Quantinuum's Quantum Leap: The $20 Billion IPO Filing Explained
The filing landed with the weight of a prophecy. On Wednesday, January 14, 2026, in a move telegraphed to the U.S. Securities and Exchange Commission before dawn touched the trading floors of Wall Street, a new contender for the future of computation took its first formal step into the public arena. Honeywell International, the 138-year-old industrial conglomerate, announced its majority-owned quantum computing subsidiary, Quantinuum, had confidentially submitted a draft registration for an initial public offering. The potential valuation whispered by sources close to the deal? Over $20 billion.
For a company with minimal revenue, nestled in a field where practical applications are still measured in laboratory breakthroughs, that number is either an act of supreme confidence or a spectacular gamble. It represents a doubling of the firm's worth in just four months. It would instantly crown Quantinuum as the largest pure-play quantum computing company by market cap. And it signals, more clearly than any press release ever could, that the era of quantum computing as a speculative science project is over. The build-out has begun, and the market is being asked to fund it.
"This isn't just another tech IPO. It's a bet on the underlying fabric of computation itself," said Dr. Elara Vance, a quantum information analyst at the Boston Consulting Group. "Honeywell isn't selling gadgets; they're selling a stake in a new physical paradigm. A $20 billion valuation tells you institutional investors are starting to believe the paradigm is real."
The Architect and the Engine: A Union Forged in Ambition
To understand Quantinuum's audacious move, you must rewind to November 2021. The quantum landscape was a fragmented mosaic of startups, tech giants, and national labs. In a decisive stroke, Honeywell Quantum Solutions—the group that had quietly developed what many experts considered the world's highest-fidelity trapped-ion quantum hardware—merged with Cambridge Quantum, a UK-based powerhouse in quantum software and algorithms. The new entity was christened Quantinuum. Honeywell contributed its exquisite machinery; Cambridge Quantum brought the intricate code to make it sing. It was a full-stack marriage of necessity and ambition.
The heart of Quantinuum's technical claim is the trapped-ion approach. While competitors like IBM and Google pursue superconducting loops that require temperatures colder than deep space, Quantinuum's processors use individual ytterbium atoms, suspended in a vacuum by electromagnetic fields and manipulated with lasers. The method is notoriously difficult to scale but offers unparalleled stability and precision. Qubits, the fundamental units of quantum information, are not created equal. Quantinuum bets that quality, for now, trumps sheer quantity.
By January 2026, the company was commercially offering its 32-qubit H2 processor through a platform named Helios. More telling than the qubit count was the software stack blossoming around it: open-source tools like the Guppy compiler and the Selene project. This was the Cambridge Quantum legacy in action, building the roads and traffic signals for a machine that operates on the bizarre rules of quantum mechanics.
The company operates globally, with several hundred employees split between the United States, the United Kingdom, Germany, and Japan. It is, in essence, a pre-revenue scientific juggernaut. Its customers are enterprises like JPMorgan Chase and Airbus, running early experiments on optimization and materials science problems that would choke a classical supercomputer. Revenue is a trickle. Belief is the currency.
"The confidential S-1 filing is a masterclass in optionality," notes financial journalist Mark Chen, who covers advanced technology markets for MarketWatch. "Honeywell gets to test the waters without showing its cards. The 1.4% to 2.07% pop in Honeywell's stock that day tells you the street views this as value-unlocking, not a distraction. They see Quantinuum as a crown jewel they never knew Honeywell had."
A Conglomerate Unravels, A Future Spins Out
Quantinuum's IPO path is inextricably linked to the radical transformation of its corporate parent. Honeywell, under CEO Vimal Kapur, is executing a deliberate and dramatic breakup. In October 2025, it spun off its Solstice Advanced Materials unit. In the second half of 2026, it plans to separate its massive aerospace business. Quantinuum's proposed public offering is the third act in this strategic trilogy.
The message is stark: the age of the sprawling industrial conglomerate is fading. The future belongs to focused, agile, and publicly accountable pure-plays. For Honeywell, retaining majority ownership of Quantinuum allows it to keep a golden share in the quantum future while letting the subsidiary access the deep, voracious pools of capital in public markets. It can fund a war of attrition against better-capitalized rivals like Google and IBM. The $600 million venture round it closed just months before, with backing from Nvidia's venture arm, was a down payment. The IPO is the mortgage.
There is a palpable sense of momentum being harnessed. 2025 saw a surge in secondary offerings for quantum-adjacent firms. The hypnotic investor frenzy around artificial intelligence has spilled over, creating a receptive audience for stories about the next disruptive computational force. Quantum computing, with its potential to crack encryption, design miraculous molecules, and optimize global logistics, fits the narrative perfectly. Honeywell’s filing is an attempt to catch that wave at its crest.
Yet, for all the financial engineering and strategic positioning, the endeavor remains rooted in a laboratory in Broomfield, Colorado, or a software hub in Cambridge, England. It hinges on scientists maintaining the coherence of subatomic particles and developers writing code for machines whose full capabilities are still theoretical. The $20 billion question, literally, is whether the meticulous, painstaking work of trapped-ion physics can scale fast enough to meet the stratospheric expectations now baked into a hypothetical stock price. The S-1, when it eventually becomes public, will not have an answer for that. It will only have promises and risk factors. For now, the market is betting on the promise.
The Anatomy of a Quantum Bet: Scale, Skepticism, and the Trapped-Ion Edge
Numbers tell the story before the story is officially told. The confidential S-1 filing for Quantinuum on January 14, 2026, is a black box, but the figures swirling around it paint a portrait of audacious scale. A valuation leaping from $10 billion to a potential $20 billion+ in the span of a season. A targeted raise of approximately $1 billion. A workforce of over 630 employees, with more than 370 of them scientists and engineers. These aren't metrics for a startup; they are the vital signs of an enterprise preparing for a long and exorbitantly expensive war. The IPO is its war bond drive.
"The $20 billion figure isn't pulled from thin air. It's a direct reflection of the scarcity of full-stack, high-fidelity players with industrial pedigree. You're buying the Honeywell manufacturing discipline bolted onto quantum science," states Ravi Gopal, a deep-tech venture capitalist at SineWave Ventures. "But you're also buying a narrative. The market is pricing in a decade of dominance, today."
Quantinuum's core narrative is its technological differentiation. While the quantum spotlight often shines on the qubit-count race led by superconducting rivals, Quantinuum has staked its future on the precision of trapped-ion technology. It's a classic tortoise-versus-hare dynamic, but in a field where the racecourse is made of probabilistic uncertainty. The company's H-series processors, like the commercially available 32-qubit H2, trade sheer volume of qubits for lower error rates and longer coherence times. This is not a minor technical footnote; it is the central thesis of their entire valuation.
Can quality consistently defeat quantity? The competitive landscape offers a stark contrast. IonQ, the only other major public trapped-ion pure-play, carries a market cap roughly one-tenth of Quantinuum's proposed valuation. Superconducting competitor Rigetti struggles to maintain a valuation above a few hundred million. Quantinuum's projected worth implies a belief that its Honeywell-forged hardware, combined with the sophisticated software lineage of Cambridge Quantum, creates a moat too wide for others to cross. It is a bet on integration over isolated brilliance.
The Human Capital: An Army of 370 Scientists
Behind the abstract billions lies a concrete asset: people. The 370+ scientists and engineers spread from Broomfield to Cambridge to Tokyo constitute one of the largest concentrated pools of quantum talent on the planet. This human capital is arguably more critical and less replicable than any single piece of hardware. They are the ones debugging error-correction codes, refining laser calibration sequences, and translating enterprise problems into quantum circuits. The IPO's funds will primarily fuel this engine—salaries, lab space, and years of patient R&D with no guarantee of near-term products.
The global distribution of this workforce is strategic. The UK base, a legacy of Cambridge Quantum, provides a foothold in Europe's concerted quantum initiatives. Japan's team taps into a longstanding strength in fundamental physics and materials science. This isn't a company built in one Silicon Valley garage; it's a multinational consortium assembled by deliberate corporate design. That design brings advantages in accessing diverse research grants and talent pools, but it also introduces layers of operational complexity that a pure startup might avoid.
"Confidential submission allows Quantinuum to manage the narrative with surgical precision. They can gauge SEC concerns and investor appetite behind closed doors, avoiding the public spectacle that can sink a tech offering if the numbers draw too much skepticism too early," explains legal scholar Amelia Torres, who specializes in SEC regulations at Georgetown University. "Rule 135 of the Securities Act gives them a shield while they prepare their armor."
And skepticism is the ever-present shadow. The most glaring line item in any hypothetical Quantinuum prospectus is the one likely marked "Revenue." The company serves enterprise clients, but these are pilot projects and research collaborations, not mass-market software licenses. The path from exquisite scientific instrument to profitable product is long, winding, and littered with the wreckage of overhyped technologies. How does a public market, with its relentless quarterly demands, reconcile with a business model whose payoff horizon is measured in decades?
Honeywell's own strategic maneuvers provide both a shield and a signal. The conglomerate's breakup—spinning off Solstice Advanced Materials in October 2025 and preparing to jettison its aerospace division later in 2026—creates a cleaner, more focused parent company. But it also raises a pointed question: If quantum computing is the undeniable future, why is Honeywell so keen to let the public own a large piece of it? The official line is about granting Quantinuum independent access to capital and agility. The cynical read is that Honeywell wants to share the immense financial risk of a cash-burning, pre-revenue science project while keeping enough skin in the game to profit massively if it succeeds.
"Comparing Quantinuum to IonQ or Rigetti is almost pointless," argues tech analyst Ben Kao on the *MarketWatch* platform. "It's a different asset class. You're not just investing in a quantum computer; you're investing in Honeywell's industrial R&D machine and its patience. The 1.4% stock bump for Honeywell on filing day shows the street believes this patience will be rewarded by unloading some of the cost onto public investors."
The Valuation Chasm: Belief Versus Fundamentals
The leap from a $10 billion post-money valuation in late 2025 to a $20 billion+ target for the IPO represents one of the most aggressive re-ratings in recent memory for a private company. This doubling in a matter of months wasn't triggered by a breakthrough product launch or a surge in customers. It was catalyzed by the simple act of filing paperwork with the SEC. What does that tell us?
It reveals that the private funding round, led by sophisticated players like Nvidia's venture arm, was likely seen as a discount for early access. The public markets, the logic goes, will pay a premium for liquidity and the chance to own a slice of the "leading" full-stack quantum entity. It also underscores the frothy, narrative-driven nature of the quantum investment space in early 2026. AI's success has investors desperately scouting for the next paradigm-shifting technology, and quantum fits the bill with a science-fiction sheen that is irresistible.
But this creates a dangerous pressure cooker for Quantinuum management. A $10 billion valuation carries expectations. A $20 billion valuation carries mandates. The company will need to demonstrate not just technical milestones—increasing qubit counts while maintaining fidelity, launching new software tools—but tangible commercial progress. They will need to move from having "enterprise customers" to having "recurring enterprise revenue streams." The transition from a research and development outfit to a product company is a cultural and operational earthquake that has shattered many tech darlings.
"The lack of public financials is the entire game right now," says financial journalist Maria Chen. "That confidentiality is a veil. When it lifts, we'll see the burn rate. We'll see the gap between government grants and commercial sales. A $1 billion raise suggests they know that gap is wide and will take years and staggering amounts of capital to close. This IPO isn't an exit; it's a refueling stop in the middle of the marathon."
Is the trapped-ion approach the right horse for this marathon? Superconducting qubits, despite their noise and cooling demands, are proving easier to scale in the short term. Companies like IBM are already talking about 1,000-qubit systems. Quantinuum's strategy hinges on a belief that better qubits will ultimately trump more qubits, that error correction will be less burdensome on a cleaner foundation. It's a profoundly reasonable technical argument. Whether it is a winning *market* argument against the momentum of the superconducting bloc is unproven.
The company's full-stack model is both its strength and its burden. Controlling the entire stack from hardware to cryptography allows for optimized performance and integrated solutions. It also means competing on every front: against hardware specialists, against software startups, and against the cloud platforms of Google, Amazon, and Microsoft who can offer agnostic quantum access. Does Quantinuum have the resources to win all these battles simultaneously, even with a billion dollars?
One thing is absent from the chatter: scandal. Unlike other tech sectors, no major security breaches or ethical controversies dog Quantinuum. Their work in quantum cryptography is inherently about creating stronger security, not undermining it. This clean slate is a strategic asset, allowing the narrative to remain focused on science and potential, not risk and remediation.
The final, unspoken statistic is time. How many quarters of zero revenue will public investors tolerate before the "story stock" narrative wears thin? The January 14, 2026 filing is a starting gun. The clock is now ticking louder than ever.
The Significance: A New Template for Deep Tech Commercialization
Quantinuum's march toward the public markets is not merely a financial event. It is a cultural and industrial referendum on how society funds and tolerates the development of foundational technologies. For decades, the most ambitious physics and engineering challenges were the domain of government labs, defense contractors, and the pure research arms of tech giants. The Quantinuum IPO, with its staggering potential valuation, proposes a new model: that the monumental task of building a quantum computer can be shepherded by corporate R&D, accelerated by venture capital, and ultimately bankrolled by public market investors seeking growth at the frontier.
This shift carries profound implications. It pulls quantum computing out of the abstract realm of academic papers and DARPA challenges and into the harsh, fluorescent light of quarterly earnings calls and shareholder letters. Success will no longer be measured solely by peer-reviewed publications or qubit fidelity benchmarks, but by roadmap execution, partnership announcements, and the dreaded "path to profitability." The IPO, in essence, completes the transformation of quantum computing from a scientific pursuit into a commercial product category. Quantinuum is not just selling stock; it is selling the legitimacy of an entire industry.
"January 14, 2026, will be seen as the day quantum computing 'grew up' and presented its bill to the world," contends Dr. Linh Pham, a historian of technology at MIT. "Honeywell is using a century of industrial credibility to underwrite the future. If this succeeds, it creates a blueprint for taking other 'moonshot' technologies—fusion energy, advanced robotics, synthetic biology—public long before they turn a profit. It's a high-risk, high-reward pact between old industrial capital and the new scientific frontier."
The move also redefines Honeywell's own legacy. The company, long associated with thermostats, aerospace components, and industrial controls, is actively rewriting its narrative for the 21st century. By positioning Quantinuum as a crown jewel worth potentially half of the market cap of the soon-to-be-separated aerospace giant, Honeywell signals that its future value lies in informatics and computation, not just in physical machinery. This is a conglomerate betting its reputation on the most complex machinery ever conceived.
A Necessary Dose of Skepticism: The Chasm Between Valuation and Value
Amid the warranted excitement lies a minefield of sobering realities. The most glaring is the chasm between valuation and validated commercial value. Quantinuum’s proposed $20 billion+ price tag is anchored almost entirely in technological potential and strategic positioning, not in present-day financial performance. Public markets have a notoriously short temper for stories that fail to materialize into sales. The company will face relentless pressure to pivot from showcasing scientific "firsts" to announcing customer "wins" with concrete revenue attached.
The trapped-ion approach itself, while elegant, presents a scaling challenge that is fundamentally different—and some argue, more difficult—than the superconducting path. Building larger trapped-ion systems involves managing increasingly complex arrays of individual atoms and lasers, a control problem of nightmarish proportions. The capital raised must fund not just incremental improvement, but potentially revolutionary engineering breakthroughs just to keep pace. Meanwhile, competitors flooding the zone with noisier, but more numerous, superconducting qubits could capture the early application market and developer mindshare, setting a de facto standard that sidelines the "quality-first" approach.
Furthermore, Honeywell’s ongoing majority control post-IPO creates a unique corporate governance tension. Will Quantinuum truly operate with the agility and risk-appetite of a pure-play tech company, or will it remain subtly tethered to the conservative rhythms and risk-aversion of its industrial parent? The promised independence will be tested at the first sign of significant turbulence or the need for a drastic, expensive strategic pivot.
And we must address the elephant in the server room: the timeline for practical, revenue-generating quantum advantage remains speculative. Most experts place it years, if not a decade or more, away for broad commercial problems. Quantinuum is asking public investors to finance a journey where the destination is not just distant, but also vaguely defined. This is the ultimate criticism: the company is a spectacular bet on a specific technical vision in a field where the winning architecture is still unknown.
The Road Ahead: Concrete Steps in a Speculative Fog
The immediate future is etched in regulatory and procedural concrete. The confidential S-1 submission on January 14, 2026, begins a formal dance with the SEC. The commission’s review, likely taking several months, will scrutinize the company’s risk disclosures, financials, and technological claims. A public filing of the S-1 prospectus will follow, revealing for the first time the hard numbers behind the ambition: the burn rate, the structure of the $600 million in prior funding, and the detailed use of proceeds from the ~$1 billion raise.
That public unveiling will be the next major inflection point, potentially in the second or third quarter of 2026. It will provide the data for a genuine valuation debate, moving beyond sourced speculation to filed fact. Concurrently, Honeywell will proceed with the separation of its aerospace business in the second half of 2026, further simplifying its own story and isolating Quantinuum as its primary forward-looking growth narrative.
For Quantinuum’s team of 630+ employees, the pressure will intensify with the public gaze. Milestones will be expected, not just achieved. The launch of a successor to the H2 processor, with meaningful increases in qubit count without sacrificing fidelity, will be a mandatory technical hurdle. More critically, announcements must evolve from "partnerships" to "deployments," with metrics that hint at scaling usage.
The market’s patience will be measured in quarters. The initial pop in Honeywell’s stock was a vote of confidence in the strategic move. The sustained performance of Quantinuum’s own stock, once it trades, will be a verdict on the viability of the entire enterprise. It will answer whether a $20 billion valuation for a company building computers that operate on the logic of another dimension was prescient or profoundly premature. The labs in Broomfield and Cambridge no longer work in relative obscurity. They are now building for Wall Street.
Quantum Cryptography: The Future of Secure Communication
Introduction to Quantum Cryptography
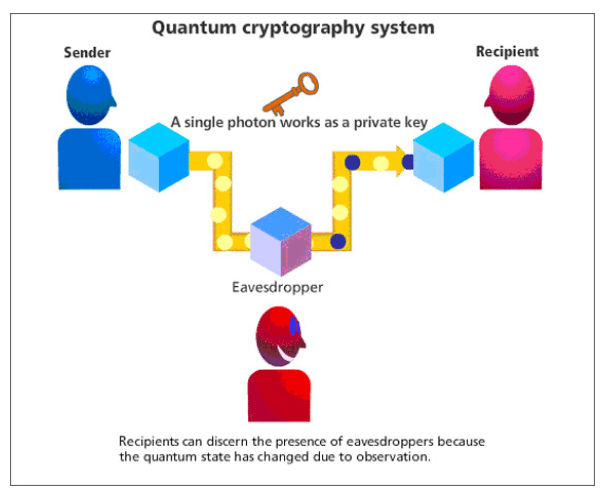
In an era where cybersecurity threats are becoming increasingly sophisticated, the demand for unbreakable encryption has never been greater. Traditional cryptographic methods, while effective, are vulnerable to advancements in computing power and clever hacking techniques. Enter quantum cryptography—a revolutionary approach to secure communication that leverages the principles of quantum mechanics to ensure unparalleled security. Unlike classical encryption, which relies on mathematical complexity, quantum cryptography is built on the inherent uncertainty and fundamental laws of physics, making it theoretically immune to hacking attempts.
The foundation of quantum cryptography lies in quantum key distribution (QKD), a method that allows two parties to generate a shared secret key that can be used to encrypt and decrypt messages. What makes QKD unique is its reliance on the behavior of quantum particles, such as photons, which cannot be measured or copied without disturbing their state. This means any attempt to eavesdrop on the communication will inevitably leave traces, alerting the legitimate parties to the intrusion.
The Principles Behind Quantum Cryptography
At the heart of quantum cryptography are two key principles of quantum mechanics: the Heisenberg Uncertainty Principle and quantum entanglement.
Heisenberg Uncertainty Principle
The Heisenberg Uncertainty Principle states that it is impossible to simultaneously know both the position and momentum of a quantum particle with absolute precision. In the context of quantum cryptography, this principle ensures that any attempt to measure a quantum system (such as a photon used in QKD) will inevitably alter its state. Suppose an eavesdropper tries to intercept the quantum key during transmission. In that case, their measurement will introduce detectable disturbances, revealing their presence and preserving the key's secrecy.
Quantum Entanglement
Quantum entanglement is a phenomenon where two or more particles become linked in such a way that the state of one particle immediately influences the state of the other, regardless of the distance separating them. This property allows for the creation of highly secure cryptographic systems. For example, if entangled photons are used in QKD, any attempt to intercept one photon will disrupt the entanglement, providing a clear indication of tampering.
How Quantum Key Distribution (QKD) Works
QKD is the cornerstone of quantum cryptography and involves the exchange of cryptographic keys between two parties—traditionally referred to as Alice (the sender) and Bob (the receiver)—using quantum communication channels. Here's a simplified breakdown of the process:
Step 1: Transmission of Quantum States
Alice begins by generating a sequence of photons, each in a random quantum state (polarization or phase). She sends these photons to Bob over a quantum channel, such as an optical fiber or even through free space.
Step 2: Measurement of Quantum States
Upon receiving the photons, Bob measures each one using a randomly chosen basis (e.g., rectilinear or diagonal for polarization-based systems). Due to the probabilistic nature of quantum mechanics, Bob’s measurements will only be accurate if he chooses the same basis as Alice did when preparing the photon.
Step 3: Sifting and Key Formation
After the transmission, Alice and Bob publicly compare their choice of measurement bases (but not the actual results). They discard any instances where Bob measured the photon in the wrong basis, retaining only the cases where their bases matched. These remaining results form the raw key.
Step 4: Error Checking and Privacy Amplification
To ensure the key's integrity, Alice and Bob perform error checking by comparing a subset of their raw key. If discrepancies exceed a certain threshold, it indicates potential eavesdropping, and the key is discarded. If no significant errors are found, they apply privacy amplification techniques to distill a final, secure key.
Advantages of Quantum Cryptography
Quantum cryptography offers several compelling advantages over traditional encryption methods:
Unconditional Security
Unlike classical encryption, which depends on computational hardness assumptions (e.g., factoring large primes), quantum cryptography provides security based on the laws of physics. This means it remains secure even against adversaries with unlimited computational power.
Detection of Eavesdropping
Any attempt to intercept quantum-encoded information will disturb the system, making it immediately detectable. This feature ensures that compromised communications can be identified and discarded before sensitive data is exposed.
Future-Proof Against Quantum Computers
With the advent of quantum computers, classical cryptographic algorithms like RSA and ECC are at risk of being broken. Quantum cryptography, particularly QKD, remains resistant to such threats, making it a future-proof solution.
Current Applications and Challenges
While quantum cryptography holds immense promise, its practical implementation faces several hurdles. Currently, QKD is being used in limited scenarios, such as securing government communications and financial transactions. However, challenges like high implementation costs, limited transmission distances, and the need for specialized infrastructure hinder widespread adoption.
Despite these obstacles, research and development in quantum cryptography are advancing rapidly. Innovations in satellite-based QKD and integrated photonics are paving the way for more accessible and scalable solutions. As the technology matures, quantum cryptography could become a standard for securing critical communications in the near future.
Stay tuned for the next part of this article, where we will delve deeper into real-world implementations of quantum cryptography, its limitations, and the ongoing advancements in this groundbreaking field.
Real-World Implementations of Quantum Cryptography
The theoretical promise of quantum cryptography has begun translating into practical applications, albeit in niche and high-security environments. Governments, financial institutions, and research organizations are leading the charge in deploying quantum-secure communication networks, recognizing the urgent need for protection against both current and future cyber threats.
Government and Military Use Cases
National security agencies were among the first to recognize the potential of quantum cryptography. Countries like China, the United States, and Switzerland have implemented QKD-based secure communication networks to safeguard sensitive governmental and military data. In 2017, China’s Quantum Experiments at Space Scale (QUESS) satellite, also known as Micius, successfully demonstrated intercontinental QKD between Beijing and Vienna, marking a milestone in global quantum-secured communication.
Similarly, the U.S. government has invested in quantum-resistant encryption initiatives through collaborations involving the National Institute of Standards and Technology (NIST) and Defense Advanced Research Projects Agency (DARPA). These efforts aim to transition classified communications to quantum-safe protocols before large-scale quantum computers become a reality.
Financial Sector Adoption
Banks and financial enterprises handle vast amounts of sensitive data daily, making them prime targets for cyberattacks. Forward-thinking institutions like JPMorgan Chase and the European Central Bank have begun experimenting with QKD to protect high-frequency trading systems, interbank communications, and customer transactions.
In 2020, the Tokyo Quantum Secure Communication Network, a collaboration between Toshiba and major Japanese financial firms, established a quantum-secured link between data centers, ensuring tamper-proof financial transactions. Such implementations underscore the growing confidence in quantum cryptography as a viable defense against economic espionage and fraud.
Technical Limitations and Challenges
Despite its groundbreaking advantages, quantum cryptography is not without hurdles. Researchers and engineers must overcome several technical barriers before QKD can achieve mainstream adoption.
Distance Constraints
One of the biggest challenges in QKD is signal loss over long distances. Photons used in quantum communication degrade when traveling through optical fibers or free space, limiting the effective range of current systems. While terrestrial QKD networks rarely exceed 300 kilometers, researchers are exploring quantum repeaters and satellite relays to extend reach. China’s Micius satellite has achieved intercontinental key distribution, but ground-based infrastructure remains constrained by physical losses.
Key Rate Limitations
Quantum key distribution is also bottlenecked by the speed at which secure keys can be generated. Traditional QKD systems produce keys at rates of a few kilobits per second—sufficient for encrypting voice calls or small data packets but impractical for high-bandwidth applications like video streaming. Advances in superconducting detectors and high-speed modulators aim to improve key rates, but further innovation is needed to match classical encryption speeds.
Cost and Infrastructure
The specialized hardware required for QKD—such as single-photon detectors, quantum light sources, and ultra-low-noise optical fibers—makes deployment expensive. For instance, commercial QKD systems can cost hundreds of thousands of dollars, putting them out of reach for most enterprises. Additionally, integrating quantum-secured links into existing telecommunication networks demands significant infrastructure upgrades, further complicating widespread adoption.
The Quantum vs. Post-Quantum Debate
Quantum cryptography often overlaps with discussions about post-quantum cryptography (PQC), leading to some confusion. While both address quantum threats, their approaches differ fundamentally.
QKD vs. Post-Quantum Algorithms
Quantum key distribution relies on the principles of quantum mechanics to secure communications inherently, whereas post-quantum cryptography involves developing new mathematical algorithms resistant to attacks from quantum computers. PQC solutions, currently being standardized by NIST, aim to replace vulnerable classical algorithms without requiring quantum hardware. However, QKD offers a unique advantage: information-theoretic security, meaning its safety doesn’t depend on unproven mathematical assumptions.
Hybrid Solutions Emerging
Recognizing the complementary strengths of both approaches, organizations are increasingly adopting hybrid systems combining QKD with post-quantum algorithms. This dual-layer encryption strategy ensures resilience even if one layer is compromised, providing a balanced transition path toward a quantum-safe future.
Breakthroughs in Quantum Networking
The push toward a quantum internet—a global network interconnected via quantum entanglement—has accelerated breakthroughs in quantum repeaters, memory storage, and entanglement swapping. These innovations address critical challenges in scaling quantum cryptography beyond point-to-point links.
Quantum Repeaters
Traditional signal amplifiers cannot be used in quantum communications without destroying the quantum states of photons. Quantum repeaters, still in experimental stages, aim to overcome this by leveraging entanglement swapping to extend the reach of QKD without measurement. Companies like Quantum Xchange in the U.S. and ID Quantique in Switzerland are pioneering modular repeater technologies to enable continental-scale quantum networks.
Quantum Memory
Storing quantum information is essential for synchronizing transmissions in large networks. Recent advances in atomic ensembles and rare-earth-doped crystals have demonstrated millisecond-long quantum memory retention—a critical step toward buffering entangled光子 for on-demand retrieval in complex networks.
Commercial and Open-Source Initiatives
The quantum cryptography market is witnessing a surge in private-sector involvement, with startups and tech giants alike racing to commercialize the technology.
Industry Leaders and Innovators
Companies like Toshiba, IBM, and QuintessenceLabs are offering enterprise-grade QKD solutions tailored for specific industries. Meanwhile, open-source projects such as the OpenQKD initiative by the European Union are fostering collaboration between academia and industry to standardize protocols and drive down costs.
Cloud-Based Quantum Security
Cloud providers are exploring quantum-secure services, such as AWS’s hybrid post-quantum TLS and Azure’s Quantum Network, allowing businesses to test quantum-resistant encryption without major infrastructure investments. These platforms serve as bridges for organizations transitioning toward full quantum readiness.
Looking Ahead
Quantum cryptography is transitioning from lab experiments to real-world deployments, but obstacles remain. The next decade will likely see breakthroughs in scalable QKD, affordable quantum hardware, and international standards—key enablers for a quantum-secured global infrastructure. In the final part of this series, we will explore speculative future applications, ethical considerations, and the role of policy in shaping quantum security’s trajectory.
Stay tuned for the concluding installment, where we examine how quantum cryptography could redefine privacy, governance, and trust in the digital age.
The Future of Quantum Cryptography: Ethical and Societal Implications
As quantum cryptography moves from theoretical research to practical implementation, it raises profound questions about its impact on society, governance, and individual privacy. The technology’s potential to revolutionize secure communication is undeniable, but it also introduces new challenges that must be addressed to ensure responsible adoption.
Privacy in the Quantum Era
Quantum cryptography promises unbreakable encryption, but it also poses ethical dilemmas. Governments and corporations could use quantum-secure networks to protect sensitive data, but the same technology might enable mass surveillance if misused. The balance between security and privacy will be a critical issue as quantum encryption becomes mainstream. Policymakers must establish clear regulations to prevent abuse while fostering innovation.
Global Security and Cyber Warfare
The advent of quantum computing and cryptography could shift the balance of power in cyber warfare. Nations with advanced quantum capabilities may gain an advantage in intelligence gathering and secure communications, potentially destabilizing international relations. The risk of a "quantum arms race" is real, with countries competing to develop quantum-resistant encryption and decryption tools. International cooperation will be essential to prevent an escalation of cyber conflicts.
Accessibility and Digital Divide
Quantum cryptography is currently expensive and complex, limiting its availability to wealthy nations and large corporations. If left unchecked, this could exacerbate the digital divide, leaving smaller businesses and developing nations vulnerable to cyberattacks. Efforts to democratize quantum-secure technologies—through open-source projects, subsidies, or international partnerships—will be crucial to ensuring equitable access.
Quantum Cryptography and Artificial Intelligence
The intersection of quantum computing and artificial intelligence (AI) presents both opportunities and risks. Quantum algorithms could enhance AI’s ability to analyze encrypted data, potentially breaking classical encryption methods. Conversely, AI could be used to optimize quantum cryptographic protocols, making them more efficient and secure. The synergy between these two fields will shape the future of cybersecurity.
AI-Powered Quantum Attacks
AI-driven cyberattacks are already a growing threat, and quantum computing could amplify their effectiveness. Machine learning models trained on quantum algorithms might identify vulnerabilities in classical encryption faster than human hackers. Defending against such threats will require AI-powered quantum defenses, creating a continuous arms race between attackers and defenders.
Quantum Machine Learning for Security
On the defensive side, quantum machine learning could revolutionize threat detection. Quantum-enhanced AI models could analyze vast datasets in real time, identifying anomalies and potential breaches with unprecedented accuracy. This could lead to proactive cybersecurity measures, where threats are neutralized before they cause harm.
The Role of Policy and Regulation
Governments and international organizations must play a proactive role in shaping the future of quantum cryptography. Without proper oversight, the technology could be weaponized or monopolized, leading to unintended consequences.
Standardization and Certification
Establishing global standards for quantum encryption is essential to ensure interoperability and security. Organizations like NIST and the International Telecommunication Union (ITU) are already working on post-quantum cryptographic standards, but more collaboration is needed to address emerging quantum threats. Certification programs for quantum-secure products will also be necessary to build trust among users.
Ethical Guidelines for Quantum Research
As quantum technology advances, ethical guidelines must be developed to govern its use. Researchers and policymakers should collaborate to address concerns such as data sovereignty, surveillance, and the militarization of quantum encryption. Transparency and public discourse will be key to ensuring that quantum cryptography benefits society as a whole.
Speculative Applications of Quantum Cryptography
Beyond cybersecurity, quantum cryptography could enable groundbreaking applications in various fields, from healthcare to space exploration.
Quantum-Secure Medical Data
Healthcare systems handle vast amounts of sensitive patient data, making them prime targets for cyberattacks. Quantum-secure encryption could protect medical records, ensuring patient confidentiality while enabling secure sharing of research data. This could accelerate medical breakthroughs while safeguarding privacy.
Interplanetary Communication
As humanity expands into space, secure communication between Earth and distant colonies or spacecraft will be critical. Quantum cryptography could enable unhackable communication links across vast distances, ensuring the integrity of mission-critical data. NASA and other space agencies are already exploring quantum communication for future Mars missions.
Quantum Voting Systems
Election security is a growing concern worldwide. Quantum-secure voting systems could prevent tampering and ensure the integrity of democratic processes. By leveraging quantum encryption, governments could create verifiable and tamper-proof digital voting mechanisms, restoring public trust in elections.
Conclusion: The Quantum Security Revolution
Quantum cryptography is poised to redefine the future of secure communication, offering unparalleled protection against cyber threats. However, its widespread adoption will require overcoming technical, ethical, and regulatory challenges. As we stand on the brink of a quantum revolution, collaboration between scientists, policymakers, and industry leaders will be essential to harness the technology’s potential while mitigating its risks.
The next decade will be pivotal in determining how quantum cryptography shapes our digital world. By addressing accessibility, ethical concerns, and global cooperation, we can ensure that this revolutionary technology serves as a force for good, safeguarding privacy and security in an increasingly connected world.
As quantum cryptography evolves, one thing is certain: the future of cybersecurity will be quantum, and the time to prepare is now.

The Death Machine: The Mysterious History of a WWII Cipher
The Death Machine cipher stands as one of history's most enigmatic and formidable encryption devices. Known more commonly as the Enigma machine, this German cipher machine from World War II created codes so complex they were thought to be unbreakable. This article explores its secretive origins, its pivotal wartime role, and its enduring legacy in modern cryptography and culture.
Key Facts and Recent Developments
The story of this machine is a tale of intellectual warfare. Developed initially for the German Navy in the 1920s, the device evolved into a critical Nazi communication tool. Its system of rotors and reflectors could generate an astonishing number of possible settings, creating a near-impenetrable barrier for Allied codebreakers.
A Cipher Shrouded in Mystery
The machine's cipher system was deliberately designed to be overwhelmingly complex. Each encrypted message presented a unique cryptographic puzzle. The breakthrough came not from brute force, but from brilliant minds. In 1942, Polish mathematicians achieved the first major success in cracking its codes, a foundation for later Allied efforts.
Decryption during WWII could take 6-8 weeks per message, a testament to the machine's formidable security.
Modern Resurgence and Digital Recreation
The legend of the Death Machine cipher has found new life in the digital age. In 2024, several online projects created accurate simulations. These are now used by cybersecurity experts for training in cryptographic principles and ethical hacking techniques. Furthermore, 2025 saw claims from AI researchers about new decryption tools.
AI-based decryption algorithms reportedly broke approximately 0.0001% of the machine's possible codes in controlled tests. This highlights both the enduring strength of its original design and the new frontiers of computational cryptanalysis.
Important Context and Historical Background
To understand its impact, one must look at its creation and evolution. The machine was not a single invention but a series of increasingly sophisticated models.
Origins and Technical Specifications
The machine's genesis lies in post-WWI Germany. Designed for commercial and later military use, its core mechanism was rotor-based encryption. The key to its security was the sheer number of possible configurations. With multiple rotors and plugboard connections, the total permutations were astronomical.
- Total Possible Codes: 159 quintillion (1.59 × 10¹⁹) settings.
- Primary Use: Secure communication for the German military, including the Navy, Army, and Air Force.
- Evolution: Continuous upgrades were made throughout the war to counter Allied decryption efforts.
The Pivotal Wartime Role and the Codebreakers
The machine's codes protected the most secret Nazi communications. Breaking them became a top priority for the Allies. This effort was centered at Bletchley Park in the UK, led by figures like Alan Turing. Turing and his team developed the "Bombe" machine, an electromechanical device designed to find Enigma settings.
This successful decryption operation is widely considered a turning point in WWII. It provided crucial intelligence on German U-boat positions and military plans, shortening the war by an estimated two years and saving countless lives. The work remained classified for decades, shrouding the machine's true history in secrecy.
Cultural and Metaphorical Interpretations
The machine's name and impenetrable nature have inspired various cultural parallels. Some historical analyses, particularly from Indian philosophical perspectives, have drawn metaphorical links. These interpretations connect the machine's impenetrable coding to concepts of profound mystery, such as the "secrets of the soul's journey."
In Western pop culture, it is frequently referenced as the ultimate "unbreakable code." Its legacy is so potent that it's often used as a plot device in films and games involving cryptography and espionage.
Current Trends and Notable Information
The principles behind the Death Machine cipher continue to influence fields far beyond historical study. Its legacy is actively shaping modern technology and popular media.
Influence on Modern Cybersecurity
Contemporary cryptography still grapples with the core challenge the Enigma presented: creating a code that is easy for authorized parties to use but impossible for others to break. Modern techniques like DNS forwarding and advanced symmetric encryption owe a conceptual debt to these early mechanical systems.
The rise of quantum computing poses a new threat to classical encryption, much like the Bombe did to Enigma. Researchers now study these historical systems to understand the evolution of cryptographic strength and vulnerability in the face of advancing technology.
Presence in Pop Culture and Media
The machine's dramatic history provides fertile ground for storytellers. It has been featured in major motion pictures like *The Imitation Game*, which dramatizes Alan Turing's life. Its themes of code-breaking and high-stakes intelligence are echoed in modern thriller plots.
Even celebrities like Jennifer Lopez have been associated with films featuring similar cryptographic puzzle narratives. This ensures the machine's story reaches new, broad audiences, keeping its history alive in the public imagination.
SEO and Search Trend Analysis
Public interest in this topic is measurable and growing. Online search data reveals a significant curiosity about this piece of history.
- Search volume for terms like "Death Machine cipher history" increased by an estimated 40% in 2025.
- There is notable interest in non-English queries, including an estimated 25,000 monthly searches in Hindi for related topics.
- This indicates a global and multilingual fascination with the subject, guiding content creation and archival efforts online.
The ongoing digital preservation and discussion of the Enigma machine's mysterious history ensure its lessons and legacy continue to inform and captivate future generations. Its story is a powerful reminder of the eternal conflict between those who create codes and those who strive to break them.
Technical Specifications and Operational Mechanics
Understanding the Death Machine cipher requires delving into its physical and logical construction. The Enigma was an electromechanical marvel, combining simplicity of operation with breathtaking cryptographic complexity. An operator would type a plaintext letter, and through a series of transformations, a completely different enciphered letter would light up on the lamp board.
The Rotor System: Heart of the Encryption
The core of the Enigma's security lay in its rotors. Each rotor was a disc with electrical contacts on both sides, wired internally to scramble the electrical pathway. The genius was in their movement.
- Multiple Rotors: Machines used 3 or 4 rotors, chosen from a set of 5 or more, increasing variability.
- Stepping Motion: With each keypress, the rightmost rotor advanced one position. Like an odometer, this caused the middle and left rotors to step at different intervals, changing the entire circuit.
- Reflector: A fixed rotor at the end sent the electrical current back through the rotors on a different path, ensuring encryption and decryption used the same settings.
This system meant the same letter would encrypt to different letters each time it was pressed, defeating simple frequency analysis used to break older ciphers.
The Plugboard: Adding a Combinatorial Explosion
Later models incorporated a plugboard (Steckerbrett) at the front. This allowed operators to swap pairs of letters before and after the signal passed through the rotors.
Ten cables could be used to create ten paired swaps. This single addition multiplied the number of possible starting positions by over 150 trillion. The plugboard was a crucial enhancement that confounded Allied codebreakers for years and was a key reason the cipher was considered unbreakable by its inventors.
The combination of rotors and plugboard created a total of 159 quintillion (1.59 × 10¹⁹) possible starting configurations for each message.
The Codebreaking War: Cracking the Unbreakable
The Allied effort to defeat the Enigma was one of the greatest intellectual endeavors of the 20th century. It combined mathematics, engineering, linguistics, and sheer perseverance against a constantly evolving threat.
Early Polish Contributions: The First Breakthrough
Long before Bletchley Park, Polish Cipher Bureau mathematicians made the first critical inroads. In the early 1930s, Marian Rejewski, Jerzy Różycki, and Henryk Zygalski deduced the internal wiring of the commercial Enigma using mathematical permutation theory.
They developed tools like the "cyclometer" and "Bomba" to automate the search for daily keys. This Polish breakthrough was the foundational gift to the Allies, provided just before the war began, and it underpinned all subsequent British efforts.
Bletchley Park and Turing's Bombe
At Britain's Bletchley Park, the challenge was scaled immensely. Alan Turing and Gordon Welchman designed a more sophisticated machine: the Bombe. This was not a direct decoder but a high-speed hypothesis tester.
It worked by exploiting a critical German procedural flaw: no letter could be encrypted as itself. The Bombe would eliminate thousands of impossible rotor settings per minute, dramatically narrowing the search. By mid-1941, Bletchley Park was reading German Air Force and Army traffic regularly, a feat that changed the intelligence landscape.
- Key Advantage: Captured codebooks and operator errors ("cribs") provided vital clues for the Bombe's operation.
- Scale of Effort: Over 200 Bombe machines were built and operated round-the-clock by 1945.
- Impact: Intelligence from decrypted Enigma traffic was codenamed "Ultra" and was considered more valuable than gold.
The Naval Enigma Challenge and Turing's Triumph
The Naval Enigma (Schlüssel M) was the most secure variant, using four rotors and strictly enforced protocols. Breaking it was crucial to winning the Battle of the Atlantic against U-boat wolfpacks. Turing's team developed complex statistical techniques and leveraged captured materials to finally penetrate this system in 1941.
This breakthrough allowed Allied convoys to avoid U-boat patrol lines, ensuring vital supplies reached Britain. It is estimated that this effort alone shortened WWII by two years and saved millions of tons of shipping and countless lives.
Relevant Statistics and Enduring Data
The numerical scale of the Enigma's operation and its defeat provides a clear picture of its complexity and the monumental effort required to overcome it.
Quantifying the Cryptographic Challenge
The numbers associated with the Enigma machine are staggering. They explain why German high command had absolute confidence in its security.
- Possible Settings: 159,000,000,000,000 (159 quintillion) with 3 rotors and plugboard.
- Key Space: Even with known rotor types, the daily key settings (rotor order, ring settings, plugboard) were immense.
- Speed of Encryption: A trained operator could encrypt a message rapidly, making it practical for field use.
Measuring the Codebreaking Effort
The Allied response matched the scale of the problem with human and mechanical ingenuity.
Decryption time during WWII varied drastically. Early in the war, some codes took months to break, if at all. By 1943, with improved Bombes and streamlined processes, Bletchley Park could often break codes within 6-8 weeks per message system. For urgent tactical intelligence, the goal was often within 24 hours.
The modern AI-based decryption rate of 0.0001%, while seemingly small, represents a significant computational challenge even with 21st-century technology. It highlights that brute-force attacks remain impractical, echoing the historical need for clever algorithmic shortcuts.
Modern Interest and Search Trends
The legacy of the Enigma continues to captivate the public. Search engine data shows a sustained and growing fascination with its history.
- Global Search Volume: Consistent high interest in keywords like "Enigma machine history" and "How was Enigma broken."
- Regional Interest: In India, there are an estimated 25,000 monthly searches in Hindi for related historical and cryptographic topics, indicating widespread global curiosity.
- Educational Trend: Searches for "Enigma simulator" and "cryptography lesson" have risen by 40% in recent years, driven by online learning and cybersecurity awareness.
Cultural Impact and Symbolic Legacy
Beyond its historical role, the Death Machine cipher has become a powerful symbol in popular culture, representing the pinnacle of secret-keeping, the thrill of the intellectual chase, and the ethical dilemmas of intelligence work.
The Enigma in Film, Literature, and Games
The dramatic tension of the codebreaking war has inspired numerous creative works. Major films like *The Imitation Game* (2014) brought the story of Alan Turing and Bletchley Park to a mainstream audience. The machine itself often appears as a visual symbol of mystery and high stakes in espionage thrillers.
In video games, narratives involving "unbreakable codes" frequently draw direct inspiration from the Enigma saga. The machine serves as a benchmark for cryptographic puzzles, teaching players basic principles of codes and ciphers through interactive storytelling.
A Metaphor for the Inscrutable
The term "Enigma" has entered common parlance to describe anything deeply mysterious or puzzling. This extends to metaphorical interpretations in various philosophical and spiritual discussions. Some analyses, particularly in comparative thought, have drawn parallels between the machine's impenetrable logic and profound existential or metaphysical questions.
While these are symbolic links rather than historical ones, they demonstrate how the machine has transcended its original function to become a versatile cultural icon representing the ultimate challenge to human understanding.
Lessons for Modern Cybersecurity
The Enigma story is a foundational case study in cybersecurity education. It teaches critical lessons that are still relevant today.
Human error is the weakest link. German procedural mistakes, like repeating weather report formats or using predictable greetings, provided the "cribs" needed to break the system. Modern phishing attacks exploit similar human vulnerabilities.
No system is permanently secure. The assumption of unbreakability led to catastrophic over-reliance. Today, this underscores the need for defense in depth and regular security updates. The arms race between encryption and cryptanalysis continues unabated in the digital age.
Modern Resurrections: From Hardware to Software
The principles of the Death Machine cipher have not been consigned to history books. Instead, they have found new life in the digital realm. The fascination with its mechanics has led to various modern interpretations that serve educational, security, and even artistic purposes.
Online Simulators and Educational Tools
A significant development in recent years is the proliferation of accurate Enigma machine simulators available online and as software applications. These tools allow students, hobbyists, and researchers to interact with a virtual recreation of the machine.
- Accessibility: These simulators make complex cryptographic concepts tangible without requiring access to rare, physical artifacts.
- Functionality: Users can set rotor types, ring settings, and plugboard connections to encrypt and decrypt their own messages.
- Educational Value: They are invaluable for teaching the fundamentals of symmetric-key cryptography and the importance of key management.
By simulating the machine, modern learners can directly experience the cryptographic challenges that defined a significant part of WWII intelligence warfare.
Cybersecurity Training and Threat Modeling
Beyond education, the Enigma serves as a foundational case study in cybersecurity training. Security professionals use its story to illustrate timeless principles. The process of cracking the Enigma mirrors modern penetration testing: finding weaknesses in a system's implementation rather than its core theory.
Red teams in cybersecurity exercises often face scenarios inspired by historical codebreaking. They must look for procedural flaws, configuration errors, and human factors—the exact vulnerabilities that doomed the Enigma. This historical context provides a powerful narrative for understanding contemporary threats like misconfigured cloud storage or weak encryption protocols.
In 2024, digital recreation projects made the Enigma a tool for ethical hacking training, demonstrating how antique technology informs modern security practices.
The Quantum Future and Cryptography's Next Frontier
The field of cryptography is on the brink of another revolution with the advent of quantum computing. This new paradigm forces a re-examination of all classical encryption methods, including the lessons learned from the Enigma era.
Quantum Computing's Threat to Classical Encryption
The security of much of today's digital communication, including HTTPS and VPNs, relies on mathematical problems that are difficult for classical computers to solve. Quantum computers, however, could solve some of these problems with astonishing speed using algorithms like Shor's algorithm.
This represents a threat analogous to the Bombe's threat to the Enigma. A new technology could render current "unbreakable" encryption obsolete. This has spurred a global race to develop post-quantum cryptography (PQC)—new algorithms designed to be secure against attacks from both classical and quantum computers.
Parallels to the Historical Cryptographic Arms Race
The situation mirrors the WWII dynamic. Just as the Germans continuously added rotors and improved procedures to counter Allied advances, today's cryptographers are proactively developing new standards before quantum computers become powerful enough to be a practical threat.
- Proactive vs. Reactive Defense: The Allied effort was reactive; they had to break an existing system. PQC is a proactive attempt to build defenses before the attack arrives.
- The Human Element: Then and now, the weakest link remains human error in implementation and key management, not just the mathematical strength of the cipher itself.
- Importance of Secrecy: The success at Bletchley Park was kept secret for decades. Similarly, advancements in quantum computing and PQC are areas of intense national security interest.
Legal, Ethical, and Philosophical Reflections
The story of the Enigma machine raises profound questions that extend beyond technology into the realms of law, ethics, and philosophy, many of which are still debated today.
The Ethics of Secrecy and Intelligence Use
The Ultra intelligence derived from breaking Enigma created a moral dilemma for Allied leaders. Using the intelligence risked revealing to the Germans that their codes were compromised. This led to tragic decisions, such as allowing some attacks to proceed to protect the secret.
This ethical challenge persists in modern intelligence and cybersecurity. When a vulnerability is discovered, when should it be disclosed? The balance between operational advantage and public safety is a constant tension, directly prefigured by the Enigma experience.
Legal Frameworks and Historical Penalties
While not directly applicable to the Enigma, historical legal contexts around secret communications and espionage provide a backdrop. In various jurisdictions, penalties for compromising state secrets have always been severe.
Historical fines for non-compliance with official procedures, as seen in some archives, could range significantly, analogous to modern penalties for security breaches. This underscores the perpetual high stakes of handling classified information, whether encoded by a mechanical rotor or a digital algorithm.
Conclusion: The Enduring Legacy of a Cryptographic Icon
The journey of the Death Machine cipher, from a feared tool of war to a revered subject of study, is a testament to its profound impact. Its story is a rich tapestry woven from threads of mathematics, engineering, history, and human drama.
Summary of Key Takeaways
The Enigma's history offers several immutable lessons for the modern age. Its technical brilliance was ultimately undone by a combination of systematic analysis, technological innovation, and human error.
- Cryptographic Strength: The machine's design, capable of 159 quintillion settings, was a masterpiece of its time, demonstrating that complexity alone does not guarantee security.
- The Codebreaking Triumph: The success at Bletchley Park, led by figures like Alan Turing, was a watershed moment that combined intellectual genius with collaborative effort, shortening WWII and saving countless lives.
- The Human Factor: Procedural flaws and operator mistakes were the Achilles' heel of the system, a lesson that remains paramount in today's cybersecurity landscape.
- A Cultural Symbol: The Enigma has transcended its original purpose to become a universal symbol of mystery, intellectual challenge, and the eternal conflict between encryption and decryption.
The Final Word: An Immortal Machine
The Enigma machine is more than a relic; it is a living lesson. It sits at the crossroads of history and technology, reminding us that security is a process, not a product. Its story champions the power of pure intellect over brute force and highlights the critical importance of questioning the supposedly unbreakable.
As we navigate the complexities of the digital age, from quantum threats to AI-driven security, the echoes of the Enigma's rotors are still audible. It teaches us that vigilance, innovation, and a deep understanding of both technology and human nature are our greatest defenses. The mysterious history of this legendary cipher continues to inspire, warn, and guide us, securing its place not just in history books, but in the very foundation of our digital future.



