The Birth of Modern Cryptography: A Journey Through Time and Technology
Cryptography, the art of securing communication, has been evolving for millennia, rooted deep in the shadows of secrecy and complexity. However, the twentieth century marked a pivotal era in this ancient craft. This was the dawn of modern cryptography, where complex algorithms and advanced computational theories emerged, transforming the digital landscape into a safer haven for secure communication. This article delves into the birth of modern cryptography, exploring the key milestones that have redefined the way we protect our digital communications.
The Early Foundations of Cryptography
To understand modern cryptography, it's essential to glance back at its ancient origins. Cryptography's roots can be traced back to the Egyptian Old Kingdom, around 2000 BCE, where hieroglyphs were used for obfuscation. Fast forward to World War II, and the use of codes and ciphers had already become a crucial element of military strategy. However, these traditional methods lacked scientific rigor and relied heavily on paradigm-based algorithms like Caesar’s cipher, where letters were simply shifted for encryption.
The Enigma machine, famously used by the Germans during World War II, was a landmark in cryptographic technology. Despite its complexity, it was ultimately deciphered by the Allies, showcasing the necessity for more secure cryptographic methods. This marked a turning point, signaling the need for an evolution in cryptography that took advantage of emerging computational technologies.
The Advent of Computers and Their Impact on Cryptography
The post-WWII era witnessed rapid advancements in computer technology, setting the stage for the birth of modern cryptography. The development of computers provided the tools needed for creating more complicated and secure cryptographic protocols. The 1970s, in particular, proved to be a definitive decade for cryptography as computing started to become mainstream.
The most significant breakthrough in this era was the publication of the Data Encryption Standard (DES) by the US National Institute of Standards and Technology (NIST) in 1977. DES utilized a 56-bit key and was intended for commercial applications, making it one of the first efforts to standardize encryption. Although DES is now considered insecure by today's standards due to advancements in computational power, it laid the groundwork for future cryptographic algorithms, underscoring the necessity of standards in operational security.
Public Key Cryptography: A Paradigm Shift
The most profound advancement in modern cryptography came with the introduction of public key cryptography. This revolutionary concept, which solved critical issues posed by symmetric-key algorithms, changed the landscape entirely. In symmetric key cryptography, both the sender and recipient shared a single private key. While straightforward, this method posed significant security risks, particularly for key distribution.
In 1976, Whitfield Diffie and Martin Hellman introduced the concept of public key cryptography, solving the key distribution problem by using two separate keys: a public key known to everyone and a private key known only to the recipient. This revolutionary idea eliminated the need for both parties to share a secret key via insecure channels and formed the foundation for future cryptographic protocols.
Shortly thereafter, in 1978, Ronald Rivest, Adi Shamir, and Leonard Adleman introduced RSA (Rivest–Shamir–Adleman) encryption, utilizing the public key infrastructure proposed by Diffie and Hellman. RSA encryption became fundamental to the growth of secure communications and remains one of the most widely used encryption systems for its robust security capabilities based on the computational complexity of factoring large numbers.
Hash Functions and Security Protocols
As the internet began to emerge as a vital tool for communication and commerce in the late 20th century, there was a growing need for additional cryptographic tools. This era saw the development and implementation of hash functions, which became crucial components of modern cryptographic systems.
Hash functions, such as SHA (Secure Hash Algorithm), produce a fixed-size string of characters from input data of any size. These functions are fundamental in ensuring data integrity, password storage, and digital signatures, serving as a backbone for data verification and authentication processes. They play a pivotal role in modern security protocols like SSL/TLS, which facilitate secure communications across the internet.
Moreover, the introduction of digital signatures, which are based on public key cryptography, offered a means to authenticate the legitimacy of digital documents and messages. Digital signatures ensure the origin and integrity of a message, allowing users to confirm the identity of the sender, adding an essential layer of security that has become indispensable in digital transactions.
In summary, the birth of modern cryptography was marked by significant advancements in computational capabilities and a shift in theoretical approaches, from traditional methods to sophisticated algorithms. As digital communication continues to evolve, these foundational developments in cryptography remain pivotal, ensuring that the digital world operates within a framework of security and trust.
The Rise of Advanced Encryption Standards
As the digital age advanced into the 21st century, the need for faster, more secure encryption standards became critical. The limitations of existing systems like the Data Encryption Standard (DES) became increasingly apparent. With computational power growing exponentially, DES was vulnerable to brute-force attacks where hackers could systematically try every possible key until they cracked the code. The call for an updated encryption method resulted in the introduction of the Advanced Encryption Standard (AES) in 2001.
Selected by the U.S. National Institute of Standards and Technology (NIST) after a rigorous public competition, AES is based on the Rijndael cipher, developed by Belgian cryptographers Vincent Rijmen and Joan Daemen. AES uses a block size of 128 bits and supports key sizes of 128, 192, and 256 bits, offering greater security against brute-force attacks. Its design ensures that even with significant computational advancements, cracking an AES-encrypted message remains infeasible. This adaptability and robustness have led to its widespread adoption in securing sensitive data around the world.
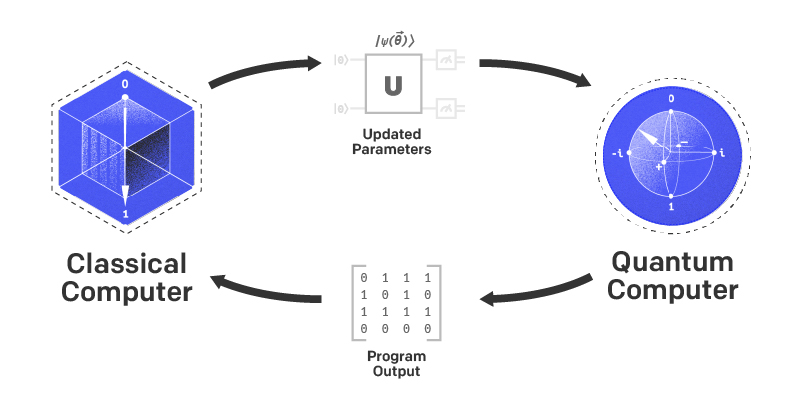
Quantum Computers: A New Challenge for Cryptography
While AES and other modern cryptographic protocols provide formidable security against current computational threats, the looming horizon of quantum computing poses unprecedented challenges to established systems. Quantum computers, leveraging the principles of quantum mechanics, promise to solve certain types of mathematical problems far more efficiently than classical computers. This includes factoring large integers and solving discrete logarithms, which underpins the security of many contemporary cryptographic systems like RSA and elliptic curve cryptography.
The potential of quantum computers to break existing encryption protocols underscores the urgent need for quantum-resistant algorithms. Researchers are earnestly seeking solutions that could ensure data security in the post-quantum era. This emerging field of post-quantum cryptography aims to develop algorithms that can withstand the power of quantum computation, safeguarding digital communications against future threats.
The Evolution of Cryptographic Practices
The evolution of cryptography doesn't rest solely on algorithms and computational capabilities; it also encompasses best practices and policies that govern cryptographic use. In parallel with technological advancements, the rise of networked systems and the internet prompted the development of protocols designed to protect online interactions.
The Transport Layer Security (TLS) protocol is one such example, originally developed as the Secure Sockets Layer (SSL) protocol by Netscape Communications to secure internet connections. TLS encrypts data as it travels over the web, ensuring privacy and data integrity, preventing third parties from eavesdropping or tampering with transmitted messages. With continuous updates to address emerging vulnerabilities, TLS remains integral to maintaining secure online transactions, from banking to confidential communications.
Moreover, the emphasis on open standards and interoperability has become increasingly significant in modern cryptographic practices. Public scrutiny and analysis of cryptographic protocols are encouraged to uncover vulnerabilities and bolster the resilience of systems. This openness allows continuous improvement and adaptation of cryptographic techniques, ensuring robust security measures are in place to protect information in an ever-changing threat landscape.
The Human Factor: Social Engineering and Cybersecurity
While cryptography provides essential technical protection against unauthorized access, the human element often remains the Achilles' heel in secure communications. Social engineering attacks exploit human psychology rather than technical vulnerabilities, manipulating individuals into divulging confidential information.
Cybersecurity experts stress the importance of integrating cryptographic solutions with comprehensive security strategies that include educating users about social engineering tactics, such as phishing and pretexting. This holistic approach combines technology, policy, and awareness to create a multi-layered defense against security breaches.
Organizations are increasingly focusing on creating a cybersecurity culture, where employees are vigilant and informed about potential threats. Training programs and simulations are employed to equip users with the knowledge and skills necessary to recognize and resist social engineering attacks, thereby enhancing the overall security posture of the organization.
Cryptography in the Era of Data Privacy
In recent years, the dialogue around data privacy has intensified, placing cryptography at the forefront of discussions surrounding personal and organizational data protection. As massive data breaches make headlines, individuals and companies are more aware than ever of the implications of inadequate data security.
Legislation like the European Union’s General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) underscores the legal imperatives of protecting personal data. These laws mandate stringent data protection measures, driving organizations to adopt robust cryptographic practices to ensure compliance.
Moreover, end-to-end encryption has gained widespread attention as a means of securing private communications. It ensures that messages are encrypted on the sender's device and can only be decrypted on the recipient's device, preventing intermediaries, including service providers, from accessing the content. Applications, particularly in messaging and email services, widely implement end-to-end encryption as a response to growing privacy demands from users.
In conclusion, the journey of modern cryptography from its nascent realization in the 20th century to becoming an integral component of today’s technological ecosystem is a testament to human ingenuity and the relentless pursuit of secure communication. As new challenges arise, cryptography continues to innovate, safeguarding the integrity and confidentiality of information in a dynamic digital world. This evolution promises to shield our communications both from present threats and those on the horizon.
The Cryptographic Ecosystem in Blockchain Technology
Among the most revolutionary applications of modern cryptography is its role in blockchain technology. Blockchain, the underlying technology for cryptocurrencies like Bitcoin, relies heavily on cryptographic principles to function. Its decentralized nature, combined with cryptography, ensures transaction security, data integrity, and participant anonymity.
At the heart of blockchain is the concept of a distributed ledger, which is secured using cryptographic hash functions. Each block in the chain contains a cryptographic hash of the previous block, a timestamp, and transaction data, forming a secure and immutable chain. This configuration ensures that once data is recorded, it cannot be altered retroactively without altering subsequent blocks, providing a robust defense against tampering and fraud.
Public key cryptography also plays a crucial role in blockchain technology, particularly in decentralizing control and ensuring user anonymity. Each participant in the blockchain ecosystem has a pair of cryptographic keys: a public key used to receive transactions and a private key used to sign transactions. This model simultaneously ensures transparency in transactions, as the public key is visible on the public ledger, and privacy, as the private key remains secure with the user.
Emerging Trends and Future Innovations
As cryptography continues to evolve, several emerging trends promise to further transform this field and its applications. One such innovation is homomorphic encryption, allowing computations to be carried out on encrypted data without decrypting it first. This breakthrough has profound implications for data privacy, enabling secure data analysis in the cloud, where third-party service providers can perform computations on data without accessing the actual content.
Zero-knowledge proofs (ZKPs) represent another milestone in cryptography. ZKPs allow one party to prove to another party that a statement is true without revealing any information beyond the validity of the statement itself. This elegant solution holds potential in numerous areas, such as securing voting systems, enhancing privacy in blockchain transactions, and authenticating users without revealing passwords.
Furthermore, the integration of artificial intelligence (AI) into cryptographic systems is an emerging frontier. AI and machine learning algorithms can enhance security by predicting and mitigating potential attacks, identifying patterns and anomalies that may indicate a security breach. As cyber threats continue to evolve, leveraging AI within cryptographic frameworks offers an adaptive and proactive approach to security.
Cryptography's Role in Securing Emerging Technologies
Beyond blockchain, cryptography plays a pivotal role in securing an array of emerging technologies, including the Internet of Things (IoT), autonomous vehicles, and smart city infrastructures. The proliferation of connected devices in the IoT ecosystem presents new security challenges, as each device could potentially serve as an entry point for cyberattacks. Cryptography is essential in safeguarding communications between these devices, ensuring data confidentiality, integrity, and authenticity.
In the realm of autonomous vehicles, cryptographic protocols secure vehicle-to-vehicle (V2V) and vehicle-to-infrastructure (V2I) communications. Ensuring the authenticity and integrity of these communications is critical for maintaining the safety and reliability of self-driving cars, preventing malicious entities from tampering with navigation or control systems.
Smart cities, composed of interconnected systems that manage everything from traffic flow to energy distribution, depend on cryptography for secure operations. The seamless integration of cryptographic solutions into the fabric of smart cities is vital for protecting sensitive data and ensuring the efficient and secure management of urban resources.
Enduring Challenges in Cryptography
Despite its advancements, cryptography is not without challenges. One ongoing issue is the balance between cryptographic strength and efficiency. Stronger encryption often requires more computational resources, posing challenges in environments with limited hardware capabilities, such as IoT devices. Finding efficient yet secure algorithms remains a priority for researchers.
Regulatory and ethical considerations also pose significant challenges. While cryptography is essential for privacy and security, it can also be misused for illicit activities. Governments and law enforcement agencies grapple with the challenge of balancing the need for encryption with the need for surveillance and crime prevention, often provoking debates on privacy rights versus national security.
The unpredictability of emerging threats, such as quantum computing, necessitates a continuous reevaluation of cryptographic strategies to anticipate future challenges and vulnerabilities. This dynamic landscape requires ongoing collaboration between academia, industry, and government to innovate and adapt to new realities.
Conclusion: The Continuing Evolution of Cryptography
The story of modern cryptography is one of perpetual innovation and adaptability. As it continues to evolve, cryptography remains a cornerstone of secure communications, underpinning the trust and security of our digital lives. From its early mathematical formulations to its sophisticated modern applications, cryptography has proven indispensable in protecting sensitive information against an increasingly complex array of threats.
In a world that increasingly relies on digital communication and interconnected systems, cryptography's role is more critical than ever. As new technologies emerge and evolve, so too will the cryptographic techniques that safeguard them. The future promises further advancements as the field addresses the challenges and opportunities of an ever-changing technological landscape. As we look ahead, the enduring journey of cryptography reflects our collective commitment to ensuring a secure and trustworthy digital future.











Comments