The Fascinating World of Polyalphabetic Ciphers: A Deep Dive into Cryptographic History
In the realm of cryptography, polyalphabetic ciphers stand as a testament to humanity's enduring quest for secure communication. Used for centuries to shield messages from prying eyes, these ciphers offer a rich tapestry of historical intrigue and operational complexity. As digital technology continues to evolve, understanding these cryptographic methods can offer valuable insights into the foundations of modern encryption.
Understanding Polyalphabetic Ciphers
At its core, a polyalphabetic cipher is an encryption technique that employs multiple substitution alphabets to disguise a message. Unlike monoalphabetic ciphers, which utilize a single letter substitution throughout the entire message, polyalphabetic ciphers alternate between different alphabetic shifts. This complexity renders it significantly more resistant to frequency analysis, a common method of cryptanalysis used to break simpler codes.
One of the defining features of polyalphabetic ciphers is their use of a keyword or key phrase, which guides the selection of substitution alphabets during encryption. Each letter in the keyword corresponds to a different cipher alphabet. When encrypting a message, the sender cycles through these alphabets according to the position of each letter in the keyword, creating a dynamic and versatile encryption process.
The Historical Significance of Polyalphabetic Ciphers
The history of polyalphabetic ciphers is deeply interwoven with the evolution of cryptanalysis and the ongoing battle between code makers and code breakers. While rudimentary forms of cryptography can be traced back to ancient times, the development of polyalphabetic ciphers represented a significant leap in sophistication.
One of the most well-known polyalphabetic ciphers is the Vigenère cipher, which gained notoriety for its apparent inscrutability. Developed during the Renaissance, it employs a tabular method based on a square of 26 rows of the alphabet. This square, often referred to as the Vigenère square or tabula recta, allows for easy substitution driven by a keyword. As each letter of the keyword shifts the alphabet, the resultant encryption is a complex amalgamation of diversions, making it incredibly challenging to decipher without the key.
The cipher, though readily crackable with today's technology, was considered unbreakable for a considerable period in the cryptographic community. Its perceived strength and simplicity in execution without requiring cumbersome tools made it a preferred method for securing diplomatic and military communications across Europe in the 16th and 17th centuries.
The Mechanics Behind Polyalphabetic Ciphers
The operation of polyalphabetic ciphers, such as the Vigenère cipher, is inherently methodical yet intricate. To illustrate this, consider a simple encryption process using the Vigenère cipher.
First, the sender chooses a keyword. For simplicity, let's use the keyword "LEMON." The message to be encrypted is "ATTACKATDAWN." The process begins by repeating the keyword until it matches the length of the plaintext message:
- Plaintext: ATTACKATDAWN
- Keyword: LEMONLEMONLE
The next step involves using the Vigenère square to encrypt each letter of the plaintext. Each letter of the keyword corresponds to a specific alphabet row, and the plaintext letter determines the column. The intersection of the row and column provides the encrypted letter.
For example, using the square:
1. 'A' with 'L' from LEMON: L is the 12th letter, so we take the 'A' row in the Vigenère square and move 12 places to get 'L'.
2. 'T' with 'E': E is the 5th letter, thus T shifts by 5 to 'X'.
3. This is repeated until the entire message is encoded.
The resultant ciphertext, "LXFOPVEFRNHR," appears entirely random and without recognizable patterns, a key advantage of polyalphabetic systems.
Advantages of Polyalphabetic Ciphers
Polyalphabetic ciphers bring a multitude of advantages to the cryptographic table. Their ability to obscure letter frequency patterns makes them a formidable opponent against decryption efforts reliant solely on statistical analysis. This inherent complexity offers a significant layer of security over monoalphabetic ciphers, which are more susceptible to brute force and pattern recognition techniques.
Moreover, the customization capability of polyalphabetic ciphers enhances their adaptability. With a simple change of the keyword, the entire encryption scheme transforms, providing a flexible framework that can adapt to various security needs. This feature was particularly advantageous in historical contexts where messages often needed to be encoded quickly and securely.
However, despite their advantages, polyalphabetic ciphers are not without their vulnerabilities. The reliance on a keyword poses a potential security risk if the keyword is intercepted or guessed. This limitation emphasized the necessity for both complexity in keyword selection and discretion in its transmission.
As we continue our exploration of polyalphabetic ciphers, the second part of this article will delve into the weaknesses and eventual decryption of these fascinating cryptographic systems, examining how historical figures have managed to crack their codes over time. Furthermore, we will consider the enduring impact of polyalphabetic principles in modern cryptography, showcasing their relevance in today's digital encryption landscape. Stay tuned for more on this intriguing topic.
The Vulnerabilities of Polyalphabetic Ciphers
While polyalphabetic ciphers like the Vigenère cipher offered significant advancements in cryptographic security over monoalphabetic systems, they were not invincible. Their complexity could be daunting, but with determined efforts, cryptanalysts developed methods to decode these tricky puzzles. Understanding the vulnerabilities of these ciphers provides valuable lessons and a historical perspective on the evolution of cryptography.
Breaking the Code: The Role of Frequency Analysis
Polyalphabetic ciphers were once considered unbreakable, largely due to their ability to produce ciphertexts that appeared random. However, in the mid-19th century, the cipher was famously broken by the pioneering cryptanalyst Charles Babbage. Though his work was not published, Babbage developed methods to effectively challenge the cipher's integrity.
The breakthrough came with the realization that repeating patterns in intercepts could hint at the cipher's keyword length. This discovery laid the groundwork for the method of Kasiski examination, named after Friedrich Kasiski, who independently published his findings in 1863.
Kasiski's technique involved looking for repeated sequences of letters in the ciphertext that could be attributed to the reuse of the same segments of the keyword. By measuring the distances between these repeating patterns, cryptanalysts could infer the likely length of the keyword. Once the keyword length was deduced, the cipher's decryption became possible by treating the message as a series of interwoven Caesar ciphers—one for each letter of the keyword.
The Impact of Keyword Selection
Another critical vulnerability of polyalphabetic ciphers resided in keyword selection. The security of the system heavily relied on the keyword's secrecy and complexity. Simple, short, or common words as keywords could significantly diminish the cipher's strength, as they were more susceptible to guessing or brute-force attempts.
To heighten security, cryptographers were advised to choose lengthy, random, and nonsensical keywords, minimizing the risk of keyword discovery. Moreover, the transmission and storage of the keyword required stringent measures to prevent compromise.
While Babbage and Kasiski’s methods were revolutionary at their time, they also underscored the importance of maintaining critical intelligence and operational secrecy. The vulnerabilities they unearthed demonstrated that even the most sophisticated cryptographic systems could be compromised by clever, determined adversaries.
The Modern Legacy of Polyalphabetic Ciphers
As we have transitioned into the digital age, the lessons from polyalphabetic ciphers continue to inform contemporary cryptography. While early ciphers have been rendered obsolete by advanced computational techniques and algorithms, the foundational principles of polyalphabetic logic persist in many modern encryption methods.
From Classical Ciphers to Modern Algorithms
The concept of using multiple alphabets in encryption is echoed in today's secure encryption algorithms. Modern systems employ complex mathematical transformations, often incorporating elements reminiscent of polyalphabetic ciphers. This includes the use of variable key lengths and substitution techniques, albeit at a vastly more complex scale.
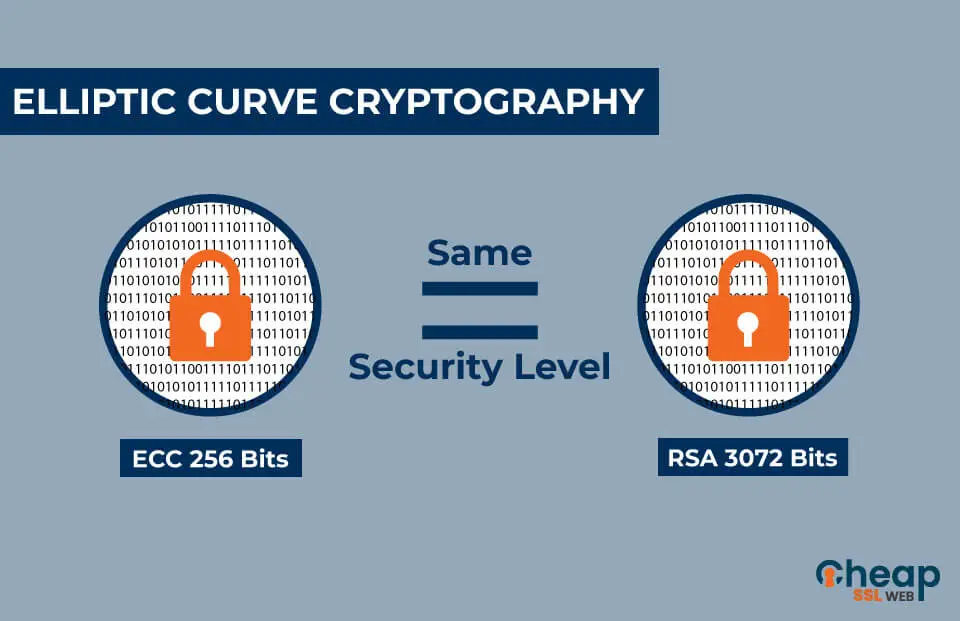
For example, advanced encryption standards (AES) and protocols like RSA and elliptic-curve cryptography (ECC) utilize similar principles of data transformation through expansive key lengths and varied substitution mechanisms. These systems build upon the foundation laid by historic ciphers to create robust, secure methods that protect sensitive data in an era dominated by cyber threats.
Principles and Practices for the Digital Frontier
One of the critical takeaways from the study of polyalphabetic ciphers is the emphasis on key management and length. In today’s digital cryptographic frameworks, the strength of an encryption system is often contingent upon the security and complexity of its keys. Long, unpredictable, and securely distributed keys form the cornerstone of modern secure cryptographic approaches, echoing the lessons learned from their analog predecessors.
Moreover, the historical development of cryptanalysis has nurtured a mindset of vigilance and innovation. The ability to anticipate potential breakthroughs in codebreaking compels modern cryptographers to evolve and refine encryption systems continually. This proactive approach to encryption design ensures resilience in an ever-evolving landscape of cybersecurity threats.
Conclusion: A Legacy of Innovation and Resilience
Polyalphabetic ciphers like the Vigenère cipher represent much more than historical artifacts. They embody the relentless pursuit of secure communication and the perpetual cat-and-mouse game between cryptographers and cryptanalysts. These ciphers illustrate the rudimentary yet ingenious efforts to safeguard information, a pursuit that continues to evolve and challenge modern cryptologists.
As we explore the nuances of these influential cryptographic techniques, it is evident that although technology has vastly advanced, the fundamental principles remain pertinent. Understanding the weaknesses and strengths of historical methods permits an appreciation of how far we have come and underscores the importance of continuous innovation in cryptography.
In the final segment of this article, we will delve into notable historical instances where polyalphabetic ciphers played crucial roles, exploring their applications and deciphering tales of espionage and diplomacy that highlight their enduring allure and significance.
Historical Instances of Polyalphabetic Cipher Use
Throughout history, polyalphabetic ciphers have not only showcased human ingenuity in the field of cryptography but have also played pivotal roles in shaping political and military strategies. Their application, often in high-stakes scenarios of war and diplomacy, reveals fascinating tales of code-making and breaking. In this final segment, we will explore some notable instances where these ciphers left their mark.
The Cipher Wars of the Renaissance
The Renaissance era was a time of tremendous intellectual and scientific progress, but it also witnessed fierce rivalries among European powers. During this period, polyalphabetic ciphers emerged as essential tools of statecraft. Diplomats and monarchs used these ciphers to encrypt sensitive correspondence, thereby safeguarding plans and negotiations from enemies and rivals.
One of the most illustrative examples is the diplomatic correspondence between European monarchs during the 16th and 17th centuries. Known for its political intrigue, this era frequently saw the use of polyalphabetic ciphers in their dispatches. The Vigenère cipher, in particular, was embraced due to its relative simplicity and perceived invulnerability, even earning the moniker "the indecipherable cipher" until its vulnerabilities were eventually exposed.
Ciphers in Military Communication
Beyond the diplomatic sphere, polyalphabetic ciphers held a strategic place in military communications. During various conflicts, the ability to transmit encrypted messages without enemy interception presented a considerable advantage. Commanders relied on these ciphers to secure troop movements, supply chain instructions, and strategic orders.
One compelling case of military cipher use was during the American Civil War. Although the Confederate and Union forces primarily employed simpler cipher systems, polyalphabetic ciphers surfaced occasionally in drafted encryption methods. The constraints of the time, particularly the need for expedient communication and limited availability of sophisticated equipment, dictated the choice of cipher systems deployed.
Later, during the World Wars, encryption technology had advanced significantly, but the foundational principles of polyalphabetic ciphers still informed the design of more sophisticated encryption machines. Devices like the Enigma machine, which became infamous during World War II, extended these principles into electromechanical engineering, showcasing the evolution of polyalphabetic concepts into increasingly complex encryptions.
Literary Intrigue and Espionage
In addition to military and diplomatic uses, polyalphabetic ciphers have frequently appeared in literature and espionage tales, adding layers of mystery and drama to storytelling. Historically accurate depictions of cryptanalysts working to unravel polyalphabetic codes have been featured in novels and films, capturing the imagination of audiences and shedding light on the art of codebreaking.
One historical anecdote enhancing this narrative was the Papal encyclicals during the Counter-Reformation, where ciphers, including polyalphabetic variants, obscured sensitive decrees intended only for loyal components within the church's structure. These clandestine documents, when decrypted by opposing forces or reformers, sometimes resulted in dramatic diplomatic shifts and profound religious controversies.
The romanticism of ciphers in literature often underscores a broader human fascination with the mystery and challenge inherent in deciphering coded messages—the thrill of secret knowledge waiting to be unlocked. This element of cryptography’s history highlights the cultural and intellectual allure these ciphers have carried through the ages.
Modern Reflections on Polyalphabetic Ciphers
As we survey the extensive history of polyalphabetic ciphers, it becomes clear that their influence persists in various facets of modern life. Cryptography today owes much to the foundational work of early cipher systems, and understanding these historical approaches enriches our comprehension of current encryption technologies.
Polyalphabetic ciphers symbolize an innovative spirit and an unending quest for secure communication—a quest that has transformed with time but remains as vital as ever. In the contemporary digital landscape, where data protection and privacy are paramount, the legacy of polyalphabetic logic continues to echo through the architectures of cybersecurity systems.
By studying the successes and failures of these early cipher systems, both historians and technologists can appreciate the progress in encryption methodology and the ingenuity of human intellect in overcoming cryptographic challenges.
Conclusion: The Enduring Legacy of Polyalphabetic Ciphers
The tale of the polyalphabetic cipher is one of continuous adaptation and evolution. These ciphers emerged at the crossroads of necessity and ingenuity, providing secure communication long before the digital age redefined our concept of privacy and security. Their story reflects a rich history of intellectual strife and breakthroughs, marking significant contributions to both historical events and modern cryptographic practices.
Their enduring legacy serves as a reminder that in the ever-evolving world of cryptography, the art of code-making and breaking is both a historical and technological journey. Polyalphabetic ciphers remain a testament to the profound impact of cryptographic thought, forging a path for future innovations as we strive for even greater heights in the realm of secure communication.










Comments