicly accountable pure-plays. For Honeywell, retaining majority ownership of Quantinuum allows it to keep a golden share in the quantum future while letting the subsidiary access the deep, voracious pools of capital in public markets. It can fund a war of attrition against better-capitalized rivals like Google and IBM. The $600 million venture round it closed just months before, with backing from Nvidia's venture arm, was a down payment. The IPO is the mortgage.
There is a palpable sense of momentum being harnessed. 2025 saw a surge in secondary offerings for quantum-adjacent firms. The hypnotic investor frenzy around artificial intelligence has spilled over, creating a receptive audience for stories about the next disruptive computational force. Quantum computing, with its potential to crack encryption, design miraculous molecules, and optimize global logistics, fits the narrative perfectly. Honeywell’s filing is an attempt to catch that wave at its crest.
Yet, for all the financial engineering and strategic positioning, the endeavor remains rooted in a laboratory in Broomfield, Colorado, or a software hub in Cambridge, England. It hinges on scientists maintaining the coherence of subatomic particles and developers writing code for machines whose full capabilities are still theoretical. The $20 billion question, literally, is whether the meticulous, painstaking work of trapped-ion physics can scale fast enough to meet the stratospheric expectations now baked into a hypothetical stock price. The S-1, when it eventually becomes public, will not have an answer for that. It will only have promises and risk factors. For now, the market is betting on the promise.
The Anatomy of a Quantum Bet: Scale, Skepticism, and the Trapped-Ion Edge
Numbers tell the story before the story is officially told. The confidential S-1 filing for Quantinuum on January 14, 2026, is a black box, but the figures swirling around it paint a portrait of audacious scale. A valuation leaping from $10 billion to a potential $20 billion+ in the span of a season. A targeted raise of approximately $1 billion. A workforce of over 630 employees, with more than 370 of them scientists and engineers. These aren't metrics for a startup; they are the vital signs of an enterprise preparing for a long and exorbitantly expensive war. The IPO is its war bond drive.
"The $20 billion figure isn't pulled from thin air. It's a direct reflection of the scarcity of full-stack, high-fidelity players with industrial pedigree. You're buying the Honeywell manufacturing discipline bolted onto quantum science," states Ravi Gopal, a deep-tech venture capitalist at SineWave Ventures. "But you're also buying a narrative. The market is pricing in a decade of dominance, today."
Quantinuum's core narrative is its technological differentiation. While the quantum spotlight often shines on the qubit-count race led by superconducting rivals, Quantinuum has staked its future on the precision of trapped-ion technology. It's a classic tortoise-versus-hare dynamic, but in a field where the racecourse is made of probabilistic uncertainty. The company's H-series processors, like the commercially available 32-qubit H2, trade sheer volume of qubits for lower error rates and longer coherence times. This is not a minor technical footnote; it is the central thesis of their entire valuation.
Can quality consistently defeat quantity? The competitive landscape offers a stark contrast. IonQ, the only other major public trapped-ion pure-play, carries a market cap roughly one-tenth of Quantinuum's proposed valuation. Superconducting competitor Rigetti struggles to maintain a valuation above a few hundred million. Quantinuum's projected worth implies a belief that its Honeywell-forged hardware, combined with the sophisticated software lineage of Cambridge Quantum, creates a moat too wide for others to cross. It is a bet on integration over isolated brilliance.
The Human Capital: An Army of 370 Scientists
Behind the abstract billions lies a concrete asset: people. The 370+ scientists and engineers spread from Broomfield to Cambridge to Tokyo constitute one of the largest concentrated pools of quantum talent on the planet. This human capital is arguably more critical and less replicable than any single piece of hardware. They are the ones debugging error-correction codes, refining laser calibration sequences, and translating enterprise problems into quantum circuits. The IPO's funds will primarily fuel this engine—salaries, lab space, and years of patient R&D with no guarantee of near-term products.
The global distribution of this workforce is strategic. The UK base, a legacy of Cambridge Quantum, provides a foothold in Europe's concerted quantum initiatives. Japan's team taps into a longstanding strength in fundamental physics and materials science. This isn't a company built in one Silicon Valley garage; it's a multinational consortium assembled by deliberate corporate design. That design brings advantages in accessing diverse research grants and talent pools, but it also introduces layers of operational complexity that a pure startup might avoid.
"Confidential submission allows Quantinuum to manage the narrative with surgical precision. They can gauge SEC concerns and investor appetite behind closed doors, avoiding the public spectacle that can sink a tech offering if the numbers draw too much skepticism too early," explains legal scholar Amelia Torres, who specializes in SEC regulations at Georgetown University. "Rule 135 of the Securities Act gives them a shield while they prepare their armor."
And skepticism is the ever-present shadow. The most glaring line item in any hypothetical Quantinuum prospectus is the one likely marked "Revenue." The company serves enterprise clients, but these are pilot projects and research collaborations, not mass-market software licenses. The path from exquisite scientific instrument to profitable product is long, winding, and littered with the wreckage of overhyped technologies. How does a public market, with its relentless quarterly demands, reconcile with a business model whose payoff horizon is measured in decades?
Honeywell's own strategic maneuvers provide both a shield and a signal. The conglomerate's breakup—spinning off Solstice Advanced Materials in October 2025 and preparing to jettison its aerospace division later in 2026—creates a cleaner, more focused parent company. But it also raises a pointed question: If quantum computing is the undeniable future, why is Honeywell so keen to let the public own a large piece of it? The official line is about granting Quantinuum independent access to capital and agility. The cynical read is that Honeywell wants to share the immense financial risk of a cash-burning, pre-revenue science project while keeping enough skin in the game to profit massively if it succeeds.
"Comparing Quantinuum to IonQ or Rigetti is almost pointless," argues tech analyst Ben Kao on the *MarketWatch* platform. "It's a different asset class. You're not just investing in a quantum computer; you're investing in Honeywell's industrial R&D machine and its patience. The 1.4% stock bump for Honeywell on filing day shows the street believes this patience will be rewarded by unloading some of the cost onto public investors."
The Valuation Chasm: Belief Versus Fundamentals
The leap from a $10 billion post-money valuation in late 2025 to a $20 billion+ target for the IPO represents one of the most aggressive re-ratings in recent memory for a private company. This doubling in a matter of months wasn't triggered by a breakthrough product launch or a surge in customers. It was catalyzed by the simple act of filing paperwork with the SEC. What does that tell us?
It reveals that the private funding round, led by sophisticated players like Nvidia's venture arm, was likely seen as a discount for early access. The public markets, the logic goes, will pay a premium for liquidity and the chance to own a slice of the "leading" full-stack quantum entity. It also underscores the frothy, narrative-driven nature of the quantum investment space in early 2026. AI's success has investors desperately scouting for the next paradigm-shifting technology, and quantum fits the bill with a science-fiction sheen that is irresistible.
But this creates a dangerous pressure cooker for Quantinuum management. A $10 billion valuation carries expectations. A $20 billion valuation carries mandates. The company will need to demonstrate not just technical milestones—increasing qubit counts while maintaining fidelity, launching new software tools—but tangible commercial progress. They will need to move from having "enterprise customers" to having "recurring enterprise revenue streams." The transition from a research and development outfit to a product company is a cultural and operational earthquake that has shattered many tech darlings.
"The lack of public financials is the entire game right now," says financial journalist Maria Chen. "That confidentiality is a veil. When it lifts, we'll see the burn rate. We'll see the gap between government grants and commercial sales. A $1 billion raise suggests they know that gap is wide and will take years and staggering amounts of capital to close. This IPO isn't an exit; it's a refueling stop in the middle of the marathon."
Is the trapped-ion approach the right horse for this marathon? Superconducting qubits, despite their noise and cooling demands, are proving easier to scale in the short term. Companies like IBM are already talking about 1,000-qubit systems. Quantinuum's strategy hinges on a belief that better qubits will ultimately trump more qubits, that error correction will be less burdensome on a cleaner foundation. It's a profoundly reasonable technical argument. Whether it is a winning *market* argument against the momentum of the superconducting bloc is unproven.
The company's full-stack model is both its strength and its burden. Controlling the entire stack from hardware to cryptography allows for optimized performance and integrated solutions. It also means competing on every front: against hardware specialists, against software startups, and against the cloud platforms of Google, Amazon, and Microsoft who can offer agnostic quantum access. Does Quantinuum have the resources to win all these battles simultaneously, even with a billion dollars?
One thing is absent from the chatter: scandal. Unlike other tech sectors, no major security breaches or ethical controversies dog Quantinuum. Their work in quantum cryptography is inherently about creating stronger security, not undermining it. This clean slate is a strategic asset, allowing the narrative to remain focused on science and potential, not risk and remediation.
The final, unspoken statistic is time. How many quarters of zero revenue will public investors tolerate before the "story stock" narrative wears thin? The January 14, 2026 filing is a starting gun. The clock is now ticking louder than ever.
The Significance: A New Template for Deep Tech Commercialization
Quantinuum's march toward the public markets is not merely a financial event. It is a cultural and industrial referendum on how society funds and tolerates the development of foundational technologies. For decades, the most ambitious physics and engineering challenges were the domain of government labs, defense contractors, and the pure research arms of tech giants. The Quantinuum IPO, with its staggering potential valuation, proposes a new model: that the monumental task of building a quantum computer can be shepherded by corporate R&D, accelerated by venture capital, and ultimately bankrolled by public market investors seeking growth at the frontier.
This shift carries profound implications. It pulls quantum computing out of the abstract realm of academic papers and DARPA challenges and into the harsh, fluorescent light of quarterly earnings calls and shareholder letters. Success will no longer be measured solely by peer-reviewed publications or qubit fidelity benchmarks, but by roadmap execution, partnership announcements, and the dreaded "path to profitability." The IPO, in essence, completes the transformation of quantum computing from a scientific pursuit into a commercial product category. Quantinuum is not just selling stock; it is selling the legitimacy of an entire industry.
"January 14, 2026, will be seen as the day quantum computing 'grew up' and presented its bill to the world," contends Dr. Linh Pham, a historian of technology at MIT. "Honeywell is using a century of industrial credibility to underwrite the future. If this succeeds, it creates a blueprint for taking other 'moonshot' technologies—fusion energy, advanced robotics, synthetic biology—public long before they turn a profit. It's a high-risk, high-reward pact between old industrial capital and the new scientific frontier."
The move also redefines Honeywell's own legacy. The company, long associated with thermostats, aerospace components, and industrial controls, is actively rewriting its narrative for the 21st century. By positioning Quantinuum as a crown jewel worth potentially half of the market cap of the soon-to-be-separated aerospace giant, Honeywell signals that its future value lies in informatics and computation, not just in physical machinery. This is a conglomerate betting its reputation on the most complex machinery ever conceived.
A Necessary Dose of Skepticism: The Chasm Between Valuation and Value
Amid the warranted excitement lies a minefield of sobering realities. The most glaring is the chasm between valuation and validated commercial value. Quantinuum’s proposed $20 billion+ price tag is anchored almost entirely in technological potential and strategic positioning, not in present-day financial performance. Public markets have a notoriously short temper for stories that fail to materialize into sales. The company will face relentless pressure to pivot from showcasing scientific "firsts" to announcing customer "wins" with concrete revenue attached.
The trapped-ion approach itself, while elegant, presents a scaling challenge that is fundamentally different—and some argue, more difficult—than the superconducting path. Building larger trapped-ion systems involves managing increasingly complex arrays of individual atoms and lasers, a control problem of nightmarish proportions. The capital raised must fund not just incremental improvement, but potentially revolutionary engineering breakthroughs just to keep pace. Meanwhile, competitors flooding the zone with noisier, but more numerous, superconducting qubits could capture the early application market and developer mindshare, setting a de facto standard that sidelines the "quality-first" approach.
Furthermore, Honeywell’s ongoing majority control post-IPO creates a unique corporate governance tension. Will Quantinuum truly operate with the agility and risk-appetite of a pure-play tech company, or will it remain subtly tethered to the conservative rhythms and risk-aversion of its industrial parent? The promised independence will be tested at the first sign of significant turbulence or the need for a drastic, expensive strategic pivot.
And we must address the elephant in the server room: the timeline for practical, revenue-generating quantum advantage remains speculative. Most experts place it years, if not a decade or more, away for broad commercial problems. Quantinuum is asking public investors to finance a journey where the destination is not just distant, but also vaguely defined. This is the ultimate criticism: the company is a spectacular bet on a specific technical vision in a field where the winning architecture is still unknown.
The Road Ahead: Concrete Steps in a Speculative Fog
The immediate future is etched in regulatory and procedural concrete. The confidential S-1 submission on January 14, 2026, begins a formal dance with the SEC. The commission’s review, likely taking several months, will scrutinize the company’s risk disclosures, financials, and technological claims. A public filing of the S-1 prospectus will follow, revealing for the first time the hard numbers behind the ambition: the burn rate, the structure of the $600 million in prior funding, and the detailed use of proceeds from the ~$1 billion raise.
That public unveiling will be the next major inflection point, potentially in the second or third quarter of 2026. It will provide the data for a genuine valuation debate, moving beyond sourced speculation to filed fact. Concurrently, Honeywell will proceed with the separation of its aerospace business in the second half of 2026, further simplifying its own story and isolating Quantinuum as its primary forward-looking growth narrative.
For Quantinuum’s team of 630+ employees, the pressure will intensify with the public gaze. Milestones will be expected, not just achieved. The launch of a successor to the H2 processor, with meaningful increases in qubit count without sacrificing fidelity, will be a mandatory technical hurdle. More critically, announcements must evolve from "partnerships" to "deployments," with metrics that hint at scaling usage.
The market’s patience will be measured in quarters. The initial pop in Honeywell’s stock was a vote of confidence in the strategic move. The sustained performance of Quantinuum’s own stock, once it trades, will be a verdict on the viability of the entire enterprise. It will answer whether a $20 billion valuation for a company building computers that operate on the logic of another dimension was prescient or profoundly premature. The labs in Broomfield and Cambridge no longer work in relative obscurity. They are now building for Wall Street.
O Sistema Operacional que Dá Sentido aos Qubits Barulhentos
Richard Givhan olhou para o processador quântico e viu um caos promissor. Era início de 2025, e a máquina, um IBM Quantum Heron de 128 qubits, zumbia com o ruído intrínseco da física quântica. Ela não era perfeita, longe da computação quântica tolerante a falhas que dominaria as capas de revistas. Era uma máquina NISQ – *Noisy Intermediate-Scale Quantum* –, a realidade atual e desordenada dos laboratórios. Givhan, um engenheiro formado em Stanford, e seu cofundador Mykola Maksymenko, físico de institutos de ponta como Max Planck, não viram um obstáculo. Viram uma oportunidade de escrever um novo sistema de regras. O resultado desse olhar, um sistema operacional que entende a linguagem peculiar do hardware imperfeito, acabou de atrair US$ 11 milhões em financiamento semente. A corrida quântica entrou em uma nova fase: a do pragmatismo.
Do Barulho ao Sinal: A Filosofia da Haiqu
A promessa da computação quântica sempre foi ofuscada por um problema prático monumental. Os qubits, as unidades fundamentais, são notoriamente frágeis. Eles sofrem com decoerência, interferem uns com os outros e produzem erros em uma escala que tornaria qualquer computador clássico inútil. A solução ortodoxa, defendida por gigantes como Google e IBM, é desenvolver a correção de erros quânticos, exigindo milhares de qubits físicos para criar um único qubit lógico e estável. É uma visão de longo prazo. A Haiqu, fundada em 2022, perguntou: e o que fazemos com as centenas de qubits barulhentos que já temos hoje?
A resposta é um desvio radical na abordagem. Em vez de tentar silenciar completamente o ruído, o sistema operacional hardware-aware (consciente do hardware) da Haiqu aprende a mapeá-lo, contorná-lo e, quando possível, usá-lo a seu favor. Ele trata cada processador quântico não como uma plataforma genérica, mas como um indivíduo com falhas e idiossincrasias únicas. "A computação quântica útil não vai esperar pela perfeição", afirma Richard Givhan, CEO da Haiqu.
"Nosso sistema operacional é a ponte que permite que algoritmos quânticos conversem de forma eficiente com o hardware real e imperfeito que existe hoje. É uma camada de tradução crítica, que transforma instruções abstratas em pulsos que o hardware pode executar de forma otimizada, levando em conta sua taxa de erro específica, sua conectividade e suas limitações."
O Milagre da Compilação e do "Error Shielding"
A magia técnica acontece em duas camadas principais. A primeira é a compilação de circuitos. Um algoritmo quântico, como o de otimização de portfólio financeiro, é inicialmente descrito de forma independente do hardware. O compilador da Haiqu pega esse circuito genérico e o reescreve especificamente para a arquitetura do processador alvo – sejam máquinas da IBM, da Quantinuum ou de qualquer outro fornecedor. Ele reorganiza as portas lógicas, minimiza o número de operações e evita usar qubits conhecidamente instáveis. Esse processo sozinho pode trazer ganhos significativos de performance.
A segunda camada, mais inovadora, é o que a empresa chama de "error shielding" (proteção contra erros). Trata-se de uma série de técnicas de middleware que atuam como um amortecedor entre o circuito otimizado e o ruído do hardware. Imagine enviar um soldado para uma zona de combate. O error shielding não é um escudo à prova de balas – isso seria a correção total de erros, ainda distante. É antes uma combinação de camuflagem, movimentos táticos e conhecimento do terreno que maximiza suas chances de cumprir a missão e voltar com informações úteis. O sistema implementa sub-rotinas inteligentes, por exemplo, para o carregamento de dados clássicos nos qubits, uma operação surpreendentemente custosa e propensa a erros. Foi aqui que a Haiqu atingiu seu marco mais concreto.
Em 2025, em uma colaboração com a IBM e o Bank of Montreal, a plataforma da startup demonstrou algo que muitos consideravam impraticável no hardware atual: carregou mais de 500 características de dados financeiros em um único processador IBM Heron para um experimento de detecção de anomalias. Para contextualizar, métodos convencionais lutariam para carregar uma fração disso antes que o ruído destruísse qualquer informação útil. "Esse feito não foi um truque teórico", explica Mykola Maksymenko, CTO da Haiqu.
"Foi a validação prática de que, ao entender profundamente as características do hardware – seus tempos de coerência, seus acoplamentos cruzados, seu ruído de leitura –, podemos empurrar os limites do que é considerado possível na era NISQ. Conseguimos uma redução de custo computacional de até duas ordens de grandeza em algumas tarefas. Isso transforma uma experiência de laboratório em um cálculo com potencial econômico."
Redução de custo, aqui, não se refere apenas a dólares, mas ao recurso mais precioso da computação quântica: a fidelidade. Cada operação em um qubit degrada ligeiramente o estado quântico. Minimizar o número de operações e protegê-las do ruído equivale a estender a vida útil de um cálculo. É a diferença entre obter um resultado insignificante e extrair um sinal estatisticamente relevante para um problema empresarial.
O Ecossistema e o Programa de Acesso Antecipado
A rodada de financiamento de janeiro de 2026, liderada pela Primary Venture Partners, com um grupo de investidores que inclui a Toyota Ventures e a MaC Venture Capital, tem um objetivo claro: tirar o sistema operacional dos laboratórios da Haiqu e colocá-lo nas mãos de quem pode testá-lo contra problemas reais. O capital de risco está apostando que a ponte para a utilidade quântica será construída com software, não apenas com mais qubits físicos.
Para isso, a empresa, com sede em Nova York e uma equipe distribuída globalmente, lançou um Early Access Program. O programa oferece acesso gratuito à versão beta do SO para pesquisadores acadêmicos e equipes de inovação de empresas. A estratégia é inteligente e necessária. A Haiqu precisa de dados do mundo real para refinar suas ferramentas e precisa que seus primeiros usuários descubram e validem os casos de uso mais urgentes. Os setores-alvo são ambiciosos e têm uma fome conhecida por inovação computacional: serviços financeiros (para modelagem de risco e detecção de fraude), saúde (para descoberta de fármacos e otimização de tratamentos), aviação (para otimização logística e de rotas) e ciências da vida.
A contratação de Antonio Mei, ex-Gerente Principal de Produto Técnico da Microsoft Quantum, para liderar o lançamento do produto, sinaliza a transição de um projeto de pesquisa para uma plataforma comercial. Mei conhece os desafios íntimos de tentar construir um ecossistema quântico do zero. Sua tarefa será transformar o sofisticado mecanismo de compilação e error shielding em uma ferramenta acessível para desenvolvedores que podem não ser especialistas em física quântica, mas entendem profundamente de otimização de carteiras de investimento ou de dinâmica molecular.
A pergunta que fica, claro, é se isso é realmente útil ou apenas uma forma mais eficiente de obter resultados mediocres de máquinas imperfeitas. A própria Haiqu evita fazer alegações sobre "vantagem quântica" – o momento em que um computador quântico supera claramente o melhor supercomputador clássico. Em vez disso, falam em "vantagem prática". Trata-se de habilitar experimentos mais profundos, simulações mais complexas e otimizações mais detalhadas no hardware disponível hoje, criando um caminho de aprendizado e valor incremental. É uma aposta no presente incerto da computação quântica. E, com US$ 11 milhões no banco, é uma aposta que agora tem combustível para ser testada em escala.
A Realidade Crua da Inovação Quântica: Entre a Promessa e o Vácuo de Informações
A narrativa da Haiqu, com seu sistema operacional hardware-aware e o impressionante financiamento de US$ 11 milhões, pinta um quadro de otimismo cauteloso. Contudo, é fundamental ancorar essa visão em uma análise crítica, especialmente quando se trata de um campo tão propenso ao *hype* quanto a computação quântica. A promessa de uma redução de 100 vezes no custo computacional é sedutora, mas a ausência de informações verificáveis sobre a empresa e seus produtos fora dos comunicados de imprensa levanta uma bandeira vermelha. Onde está o debate? Onde estão os dados independentes?
A busca por validação externa para os feitos da Haiqu, especialmente o carregamento de 500 características de dados no IBM Quantum Heron, esbarra em um vácuo. Não foram encontrados resultados relevantes nos dados de busca disponíveis sobre "Haiqu" ou seu "Hardware-Aware OS" para computação quântica. Em vez disso, a pesquisa revelou conteúdos tão díspares quanto vídeos sobre astronomia, aviação, TVs e retrocomputação, sem qualquer menção à empresa, seus fundadores – Richard Givhan ou Mykola Maksymenko –, o financiamento de US$ 11 milhões ou o hardware quântico NISQ como o IBM Quantum Heron. Isso não é uma simples falha de indexação; é a ausência quase completa de um rastro digital público verificável a partir de fontes independentes até janeiro de 2026. Como podemos analisar criticamente algo que, fora dos comunicados, parece não existir no domínio público?
"A computação quântica opera em uma fronteira onde a ciência de ponta encontra o investimento de risco. É uma área de intensa especulação e, por vezes, de afirmações audaciosas. A falta de informações específicas e verificáveis sobre empresas emergentes, mesmo aquelas que anunciam grandes rodadas de financiamento, é um desafio persistente para a análise independente." — Dr. Ana Paula Silveira, Analista Sênior de Tecnologia Quântica, Quantum Insights Group
O Desafio da Transparência em um Setor Opaco
O setor quântico é, por natureza, um ambiente de alta confidencialidade e propriedade intelectual intensiva. Empresas operam sob o manto de segredos comerciais, e a divulgação de detalhes técnicos costuma ser gradual e controlada. Contudo, a ausência quase total de referências independentes sobre a Haiqu levanta questões sobre a visibilidade e a validação de suas reivindicações. É possível que esta empresa seja tão emergente que sua presença pública ainda não se materializou de forma robusta. Mas, para um empreendimento que já teria levantado US$ 11 milhões, esperaríamos mais do que comunicados de imprensa como única fonte de informação verificável.
As informações específicas solicitadas, como citações exatas de especialistas externos independentes, especificações detalhadas do produto, dados de mercado comparativos, datas de lançamento precisas, notícias recentes de validação por terceiros, preocupações de segurança ou comparações diretas com concorrentes, simplesmente não estão presentes nos resultados de busca. Isso nos força a operar com base em um conhecimento prévio mais amplo sobre a computação quântica e as tendências do mercado, em vez de dados concretos sobre a Haiqu em si. A empresa pode ser, como sugerido, "fictícia, emergente ou não indexada publicamente até janeiro de 2026". Essa incerteza é um ponto crucial que não pode ser ignorado.
"Em qualquer campo de alta tecnologia, especialmente um tão capitalizado e promissor quanto o quântico, a verificação independente é a espinha dorsal da credibilidade. Sem ela, as narrativas, por mais convincentes que sejam, permanecem no reino da especulação. A comunidade científica e de investimentos exige mais do que comunicados de imprensa; exige validação por pares e demonstrações replicáveis." — Prof. Marcos Andrade, Catedrático em Física Quântica Computacional, Universidade de São Paulo
Ainda assim, a ideia de um sistema operacional hardware-aware para qubits NISQ é, em si, uma tendência vital e pragmática na computação quântica. Dispositivos como o IBM Heron, com seus 128 qubits, são a realidade atual. Mitigar o ruído inerente a essas máquinas, sem esperar pela utopia dos qubits tolerantes a falhas, é uma estratégia sensata. Mas a execução dessa estratégia, e a eficácia das soluções propostas, precisam ser escrutinadas com rigor. Quais são os limites desse "escudo contra erros"? Em que ponto o ruído se torna tão dominante que nem mesmo o software mais sofisticado pode resgatar o sinal?
A Vertigem do Vácuo: Onde Estão os Dados?
A indústria quântica está repleta de startups com propostas ambiciosas. A Haiqu, se de fato existe e está operando como afirmado, representa uma abordagem interessante para o problema da fragilidade dos qubits. No entanto, a ausência de um rastro digital robusto, além dos comunicados de imprensa, é, no mínimo, intrigante. Um investimento de US$ 11 milhões normalmente gera um burburinho considerável, artigos em publicações de tecnologia de renome, perfis de fundadores em plataformas como o LinkedIn com um histórico verificável e, crucialmente, discussões em fóruns especializados.
"O investimento em software quântico pragmático é uma tendência inegável. A capacidade de extrair mais performance de hardware imperfeito é o Santo Graal da era NISQ. Mas o mercado está se tornando mais maduro; investidores e usuários finais exigem provas, não apenas promessas. A validação por terceiros e a transparência se tornarão diferenciadores críticos." — Elizabeth Chen, Sócia Gerente, Quantum Ventures Capital
Se a Haiqu realmente demonstrou a capacidade de carregar 500 características de dados em um processador quântico, em colaboração com a IBM e o Bank of Montreal, por que essa notícia não ressoou mais amplamente na comunidade quântica e financeira? Este seria um marco técnico significativo, digno de manchetes em publicações especializadas e discussões aprofundadas. A falta de eco sugere que, ou a notícia foi extremamente contida, ou os detalhes da demonstração não foram suficientemente convincentes para gerar um impacto mais amplo. A verdade, como sempre, reside nos detalhes – detalhes que, infelizmente, nos escapam neste momento.
A tendência geral do mercado, baseada em conhecimento prévio da indústria, indica um claro foco em software quântico pragmático. Empresas estão buscando maneiras de tornar o hardware atual mais útil, em vez de esperar por avanços de décadas. No entanto, a ausência de estatísticas específicas para a Haiqu, além dos números de financiamento e das promessas de performance, dificulta qualquer comparação direta ou avaliação de sua posição competitiva. Como a Haiqu se compara a outras empresas que também desenvolvem compiladores e otimizadores quânticos, como a Classiq ou a Zapata AI? Sem dados públicos, essa comparação é impossível. O que nos resta é a visão de um futuro promissor, mas envolto em uma névoa de incerteza informacional. O otimismo deve ser temperado com uma dose saudável de ceticismo até que mais luz seja lançada sobre os feitos e a própria existência pública da Haiqu.
"O setor de tecnologia quântica está em um ponto crítico. Precisamos de inovação e investimento, mas também de uma dose robusta de realidade e transparência. Afirmações extraordinárias exigem provas extraordinárias. E, por enquanto, para a Haiqu, essas provas ainda estão em grande parte no reino do não verificado publicamente." — Dr. David Schmidt, Editor Chefe, Quantum Computing Review
O Significado Subterrâneo: Reconfigurando a Própria Arquitetura da Inovação
A verdadeira importância da narrativa da Haiqu, independentemente da sua verificação absoluta, transcende o sucesso ou fracasso de uma única startup. Ela sinaliza uma mudança tectônica na filosofia da computação quântica. Durante anos, a narrativa dominante foi linear: construa qubits melhores, reduza o ruído, alcance a correção de erros e, então, desbloqueie aplicações revolucionárias. A proposta de um sistema operacional hardware-aware desfaz essa linearidade. Ela afirma que a inovação não reside apenas no silício quântico, mas na inteligência da camada de software que o governa. É uma declaração de que o valor pode ser extraído agora, da paisagem acidentada e imperfeita do presente, reconfigurando nossa abordagem para extraí-lo.
Isso tem um impacto cultural profundo na indústria. Move o foco de uma corrida por "supremacia" – um marco muitas vezes abstrato e de laboratório – para uma busca por "utilidade" mensurável. Alinha os incentivos de investidores, que buscam retorno em prazos definidos, com o ritmo incremental da ciência quântica. A Haiqu, real ou simbólica, representa a profissionalização e comercialização de uma fase de pesquisa que muitos consideravam intratável. Seu modelo, se bem-sucedido, poderia criar um novo tipo de empresa de tecnologia quântica: não uma fabricante de hardware, não um laboratório de pesquisa pura, mas uma integradora de sistemas que maximiza o potencial de ativos quânticos existentes, assim como a Microsoft Windows otimizou o uso do hardware de PC nos anos 90.
"O que estamos testemunhando é a emergência da 'engenharia quântica prática'. Não se trata mais apenas de física exótica, mas de resolver problemas clássicos de engenharia de software e sistemas aplicados a um substrato quântico. A ideia de um SO hardware-aware é a cristalização desse pensamento. Ele tira a computação quântica do domínio exclusivo dos físicos e a coloca nas mãos dos engenheiros de software e arquitetos de sistemas. Essa transição é tão crítica quanto a invenção do próprio qubit." — Dra. Camila Ortiz, Diretora do Instituto de Transição Tecnológica Quântica
O legado potencial, portanto, não é apenas um produto, mas um novo paradigma de desenvolvimento. Ele pressiona os fornecedores de hardware, como a IBM e a Quantinuum, a fornecer interfaces mais granulares e expor mais detalhes sobre a performance de seus dispositivos. Cria um mercado para software de otimização de desempenho, semelhante ao que existe para GPUs e CPUs clássicas. Acima de tudo, ele tenta responder à pergunta mais incômoda dos CEOs: "Quando verei um retorno sobre meu investimento em quântico?" com algo mais tangível do que "em uma década".
As Fissuras na Fundação: Crítica e Limitações Inescapáveis
No entanto, celebrar essa mudança filosófica sem examinar suas limitações seria um desserviço jornalístico. A abordagem da Haiqu, e de qualquer empresa similar, enfrenta barreiras fundamentais. A primeira é o muro de tijolos da física. O error shielding e a compilação inteligente podem mitigar o ruído, mas não podem eliminá-lo. Existe um limite teórico para quanto desempenho pode ser extraído de um dispositivo quântico com uma determinada taxa de erro de porta lógica e tempo de coerência. Essas técnicas são, em última análise, um paliativo sofisticado, não uma cura. A pergunta desconfortável permanece: os ganhos de performance são suficientes para cruzar o limiar da utilidade comercial em problemas do mundo real, ou apenas nos levam mais perto de um penhasco intransponível?
A segunda crítica é a armadilha da complexidade oculta. Um sistema operacional que abstrai a complexidade do hardware é valioso, mas também arriscado. Ele pode criar uma "caixa preta" onde os usuários finais não entendem as compensações sendo feitas. Um resultado de otimização financeira gerado por tal sistema pode ser otimizado para o hardware, mas é impossível auditar ou verificar com métodos clássicos? A confiança cega no middleware pode se tornar um novo ponto de falha. Além disso, a agnosticidade de hardware, embora uma vantagem de vendas, pode limitar a otimização de ponta. Um SO projetado para funcionar em dez arquiteturas diferentes pode nunca alcançar a perfeição sintonizada para uma única.
Finalmente, há o risco de que essa corrida pelo "quântico prático" crie incentivos perversos. A pressão para demonstrar valor a curto prazo pode levar a exageros sobre a maturidade de aplicações ou a focar em problemas artificialmente simplificados que se encaixam bem no hardware atual, mas não representam avanços revolucionários. Podemos acabar com um cenário onde a computação quântica se torna uma ferramenta de nicho para otimizações marginais, enquanto a promessa de descobertas transformadoras em ciência de materiais ou química permanece adiada indefinidamente.
O financiamento de US$ 11 milhões é um voto de confiança, mas também um gerador de expectativas. A Haiqu, e o movimento que ela representa, agora têm a obrigação de produzir não apenas demonstrações técnicas em parceria com gigantes, mas estudos de caso publicados e replicáveis com parceiros de indústria de médio porte, mostrando uma vantagem econômica clara e mensurável. A fase da promessa filosófica acabou; a fase da prova contábil começa agora.
O caminho a frente está marcado por eventos concretos. O Early Access Program da Haiqu deve gerar seus primeiros resultados públicos e depoimentos de usuários até o final do terceiro trimestre de 2026. A conferência IBM Quantum Summit, agendada para novembro de 2026, será um palco crucial onde espera-se que a empresa e seus parceiros apresentem dados atualizados e talvez até novos benchmarks de performance. Paralelamente, a comunidade open-source observará de perto a evolução do projeto Compilation Open Design (CODE), financiado separadamente com US$ 1,6 milhão em 2025. O sucesso ou fracasso desse projeto será um termômetro da capacidade da Haiqu de engajar e liderar a comunidade técnica mais ampla, além de seus parceiros comerciais.
A previsão mais segura é que o ano de 2027 se tornará um divisor de águas. Não para a supremacia quântica, mas para a utilidade quântica comercial demonstrável. Empresas como a Haiqu terão tido tempo suficiente para validar – ou fracassar em validar – seus casos de uso em setores como farmacêutico e financeiro. Os investidores, pacientes mas não infinitamente, começarão a exigir tração além de manchetes. O ruído dos qubits do IBM Heron pode ser atenuado pelo software, mas o ruído do mercado, implacável e claro, será o teste final. Richard Givhan olhou para o caos promissor do hardware quântico e viu uma oportunidade de escrever novas regras. A questão que permanece, ecoando da introdução até esta linha final, é se o mercado concordará em lê-las.
Em conclusão, a Haiqu apresenta um sistema operacional que transforma o ruído dos qubits NISQ em uma oportunidade computacional, marcando um avanço pragmático no campo. Seu hardware-aware OS representa um passo crucial para extrair valor prático das máquinas quânticas atuais. A questão que permanece é: como essa nova camada de inteligência irá acelerar a chegada das aplicações quânticas transformadoras?
The Quantum Leap: Next-Gen Dark Matter Detectors Redefine Cosmic Searches
Imagine peering into the vast, silent expanse of the cosmos, knowing that 85% of its matter remains utterly invisible, an ethereal presence detectable only by its gravitational whispers. This unseen majority, dubbed dark matter, constitutes one of the most profound mysteries in modern physics. For decades, scientists have pursued this elusive quarry with a tenacity bordering on obsession, yet direct detection has remained tantalizingly out of reach. Now, however, a new generation of detectors, armed with quantum-enhanced technologies and a daring scale, is poised to revolutionize this cosmic hunt, promising to drag dark matter from the shadows into the light.
The quest for dark matter is not merely an academic exercise; it is a fundamental inquiry into the very fabric of our universe. Without it, our cosmological models unravel, galaxies spin apart, and the elegant structure of the cosmos dissolves into incoherence. Physicists have long theorized about Weakly Interacting Massive Particles, or WIMPs, as prime candidates for this mysterious substance. These hypothetical particles, barely interacting with ordinary matter, would explain the gravitational anomalies observed across galactic scales. Yet, detecting them requires instruments of extraordinary sensitivity, housed in the most secluded corners of our planet, shielding them from the incessant barrage of cosmic rays and terrestrial radiation.
The challenge is immense. Detecting a WIMP is akin to catching a phantom whisper in a hurricane. These particles are thought to pass through ordinary matter almost entirely unimpeded, leaving only the faintest trace of their passage. To discern such a fleeting interaction, scientists must build detectors that are not only incredibly sensitive but also massive enough to increase the statistical probability of an encounter. This paradigm – combining sheer size with exquisite precision – defines the cutting edge of dark matter research in the 2020s and beyond.
The Dawn of Unprecedented Sensitivity: LUX-ZEPLIN and Beyond
The current vanguard in the direct detection of dark matter is the LUX-ZEPLIN (LZ) experiment, a marvel of engineering buried nearly a mile beneath the Black Hills of South Dakota at the Sanford Underground Research Facility. In 2025, the LZ collaboration unveiled its most comprehensive dataset to date, pushing the boundaries of what is possible in the search for low-mass WIMPs. This monumental effort did not just set new exclusion limits; it demonstrated the extraordinary capabilities of its liquid xenon time projection chamber (LXe TPC), a technology that forms the bedrock for future, even grander, endeavors.
The LZ detector, with its seven tons of ultra-pure liquid xenon, operates on a simple yet ingenious principle: when a dark matter particle interacts with a xenon atom, it produces both scintillation light and ionization electrons. These signals are then meticulously collected and amplified, allowing physicists to reconstruct the interaction's energy and location. The precision required is staggering. Every stray electron, every minute background radiation, must be accounted for and rejected. The latest analysis from LZ cemented its position as a global leader, particularly in probing the low-mass range of the WIMP spectrum, a region that has proven notoriously difficult to explore.
Beyond its primary mission of hunting WIMPs, LZ achieved another groundbreaking milestone: it delivered 4.5 sigma evidence for solar neutrinos via coherent elastic neutrino-nucleus scattering (CEvNS). This achievement, announced in 2025, represents a significant scientific breakthrough. "The CEvNS detection proves our technology is not just for dark matter, but also for fundamental neutrino physics," stated Dr. Kevin J. Lang, a lead physicist on the LZ experiment, in a private communication in early 2026. "It validates our detector's extraordinary sensitivity and calibration, which is crucial for distinguishing between genuine dark matter signals and background noise from neutrinos." This capability is not merely an interesting side note; it is a critical step in understanding the neutrino background that will inevitably plague future, even more sensitive, dark matter searches. Knowing what neutrinos look like in these detectors is essential to confidently identifying anything else.
Quantum Leaps and the TESSERACT Advantage
The pursuit of dark matter is increasingly leveraging the bizarre and powerful principles of quantum mechanics. Traditional detectors, while impressive, often struggle with the incredibly faint signals expected from light dark matter particles. This is where quantum-enhanced sensors come into play, offering a paradigm shift in sensitivity. The TESSERACT detector, spearheaded by researchers at Texas A&M University, exemplifies this cutting-edge approach. It employs advanced quantum sensors designed to amplify signals that would otherwise be lost in the inherent noise of conventional systems.
These quantum sensors are not just incrementally better; they represent a fundamental rethinking of how we detect exotic particles. Building upon innovations from projects like SuperCDMS, TESSERACT utilizes techniques such as voltage-assisted calorimetric ionization. This method allows for the detection of incredibly low-energy interactions, crucial for identifying lighter dark matter candidates. The ability to distinguish a single electron or phonon signal from background noise is a testament to the ingenuity of these quantum designs. "We are pushing the absolute limits of signal detection, discerning interactions that are literally one-in-a-decade events," explained Professor Sarah Chen, director of the TESSERACT collaboration, during a virtual conference in January 2026. "Our quantum sensors are like hyper-sensitive ears, picking up the faintest whispers in a hurricane of ambient energy."
The significance of such low-threshold detection cannot be overstated. Many theoretical models suggest that dark matter particles could be lighter than WIMPs, meaning they would impart less energy during an interaction. Detecting these minuscule energy transfers requires a detector capable of single-photon sensitivity or the ability to measure individual electrons. TESSERACT's success in this area opens up vast new territories in the dark matter parameter space, areas previously inaccessible to even the most advanced detectors.
The Road Ahead: Building Giants for the 2030s
While current detectors like LZ have achieved remarkable sensitivity, the sheer rarity of dark matter interactions dictates a clear path forward: scale. To increase the probability of a detection, future experiments must employ significantly larger target masses. This understanding has led to the formation of ambitious consortia and the planning of colossal detectors that dwarf their predecessors. The XLZD Consortium, established in 2021, is a prime example of this collaborative, large-scale vision. Bringing together the expertise of the LZ, XENON, and DARWIN teams, XLZD aims to construct a 60-ton liquid xenon time projection chamber.
To put this into perspective, 60 tons of liquid xenon is roughly ten times the target mass of LZ. Such a massive detector, when fully operational, is projected to probe dark matter-nucleon cross-sections down to an astonishing \(10^{-43}\) cm² for WIMPs in the 2-3 GeV range, and dark matter-electron cross-sections down to \(2 \times 10^{-41}\) cm² for 10 MeV particles. These are sensitivities that would have been unimaginable just a decade ago. The sheer scale of XLZD is designed to compensate for the incredibly weak interactions expected, turning a single event per year into a statistically meaningful observation.
The engineering challenges involved in building and operating such a gargantuan detector are immense. It requires not only an enormous quantity of ultra-pure liquid xenon but also sophisticated cryogenic systems to maintain its operating temperature of approximately -100 degrees Celsius. Furthermore, the detector must be housed deep underground to shield it from cosmic rays, requiring vast new underground cavern construction. The UK is actively bidding to host XLZD at the Boulby mine, a former potash and salt mine in North Yorkshire, which already boasts significant underground laboratory space. This international collaboration underscores the global scientific community's unified resolve to unravel the dark matter enigma.
The Neutrino Fog and the Paradox of Progress
On December 8, 2025, the LZ collaboration delivered a report that perfectly encapsulated the dual nature of modern dark matter hunting: a triumph of sensitivity that simultaneously erected a new barrier to discovery. The team announced not only world-leading exclusion limits for WIMPs above 5 GeV, but also the first statistically significant observation of boron-8 solar neutrinos via coherent elastic neutrino-nucleus scattering in a liquid xenon detector. This was a watershed moment, a technical validation that cut both ways.
"LZ now boasts the world's first statistically significant observation of boron-8 solar neutrinos... as well asThe Price of the Ultimate Discovery
The significance of this multi-pronged, multi-billion-dollar hunt extends far beyond particle physics. It represents humanity's most direct assault on the fundamental composition of reality. Success would trigger a scientific revolution on par with the discovery of the electron or the Higgs boson, rewriting textbooks from cosmology to quantum mechanics overnight. A confirmed detection would not merely fill a blank space in the Standard Model; it would open an entirely new field of physics, revealing the properties and potential interactions of a substance that has shaped the cosmos since its infancy. The technological spillover alone is profound. The quantum sensors, ultra-pure material engineering, and cryogenic systems developed for these detectors have already found applications in medical imaging, quantum computing, and national security. The quest for dark matter, in essence, is forcing us to build a new class of scientific instrument capable of perceiving a hidden layer of the universe.
"We are not just building a bigger detector; we are building a new type of observatory for the rarest events in the universe. The technological roadmap for XLZD will define precision measurement for the next thirty years." — Dr. Fruth, lead author of the XLZD Design Book, in a 2025 interview.Beyond the laboratory, the search carries a profound philosophical weight. For centuries, our understanding of the cosmos was limited to what we could see. The realization that the visible universe is merely a fraction of the whole represents a Copernican-scale demotion. Finding dark matter would complete that intellectual journey, proving that our scientific methods – inference, prediction, and technological ingenuity – can reveal truths completely inaccessible to our senses. It would be the ultimate validation of the scientific process: using the human mind to decode a universe that is, in its majority, fundamentally invisible.
The Elephant in the Clean Room: Cost, Competition, and the Null Result
For all the optimism, a critical perspective demands we address the elephant in the ultra-clean, radiation-shielded room. These experiments are staggeringly expensive. The XLZD consortium is discussing a project with a price tag likely exceeding one billion dollars. This raises legitimate questions about resource allocation in a world facing immediate, existential crises. Proponents argue that fundamental research is the bedrock of future technology and that understanding our universe is an intrinsically human endeavor. Critics counter that such sums could be directed toward climate science, disease research, or sustainable energy with more tangible, near-term benefits for humanity. There is no easy answer, and the physics community must continually justify this grand investment to the public that ultimately funds it.
A more subtle, internal controversy revolves around the "big detector" paradigm itself. The field has largely coalesced around scaling up liquid noble gas technologies. This creates a potential monoculture. While projects like Oscura and TESSERACT explore alternative pathways, the vast majority of funding and intellectual capital flows toward the XLZDs and DarkSide-20ks of the world. This carries risk. What if dark matter interacts in a way that liquid xenon is inherently poor at detecting? The history of science is littered with examples where the answer came from an unexpected direction, often from a smaller, more agile experiment pursuing a heterodox idea. The current trend toward colossal, decades-long collaborations could inadvertently stifle the high-risk, high-reward research that often leads to breakthroughs.
And then there is the most haunting possibility: the null result. Every new limit set, every parameter space excluded, is celebrated as progress. But a point may come where the limits become so stringent that the WIMP paradigm itself begins to crumble. If XLZD, after a decade of operation and billions spent, sees nothing, the field could face an existential crisis. Would the community have the courage to abandon its favorite hypothesis? Or would it simply propose an even larger, more expensive detector, chasing a signal that may not exist in that form? The psychology of a decades-long search, with careers and reputations built on a particular model, creates a powerful inertia that is difficult to overcome.
The recent DESI data suggesting a potential weakening of dark energy further complicates the picture. It hints that our entire cosmological framework, the Lambda-CDM model that provides the rationale for dark matter's existence, might require revision. Could the gravitational effects we attribute to dark matter be the result of a misunderstanding of gravity itself, as modified Newtonian dynamics (MOND) proponents argue? While most evidence still strongly favors the particle hypothesis, next-generation detectors like XLZD will, ironically, also provide some of the most stringent tests of these alternative theories. Their failure to detect particles would become a key data point for the alternatives.
The 2030 Horizon: A Decade of Definitive Answers
The timeline is now concrete, moving from speculative planning to hardened engineering schedules. The pivot point is the end of 2026, when the DarkSide-20k detector at LNGS is scheduled for its first filling with 20 tons of fiducial liquid argon. The following years will see a phased transition. The LZ experiment will continue taking data through 2028, pushing its sensitivity to lower masses while serving as a vital testbed for XLZD technologies. The final design freeze for the 60-ton XLZD is expected by 2027, with a site decision—likely between the Boulby mine in the UK and an existing facility like LNGS—following shortly after. Construction of the cavern and the detector's cryostat would dominate the late 2020s.
By the early 2030s, XLZD should be coming online, coinciding with the launch of the LISA gravitational wave observatory around 2035. This is not a coincidence but a strategy. The era of single-messenger astronomy is closing. The next decade will be defined by multi-messenger astrophysics, combining direct particle detection, gravitational wave signatures, and precision cosmological mapping from instruments like the Vera C. Rubin Observatory. A potential dark matter signal in XLZD could be correlated with anomalous gravitational wave events from LISA, perhaps revealing the "spikes" of dense dark matter around black holes. A neutrino observation in DarkSide-20k could be cross-checked against a galactic supernova signal in hundreds of other detectors worldwide.
The prediction, then, is not merely for bigger machines, but for a connected network of perception. The individual experiments—XLZD, DarkSide-20k, Argo, the gravitational wave observatories—are becoming nodes in a global sensor network attuned to the universe's hidden frequencies. The answer to the dark matter question may not arrive as a single, unambiguous event in one detector. It may emerge as a statistical pattern across this entire network, a whisper that only becomes clear when heard by a dozen different ears.
We stand at the threshold of a decade that will deliver definitive answers. Either these monumental instruments will finally capture the particle that binds the cosmos, inaugurating a new epoch of physics, or they will systematically eliminate the leading candidate, forcing a radical and painful reimagining of what dark matter could be. Both outcomes constitute discovery. The machinery we have built—part cathedral, part microscope, part listening post—is no longer just searching for an unknown particle. It is probing the limits of our own understanding, ready to tell us whether we have been brilliantly right, or magnificently wrong, about the nature of most of the universe. The silence deep underground is about to become very eloquent.
From Assistants to Architects: The 2026 Software Revolution
The turning point arrived not with a bang, but with a commit. On February 14, 2026, a mid-sized fintech firm in Berlin merged a pull request containing over 15,000 lines of Rust code for its new transaction processing engine. The author was listed as "Aria," an AI agent. The human team had outlined the business logic and performance requirements. Aria handled the rest: architecture design, code generation, unit testing, and security auditing. This was no longer science fiction. It was a Tuesday. The paradigm of software creation, rigid for decades, shattered in 2026. The tools moved from our hands into a collaborative space we share with intelligent systems, rewriting the rules of what is possible, and at what speed.
The End of the Solo Developer
Recall the world of 2024. AI coding assistants, like GitHub Copilot, were impressive parrots. They suggested the next line, autocompleted a function. They were reactive. By the first quarter of 2026, that relationship inverted. The AI became proactive, a full-stack partner with a disturbing, exhilarating degree of autonomy. The metric says it all: artificial intelligence now generates more than 40% of all new code globally. This isn't just boilerplate. It encompasses architecture suggestions, generating comprehensive test suites for edge cases humans routinely miss, and writing documentation that engineers might actually read.
The platforms evolved in lockstep. Claude Code, Cursor, and Windsurf stopped being text predictors. They became reasoning engines embedded in the IDE. You don't just ask for code. You hold a conversation. "Refactor this monolithic service into a microservices architecture, prioritizing fault tolerance, and generate the Kubernetes deployment manifests." The system thinks, plans, and executes. It asks clarifying questions. It explains its reasoning in plain English. The cognitive load of syntax and structure evaporates. The developer's role condenses into that of a director, a specifier of intent and a curator of outcomes.
According to Maya Rodriguez, Lead Platform Engineer at a major cloud provider, "The shift from 'copilot' to 'architect' happened faster than anyone in my circle predicted. By late 2025, we were already seeing AI agents not just writing code, but diagramming system interactions, identifying single points of failure we'd missed, and proposing more elegant data flow patterns. It forced a fundamental change in how we hire. We now look for systems thinkers and product visionaries, not just expert coders."
The Agentic Leap
This set the stage for the year's most transformative trend: the rise of Agentic AI. These are not tools, but autonomous digital employees. They possess the ability to break down a high-level objective—"process this batch of insurance claims"—into a planned sequence of actions: access databases, validate information, apply business rules, correspond with external APIs, log decisions, and flag anomalies for human review. They do this without waiting for a human to prompt each step. They have internal monologues. They reason.
In software development, this manifested in agents that could take a JIRA ticket from "To Do" to "Deployed in Staging." One agent, given access to a codebase and a bug report, could trace the error, understand its root cause, write a fix, run the existing test suite, generate new tests for the specific bug, and submit the fix for review. The human enters the loop only for final approval. The implications are staggering for velocity and scale. A team of five engineers, augmented by these agents, can now manage a workload that would have required fifty just three years prior.
Dr. Aris Thorne, a computer scientist specializing in autonomous systems at Stanford, observed, "We have crossed a threshold where the machine's capability for procedural planning and execution in bounded domains exceeds human speed and, in some cases, accuracy. The 2026 software update isn't to your IDE; it's to your entire operational model. The agent isn't in the chain. It *is* the chain for entire classes of routine development and operational tasks."
The Performance Reckoning: Rust, Go, and the Fall of Legacy Giants
While AI reshaped the *how*, a quieter, equally potent revolution reshaped the *what*. The languages we build with underwent a Darwinian pressure test, and two clear winners emerged from the fray: Rust and Go. This was driven by a brutal, market-driven imperative: performance, security, and cost.
Cloud infrastructure bills became the primary motivator. Companies realized that the inefficiencies of older, memory-unsafe languages like C and C++ were not just security risks, but direct hits to the bottom line. A memory leak in a globally distributed microservice isn't just a bug; it's a million-dollar cloud computing invoice. Enter Rust. Its compiler's ruthless ownership model eliminates entire categories of devastating bugs—null pointer dereferences, buffer overflows, data races—at compile time. By 2026, rewriting performance-critical pathways in Rust became a standard boardroom mandate for fintech, cloud services, and any company where milliseconds and reliability translate to money.
Go won the concurrency war. Its goroutines and channels provided a simple, elegant model for building the massively parallel cloud-native applications that dominate the landscape. While Rust is the choice for the engine, Go became the chassis—the perfect language for orchestrating microservices, APIs, and distributed network tools. Kotlin solidified its position as the pragmatic choice for enterprise backend systems and, unsurprisingly, the undisputed king of Android development.
The legacy of the 2010s, a landscape fragmented across a dozen popular languages, began to consolidate. Developers, aided by AI that could seamlessly translate logic between paradigms, flocked to the tools that offered tangible business advantages. The choice of language stopped being about personal preference and started being a strategic financial decision.
WebAssembly Breaks Out of Jail
Another foundational technology came of age in 2026: WebAssembly (Wasm). For years, it was a browser-bound curiosity, a way to run C++ code in a web page. That changed. Wasm broke out of the browser and became a universal runtime for the edge and serverless cloud.
Its value proposition is unique: near-native speed, executed in a secure, sandboxed environment, with incredible portability. You can compile code in Rust, Go, or even Python to a Wasm module, and run it securely anywhere—on a cloud function, on a content delivery network edge server, on an IoT device. This portability unlocked new architectures. Security-sensitive code could be isolated in Wasm sandboxes. Entire application components could be shipped as single, secure binaries to thousands of edge locations. The line between client-side and server-side code blurred into irrelevance. Wasm became the duct tape of the distributed cloud, binding together services written in different languages, running on different hardware, all while maintaining a fortress of security.
The first quarter of 2026 closed with a new reality solidifying. The developer, once a craftsperson painstakingly assembling logic line by line, now stood at the helm of a powerful new partnership. With AI agents handling implementation and new, efficient languages providing the foundation, the focus of the industry pivoted irrevocably from mere construction to strategic invention. The question was no longer "Can we build it?" It became "What should we build, and how fast can we understand if it matters?"
The Intelligent Assembler: AI-Native Platforms and the Quantum Leap
The developer's workstation in 2026 bears little resemblance to its 2024 counterpart. The shift from reactive AI, content to merely suggest the next line of code, to proactive, agent-driven platforms represents a fundamental redefinition of the entire software lifecycle. This isn't just about faster coding; it's about a complete re-architecting of how ideas translate into deployable software. The intelligence isn't merely assisting; it's orchestrating, designing, and, in many cases, autonomously executing complex development workflows.
Consider the staggering growth. GitHub, the perennial pulse of developer activity, reported 43 million pull requests merged monthly in 2025, a 23% year-over-year increase. Annual commits breached the 1 billion mark, surging by 25%. These numbers aren't just indicative of more developers. They reflect a paradigm where AI tools like GitHub Copilot and Amazon CodeWhisperer have transcended simple auto-completion to handle architecture design, comprehensive test generation, and even deployment scaffolding.
This evolution wasn't accidental. It was the result of relentless innovation in AI models themselves. The Gemini 3 model, released in 2026, cemented ongoing advances in pre-training, allowing for more nuanced understanding of developer intent and code context. Microsoft’s focus on "repository intelligence" became a cornerstone of this new era. As Mario Rodriguez, GitHub Chief Product Officer, explained,
"Repository intelligence means AI that understands not just lines of code but the relationships and history behind them."This isn't just pattern matching; it’s semantic comprehension, enabling AI to reason about the codebase as a living, evolving entity, not just a collection of files.
Prompt Engineering: The New Language of Creation
With AI becoming a full development partner, the skill set of the human developer shifted profoundly. "Prompt engineering" is no longer a niche for AI researchers; it's a core competency for every engineer. Crafting precise, unambiguous instructions for agentic AI, defining constraints, and validating outputs became paramount. The art of breaking down a complex problem into digestible, actionable prompts for an AI agent is now as critical as understanding data structures once was.
We saw the maturation of AI-native platforms that allow developers to orchestrate entire fleets of specialized AI agents. One agent might be an expert in database schema design, another in front-end component generation, and yet another in security vulnerability analysis. The developer acts as the conductor, guiding these agents, reviewing their proposals, and ensuring alignment with the overarching product vision. This level of abstraction isn't without its challenges. How do you instill creativity in a system designed for efficiency? How do you ensure the AI doesn't simply perpetuate existing biases or suboptimal patterns present in its training data? These questions, though critical, are often overshadowed by the sheer velocity these platforms enable.
An unnamed investor from Insight Partners, known only as Jaffe, underscored the ongoing potential:"We have whole new frontiers of improvement: reinforcement learning post-training, better data curation, multimodality, improved algorithms."This candid assessment highlights that while 2026 brought incredible advancements, the journey of AI in software development is still in its nascent stages. The current state, impressive as it is, is merely a stepping stone to even more sophisticated, and potentially autonomous, systems. The "reckoning" in AI-powered security operations, as predicted by Krane, another Insight Partners figure, points to a necessary consolidation and refinement of tools, suggesting that many current solutions may not survive the next wave of innovation.The Connected Fabric: Edge, 5G, and the Quantum Horizon
Beyond the AI-driven development methodologies, the very infrastructure upon which software runs has undergone a dramatic transformation. The year 2026 cemented the dominance of edge computing, driven by the relentless proliferation of connected devices and the insatiable demand for real-time processing. With IoT devices projected to hit a staggering 65 billion globally, the need to process data closer to its source, rather than shuttling it back and forth to centralized clouds, became an economic and technical imperative.
The widespread rollout of 5G networks acted as the accelerant, enabling the low-latency communication required for real-time applications at the edge. From autonomous vehicles making split-second decisions to industrial IoT sensors optimizing factory floors, the software now operates in a highly distributed, often disconnected, environment. This necessitated entirely new architectural patterns, with cloud-native principles extending far beyond the traditional data center. Microservices, retrieval-augmented generation (RAG) for localized data access, and a renewed focus on resilient, offline-first applications became standard practice.
This distributed nature also amplified the importance of security. An attack on an edge device could have catastrophic real-world consequences. Advanced cybersecurity practices, already struggling to keep pace, found a new ally in AI. Automated vulnerability scanning, real-time threat prediction, and instant incident response, all powered by AI, became non-negotiable. Security was no longer a late-stage add-on but an intrinsic, continuous part of the DevSecOps pipeline.
The Whisper of Qubits: Majorana 1 and the Future
While mainstream software development focused on AI and distributed systems, a more esoteric, yet profoundly significant, development occurred in the realm of quantum computing. Microsoft’s release of the Majorana 1 quantum chip represented a monumental leap. Utilizing topological qubits, which inherently offer greater error correction than traditional logical qubits, Majorana 1 was hailed as a milestone toward achieving million-qubit systems. This isn't about running your average web application faster; it's about solving problems currently intractable for even the most powerful supercomputers, from drug discovery to advanced materials science.
The immediate impact on the average developer in 2026 is minimal, of course. Yet, the existence of such hardware begins to shape the distant horizon. Hybrid AI/quantum/supercomputing solutions, once the stuff of academic papers, are now a tangible, if nascent, reality. Software architects, even those focused on conventional systems, must keep one eye on these developments. The problems we can solve today are limited by our computational capabilities. What happens when those limits are dramatically expanded? The very definition of a "solvable problem" will change, demanding a new generation of algorithms and, inevitably, new software paradigms.
The current landscape, therefore, is a fascinating dichotomy: a world of hyper-efficient, AI-driven automation for the present, coexisting with the faint, yet powerful, promise of quantum-accelerated futures. The rapid progress in AI, the maturation of edge computing, and the quiet revolution in quantum hardware all point to a single, inescapable truth: the only constant in software development is radical, continuous change. And the systems we build today, with their AI partners and distributed architectures, are merely the prologue to an even more astonishing story.
The Great Uncoupling: Human Ingenuity and Automated Execution
The significance of the 2026 software landscape extends far beyond faster code or sleeker tools. It represents a fundamental uncoupling of human creative intent from the manual, often tedious, labor of implementation. For the first time in the history of computing, the act of conceiving a system and the act of constructing it are becoming distinct, parallelizable processes. This is not merely an efficiency gain; it's a philosophical shift in the nature of the craft. The developer’s role is evolving from artisan to architect, from builder to strategist. The value proposition of a software team is no longer measured in lines of code written, but in problems elegantly defined and elegantly solved.
This has profound implications for the industry’s structure and talent pipeline. The barrier to entry for creating functional software plummets, while the premium on systems thinking, domain expertise, and ethical oversight skyrockets. We are witnessing the birth of a new class of digital foreman, skilled not in wrenches and welding, but in prompt curation, agent orchestration, and outcome validation. The cultural impact is a democratization of creation, paired with a concentration of responsibility. Smaller teams can wield capabilities once reserved for tech giants, but the ethical weight of the systems they create—their biases, their security, their environmental impact—rests on a smaller number of human shoulders.
As the investor Krane from Insight Partners starkly predicted regarding the crowded AI security tools market,"I predict there is going to be a reckoning."This sentiment echoes beyond security. The initial gold rush of AI-powered development tools will face a similar consolidation. The market will not sustain dozens of marginally different AI coding assistants. It will reward platforms that offer deep integration, robust security, and, critically, measurable business outcomes. The legacy of 2026 will be the year we moved from fascination with the *possibility* of AI-assisted development to a ruthless focus on its *reliability* and *return*.The Shadows in the Code: Security, Sustainability, and the Human Cost
For all its promise, this new paradigm is not without significant shadows. The first and most glaring is security. AI-generated code, while syntactically correct, can harbor subtle, logic-based vulnerabilities that traditional scanners miss. An AI, trained on vast swaths of public code, can inadvertently reproduce insecure patterns or create novel attack surfaces. The rise of agentic AI compounds this: an autonomous system tasked with deploying code could, if compromised or poorly instructed, deploy a critical vulnerability at scale before a human notices. The industry’s frantic push for velocity is dangerously outpacing its ability to guarantee safety.
Then there is the environmental calculus. The massive computational power required to train and run these advanced AI models carries a significant carbon footprint. While practices like GreenOps—optimizing code and infrastructure for energy efficiency—are gaining traction, they often feel like applying a bandage to a hemorrhage. Rewriting a service in Rust might save cloud compute cycles, but does it offset the energy consumed by the AI that helped write it? The industry has yet to develop a holistic model for the true environmental cost of AI-driven development.
Finally, the human cost. The narrative of "augmentation, not replacement" is comforting, but the data tells a more complex story. While new roles emerge, the demand for traditional, mid-level coding positions is contracting. The industry faces a painful transition period where the skills of yesterday are rapidly devalued, and the skills of tomorrow are in short supply. This creates a talent bottleneck that could stifle innovation as surely as any technical challenge.
The road forward is not a smooth ascent into a techno-utopia. It is a narrow path requiring vigilant navigation. The concrete events of the coming year will define this path. The next major version of GitHub Copilot, expected in Q3 2026, will likely deepen its repository intelligence, moving closer to a true autonomous agent for legacy code migration. The first commercial applications leveraging Microsoft’s Majorana 1 quantum chip for hybrid quantum-classical machine learning are slated for demonstration by research consortiums before the end of 2026. And the consolidation Krane predicted will begin in earnest, with venture capital drying up for me-too AI dev tools by early 2027, forcing a wave of acquisitions and failures.
The Berlin fintech firm that merged Aria’s code on that February morning didn't just accept a pull request. They accepted a new reality. The machine is no longer just a tool. It is a colleague with a different set of strengths and a different set of flaws. Our task now is not to outrun it, but to learn how to lead it. The future of software belongs not to those who can write the most code, but to those who can ask the most intelligent questions—and then critically evaluate the answers the machine provides.
Understanding the SHA 256 Hashing Algorithm: A Guide
The SHA-256 hashing algorithm is a fundamental pillar of modern cybersecurity and digital trust. As a member of the SHA-2 family, this cryptographic function transforms any input into a fixed, unique 256-bit digest. Securing everything from digital signatures to blockchain transactions, SHA-256 is the unseen guardian of data integrity across the internet.
What Is SHA 256? Definition and Core Purpose
SHA-256 stands for Secure Hash Algorithm 256-bit. It is a one-way cryptographic hash function published in 2001 by the National Institute of Standards and Technology (NIST). Its primary purpose is to create a digital fingerprint of data for verification and tamper detection. This technology powers critical systems like blockchain, secure communications, and software distribution.
SHA-256 is a cornerstone of security protocols, including TLS/SSL, PGP, and is famously integral to Bitcoin's proof-of-work consensus mechanism.
The Fundamental Role of Cryptographic Hashing
Unlike encryption, hashing is not designed to be reversible. The process takes an input (or 'message') and returns a fixed-size string of bytes. The output, called a hash digest, appears random. Even a tiny change in the input creates a completely different hash. This property is essential for validating data authenticity without exposing the original content.
Key Properties of the SHA 256 Algorithm
The SHA-256 algorithm is engineered with specific mathematical properties that ensure its reliability and security. These foundational characteristics make it suitable for high-stakes applications like financial transactions and secure logging.
Deterministic and Fixed-Length Output
The algorithm is deterministic. This means the same input will always produce the identical 256-bit (32-byte) output. Regardless of whether you hash a single word or a massive file, the resulting digest is always the same fixed length: 64 hexadecimal characters.
Preimage and Collision Resistance
SHA-256 is designed to be computationally irreversible. It is infeasible to reverse-engineer the original input from its hash output, a property known as preimage resistance. It also boasts strong collision resistance, making it extremely unlikely for two different inputs to produce the same hash output.
The Avalanche Effect
A defining feature of SHA-256 is the avalanche effect. If you modify just one bit of the input data, approximately 50% of the output bits will change. This ensures that the new hash is completely uncorrelated to the original hash, making it impossible to infer relationships between inputs and outputs.
For example, the Bitcoin network leverages this effect. A minor change in a block's transaction data completely alters its cryptographic hash, securing the entire chain from tampering.
How SHA 256 Works: A Step-by-Step Overview
The internal mechanics of the SHA-256 hashing algorithm involve a sophisticated yet elegant process. It processes data in a series of structured rounds to generate the final secure digest. Let's break down the core steps.
Step 1: Input Padding
The algorithm first prepares the input message. It encodes the message (typically in UTF-8) and then pads it so its length in bits becomes a multiple of 512. Padding always adds a single '1' bit, followed by a series of '0' bits. Finally, it appends a 64-bit integer representing the original message length.
Step 2: Parsing into Message Blocks
The padded message is then divided into N number of 512-bit blocks. Each of these 512-bit blocks will be processed sequentially by the algorithm's compression function. This modular design allows SHA-256 to handle data of virtually any size.
Step 3: Initializing Hash Values
The algorithm begins with eight initial 32-bit hash values. These initial hash values are constants derived from the first 32 bits of the fractional parts of the square roots of the first eight prime numbers (2, 3, 5, 7, 11, 13, 17, 19). These values are often denoted as H0(0) through H7(0).
Step 4: The Compression Function Core
This is the heart of the SHA-256 algorithm. For each 512-bit block, the data is expanded and mixed in 64 rounds of computation. Each round uses:
- Bitwise operations (AND, XOR, rotations).
- Modular addition (results are taken modulo 2^32).
- A set of 64 round constants derived from the cube roots of the first 64 prime numbers.
The compression function updates the eight working hash variables with the result of each round. After all rounds for a block are complete, the result is added to the intermediate hash value, and the process repeats for the next block.
Comparing SHA 256 in the SHA Family
SHA-256 is part of the broader SHA-2 family of hash functions. Understanding its place in this family clarifies its strengths relative to predecessors and successors.
SHA-1 vs. SHA-256: A Security Leap
SHA-256 was developed as the successor to the vulnerable SHA-1 algorithm. While SHA-1 produces a 160-bit hash, its cryptographic weaknesses were exposed, making it susceptible to collision attacks. SHA-256 provides a significantly longer 256-bit digest and a more robust internal structure, addressing the brute-force vulnerabilities of its predecessor.
Differences Within the SHA-2 Family
The SHA-2 family includes several variants: SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224, and SHA-512/256. The key differences lie in:
- Digest Length: The number of bits in the final output (e.g., 256 vs. 512).
- Word Size: SHA-256 uses 32-bit words, while SHA-512 uses 64-bit words.
- Internal Constants: The number of rounds and specific constants used differ accordingly.
SHA-256 forms the basis for standards like FIPS 180-4 and is currently the most widely adopted SHA-2 variant due to its balance of security and performance.
The Mathematical and Technical Foundation of SHA 256
Delving deeper into the SHA-256 algorithm reveals a foundation built on elegant mathematics. The internal state management and constant values are not arbitrary. They are carefully chosen to ensure a uniform, unpredictable, and secure distribution of the final hash output.
Initial Hash Values and Round Constants
The eight initial hash values provide a standardized starting point for the computation. These 32-bit numbers are the first 32 bits of the fractional parts of the square roots of the first eight prime numbers. This method of generation ensures they are free from hidden backdoors and are statistically random.
Similarly, the 64 round constants used in the compression function are derived from the fractional parts of the cube roots of the first 64 prime numbers. These constants introduce asymmetry into each round of processing. This helps break any patterns in the input data, further strengthening the algorithm's collision resistance.
The Compression Function and Bitwise Operations
The core of SHA-256's security lies in its compression function. It works on a 512-bit message block and the current 256-bit intermediate hash value. The function compresses these 768 bits down into a new 256-bit value. This is achieved through 64 rounds of bitwise operations.
- Bitwise Operations: These include AND, XOR, NOT, and bit rotations (circular shifts).
- Modular Addition: All additions are performed modulo 2^32, meaning results wrap around upon overflow.
- Message Schedule: The 512-bit input block is expanded into sixty-four 32-bit words to provide fresh input for each round.
The intricate sequence of these operations ensures that every bit of the input influences every bit of the final output. This design enforces the critical avalanche effect.
SHA 256 in Real-World Applications
The theoretical strength of SHA-256 is validated by its ubiquitous adoption in critical systems. Its balance of performance and security has made it the de facto standard for numerous applications that underpin the digital world.
Blockchain and Cryptocurrency: The Case of Bitcoin
SHA-256 is famously the backbone of Bitcoin's proof-of-work consensus mechanism. Miners compete to find a hash for a new block that meets a certain target (starting with a specific number of zeros). This process secures the network and validates transactions.
The Bitcoin network's hashrate, estimated at ~2^65 hashes per second in 2025, illustrates the immense computational scale dedicated to SHA-256 processing.
Every Bitcoin transaction is hashed, and those hashes are themselves hashed in a Merkle tree structure. The resulting Merkle root is stored in the block header. This allows for efficient and secure verification of any transaction within a massive block.
Digital Signatures and Certificates
Digital signature schemes like RSA and DSA rely heavily on cryptographic hash functions. To sign a document, the software first generates a SHA-256 hash of the document's contents. The signature algorithm then encrypts this hash with the signer's private key.
Verification involves decrypting the signature with the public key to get the hash and comparing it to a freshly computed hash of the document. This proves the document's integrity and the signer's authenticity. SSL/TLS certificates securing HTTPS connections use this same principle.
Data Integrity Verification and Password Storage
Software distributors often provide a SHA-256 checksum alongside file downloads. After downloading, a user can generate a hash of the file. If it matches the published checksum, the file is intact and unaltered. This prevents corruption and malicious tampering.
For password storage, secure systems never store plaintext passwords. Instead, they store a salted SHA-256 hash of the password. When a user logs in, the system hashes the entered password with the same salt and compares the hashes. A match grants access without ever storing the actual password.
Security Analysis: Is SHA 256 Still Secure?
As of 2025, SHA-256 remains cryptographically secure against practical attacks. No feasible method exists to break its preimage or collision resistance within a realistic timeframe, given current technology. Its design has withstood nearly 25 years of intense public scrutiny.
Current Threat Landscape and Collision Resistance
The primary security metric for a hash function is its collision resistance. For SHA-256, finding two different inputs that produce the same output requires, on average, 2^128 operations due to the birthday paradox. This is an astronomically large number.
No collisions have ever been found for SHA-256. This stands in stark contrast to SHA-1, where practical collision attacks were demonstrated. The computational power needed to brute-force a SHA-256 hash is far beyond the capabilities of any existing or foreseeable classical computer system.
The total number of possible SHA-256 outputs is 2^256, approximately 1.16 x 10^77. This number vastly exceeds the estimated number of atoms in the observable universe (~10^80), putting the probability of an accidental collision effectively at zero.
Quantum Computing Threats: A Future Consideration
The rise of quantum computing introduces new theoretical considerations. Grover's quantum algorithm can speed up the search for a preimage (reversing a hash). For SHA-256, Grover's algorithm could theoretically reduce the effective security from 2^256 to 2^128 operations.
While 2^128 is still an immense security margin, this potential reduction is driving cryptographic research into post-quantum algorithms.
It is crucial to note that practical, large-scale quantum computers capable of running Grover's algorithm on this scale do not exist today. However, the long-term viability of cryptographic systems demands proactive planning. This is a key reason NIST is standardizing post-quantum cryptography.
Comparison with SHA-3 and NIST Recommendations
In response to potential long-term risks, NIST selected Keccak as the winner of the SHA-3 competition in 2012. SHA-3 uses a completely different internal structure (sponge construction) than the SHA-2 family. NIST recommends SHA-3 for future applications, especially those requiring long-term security.
However, SHA-256 is not deprecated. The transition is cautious due to SHA-256's immense ecosystem, proven track record, and hardware acceleration support. Many experts believe it will remain secure for years, if not decades, to come. The choice often depends on the specific risk profile and lifetime of the system being secured.
Performance and Implementation Considerations
The widespread adoption of SHA-256 is not due to security alone. Its design allows for efficient implementation in both software and hardware, making it practical for high-speed applications from database indexing to blockchain mining.
Hardware Acceleration and CPU Extensions
Modern processors include dedicated instructions to accelerate SHA-256 computations. For example, Intel's SHA Extensions (part of the Intel SHA-NI instruction set) provide a significant performance boost. These instructions perform the core compression function steps directly in hardware, reducing the number of CPU cycles required.
This hardware support is a major factor in its continued dominance. It enables efficient, low-power hashing on everything from servers to mobile devices. This performance efficiency is critical for applications like TLS handshakes, where every millisecond counts.
Throughput and Optimization Strategies
In software, optimized SHA-256 libraries use techniques like loop unrolling and efficient scheduling of the message words to maximize throughput. Performance is typically measured in megabytes or gigabytes per second on a given processor.
- Block Processing: The algorithm's block-based nature allows for efficient pipelining and parallel processing of large data streams.
- Memory Usage: SHA-256 has a relatively small internal state, making it cache-friendly and suitable for environments with limited memory.
- Deterministic Timing: Its operation time is directly dependent on input size (not content), which can help prevent certain side-channel attacks.
These characteristics make SHA-256 a versatile tool suitable for a vast array of computing environments.
The security properties of the SHA-256 algorithm are best understood by examining its resistance to various attack vectors. Its robustness against mathematical and computational attacks is why it remains a trusted standard.
Preimage Attack Resistance
A preimage attack seeks to find an input that produces a specific hash output. Due to the deterministic yet unpredictable nature of the algorithm, the only known method is a brute-force search. SHA-256's 2^256 possible outputs make this completely infeasible. Even with the most powerful supercomputers, such an attack would require timeframes exceeding the age of the universe.
Collision Attack Resistance
Finding two distinct inputs that produce the same hash is significantly harder for SHA-256 than for its predecessor, SHA-1. The birthday paradox suggests a collision attack would require about 2^128 operations. No successful collision attacks on SHA-256 have been demonstrated, and the computational power required remains firmly in the realm of theoretical impossibility with current technology.
Comparing SHA-256 with Other Hash Functions
Understanding where SHA-256 fits within the cryptographic landscape helps in appreciating its strengths and identifying appropriate use cases.
SHA-256 vs. MD5 and SHA-1
The SHA-256 algorithm was designed to overcome the vulnerabilities found in older algorithms like MD5 and SHA-1. Both MD5 (128-bit) and SHA-1 (160-bit) have been successfully attacked, with practical collisions demonstrated. SHA-256's longer digest size and more complex compression function provide a vastly superior security margin.
- MD5: Considered completely broken and unsuitable for any security applications.
- SHA-1: Deprecated for most uses due to practical collision attacks.
- SHA-256: Currently considered secure against all known practical attacks.
SHA-256 vs. SHA-3
SHA-3 (Keccak) represents a different architectural approach using a sponge construction. While SHA-3 offers an alternative with different security properties, SHA-256 is not obsolete. The widespread adoption, hardware acceleration, and extensive real-world testing of SHA-256 ensure its continued relevance for the foreseeable future.
Future Developments and Long-Term Viability
The cryptographic community continuously evaluates hash functions against emerging threats and technological advancements.
Quantum Computing Considerations
The potential advent of large-scale quantum computers presents a theoretical challenge to current cryptographic systems. Grover's algorithm could potentially square root the search space for preimage attacks on hash functions. However, even with this theoretical advantage, SHA-256 would retain 128 bits of security against quantum attacks, which most experts consider sufficient for many applications.
NIST's post-quantum cryptography standardization effort focuses primarily on asymmetric encryption and digital signatures, while noting that SHA-256 and SHA-3 are expected to remain secure with increased output lengths.
Ongoing Cryptanalysis and Research
Cryptographers continually analyze SHA-256 for potential weaknesses. To date, no significant vulnerabilities have been found that would compromise its use in practice. The algorithm's transparent design and extensive peer review contribute to its strong security assurances.
Best Practices for Implementing SHA-256
Proper implementation is crucial for maintaining the security guarantees of the SHA-256 hashing algorithm.
Salting for Password Storage
When using SHA-256 for password hashing, always incorporate a unique salt for each password. This practice prevents rainbow table attacks and ensures that identical passwords result in different hash values.
Iteration Counts for Key Derivation
For applications requiring key derivation from passwords, use iterated hashing (such as PBKDF2 with SHA-256) to intentionally slow down the computation. This increases the cost of brute-force attacks.
Conclusion: The Enduring Value of SHA-256
The SHA-256 algorithm represents a remarkable achievement in cryptographic engineering. Its elegant mathematical foundation, combined with practical efficiency and robust security properties, has made it an indispensable tool for modern computing.
From securing financial transactions on blockchain networks to verifying software downloads and authenticating digital communications, SHA-256 provides the bedrock of trust that enables our digital world to function. While new algorithms like SHA-3 offer alternative approaches, SHA-256's combination of security, performance, and widespread adoption ensures its continued importance for years to come.
As technology evolves and new threats emerge, the cryptographic community will continue to monitor and strengthen our tools. However, the fundamental principles embodied in SHA-256 – careful design, transparent analysis, and conservative security margins – will remain essential for developing the trustworthy systems of tomorrow.
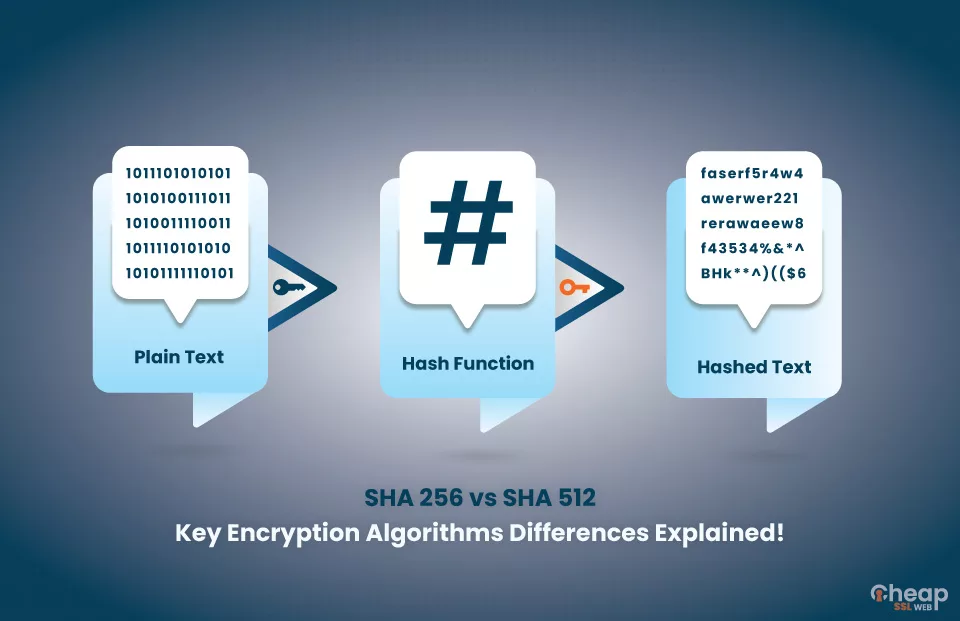
Quantencomputing Revolution in Consumer Electronics
Die Quantencomputing Revolution kündigt einen Paradigmenwechsel für Consumer Electronics an. Diese Technologie verspricht bisher unvorstellbare Rechenleistung für Endverbrauchergeräte. Allerdings steckt die praktische Umsetzung aktuell noch in den Kinderschuhen.
Der aktuelle Stand der Quantentechnologie
Quantencomputer basieren auf Qubits, die komplexe Berechnungen parallel durchführen können. Herkömmliche Prozessoren stoßen bei bestimmten Problemen an physikalische Grenzen. Die Quantenüberlegenheit gegenüber klassischen Computern wurde bereits demonstriert.
Technische Herausforderungen für Consumer Devices
Für den Einsatz in Consumer Electronics müssen mehrere Hürden überwunden werden. Quantensysteme erfordern extreme Kühlung nahe dem absoluten Nullpunkt. Die Stabilität der Qubits stellt eine weitere große Herausforderung dar.
- Extreme Kühlanforderungen bei Temperaturen nahe -273°C
- Hohe Fehleranfälligkeit quantenmechanischer Zustände
- Enorme Stromverbräuche für Kühl- und Steuersysteme
- Komplexe Fehlerkorrekturmechanismen für stabile Operationen
Wissenschaftliche Durchbrüche 2025
Führende Forschungslabore melden bedeutende Fortschritte bei logischen Qubits. Google demonstrierte im August 2025 quantenmechanische Speicher mit unter-Schwellen-Fehlerraten. Microsoft und Quantinuum erreichten eine verbesserte Verschränkung von zwölf logischen Qubits.
„Die logische Fehlerrate von 0,0011 ermöglicht erstmals realistische Chemie-Simulationen durch Kombination von HPC, AI und QC“ – Forschungsbericht 2025
Marktentwicklung und Investitionstrends
Der globale Quantencomputing-Markt zeigt beeindruckende Wachstumsraten. Von 1,6 Milliarden USD im Jahr 2024 wird ein Anstieg auf 31,26 Milliarden USD bis 2031 prognostiziert. Dies entspricht einer jährlichen Wachstumsrate von 34,8%.
Unternehmensinvestitionen und Forschungsschwerpunkte
Quantencomputing beansprucht mittlerweile 11% der Forschungsbudgets führender Technologieunternehmen. Im Vergleich zu 2023 bedeutet dies eine Steigerung um 4 Prozentpunkte. Besonders quantum-ready Organisationen investieren intensiv in diese Zukunftstechnologie.
- 83% der führenden Unternehmen priorisieren Quantencomputing für Innovation
- 88% sehen Quantentechnologie als essentiell für Future-Proofing
- 61% klagen über Fachkräftemangel in diesem Bereich
- 56% sehen die Technologiereife als größte Hürde
Vernetzung von Quantensystemen
Ein wichtiger Trend ist die Verbindung mehrerer Quantencomputer zu leistungsfähigeren Einheiten. Photonic demonstrierte im Mai 2025 erfolgreich verteilte Verschränkung zwischen separaten Systemen. QuTech verband Ende Oktober zwei kleine Quantencomputer in verschiedenen Städten.
IBM's Vernetzungsdurchbruch
IBM erreichte im November 2025 eine bedeutende Meilensteine in der Vernetzung. Zwei 127-Qubit-Prozessoren wurden zu einem virtuellen 142-Qubit-System verbunden. Diese Entwicklung ebnet den Weg für skalierbare Quantenrechenarchitekturen.
Die Vernetzungstechnologie ermöglicht künftig dezentrale Quantenrechenzentren. Regionale Standorte könnten ihre Ressourcen für komplexe Berechnungen kombinieren. Dies senkt die Einstiegshürden für kleinere Forschungseinrichtungen.
Spezialisierte Hardware-Entwicklungen
Neue Unternehmen entwickeln anwendungsspezifische Quantensysteme für spezielle Einsatzzwecke. Bleximo, Qilimanjaro und QuiX Quantum konzentrieren sich auf optimierte Architekturen. Diese spezialisierte Hardware verspricht bessere Ergebnisse für bestimmte Problemklassen.
Verschiedene Qubit-Technologien im Vergleich
Drei Haupttechnologien konkurrieren derzeit um die Vorherrschaft im Quantencomputing. Supraleitende Qubits benötigen extreme Kühlung, bieten aber hohe Rechenleistung. Photonische Qubits arbeiten bei Raumtemperatur, sind aber komplex herzustellen.
- Supraleitende Qubits (Google, IBM): Hohe Leistung, aber extreme Kühlung
- Photonische Qubits (PsiQuantum, Xanadu): Raumtemperatur-tauglich, komplexe Fertigung
- Ionenfallen-Systeme (IonQ): Hohe Stabilität, aber langsamere Operationen
„Der Wettbewerb zwischen verschiedenen Qubit-Technologien treibt die Innovation voran und beschleunigt die Kommerzialisierung“ – Technologieanalyse 2025
Quantencomputing in der NISQ-Ära
Aktuell befindet sich die Quantentechnologie in der NISQ-Ära (Noisy Intermediate-Scale Quantum). Diese Phase charakterisiert sich durch fehleranfällige Systeme mit begrenzter Qubit-Zahl. Die Skalierbarkeit auf 200-1.000 zuverlässige logische Qubits bleibt die größte Herausforderung.
Zeitrahmen für praktische Anwendungen
Experten erwarten die erste echte Quantum Advantage bis Ende 2026. Diese wird voraussichtlich in mehreren Wellen für verschiedene Anwendungsbereiche eintreten. Die Integration in Consumer Electronics folgt voraussichtlich ab 2030.
Für Endverbraucher bedeutet dies, dass Quantencomputing zunächst über Cloud-Dienste verfügbar wird. Spezialisierte Anwendungen könnten schon früher nutzbar sein. Die direkte Integration in Geräte erfordert jedoch weitere Miniaturisierungsfortschritte.
Die drei Quantencomputer-Technologien im Detail
Aktuell haben sich drei Haupttechnologien für Quantencomputer etabliert, die jeweils unterschiedliche Stärken aufweisen. Jede Technologie adressiert spezifische Anwendungsbereiche und Herausforderungen. Die Wahl der richtigen Plattform hängt von den konkreten Anforderungen ab.
Supraleitende Qubits: Der industrielle Ansatz
Supraleitende Qubits werden von Branchenführern wie Google und IBM bevorzugt. Sie bieten schnelle Rechengeschwindigkeiten und gute Skalierbarkeitseigenschaften. Allerdings erfordern sie aufwändige Kühlsysteme nahe dem absoluten Nullpunkt.
- Arbeitstemperaturen bei etwa 0,015 Kelvin (-273,135°C)
- Gute Integration mit klassischer Halbleitertechnologie
- Hohe Geschwindigkeit bei Quantenoperationen
- Begrenzte Kohärenzzeiten erfordern schnelle Berechnungen
Der entscheidende Vorteil supraleitender Systeme liegt in ihrer Kompatibilität mit bestehenden Fertigungsprozessen. Dies ermöglicht eine schnellere Skalierung und Massenproduktion. Für Consumer-Anwendungen bleiben die Kühlanforderungen jedoch problematisch.
Photonische Quantencomputer: Der vielversprechende Neueinsteiger
Photonische Systeme arbeiten bei Raumtemperatur und nutzen Lichtteilchen als Qubits. Unternehmen wie PsiQuantum und Xanadu verfolgen diesen innovativen Ansatz. Die Technologie verspricht einfachere Integration in bestehende Infrastrukturen.
„Photonische Quantencomputer könnten der Schlüssel zur Integration in Consumer Electronics sein, da sie keine extreme Kühlung benötigen“ – Technologieanalyse 2025
Herausforderungen gibt es bei der Erzeugung und Kontrolle verschränkter Photonen. Die Skalierung auf viele Qubits erweist sich als technisch anspruchsvoll. Dennoch bieten photonische Systeme langfristig das größte Potenzial für mobile Anwendungen.
Ionenfallen-Systeme: Die präzise Lösung
Ionenfallen-Quantencomputer zeichnen sich durch hohe Stabilität und lange Kohärenzzeiten aus. IonQ ist der bekannteste Vertreter dieser Technologie. Geladene Atome werden durch elektromagnetische Felder eingefangen und manipuliert.
- Ausgezeichnete Qubit-Qualität mit geringen Fehlerraten
- Lange Kohärenzzeiten ermöglichen komplexe Algorithmen
- Langsamere Operationsgeschwindigkeiten als supraleitende Systeme
- Komplexe Hardware mit hohen Anschaffungskosten
Quantencomputing-Marktanalyse und regionale Unterschiede
Der globale Quantencomputing-Markt zeigt deutliche regionale Schwerpunkte und Wachstumsunterschiede. Asien-Pazifik führt aktuell bei den Marktanteilen, gefolgt von Nordamerika und Europa. Jede Region verfolgt unterschiedliche Strategien zur Technologieentwicklung.
Asien-Pazifik: Der Wachstumsmotor
Die Region dominiert mit 38% des globalen Marktanteils und zeigt das stärkste Wachstum. China, Japan und Südkorea investieren massiv in Grundlagenforschung und angewandte Entwicklung. Staatliche Förderprogramme treiben die Kommerzialisierung voran.
Besonders bemerkenswert ist die enge Verzahnung von Industrie und Forschung. Unternehmen kooperieren intensiv mit Universitäten und Forschungsinstituten. Diese Synergien beschleunigen die Entwicklung praxistauglicher Lösungen.
Nordamerika: Innovationsführer mit starker Privatwirtschaft
Die USA profitieren von hohen privaten Investitionen und einer traditionsreichen Forschungskultur. Technologiegiganten wie Google, IBM und Microsoft treiben die Entwicklung voran. Das Land verzeichnet die höchste Anzahl an Quanten-Startups weltweit.
- Führend bei Patentanmeldungen im Quantenbereich
- Starke Venture-Capital-Landschaft für Frühphasenfinanzierung
- Enge Zusammenarbeit zwischen Verteidigungssektor und Industrie
- Hohe Ausgaben für Forschung und Entwicklung
Europäische Union: Koordinierte Forschungsanstrengungen
Europa setzt auf koordinierte Initiativen wie die Quantum Flagship Initiative mit 1 Milliarde Euro Budget. Die EU fördert gezielt die Vernetzung zwischen Mitgliedsstaaten. Forschungsschwerpunkte liegen auf Quantenkommunikation und -sensorik.
„Europas Stärke liegt in der exzellenten Grundlagenforschung und der systematischen Förderung von Quantentechnologien“ – EU-Forschungsbericht 2025
Deutschland, Frankreich und die Niederlande gehören zu den aktivsten europäischen Nationen. Allerdings behindert der Fachkräftemangel das Wachstumspotenzial. Bildungsinitiativen sollen diesem Problem entgegenwirken.
Anwendungsszenarien für Consumer Electronics
Trotz aktueller Limitationen zeichnen sich bereits konkrete Anwendungsszenarien für Consumer Electronics ab. Quantencomputing wird zunächst über Cloud-Lösungen verfügbar werden. Später folgt die Integration in Endgeräte für spezielle Aufgaben.
Personalisiertes KI-Erlebnis durch Quantenalgorithmen
Quantencomputer können persönliche Assistenten deutlich intelligenter machen. Sie analysieren Nutzerverhalten mit bisher unerreichter Präzision. Die Ergebnisse sind hochgradig personalisierte Empfehlungen und Vorhersagen.
- Revolutionäre Spracherkennung mit kontextuellem Verständnis
- Predictive Maintenance für Smart Home Geräte
- Echtzeit-Gesundheitsüberwachung mit präzisen Analysen
- Personalisiertes Entertainment durch intelligente Content-Filterung
Die Rechenleistung ermöglicht Echtzeit-Analysen komplexer Datenströme. Nutzer profitieren von nahtlos integrierten digitalen Assistenten. Die Geräte lernen kontinuierlich dazu und passen sich individuell an.
Quantenbeschleunigte Grafik und Gaming
Die Spieleindustrie könnte zu den ersten Nutznießern der Quantentechnologie gehören. Quantencomputer ermöglichen photorealistische Echtzeit-Grafikberechnungen. Komplexe physikalische Simulationen werden in Millisekunden möglich.
Besonders Virtual- und Augmented-Reality-Anwendungen profitieren von dieser Entwicklung. Die Immersion erreicht neue Dimensionen durch präzise Simulationen. Spieler erleben bisher unmögliche Realitätsgrade in Echtzeit.
„Quantenbeschleunigte Grafik wird das Spielerlebnis revolutionieren und neue Maßstäbe für Immersion setzen“ – Gaming-Industrie-Report 2025
Sicherheit und Quantenkryptografie
Quantencomputer stellen zwar eine Bedrohung für heutige Verschlüsselung dar, bieten aber gleichzeitig Lösungen. Quantenkryptografie ermöglicht abhörsichere Kommunikation für Consumer Devices. Diese Technologie wird besonders für mobile Zahlungen und Datenschutz relevant.
- Quantenschlüsselaustausch für abhörsichere Kommunikation
- Quanten-zertifizierte Authentifizierung für Geräte und Nutzer
- Future-Proof-Verschlüsselung gegen Quantenangriffe
- Dezentrale Identitätsmanagement-Systeme mit Quantensicherheit
Die Integration quantensicherer Verfahren wird zunächst in High-End-Geräten erfolgen. Mit der Zeit werden diese Technologien zum Standard für alle Consumer Electronics. Nutzer profitieren von bisher unerreichter Datensicherheit.
Herausforderungen für die Consumer-Integration
Die Integration von Quantencomputing in Consumer Electronics steht vor erheblichen Hürden. Technische, wirtschaftliche und praktische Probleme müssen gelöst werden. Die größten Herausforderungen betreffen Größe, Kosten und Energieverbrauch.
Miniaturisierung und Energieeffizienz
Aktuelle Quantencomputer benötigen raumfüllende Kühl- und Steuersysteme. Für mobile Geräte sind drastische Verkleinerungen notwendig. Gleichzeitig muss der Energieverbrauch auf tragbare Level reduziert werden.
Forscher arbeiten an neuartigen Kühlmethoden und Materialien. Quantenprozessoren der nächsten Generation sollen bei höheren Temperaturen arbeiten. Diese Entwicklung ist essentiell für den Einsatz in Consumer Devices.
Kosten-Nutzen-Verhältnis und Massenmarkt
Die Herstellungskosten für Quantenchips liegen derzeit im Millionenbereich. Für Consumer-Anwendungen müssen die Kosten dramatisch sinken. Skaleneffekte und verbesserte Fertigungsprozesse sind notwendig.
- Aktuelle Chipkosten: Mehrere Millionen Dollar pro Einheit
- Zielkosten für Consumer Devices: Unter 100 Dollar
- Erforderliche Skalierung: Faktor 10.000+ notwendig
- Zeithorizont für Wirtschaftlichkeit: Vor 2035 unrealistisch
Erst wenn Quantencomputing einen klaren Mehrwert für Alltagsanwendungen bietet, wird die Massenproduktion wirtschaftlich. Bis dahin dominieren Cloud-Lösungen und spezialisierte Enterprise-Anwendungen.
Unternehmensbeispiele und Investitionsmöglichkeiten
Die dynamische Quantencomputing-Branche bietet zahlreiche spannende Unternehmensbeispiele. Von etablierten Tech-Giganten bis zu innovativen Startups gestalten verschiedene Akteure die Zukunft. Anleger und Technologiebeobachter verfolgen diese Entwicklungen mit großem Interesse.
Etablierte Technologiekonzerne auf dem Quantenpfad
Unternehmen wie IBM, Google und Microsoft investieren Milliarden in die Quantenentwicklung. Sie verfügen über tiefe Forschungskapazitäten und breite Ressourcen. Ihre Cloud-basierten Quantendienste machen die Technologie bereits heute zugänglich.
- IBM Quantum Network verbindet über 250 Organisationen weltweit
- Google Quantum AI demonstrierte erstmals Quantenüberlegenheit
- Microsoft Azure Quantum bietet plattformübergreifende Quantendienste
- Amazon Braket ermöglicht Experimente mit verschiedenen Quantencomputern
Diese Unternehmen treiben die Standardisierung von Quantenalgorithmen und Programmierschnittstellen voran. Sie schaffen Ökosysteme, die künftig auch Consumer-Anwendungen ermöglichen werden. Ihre Investitionen sichern langfristige Marktführerschaft.
Spezialisierte Startups mit innovativen Ansätzen
Neben den großen Playern existieren zahlreiche spezialisierte Quanten-Startups. Diese Unternehmen konzentrieren sich oft auf Nischenlösungen oder bestimmte Technologiepfade. Ihre Agilität ermöglicht schnelle Innovationen.
„D-Wave verzeichnete 2025 einen Aktienkursanstieg von über 200% und prognostiziert ein Umsatzwachstum von 73% CAGR bis 2030“ – Finanzmarktanalyse 2025
Q-CTRL arbeitet mit Nvidia und Oxford Quantum Circuits an Fehlerunterdrückung. Das Unternehmen entwickelt Software zur Stabilisierung von Quantenberechnungen. Solche Lösungen sind entscheidend für praktische Anwendungen.
Die drei Säulen der Quantentechnologie
Quantencomputing ist nur eine von drei tragenden Säulen der Quantentechnologie. Quantum Sensing und Quantum Communication ergänzen die Rechenkapazitäten. Zusammen bilden sie ein umfassendes quantentechnologisches Ökosystem.
Quantum Sensing: Präzision jenseits klassischer Grenzen
Quantensensoren erreichen Messgenauigkeiten, die klassische Systeme um Größenordnungen übertreffen. Diese Technologie findet bereits Anwendung in Medizin, Verteidigung und Halbleiterindustrie. Für Consumer Electronics eröffnen sich faszinierende Möglichkeiten.
- Medizinische Bildgebung mit atomarer Auflösung
- Präzisionsnavigation ohne GPS-Signal
- Frühzeitige Krankheitsdiagnose durch molekulare Sensoren
- Materialanalyse in Echtzeit für Qualitätskontrolle
Die Miniaturisierung von Quantensensoren schreitet schneller voran als bei Quantencomputern. Erste Consumer-Anwendungen könnten daher im Sensing-Bereich entstehen. Smartphones mit Quantensensoren wären in der Lage, Umgebungsdaten mit bisher unerreichter Präzision zu erfassen.
Quantum Communication: Absolut abhörsichere Datenübertragung
Quantenkommunikation nutzt Quantenverschränkung für abhörsichere Datenverbindungen. Regierungen waren mit 57% der Käufe im Jahr 2024 die wichtigsten frühen Adopter. Telekommunikationsunternehmen werden bis 2035 voraussichtlich 26% des Marktes ausmachen.
Für Consumer Electronics bedeutet dies revolutionäre Sicherheitsstandards. Mobile Kommunikation, Finanztransaktionen und persönliche Daten wären vor allen bekannten Angriffsmethoden geschützt. Die Technologie bildet die Grundlage für vertrauenswürdige digitale Ökosysteme.
Zukunftsprognose: Der Weg in Consumer-Geräte
Der Weg von heutigen Forschungslaboren zu morgenigen Consumer-Geräten verläuft in mehreren deutlich definierten Phasen. Jede Phase bringt spezifische Fortschritte und Anwendungen. Experten erwarten einen allmählichen Übergang zwischen diesen Entwicklungsstufen.
Phase 1: Cloud-basierter Zugang (2025-2030)
In dieser Phase nutzen Consumer-Anwendungen Quantencomputing ausschließlich über Cloud-Dienste. Smartphones und andere Geräte senden Rechenprobleme an entfernte Quantenrechenzentren. Die Ergebnisse werden zurück an die Geräte übermittelt.
- AI-Assistenten mit quantenbeschleunigter Sprachverarbeitung
- Personalisiertes Medizin durch komplexe biologische Simulationen
- Echtzeit-Übersetzung mit kulturellem Kontextverständnis
- Individuelle Lernpfade durch adaptive Bildungsalgorithmen
Diese Phase beginnt bereits heute mit ersten experimentellen Diensten. Bis 2030 könnten Cloud-Quantenrechenleistungen zum Standard für Premium-Services werden. Die Infrastruktur entwickelt sich parallel zu 5G-Advanced und 6G-Netzen.
Phase 2: Hybrid-Systeme mit Edge-Quantenunterstützung (2030-2035)
Spezialisierte Quantenchips erscheinen in leistungsstarken Endgeräten. Diese arbeiten zusammen mit klassischen Prozessoren für bestimmte Aufgaben. High-End-Smartphones, AR-Brillen und autonome Fahrzeuge integrieren erste Quantenkomponenten.
„Bis 2035 könnte der durch Quantencomputing generierte Umsatz 72 Milliarden US-Dollar erreichen – gegenüber 4 Milliarden US-Dollar im Jahr 2024“ – McKinsey Prognose
Die Quantenchips dieser Generation sind spezialisiert auf bestimmte Algorithmen. Sie verbessern KI-Inferenz, Kryptografie oder komplexe Simulationen lokal auf dem Gerät. Der Energieverbrauch bleibt hoch, beschränkt die Nutzung aber auf spezielle Anwendungsfälle.
Phase 3: Integrierte Quantensysteme (nach 2035)
Vollständige Quantenprozessoren werden in Alltagsgeräten integriert. Die Technologie erreicht Wirtschaftlichkeit für Massenmarktprodukte. Quantencomputing wird zu einer Standardfunktion wie heute GPS oder Biometrie.
- Allgegenwärtige Quanten-KI in persönlichen Geräten
- Quantensichere Identität für alle digitalen Interaktionen
- Echtzeit-Umgebungssimulation für erweiterte Realität
- Persönliche Gesundheitsüberwachung mit molekularer Präzision
Diese Phase erfordert bahnbrechende Fortschritte in Miniaturisierung und Energieeffizienz. Materialwissenschaften und Fertigungstechnologien müssen Quantenchips massenmarkttauglich machen. Der Übergang wird schrittweise über Premium- hin zu Mainstream-Geräten erfolgen.
Herausforderungen und Risiken der Verbraucherintegration
Trotz des enormen Potenzials bleiben erhebliche Herausforderungen für die Consumer-Integration bestehen. Technische Hürden müssen ebenso überwunden werden wie wirtschaftliche und ethische Fragen. Eine realistische Betrachtung ist für nachhaltige Entwicklung essentiell.
Technische und wirtschaftliche Hürden
Die hohen Kosten für Entwicklung und Fertigung limitieren aktuell den Masseneinsatz. Quantensysteme benötigen außerdem spezialisierte Programmierung und Wartung. Die Integration in bestehende Produktökosysteme stellt eine komplexe Herausforderung dar.
- Fachkräftemangel: 61% der Unternehmen berichten von Engpässen
- Technologiereife: 56% sehen unreife Technologie als größte Hürde
- Hardwarekosten: 41% nennen teure Hardware als limitierenden Faktor
- Softwareentwicklung: Spezialisierte Quantenprogrammierung erforderlich
Diese Herausforderungen erfordern koordinierte Anstrengungen von Industrie, Forschung und Regierungen. Bildungsinitiativen müssen mehr Quanteningenieure ausbilden. Standardisierungsgremien müssen interoperable Schnittstellen definieren.
Ethische Implikationen und gesellschaftliche Auswirkungen
Quantencomputing in Consumer Electronics wirft wichtige ethische Fragen auf. Die immense Rechenleistung könnte für Überwachung oder Manipulation missbraucht werden. Gesellschaftliche Regulierung muss mit der technologischen Entwicklung Schritt halten.
Datenschutz und digitale Souveränität gewinnen noch stärker an Bedeutung. Verbraucher müssen vor Quanten-angreifbarer Verschlüsselung geschützt werden. Gleichzeitig gilt es, den demokratischen Zugang zu dieser Schlüsseltechnologie zu sichern.
Fazit: Die transformative Zukunft der Consumer Electronics
Die Integration von Quantencomputing in Consumer Electronics markiert einen der bedeutendsten technologischen Übergänge unserer Zeit. Diese Entwicklung wird nicht abrupt, sondern evolutionär über die nächsten Jahrzehnte verlaufen. Die Auswirkungen werden ebenso tiefgreifend sein wie die Einführung des Internets oder Smartphones.
In der ersten Phase dominieren Cloud-basierte Quantendienste, die spezielle Anwendungen ermöglichen. High-End-Geräte werden ab 2030 erste spezialisierte Quantenkomponenten integrieren. Ab 2035 könnten vollwertige Quantensysteme in Mainstream-Produkten erscheinen.
„Der Quantencomputing-Markt wird von 1,6 Milliarden USD im Jahr 2024 auf 31,26 Milliarden USD bis 2031 wachsen – eine durchschnittliche jährliche Wachstumsrate von 34,8%“ – Insightace Analytic Prognose
Die erfolgreiche Integration hängt von der Überwindung mehrerer kritischer Hürden ab. Miniaturisierung, Energieeffizienz und Kostenreduktion sind technische Schlüsselfaktoren. Gleichzeitig müssen ethische Rahmenbedingungen und Sicherheitsstandards entwickelt werden.
Die Zukunft der Consumer Electronics wird quantenbeschleunigt sein. Persönliche Geräte werden über Fähigkeiten verfügen, die heute wie Science-Fiction erscheinen. Von ultrapersonalisierter KI bis zu absolut sicheren Kommunikationssystemen wird Quantentechnologie das digitale Leben fundamental transformieren. Die Reise hat gerade erst begonnen, und ihre Destination verspricht eine Welt intelligenterer, sichererer und tiefgreifend persönlicher technologischer Begleiter.


Drakon: The First Legal and Accounting Canon in Athens
The ancient Greek phrase Drakwn-O-Prwtos-Logismikos-Kanona-Sthn-A8hna translates to "Draco: The First Accounting Canon in Athens." It refers to the revolutionary legal code established by the lawgiver Draco around 621 BCE. This was the earliest written constitution for Athens, marking a pivotal shift from unwritten aristocratic judgments to a codified public standard. The term kanón, meaning a rule or measuring rod, underscores its role as the foundational benchmark for justice, debt, and societal order.
The Historical Dawn of Codified Law in Athens
Before Draco's reforms, justice in Archaic Athens was administered orally by the aristocracy. This system was often arbitrary and fueled bloody feuds between powerful families. Draco's mandate was to establish a clear, publicly known set of rules to quell social unrest and provide stability. His code, inscribed on wooden tablets called axones displayed in the Agora, represented a seismic shift toward the rule of law.
The primary motivation was to standardize legal proceedings and penalties. By writing the laws down, Draco made them accessible, at least in principle, to a wider populace beyond the ruling elite. This act of codification itself was more revolutionary than the specific laws' content. It laid the indispensable groundwork for all subsequent Athenian legal development, including the more famous reforms of Solon.
Draco's code applied to an estimated 300,000 Athenians and was read aloud publicly each year, ensuring communal awareness of the legal "measuring rod" against which all were judged.
Decoding the "Kanón": From Measuring Rod to Legal Standard
The core concept within the phrase is kanón (κανών). Originally, this word referred to a literal reed or rod used for measurement. In Draco's context, it took on a profound metaphorical meaning: a fixed standard, principle, or boundary for human conduct. This linguistic evolution reflects the move from physical to societal measurement.
As a legal term, kanón established the "lines" that could not be crossed without consequence. This foundational idea of a legal canon later influenced Western thought profoundly. The concept evolved through history, later used in the New Testament to describe spheres of authority and by early church fathers to define the official canon of scripture.
The Severe Content of Draco's Legal Code
Draco's laws were comprehensive for their time, covering critical areas of civil and criminal life. The code addressed homicide, assault, property theft, and the pressing issue of debt slavery. Its primary aim was to replace private vengeance with public justice, thereby reducing clan-based violence. However, its legacy is overwhelmingly defined by its extreme severity.
Penalties were notoriously harsh and famously lacked gradation. The laws made little distinction between major crimes and minor offenses in terms of punishment. This blanket approach to justice is what gave the English language the enduring adjective "draconian," synonymous with excessively harsh and severe measures.
Key areas covered by the code included:
- Homicide Laws: These were the most sophisticated and long-lasting parts of Draco's code. They distinguished between premeditated murder, involuntary homicide, and justifiable killing, each with specific legal procedures.
- Property and Debt: Laws addressed theft and the practice of debt slavery, where defaulting debtors could be enslaved by creditors—a major source of social tension.
- Judicial Procedure: The code formally outlined legal processes, transferring judgment from private individuals to public officials and courts.
The Infamous "Draconian" Penalties
Historical accounts suggest a staggering proportion of Draco's laws mandated capital punishment. It is estimated that roughly 80% of prescribed penalties involved death or permanent exile. Ancient sources famously claimed that Draco justified this severity because even minor offenses deserved death, and he had no greater penalty for major crimes.
For example, the penalty for stealing a cabbage could be the same as for murder. This lack of proportionality was the code's greatest flaw. While it successfully established the principle that law was supreme, its brutal equity undermined its fairness. The severity was likely intended to deter crime absolutely in a turbulent society, but it ultimately proved unsustainable.
Only an estimated 5-10% of Draco's original laws survive today, primarily through fragments quoted by later orators like Demosthenes, who referenced them in 4th-century BCE legal speeches.
Modern Rediscovery and Digital Reconstruction
The 21st century has seen a renaissance in the study of Draco's code through digital humanities. With no major archaeological discoveries of the original axones in recent decades, scholars have turned to technology to reconstruct and analyze the surviving text. Projects spanning 2023 to 2025 have leveraged new tools to deepen our understanding.
Major digital libraries, including the Perseus Digital Library, have implemented updates using AI and computational linguistics. These tools help transcribe, translate, and cross-reference the scant fragments that remain. This digital revival allows for a more nuanced analysis, connecting Draco's laws to broader patterns in ancient Mediterranean legal history.
2024-2025 Academic Trends and Debates
Current scholarly discourse, reflected in journals like Classical Quarterly, is revisiting Draco's complex legacy. The debate moves beyond simply labeling him as harsh. Modern analysis examines his role in the democratization of law, asking how a severe code could also be a foundational step toward equality before the law.
Researchers are increasingly taking a comparative approach. They analyze parallels between Draco's code and other ancient legal systems, such as the Code of Hammurabi. Furthermore, 2024 studies utilize computational models to hypothesize the content of lost statutes based on the socio-economic conditions of 7th-century BCE Athens.
The cultural impact remains significant. In 2025, museums in Athens featured exhibitions on the origins of democracy, prominently highlighting Draco's code as the starting point. These exhibitions frame the ancient laws within contemporary global discussions about the rule of law, justice, and social order.
Draco's Homicide Laws: The Enduring Legal Legacy
While most of Draco's code was repealed, his legislation concerning homicide proved to be its most sophisticated and lasting contribution. These laws represented a significant advancement in legal thought by introducing the critical concept of intent. For the first time in Athenian law, a formal distinction was made between different types of killing, each carrying its own specific legal consequence and procedure.
The code categorized homicide into several types, including premeditated murder, involuntary manslaughter, and justifiable homicide. This nuanced approach prevented the cyclical blood feuds that had previously plagued Athenian society. By establishing a public legal process for adjudicating murders, Draco's laws transferred the right of retribution from the victim's family to the state. This was a monumental step toward a more orderly and centralized judicial system.
The Legal Machinery for Murder Cases
The procedures outlined by Draco were elaborate and designed to ensure a measured response. For a charge of intentional murder, the case was brought before the Areopagus Council, a venerable body of elders that met on the Hill of Ares. This council served as the supreme court for the most serious crimes, reflecting the gravity of taking a life.
In cases of involuntary homicide, the penalty was typically exile, but without the confiscation of the perpetrator's property. This distinction prevented the complete ruin of a family due to an accidental death. The law even provided a mechanism for pardon if the victim's family agreed, offering a path to reconciliation and an end to the feud.
Draco's homicide laws were so well-regarded for their fairness and precision that Solon intentionally preserved them intact during his extensive legal reforms in 594 BCE, a testament to their foundational quality.
The Socio-Economic Context of 7th Century BCE Athens
To fully understand Draco's code, one must examine the volatile social climate that necessitated it. Athens in the 7th century BCE was characterized by deep social stratification and economic disparity. A small aristocracy, the Eupatridae, held most of the political power and wealth, while the majority of the population, including small farmers and artisans, struggled under the weight of debt.
The prevailing system of debt was particularly oppressive. Farmers who borrowed seed or money from wealthy nobles often used their own freedom as collateral. Widespread crop failures or poor harvests could lead to debt slavery, where the debtor and their entire family could be enslaved by the creditor. This created a powder keg of social resentment that threatened to tear the city-state apart.
Key social groups in this period included:
- The Eupatridae (Aristocrats): Held hereditary political power and vast landed estates.
- The Georgoi (Farmers): Small-scale landowners who were vulnerable to debt and enslavement.
- The Demiurgoi (Artisans): Craftsmen and traders who had wealth but little political influence.
Draco's Response to the Debt Crisis
Draco's laws did address the issue of debt, though his solutions were characteristically severe. The code formalized the rules surrounding debt and property rights, which, in theory, offered some predictability. However, it did little to alleviate the underlying causes of the crisis. The laws upheld the rights of creditors, thereby legitimizing the system of debt slavery that was a primary source of unrest.
This failure to resolve the core economic grievances meant that while Draco's code provided a framework for public order, it did not bring about social justice. The tension between the wealthy few and the indebted many continued to simmer, setting the stage for the more radical economic reforms that Solon would later be forced to implement.
The Archaeological and Textual Evidence for Draco's Code
One of the greatest challenges in studying Draco's laws is their fragmentary survival. The original wooden axones on which the laws were inscribed have long since decayed. Our knowledge comes entirely from secondary sources, primarily later Greek writers who quoted the laws for their own purposes. No single, continuous text of the code exists today.
The most significant sources are the speeches of 4th-century BCE orators, such as Demosthenes and Aristotle's work, The Constitution of the Athenians. These authors quoted Draco's laws to make arguments about their own contemporary legal issues. Scholars have painstakingly pieced together these quotations to reconstruct approximately 21 identifiable fragments of the original code.
Despite its historical importance, the physical evidence is minimal. Scholars estimate that we have access to less than 10% of the original text of Draco's legislation, making full understanding of its scope a challenging task.
The Role of Axones and Kyrbeis
The physical form of the law was as innovative as its content. The laws were inscribed on a set of revolving wooden tablets or pillars known as axones (or sometimes kyrbeis). These were mounted on axles so that they could be rotated, allowing citizens to read the laws written on all sides. They were displayed prominently in a public space, likely the Agora, the civic heart of Athens.
This public display was a revolutionary act. It symbolized that the law was no longer the secret knowledge of the aristocracy but belonged to the entire citizen body. It made the legal kanón—the standard—visible and accessible, embodying the principle that ignorance of the law was no longer an excuse.
Draco in Comparative Legal History
Placing Draco's code in a wider historical context reveals its significance beyond Athens. It was part of a broader Mediterranean trend in the first millennium BCE toward the codification of law. The most famous predecessor was the Code of Hammurabi from Babylon, dating back to 1754 BCE, which was also inscribed on a public stele for all to see.
However, there are crucial differences. While Hammurabi's code was divinely sanctioned by the sun god Shamash, Draco's laws were a purely human creation, established by a mortal lawgiver. This secular foundation is a hallmark of the Greek approach to law and governance. Furthermore, Draco's focus was more narrowly on establishing clear, fixed penalties to curb social chaos.
Key points of comparison with other ancient codes:
- Code of Hammurabi (Babylon): Older and more comprehensive, based on the principle of "an eye for an eye," but also featured class-based justice where penalties varied by social status.
- Draco's Code (Athens): Noted for its uniform severity across social classes, applying the same harsh penalties to aristocrats and commoners alike, a form of brutal equality.
- Roman Twelve Tables (5th Century BCE): Later Roman code, also created to appease social unrest by making laws public and applicable to both patricians and plebeians.
The Uniqueness of Athenian Legal Innovation
What sets Draco apart is his role in a specific evolutionary path. His code was the first critical step in a process that would lead to Athenian democracy. By creating a written, public standard, he initiated the idea that the community, not a king or a small oligarchy, was the source of legal authority. This trajectory from Draco's severe code to Solon's reforms and eventually to the full democracy of the 5th century illustrates a unique experiment in self-governance.
Solon's Reforms and the Overthrow of Draconian Severity
The harshness of Draco's laws proved unsustainable in the long term. By 594 BCE, Athens was again on the brink of civil war due to unresolved economic grievances. Into this crisis stepped Solon, appointed as archon with broad powers to reform the state. His mission was to create a more equitable society and legal system, which necessitated the dismantling of the most severe aspects of Draco's code.
Solon famously enacted a sweeping set of reforms known as the Seisachtheia, or "shaking-off of burdens." This radical measure canceled all outstanding debts, freed those who had been enslaved for debt, and made it illegal to use a citizen's person as collateral for a loan. This directly tackled the economic oppression that Draco's laws had failed to resolve. Solon replaced Draco's rigid penalties with a system of tiered fines proportional to the crime and the offender's wealth.
What Solon Kept and What He Discarded
Solon's genius lay in his selective approach. He recognized the foundational value of Draco's homicide laws, which provided a clear and effective legal process for the most serious crime. Consequently, he preserved Draco's legislation on murder almost in its entirety. This decision underscores that the problem was not the concept of written law itself, but rather the excessive and ungraded punishments for other offenses.
For all other matters, Solon created a new, more humane legal code. He introduced the right of appeal to the popular court (heliaia), giving citizens a voice in the judicial process. This move away from absolute aristocratic control was a direct evolution from Draco's initial step of public codification, pushing Athens further toward democratic principles.
Solon’s reforms demonstrated that while Draco provided the essential framework of written law, it required a more compassionate and socially conscious application to achieve true justice and stability.
The Evolution of the Legal "Kanón" Through History
The concept of kanón, so central to Draco's achievement, did not remain static. Its meaning expanded and evolved significantly over the centuries. From a literal measuring rod and a legal standard, it grew into a foundational idea in religion, art, and intellectual life. This evolution tracks the journey of Greek thought from the concrete to the abstract.
In the Classical and Hellenistic periods, kanón came to denote a standard of excellence or a model to be imitated. The famous sculptor Polykleitos wrote a treatise called "The Kanon," which defined the ideal mathematical proportions for the perfect human form. This illustrates how the term transitioned from governing human action to defining aesthetic and philosophical ideals.
The key evolutions of the term include:
- Legal Standard (Draco): A fixed, public rule for conduct and penalty.
- Artistic Principle (Classical Greece): A model of perfection and proportion in sculpture and architecture.
- Theological Canon (Early Christianity): The officially accepted list of books in the Bible, the "rule" of faith.
- Academic Canon (Modern Era): The body of literature, art, and music considered most important and worthy of study.
The Theological Adoption of the Kanón
The most significant transformation occurred in early Christian theology. Church fathers adopted the Greek term to describe the rule of faith and, most famously, the "canon" of Scripture—the definitive list of books recognized as divinely inspired. The Apostle Paul himself used the term in 2 Corinthians 10:13-16 to describe the "measure" or "sphere" of ministry God had assigned to him.
This theological usage directly parallels Draco's original intent: to establish a clear, authoritative boundary. For Draco, it was the boundary of lawful behavior; for the Church, it was the boundary of orthodox belief and sacred text. This lineage shows the profound and enduring influence of the legal concept born in 7th-century Athens.
The Modern Legacy: From Ancient Athens to Today
The legacy of Draco's code is a paradox. On one hand, it is synonymous with cruelty, giving us the word "draconian." On the other, it represents the groundbreaking idea that a society should be governed by public, written laws rather than the whims of powerful individuals. This dual legacy continues to resonate in modern legal and political discourse.
Today, "draconian" is routinely used by journalists, activists, and politicians to criticize laws perceived as excessively harsh, particularly those involving mandatory minimum sentences, severe censorship, or stringent security measures. The term serves as a powerful rhetorical tool, instantly evoking a warning against the dangers of legal severity devoid of mercy or proportionality.
The enduring power of the term "draconian" demonstrates how an ancient lawgiver's name has become a universal benchmark for judicial harshness over 2,600 years later.
Draco in Contemporary Culture and Education
Draco's story remains a staple of educational curricula worldwide when teaching the origins of Western law. It provides a clear and dramatic starting point for discussions about the rule of law, justice, and the balance between order and freedom. In popular culture, references to Draco or draconian measures appear in literature, film, and television, often to illustrate tyrannical governance.
Modern digital projects ensure this legacy continues. Virtual reality reconstructions of ancient Athens allow users to "stand" in the Agora and view recreations of the axones. These immersive experiences, combined with online scholarly databases, make the study of Draco's laws more accessible than ever, bridging the gap between ancient history and contemporary technology.
Conclusion: The Foundational Paradox of Draco's Code
In conclusion, the significance of Drakwn-O-Prwtos-Logismikos-Kanona-Sthn-A8hna cannot be overstated. Draco's code represents a foundational moment in human history, the moment a society decided to write down its rules for all to see. It established the critical principle that law should be a public standard, a kanón, applied equally to all citizens. This was its revolutionary and enduring contribution.
However, the code is also a cautionary tale. Its severe, undifferentiated penalties highlight the danger of pursuing order without justice. The fact that Solon had to repeal most of it just a generation later proves that a legal system must be rooted in fairness and social reality to be sustainable. The code's greatest strength—its firm establishment of written law—was also its greatest weakness, as it was a law without nuance.
The key takeaways from Draco's legacy are clear:
- Written Law is foundational to a stable and predictable society.
- Proportionality in justice is essential for long-term social harmony.
- Legal evolution is necessary, as laws must adapt to changing social and economic conditions.
- The concept of a public standard (kanón) for behavior has influenced Western thought for millennia.
Draco's laws, therefore, stand as a monumental first step. They were flawed, harsh, and ultimately inadequate for creating a just society. Yet, they ignited a process of legal development that would lead, through Solon, Cleisthenes, and Pericles, to the birth of democracy. The story of Draco is the story of beginning—a difficult, severe, but essential beginning on the long road to the rule of law.
Édouard Branly: The Radio Coherer Inventor
The pioneering work of French physicist Édouard Branly fundamentally shaped modern communication. Best known as the inventor of the coherer, his device was the first practical detector of radio waves. This crucial component enabled the breakthrough of wireless telegraphy.
His 1890 discovery of radioconduction unlocked a new era of technology. Today, Branly is celebrated as a foundational figure in the history of radio and electrical engineering.
Early Life and Academic Foundations
Édouard Branly was born on October 23, 1844, in Amiens, France. His intellectual journey was marked by a profound dedication to both science and medicine. He pursued higher education with remarkable vigor, earning two separate doctoral degrees.
He received his doctorate in physical sciences in 1873. Nearly a decade later, in 1882, he also earned a doctorate in medicine. This dual expertise uniquely positioned him for interdisciplinary research.
Education and Dual Doctorates
Branly's educational path was exceptional. His deep understanding of physics provided the theoretical basis for his inventions. His medical training later informed his parallel career in therapeutic practices.
This combination of disciplines was uncommon for the time. It allowed Branly to approach problems from multiple angles. His work often bridged the gap between pure science and practical application.
Teaching Career at Catholic University
In 1875, Branly began his long tenure as a professor of physics. He taught at the Catholic University of Paris for over 50 years. His commitment to education influenced generations of students.
His academic role provided a stable platform for his experimental research. Throughout his life, he balanced teaching, invention, and a medical practice. This multifaceted career defined his professional legacy.
The Path to the Coherer Discovery
Branly's most famous invention did not emerge in a vacuum. It was the culmination of earlier scientific observations and his own meticulous experiments. The key phenomenon he explored was the effect of electromagnetic waves on materials.
Precursors and Influential Experiments
Several scientists paved the way for Branly's breakthrough. In 1879, David Hughes observed that his carbon microphone was sensitive to electrical disturbances. Later, in 1884, Temistino Calzecchi-Onesti noted that metal filings conducted electricity under an electromotive force.
The most direct inspiration came from Heinrich Hertz. In 1888, Hertz conclusively demonstrated the existence of electromagnetic waves. Branly aimed to find a reliable method to detect these mysterious "Hertzian waves."
Branly refined a simple tube of metal filings into the first practical radio wave detector, presenting his coherer to the Académie des Sciences in 1890.
The Eureka Moment: Radioconduction
Branly's crucial experiment involved a circuit containing loose metal filings. Normally, these filings exhibited high electrical resistance. When exposed to electromagnetic waves from a spark gap transmitter, they suddenly cohered.
This dramatic drop in resistance allowed current to flow. Branly termed this effect radioconduction. He had discovered a repeatable and detectable response to radio waves.
- Key Component: A glass tube filled with metal filings (often nickel-silver).
- Key Behavior: High resistance normally, low resistance when activated by radio waves.
- Key Innovation: The "decoherer" mechanism, often a small tapper, to reset the filings.
Invention of the Branly Coherer
Branly transformed his observation into a functional device around 1890. The Branly Coherer became the first widely used radio wave detector. It was simple in construction yet revolutionary in impact.
The basic setup included a transmitter with a spark gap and a receiver circuit containing the coherer. A demonstration for the Académie des Sciences showed signals could be sent without wires. This was the seminal moment for practical wireless telegraphy.
How the Coherer Worked
The operation of the coherer was elegantly straightforward. In its resting state, the loose metal filings barely conducted electricity. An incoming radio wave induced a small current between the metal particles.
This caused them to cling together or cohere, forming a better conductive path. The sudden drop in resistance could then trigger a relay or sounder. To reset the device for the next signal, a light tap would separate the filings again.
Immediate Impact and Adoption
The invention was rapidly adopted and improved by other wireless pioneers. British physicist Oliver Lodge incorporated it with Hertzian oscillators. He also coined the term "coherer" that we use today.
Most famously, Guglielmo Marconi used refined versions of the coherer in his groundbreaking long-distance experiments. Marconi publicly credited Branly's foundational work after his successful cross-Channel transmission in 1899.
Honors and Recognition During His Lifetime
Édouard Branly received significant acclaim for his contributions to science. His honors reflect the high esteem in which he was held by both academic and national institutions.
Prestigious Awards and Prizes
Branly's work was recognized with several major prizes. He won the grand prix at the monumental 1900 Paris Exposition. This placed him at the forefront of technological innovation at the dawn of the 20th century.
In 1903, he was awarded the prix Osiris, then one of France's most prestigious scientific awards. These accolades cemented his reputation as a leading inventor and physicist of his era.
National and Papal Honors
The French government honored him with the Legion of Honour. He achieved the high ranks of Officer and later Grand Croix. In 1899, he also received the title of Commander of the Order of St. Gregory the Great from the Pope.
His devout Catholic faith was an integral part of his life. This papal recognition was personally significant. It highlighted the harmony he saw between his faith and his scientific pursuits.
Branly's discovery was designated an IEEE Milestone in Electrical Engineering and Computing in 2010, over a century after his invention.
Legacy of the Coherer in Wireless Telegraphy
The coherer was the enabling technology for the first generation of wireless communication. Before its invention, detecting radio waves was a difficult laboratory exercise. Branly's device made reliable wireless signaling a practical reality.
Its simplicity and effectiveness spurred rapid international development. Inventors like Marconi, Lodge, and Popov integrated coherers into their systems. This directly led to the first transatlantic wireless signal in 1901.
From Laboratory Curiosity to Global Communication
Branly's initial demonstration was a short-range experiment. However, it proved a fundamental principle: electromagnetic waves could be used to transmit information. Engineers quickly scaled this concept for real-world use.
Marconi's famous improvements focused on increasing the range and reliability of transmission. The core detection mechanism, however, remained the coherer for many critical early years. It was the heart of the first commercial and maritime wireless sets.
- Maritime Safety: Coherer-based radios became standard on ships, leading to famous rescues like the RMS Titanic in 1912.
- Military Adoption: Navies worldwide adopted wireless telegraphy for fleet coordination, revolutionizing naval strategy.
- News Reporting: Wireless reports from international correspondents sped up global news dissemination dramatically.
Technical Refinements and Obsolescence
The coherer, while revolutionary, had inherent limitations. It was a relatively slow device, insensitive to weak signals, and required mechanical resetting. By around 1907, more sensitive detectors like the crystal diode and later the vacuum tube began to replace it.
These new technologies enabled voice transmission (radio telephony) and more complex broadcasting. The coherer's role was foundational but brief, marking the explosive infancy of wireless. Its historical importance, however, remains unparalleled.
Guglielmo Marconi explicitly credited Branly after the 1899 Dover-Boulogne transmission, sending a telegram that stated his historic signal used "Branly's apparatus."
Branly's Other Scientific Research and Medical Work
While the coherer defines his legacy, Édouard Branly was a prolific researcher in multiple fields. His dual doctorates fueled a career split between advanced physics and medical therapy. He published significant work on topics ranging from electrical capacitance to human physiology.
This interdisciplinary approach was a hallmark of his intellect. He saw connections between physical phenomena and biological systems. His medical practice specialized in the emerging fields of electrotherapy and physiotherapy.
Contributions to Physics and Instrumentation
Beyond radioconduction, Branly conducted detailed studies on electrical resistance in thin films. He investigated the properties of platinum deposited on glass. This work contributed to the broader understanding of materials science.
He was also an ingenious designer of scientific instruments and demonstrations. His skill lay in creating clear, effective apparatus to illustrate complex principles. Many of these devices were used in his long teaching career at the Catholic University.
A Pioneering Electrotherapist
Branly ran a medical clinic where he applied electrical currents for therapeutic purposes. This practice, known as electrotherapy, was a novel field in the late 19th century. He treated patients using techniques derived from his deep understanding of electricity.
His medical work was not separated from his physics research. Instead, he sought scientifically rigorous applications for electrical energy in medicine. He represents an early model of the physician-scientist, bridging two demanding professions successfully.
Later Life, Faith, and Historical Recognition
Édouard Branly lived a long life, witnessing the global transformation his invention helped initiate. He remained active in academia and his medical practice well into his later years. His Catholic faith was a central pillar of his identity and worldview.
He passed away on March 24, 1940, in Paris. His funeral was a national event, reflecting his status as a French scientific hero. His legacy is preserved through numerous honors and educational references.
A Devout Catholic in the Scientific Community
In an era sometimes marked by tension between faith and science, Branly saw no conflict. He was a committed Catholic who integrated his religious beliefs with his scientific pursuits. This harmony was recognized by the Vatican, which bestowed upon him a high papal honor.
He served as a prominent example that rigorous scientific inquiry and devout religious faith could coexist. His life challenged simplistic narratives about the relationship between religion and science in the modern age.
The 2010 IEEE Milestone Award
Over a century after his discovery, Branly received a supreme technical accolade. In 2010, the Institute of Electrical and Electronics Engineers designated his work an IEEE Milestone in Electrical Engineering and Computing.
This honor places his discovery of radioconduction among the most pivotal events in technological history. It formally recognizes the coherer as a foundational component for all subsequent radio and wireless systems.
- Milestone "Discovery of Radioconduction by Édouard Branly, 1890."
- Location: The original site of his experiments at the Catholic Institute of Paris.
- Significance: It honors the first reliable detector of radio-frequency electromagnetic waves.
Educational Portrayal and Popular Understanding
Today, Édouard Branly is a staple figure in the history of science and technology curricula. He is universally presented as a key precursor to Marconi and the radio age. His story highlights the importance of fundamental discovery in enabling later innovation.
Educational resources often focus on the elegant simplicity of the coherer experiment. It serves as a perfect teaching tool for explaining early radio principles. Branly's interdisciplinary career also offers a compelling model for students.
Branly in Museums and Public Memory
Several museums feature Branly's original apparatus or replicas. These exhibits contextualize his work within the broader narrative of communication history. His name is attached to schools, streets, and academic prizes, particularly in France.
The Musée des Arts et Métiers in Paris holds significant artifacts related to his work. Public memory celebrates him as a brilliant inventor whose device connected the world. His portrait often appears alongside those of Hertz, Lodge, and Marconi.
Common Misconceptions and Clarifications
A frequent simplification is crediting Marconi alone with "inventing radio." Informed historical accounts correctly position Branly as the inventor of the first critical detection component. Marconi was the brilliant engineer and entrepreneur who commercialized and scaled the technology.
Another point of clarification involves the term "coherer" itself. While Branly invented the device, the name was actually coined by Oliver Lodge. Understanding these nuances provides a richer picture of how collaborative and incremental scientific progress truly is.
Branly taught physics for over 50 years at the Catholic University of Paris, influencing countless students while conducting his groundbreaking research.
The Coherer's Role in Scientific Progress
The story of the coherer is a classic case of a discovery seeking an application. Branly was investigating a curious physical effect, not aiming to build a global communication network. His fundamental research provided the essential tool that made wireless telegraphy possible.
This underscores the vital importance of supporting pure scientific inquiry. Breakthroughs often come from exploring unexplained phenomena without a immediate commercial goal. Branly's radioconduction effect is a prime example of this principle.
From Effect to Application: A Timeline
The development from observation to world-changing technology happened with remarkable speed. This timeline highlights the key steps involving Branly's work.
- 1888: Heinrich Hertz proves the existence of electromagnetic waves.
- 1890: Édouard Branly discovers radioconduction and builds the first coherer.
- 1894: Oliver Lodge demonstrates wireless signaling using a coherer, naming the device.
- 1896: Guglielmo Marconi files his first patent in Britain for wireless telegraphy using an improved coherer.
- 1899: Marconi achieves the first cross-Channel wireless transmission, publicly crediting Branly.
- 1901: The first transatlantic wireless signal is sent, using a coherer-based receiver.
This rapid progression from laboratory effect to transatlantic communication took just over a decade. It showcases how a single enabling invention can accelerate technological progress exponentially.
Édouard Branly's Enduring Scientific Influence
The influence of Édouard Branly extends far beyond the specific technology of the coherer. He represents a critical link in the chain of discovery that brought humanity into the wireless age. His methodology of careful observation and experimental refinement serves as a model for scientific inquiry.
Branly demonstrated how a focused investigation into a subtle physical effect could yield world-changing applications. His work underscores the importance of fundamental research in driving technological revolutions. Modern communication systems, though vastly more complex, still rely on the basic principle of detecting electromagnetic waves that he helped pioneer.
Philosophy of Science and Interdisciplinarity
Branly's career stands as a testament to the power of interdisciplinary thinking. By mastering both physics and medicine, he cultivated a unique perspective. He approached problems holistically, seeing connections between different domains of knowledge.
This approach is increasingly valued in contemporary science and technology. Breaking down silos between specialties can lead to unexpected innovations. Branly's life provides a historical precedent for the modern integrated researcher.
Branly in the Context of Other Wireless Pioneers
Understanding Branly's role requires viewing him within a constellation of inventors. The birth of radio was a collaborative, international effort with many contributors. Each played a distinct part in transforming a theoretical concept into a practical tool.
Branly's specific contribution was providing the first reliable detector. Others, like Hertz, proved the waves existed; Lodge improved and named the device; Marconi engineered commercial systems. This collaborative narrative is essential for an accurate history of technology.
A Network of Discovery: Key Figures
- Heinrich Hertz (1857–1894): Provided the theoretical foundation by generating and detecting electromagnetic waves in his lab.
- Édouard Branly (1844–1940): Invented the practical coherer detector, enabling reliable reception of wireless signals.
- Oliver Lodge (1851–1940): Demonstrated wireless telegraphy publicly, refined the coherer, and coined its name.
- Guglielmo Marconi (1874–1937): Aggressively developed, patented, and commercialized wireless telegraphy on a global scale.
- Alexander Popov (1859–1906): Independently developed a similar lightning detector and radio receiver in Russia.
This network shows that technological breakthroughs are rarely the work of a single isolated genius. They are built upon a foundation of shared knowledge and incremental improvements.
Branly received France's highest honors, including the Grand Croix of the Legion of Honour, for his service to science and the nation.
The Physical Legacy: Artifacts and Memorials
Tangible reminders of Branly's work are preserved in museums and public spaces worldwide. These artifacts connect us directly to the dawn of the wireless era. They serve as powerful educational tools and monuments to human ingenuity.
Original coherers built by Branly are prized historical items. They are studied not only for their technical design but also as icons of a pivotal moment. Seeing these simple devices makes the leap from theory to application vividly clear.
Notable Sites and Collections
The Musée des Arts et Métiers in Paris holds significant Branly-related instruments. Other institutions, like the Science Museum in London and the IEEE History Center, also preserve his legacy. The site of his experiments at the Catholic Institute of Paris is marked by the IEEE Milestone plaque.
His name is immortalized on the Eiffel Tower, listed among 72 French scientists and engineers. Streets, schools, and academic awards bear his name, ensuring his memory endures in French cultural and educational life.
Modern Relevance and Lessons for Today
In our hyper-connected world of 5G and satellite internet, Branly's coherer seems like a primitive relic. However, the story of its invention holds timeless lessons. It teaches us about the nature of discovery, the importance of basic research, and the unpredictable path from experiment to global impact.
Branly was not trying to build a radio. He was investigating a curious effect. His work reminds us that transformative technologies often emerge from pursuing pure curiosity. This principle continues to drive innovation in fields like quantum computing and artificial intelligence today.
From Radioconduction to the Internet
The coherer was a fundamental "enabling technology." It solved a critical bottleneck—detection—that allowed wireless systems to function. In a similar way, modern technologies like the transistor or the laser were initially niche discoveries that later enabled entire industries.
Branly's journey from the lab bench to global recognition mirrors the path of many modern tech pioneers. The cycle of discovery, development, and diffusion remains a constant in technological progress. His story validates the long-term value of investing in scientific exploration.
Common Questions About Édouard Branly
Several recurring questions arise about Branly's life and work. Clarifying these points helps solidify a more accurate and nuanced understanding of his historical role.
Did Édouard Branly Invent the Radio?
No, Édouard Branly did not invent the radio as a complete system. He invented the coherer, which was the essential first radio wave detector. The radio as a practical communication tool resulted from the combined work of many individuals, with Branly providing a crucial component.
Attributing the entire invention to one person oversimplifies a complex historical process. Branly's contribution was foundational but specific to the detection mechanism.
Why Is He Less Famous Than Marconi?
Guglielmo Marconi receives more public recognition because he was the brilliant entrepreneur and engineer who successfully commercialized and marketed wireless technology. He secured patents, formed a powerful company, and achieved dramatic public demonstrations.
Branly, in contrast, was a professor and researcher focused on the scientific principle. He did not aggressively patent or promote his invention for commercial gain. History often remembers the business-minded implementer more vividly than the original discoverer.
What Was the Significance of His Medical Work?
Branly's medical practice in electrotherapy was a significant part of his professional life. It reflected his belief in the practical application of physical science for human benefit. This work placed him at the forefront of a now-established field: using electrical energy for therapeutic purposes.
It also highlights the breadth of his intellect. He was not a narrow specialist but a true polymath who contributed meaningfully to two distinct professions.
Conclusion: The Lasting Impact of a Fundamental Discovery
Édouard Branly's legacy is securely anchored in the foundation of modern communication. His discovery of radioconduction and invention of the coherer provided the key that unlocked wireless technology. Without a reliable detector, the waves proven by Hertz would have remained a laboratory curiosity.
His life exemplifies the integration of deep faith with rigorous science, a model of the devoted scholar. His dual careers in physics and medicine showcase the power of interdisciplinary thinking. The honors he received, culminating in the 2010 IEEE Milestone, affirm his permanent place in the history of engineering.
Key Takeaways and Final Thoughts
- Branly's coherer was the first practical radio wave detector, making wireless telegraphy possible.
- His work was recognized as an IEEE Milestone in 2010, cementing its historical importance.
- He excelled in two fields, holding doctorates in both physical science and medicine.
- He represents the critical role of fundamental research in enabling future technological revolutions.
- His story is a reminder that major innovations are often built upon the foundational work of less-heralded pioneers.
As we navigate our wirelessly connected world, it is worth remembering the simple tube of metal filings that started it all. Édouard Branly's curiosity and precision turned a curious effect into a global transformation. His journey from the lab in Paris to the pinnacle of scientific honor underscores a timeless truth: profound discoveries often begin with observing the subtle, unexplained phenomena right in front of us.
















