Understanding the SHA-256 Hashing Algorithm: A Comprehensive Guide
In the realm of cryptography, hashing algorithms play a pivotal role in securing data and ensuring the integrity of digital information. One such algorithm is SHA-256, part of the SHA-2 (Secure Hash Algorithm 2) family, which has become a standard in data protection due to its robustness and security features. This article explores the intricacies of the SHA-256 hashing algorithm, its history, functioning, applications, and why it is a preferred choice in the digital world.
The Genesis of SHA-256
To appreciate the significance of SHA-256, it is essential to understand its origins. Developed by the National Security Agency (NSA) and published by the National Institute of Standards and Technology (NIST) in 2001, the SHA-2 family was introduced as an enhancement over its predecessor, SHA-1. The shift from SHA-1 to SHA-2 was primarily driven by concerns over vulnerabilities that could potentially compromise data integrity.
SHA-256 stands for Secure Hash Algorithm 256-bit, indicating that it generates a hash value that is 256 bits long. This length makes it significantly more secure than the 160-bit hash value produced by SHA-1. The enhanced security was an answer to the growing computational power of attackers and the necessity for stronger cryptographic algorithms in various applications, from digital signatures to password hashing.
How SHA-256 Works
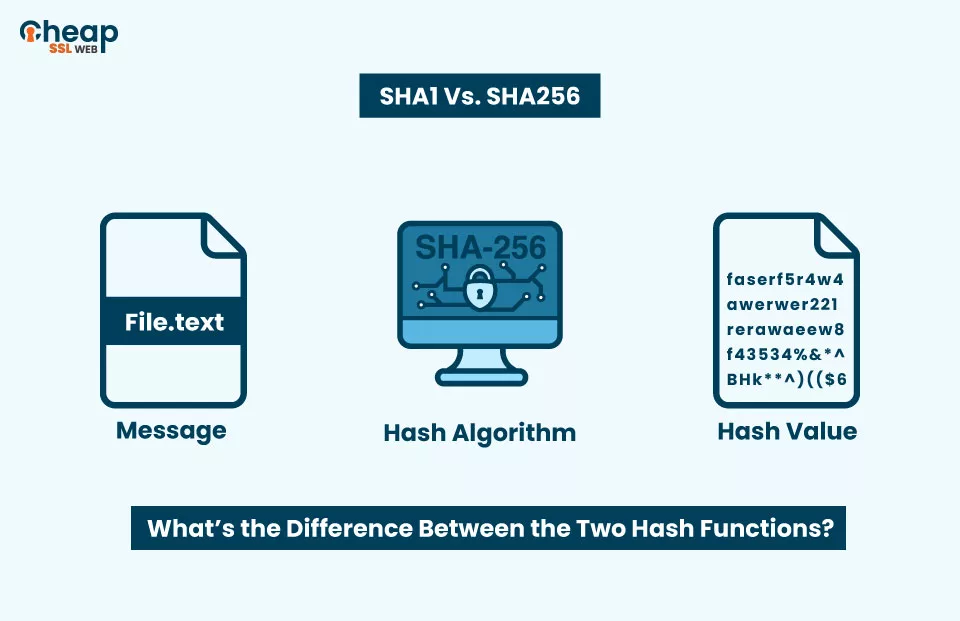
SHA-256 is a deterministic algorithm, meaning that no matter how many times you apply it to the same input, it will always produce the same output, known as a hash value or digest. This property is fundamental for verifying data integrity, as it allows two parties to ensure that a message or piece of data has not been altered during transmission.
The process of hashing with SHA-256 involves several stages:
1. **Pre-processing* This initial step involves padding the input data to ensure that its length is a multiple of 512 bits. This step also includes appending the length of the original message to the end of the padded message.
2. **Message Parsing* The padded message is divided into 512-bit blocks, which are processed individually through several rounds of hashing.
3. **Hash Computation* SHA-256 utilizes a series of logical functions, constant values, and bitwise operations, dispersed across 64 rounds, to compute the hash value from each block. It uses eight working variables, initialized with specific constants, and processes each 512-bit block sequentially. The final hash is constructed from the resulting state of these variables.
4. **Output* The end result is a 256-bit hash value that is unique to the input data provided.
Key Characteristics of SHA-256
The strength and reliability of SHA-256 stem from several of its defining characteristics:
- **Fixed Length Output* Regardless of the size of the input data, SHA-256 always produces a hash value that is 256 bits long. This ensures consistency and makes it easy to compare hash values.
- **Avalanche Effect* A slight change in the input data results in a significantly different hash value. This property is crucial in detecting minute changes in data and ensuring data integrity.
- **Uniqueness* SHA-256 hashes are statistically unique. While it is theoretically possible for two different inputs to produce the same hash (a collision), the likelihood is extraordinarily low due to the 256-bit length of the hash.
- **Irreversibility* Once data is hashed using SHA-256, it is computationally infeasible to retrieve the original input from its hash value, making it an excellent choice for applications requiring data confidentiality.
Applications of SHA-256
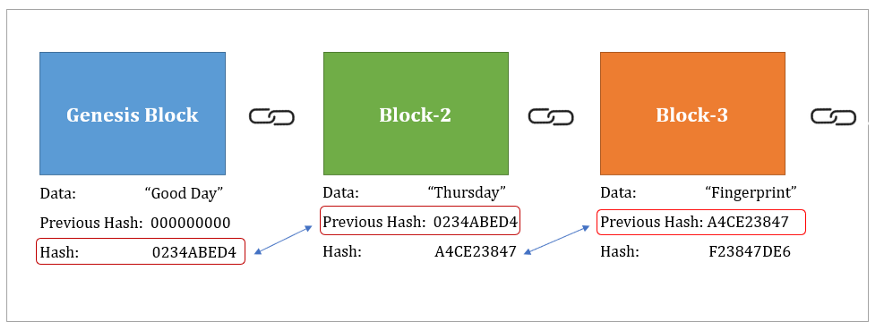
SHA-256 finds extensive use across a broad range of applications, central to which is its role in blockchain technology. Cryptocurrencies like Bitcoin rely heavily on SHA-256 for securing transactions and ensuring trust among users. Each block in a blockchain contains a SHA-256 hash of the previous block, integrating it into the blockchain and preserving its integrity.
Beyond blockchain, SHA-256 is widely used in secure password storage, digital signatures, SSL/TLS certificates, and even in file verification processes. Its reliability and efficiency have made it a staple in cybersecurity protocols.
As we advance to the next parts of this article, we will delve deeper into understanding the limitations of SHA-256, its role in modern security architectures, and how emerging technologies may influence its future application. Stay tuned as we continue to explore the profound impact of this hashing algorithm on the digital world.
Limitations and Challenges of SHA-256
While SHA-256 is celebrated for its security and effectiveness, it is not without limitations and challenges. As cryptographic technologies continue to evolve, it is crucial to examine these limitations and understand how they impact the future of secure data processing.
Computational Intensity
One of the primary criticisms of SHA-256 is its computational intensity. Generating a hash using SHA-256 requires significant processing power relative to some other hashing algorithms. This computational demand can become a bottleneck in environments where resources are limited or where high-speed processing is critical, such as real-time transaction systems or when handling vast datasets.
The computational requirements stem from its design, which, despite providing enhanced security, can be energy-intensive, making it less ideal for devices with limited battery life or in large-scale deployments where energy efficiency is a priority.
Vulnerability to Quantum Computing
Quantum computing presents a unique challenge to cryptographic functions, including SHA-256. While classical computers handle operations in a linear fashion, quantum computers utilize qubits, allowing them to process information exponentially faster for certain tasks.
SHA-256's security is based on its resistance to collision and pre-image attacks—tasks that are computationally infeasible for classical computers. However, it is theoretically possible that a sufficiently advanced quantum computer could perform these tasks significantly faster, thus threatening the security of systems relying solely on SHA-256.
In response, cryptographers are exploring quantum-resistant algorithms and more robust versions of SHA-2, ensuring they are well-prepared for the dawn of practical quantum computing. This proactive approach seeks to maintain data security even as technology evolves.
SHA-256 in Modern Security Architectures
Despite these challenges, SHA-256 continues to be a linchpin in modern security architectures due to its resilience against attacks that are feasible on classical computing platforms. Many organizations integrate SHA-256 into their systems not only for its tried-and-true robustness but also for compliance with industry standards and regulations.
Integration with Blockchain Technology
SHA-256 is perhaps most famously utilized in blockchain technology. Cryptocurrency networks such as Bitcoin rely on SHA-256 not just for hashing blocks but also in mining processes. During mining, miners compute SHA-256 hashes in search of a block hash that meets a specified difficulty target—a process integral to validating transactions and securing the network.
The very foundation of blockchain technology is its ability to create an immutable ledger. SHA-256 plays a crucial role here by ensuring each block is mathematically linked to the preceding block through these hash values, thereby making alterations to past blocks not just detectable, but effectively impossible without redoing the entire chain—a task that becomes exponentially difficult with each new block added.
Enhancing Cloud Security and Data Protection
With the surge in cloud-based services, ensuring data integrity during transmission and storage is imperative. SHA-256 is widely employed in these environments to hash data and verify its integrity. When data is sent across networks or stored in cloud resources, it can be hashed to ensure it remains unaltered, offering an extra layer of protection that is vital for both service providers and their customers.
Furthermore, SHA-256 is an essential component of SSL/TLS, critical protocols for secure communications over the internet. By ensuring data is safely encrypted during transfer, it protects against man-in-the-middle attacks that could compromise sensitive information.
Developments and the Road Ahead
As the digital landscape evolves, so too must hashing algorithms and security protocols. Researchers continue to explore the potential of hashing beyond SHA-256, considering post-quantum cryptography and algorithms capable of withstanding increasing computational advancements.
The SHA-3 family, for example, offers a different approach and is considered as a potential successor or complement to SHA-2 in some scenarios, designed with distinct internals to address emerging threats. However, the transition from SHA-256 to any new standard requires a clear strategy to ensure backward compatibility and a smooth migration path for existing systems.
Moreover, integration with machine learning and AI technologies promises new frontiers in data security. These technologies can augment the capabilities of SHA-256, offering predictive insights into vulnerabilities and threats.
In the forthcoming section of our article, we will delve into case studies where SHA-256 has been instrumental, review real-world applications, and explore user perspectives on the balance between security and performance. We’ll also consider expert opinions on how this algorithm might adapt to future technological shifts. Stay tuned as we continue this exploration of one of the most influential hashing algorithms in the modern digital era.
Real-World Applications and Case Studies of SHA-256
SHA-256's pervasive influence can be observed across various industries and applications, demonstrating its versatility and reliability. From securing financial transactions to data integrity in software applications, this hashing algorithm has become synonymous with trusted cryptographic security.
Cryptocurrencies: The Backbone of Trust
Perhaps the most notable application of SHA-256 is within the realm of cryptocurrencies, with Bitcoin being the most prominent example. The integrity and security of Bitcoin's blockchain are maintained through SHA-256, ensuring that every transaction is verified and immutable.
A pertinent case study is Bitcoin's evolution and resilience against attacks. Over the years, despite numerous attempts to breach Bitcoin's security, its SHA-256 backbone has remained solid, successfully thwarting collision and pre-image attacks. This has bolstered user confidence in cryptocurrency networks, prompting widespread adoption and investment.
Moreover, SHA-256's role in proof-of-work mechanisms not only validates transactions but also controls the release of new cryptocurrencies into circulation. By requiring significant computational work to solve cryptographic puzzles, SHA-256 helps secure the network, albeit with concerns over energy consumption, prompting discussions on proof-of-stake and other innovative alternatives.
Digital Signatures and Secure Communications
Beyond blockchain, SHA-256 is integral to digital signatures, a mechanism widely used to authenticate digital documents. In legal and business sectors, documents bearing digital signatures hashed with SHA-256 provide a guarantee of authenticity and integrity, ensuring that the content has not been altered after signing.
This hashing algorithm also anchors trust in secure communications through SSL/TLS protocols. These protocols, fundamental to internet security, employ SHA-256 to verify the legitimacy of website certificates, safeguarding users against phishing attacks and ensuring that sensitive data, like payment information, is securely encrypted during transmission.
A notable example is its implementation in e-commerce platforms and online banking, where users trust SHA-256 secured environments to carry out transactions safely. These platforms depend on SHA-256 not just for maintaining cryptographic security but also for adhering to strict regulatory requirements concerning data protection.
Password Hashing for Enhanced Security
In the realm of password protection, SHA-256 is frequently used to hash passwords before storing them in databases. This practice ensures that even if a data breach occurs, attackers are unable to retrieve plain-text passwords. Many organizations pair SHA-256 with additional techniques such as salting—adding random data to each password before hashing—to further augment security and complicate potential brute-force attacks.
Real-world attacks and subsequent data breaches have highlighted the importance of robust password hashing, forcing companies to reconsider their security protocols. Learning from past events, numerous organizations have transitioned to SHA-256, acknowledging its ability to mitigate risks associated with weak or compromised passwords, hence fostering a safer digital environment for users.
User Perspectives and Balancing Security with Performance
For many users, the choice to implement SHA-256 involves weighing security benefits against performance costs. Some may find the computational demand associated with SHA-256 cumbersome, particularly in resource-constrained environments or devices. However, given its robust cryptographic assurances, many industries continue to prioritize security over performance, recognizing the long-term advantages of fortified data protection.
Interviews with cybersecurity experts reveal a consensus that, while SHA-256 is currently sufficient for most security needs, organizations should remain vigilant about future vulnerabilities. They stress the necessity for ongoing research into more efficient algorithms, adaptive security measures, and the potential impact of quantum computing on current cryptographic standards.
The Future of SHA-256 and Cryptography
Looking ahead, the future of SHA-256 is likely to evolve alongside advancements in technology and cryptographic research. It will continue to be scrutinized under the lens of emerging threats such as quantum computing, which necessitates innovations in quantum-resistant algorithms.
Cryptographers and technology companies are already exploring SHA-3 and other secure hash functions as potential successors, ensuring a seamless transition when needed. As these innovations progress, understanding the robust foundation provided by SHA-256 will remain crucial, offering insights into the trajectory of cryptographic standards globally.
Advocates of SHA-256 emphasize its vital role as a building block in cybersecurity, but they also foresee enhancements in integration with AI for threat detection, adaptive learning systems to automatically update security measures, and cross-industry collaborations for a more unified approach to data protection.
Conclusion
SHA-256 stands as a testament to modern cryptographic achievement, playing an indispensable role in shaping a secure digital landscape. Despite its challenges related to computational demands and the looming shadow of quantum computing, it remains a stalwart protector in the fight against data breaches and cyber attacks. As technology continues to evolve, so will the applications and implementations of SHA-256, adapting to new challenges and securing digital frontiers for years to come. By understanding its strengths and limitations, industries can better prepare for a future where data integrity and security remain paramount.
















Comments