The Enigma Machine: A Fascinating Tale of Encryption and Espionage
Introduction
The Enigma machine stands as one of the most iconic and mysterious inventions of the 20th century. A sophisticated cipher device used primarily during World War II, it became synonymous with encryption, intelligence, and the high-stakes battle between code makers and code breakers. The story of the Enigma machine is not just about technology; it encompasses history, mathematics, and the incredible efforts of cryptanalysts who worked tirelessly to unravel its secrets. In this article, we will explore the origins, mechanics, and significance of the Enigma machine, as well as its impact on modern cryptography.
The Origins of the Enigma Machine
Early Development
The Enigma machine was not originally designed for military use. Its earliest versions were conceived in the aftermath of World War I by German engineer Arthur Scherbius, who patented the device in 1918. Scherbius envisioned the Enigma as a commercial encryption tool for businesses seeking to protect sensitive communications. However, the machine's potential for military applications quickly became apparent.
In the 1920s, the German military recognized the advantages of secure communication and began adapting Scherbius’s invention. By the 1930s, customized versions of the Enigma were being used by the German Army, Navy, and Air Force. The machine's ability to scramble messages into seemingly indecipherable code made it a critical asset for Germany’s wartime strategy.
How the Enigma Machine Worked
At its core, the Enigma machine was an electromechanical device designed to encrypt and decrypt messages. It resembled a typewriter but functioned as a highly complex substitution cipher. The operator would type a plaintext letter, and the machine would output an encrypted letter based on a series of rotating wheels and electrical circuits.
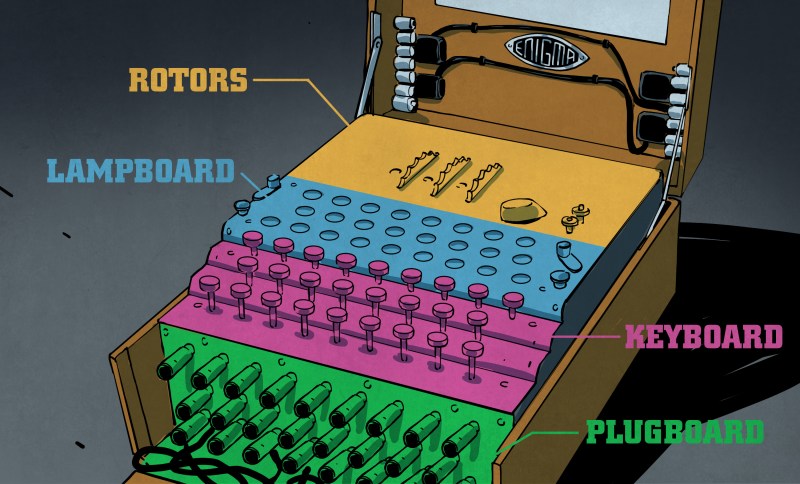
Key Components
The Enigma consisted of several crucial components:
- Keyboard: Used to input plaintext letters.
- Rotors (Wheels): The primary encryption mechanism. Each rotor contained a unique wiring pattern that scrambled the input letter as it passed through.
- Plugboard: Added an additional layer of complexity by swapping letters before and after they passed through the rotors.
- Lampboard: Displayed the encrypted letter after processing.
The brilliance of the Enigma lay in its variable settings. The rotors could be configured in different starting positions, and the plugboard could be rewired in numerous ways, creating billions of possible encryption combinations. This made brute-force decryption nearly impossible without knowledge of the exact settings used by the sender.
The Unbreakable Code?
German Confidence and Allied Concerns
German military leaders believed the Enigma machine produced an unbreakable cipher. The sheer number of possible configurations—approximately 158 quintillion—was daunting for any adversary. However, this confidence proved to be a double-edged sword. While the Enigma provided secure communications, the assumption of its invincibility led to occasional lapses in operational security that would later be exploited by Allied cryptanalysts.
Early Efforts to Crack Enigma
Before World War II, Polish cryptographers were among the first to recognize the threat posed by the Enigma. In the 1930s, a team of Polish mathematicians—Marian Rejewski, Jerzy Różycki, and Henryk Zygalski—made groundbreaking progress in reverse-engineering the machine’s mechanics. Using mathematical theories and careful observation, they developed tools such as the "Bomba" to decrypt Enigma messages. However, as Germany increased the complexity of their encryption methods, Poland shared their findings with Britain and France in 1939.
The Role of Bletchley Park
With the outbreak of World War II, Britain assembled a team of codebreakers at Bletchley Park, a secret facility dedicated to intelligence operations. Among them was Alan Turing, a mathematician whose work would prove pivotal in defeating Enigma. Building on the Polish contributions, Turing developed the "Bombe," a more advanced electromechanical device capable of deducing Enigma settings at an unprecedented speed.
Impact and Legacy
The Turning Point in the War
The successful decryption of Enigma-encrypted messages gave the Allies a critical advantage. Intelligence gathered from decoded communications—referred to as "Ultra"—allowed for strategic military decisions that influenced key battles, including the Battle of the Atlantic. Historians estimate that breaking Enigma shortened the war by at least two years, saving countless lives.
Modern Cryptography Lessons
The Enigma’s legacy extends beyond World War II. It demonstrated the importance of cryptography in national security and spurred advancements in computer science. Alan Turing’s work, in particular, laid the foundation for modern computing and artificial intelligence. Today, encryption technologies—though far more advanced—still grapple with the same fundamental challenge of balancing security with accessibility.
Stay tuned for the next part of this article, where we will delve deeper into the personalities behind the Enigma’s history, the evolving complexities of wartime cryptography, and the ethical debates surrounding intelligence operations.
>The Human Side of the Enigma Story
Unsung Heroes of Cryptography
While the Enigma machine itself was a technological marvel, the human element of its story is equally compelling. Beyond the famous figures like Alan Turing, thousands of individuals worked tirelessly to break the German codes. Many were mathematicians and linguists, but others were clerks, engineers, and even crossword puzzle champions recruited for their pattern recognition skills. Women played a particularly crucial role at Bletchley Park, making up about 75% of the workforce. Their contributions, often overlooked in historical accounts, were vital to the Allied victory.
The Daily Life of Codebreakers
Life at Bletchley Park was a strange mix of intense intellectual work and military discipline. Codebreakers worked in shifts around the clock, with strict security protocols that forbade discussing their work even with colleagues in different sections. The pressure was immense - a single decrypted message could mean the difference between life and death for thousands. Workers developed coping mechanisms, from musical performances in the mansion's ballroom to elaborate pranks played on colleagues. The stress took its toll, with many suffering from what we would now recognize as burnout, though they soldiered on knowing the stakes.
Technological Evolution of the Enigma
German Countermeasures
As the war progressed, German forces continually upgraded their Enigma machines to counter Allied decryption efforts. The most significant change came in 1942 with the introduction of the four-rotor naval Enigma (M4), which dramatically increased the possible settings. This upgrade caused a "blackout" in Allied intelligence that lasted nearly a year until the code was broken again. Other modifications included more frequent key changes, destruction of codebooks when threatened with capture, and the introduction of additional security procedures for high-level communications.
Allied Technological Responses
To keep pace with German improvements, Bletchley Park developed increasingly sophisticated decryption machines. The most famous was Colossus, the world's first programmable electronic computer, designed specifically to break the more complex Lorenz cipher used by German high command. Meanwhile, the U.S. Navy developed the Bombe machines based on British designs, with over 100 in operation by 1945. These technological arms races in cryptography foreshadowed the Cold War's computing developments and the digital revolution that followed.
Ethical Dilemmas of Codebreaking
The Cost of Secrecy
One of the most difficult aspects of Ultra intelligence was determining when to act on decrypted information without revealing that the code had been broken. Sometimes, this meant allowing attacks to proceed that could have been prevented, or carefully staging "accidental" discoveries of information to maintain the illusion. The most controversial example was the bombing of Coventry in November 1940 - while the exact nature of what was known remains debated, it illustrates the impossible choices intelligence officers faced in balancing immediate lives against long-term strategic advantage.
Post-War Consequences
After the war, the Allies carefully guarded the secret of their codebreaking success, even returning captured Enigma machines to Germany to avoid suspicion. This secrecy had far-reaching consequences - it meant many veterans couldn't discuss their wartime service for decades, and the full story of their achievements only emerged in the 1970s. Meanwhile, former Axis cryptographers were recruited by both sides in the Cold War, with their expertise shaping the next generation of cryptographic systems.
Enigma in Popular Culture
From Obscurity to Fame
For decades after the war, the Enigma story remained classified. When the truth finally emerged, it captured the public imagination. The 2001 film "Enigma" (though fictionalized) introduced the story to new audiences, while books like "The Code Book" and "Cryptonomicon" explored its historical and technological significance. The 2014 film "The Imitation Game" brought Alan Turing's story to mainstream attention, though it took significant dramatic liberties with historical facts.
Enigma Collectors and Replicas
Today, original Enigma machines are highly prized collector's items, with working models selling for hundreds of thousands of dollars at auction. Several museums have working replicas that demonstrate the encryption process, and hobbyists have built functional recreations using modern components. The fascination with Enigma persists as a symbol of both human ingenuity and the complex moral calculus of war.
In the final section of this article, we'll examine the Enigma's lasting impact on modern technology, the ongoing debates about its historical interpretation, and where you can see surviving Enigma machines today.
The Enduring Legacy of the Enigma MachineThe Birth of Modern Cryptography
The Enigma machine’s influence extends far beyond World War II. Its complex encryption methods laid the foundation for modern cryptography, shaping the digital security systems we rely on today. The principles of substitution, permutation, and key-based encryption that defined Enigma are still fundamental to cybersecurity.
One of the most significant developments inspired by Enigma was the creation of the **Data Encryption Standard (DES)** in the 1970s, which later evolved into the **Advanced Encryption Standard (AES)**—the backbone of secure internet communication. Without the cryptographic challenges posed by Enigma, modern encryption might not have advanced as quickly.
The Turing Test and Artificial Intelligence
Alan Turing’s work on breaking Enigma didn’t just contribute to wartime intelligence—it also shaped the future of computing. His theoretical work on computation led to the **Turing Machine**, a conceptual model for modern computers. Later, he proposed the **Turing Test**, a benchmark for artificial intelligence.
Tragically, despite his contributions, Turing faced persecution for his sexuality and was subjected to chemical castration. He died in 1954, long before his work was fully recognized. In 2013, he received a posthumous royal pardon, and today, he is celebrated as a pioneer of computer science.
The Ethical Debate: Secrecy vs. Transparency
The story of Enigma raises important ethical questions about intelligence operations. Governments must balance **national security** with **historical transparency**. For decades, the full extent of Allied codebreaking efforts was classified, leaving many veterans unable to share their contributions.
Some argue that keeping such information secret was necessary to protect intelligence methods. Others believe that the public has a right to know the full history of wartime efforts. This debate continues today, especially with modern surveillance technologies like **mass data collection** and **AI-driven intelligence**.
Where to See Enigma Machines Today
Several museums around the world house original Enigma machines, allowing visitors to see the device that changed history. Some notable locations include:
- **Bletchley Park (UK)** – The historic site of British codebreaking, now a museum.
- **National Cryptologic Museum (USA)** – Located near the NSA headquarters in Maryland.
- **Deutsches Museum (Germany)** – Features a collection of wartime encryption devices.
- **Polish Army Museum (Poland)** – Honors the early Polish contributions to breaking Enigma.
Many of these museums offer interactive exhibits where visitors can try their hand at encryption and decryption, providing a hands-on understanding of how Enigma worked.
The Enigma in Popular Culture
The intrigue surrounding the Enigma machine has inspired countless books, films, and documentaries. Some of the most notable include:
- **"The Imitation Game" (2014)** – A dramatized account of Alan Turing’s life, though criticized for historical inaccuracies.
- **"Enigma" (2001)** – A fictional thriller based on Robert Harris’ novel.
- **"Cryptonomicon" (1999)** – A novel by Neal Stephenson that weaves Enigma’s history into a modern tech thriller.
These works have helped keep the Enigma’s story alive, introducing new generations to the fascinating world of cryptography.
The Future of Encryption
As technology advances, encryption continues to evolve. **Quantum computing** poses a new challenge—current encryption methods could be broken by quantum algorithms, leading to a race for **post-quantum cryptography**. Governments and tech companies are already working on new encryption standards to withstand future threats.
The Enigma machine reminds us that **security is a constant battle**—what was once unbreakable can become obsolete. The lessons from World War II cryptography still apply today: innovation, vigilance, and ethical responsibility are key to protecting information.
Final Thoughts
The Enigma machine is more than a historical artifact—it’s a symbol of human ingenuity, perseverance, and the complex relationship between secrecy and progress. Its story encompasses **war, science, ethics, and technology**, making it one of the most fascinating chapters in modern history.
From the mathematicians who cracked its codes to the modern encryption that secures our digital lives, Enigma’s legacy endures. As we move into an era of AI and quantum computing, the lessons of Enigma remain relevant: **the best defense is constant evolution.**
Would you like to try decrypting a message yourself? Some online simulators let you experience the challenge firsthand—just remember, it’s not as easy as it looks!



















Comments