Robert J. Skinner: The Cyber Guardian of the Digital Age
From Second Lieutenant to Three-Star General: A Journey of Leadership and Innovation
In the ever-evolving landscape of cyber warfare and digital defense, few names stand out like that of **Robert J. Skinner**. A retired United States Air Force lieutenant general, Skinner's career spans over three decades, marked by relentless dedication to communications, cyber operations, and information systems. His journey from a second lieutenant to a three-star general is not just a testament to his leadership but also a reflection of the critical role cybersecurity plays in modern military operations.
The Early Years: Foundation of a Cyber Leader
Robert J. Skinner's story begins on **November 7, 1989**, when he was commissioned as a second lieutenant via Officer Training School. His early achievements were a harbinger of the stellar career that lay ahead—he graduated as the second honor graduate, a clear indication of his commitment and prowess. Over the next three decades, Skinner would climb the ranks, eventually reaching the pinnacle of his military career as a lieutenant general on **February 25, 2021**.
Skinner’s early career was defined by his roles in tactical communications and space operations. He commanded the **27th Communications Squadron** from 2000 to 2002, where he honed his skills in managing critical communication infrastructures. This was followed by his leadership of the **614th Space Communications Squadron** from 2004 to 2005, a role that underscored his expertise in space-based communications—a domain that has become increasingly vital in modern warfare.
Rising Through the Ranks: A Career of Strategic Impact
Skinner’s career trajectory is a masterclass in strategic leadership. His roles were not confined to a single domain but spanned a broad spectrum of military operations. He served as the **director of Command, Control, Communications, and Cyber for U.S. Indo-Pacific Command**, a position that placed him at the heart of one of the most strategically important regions in the world. Here, he was responsible for ensuring seamless communication and cybersecurity across a vast and complex theater of operations.
His tenure as the **Deputy Commander of Air Force Space Command** further solidified his reputation as a leader who could navigate the complexities of space and cyber operations. In this role, Skinner was instrumental in shaping the Air Force’s approach to space-based assets, ensuring that the U.S. maintained its technological edge in an increasingly contested domain.
Commanding the Digital Frontier: Leading DISA and JFHQ-DoDIN
Perhaps the most defining chapter of Skinner’s career came when he was appointed as the **Director of the Defense Information Systems Agency (DISA)** and **Commander of Joint Force Headquarters-Department of Defense Information Network (JFHQ-DoDIN)**. From 2021 to 2024, Skinner led a team of approximately **19,000 personnel** spread across **42 countries**, tasked with modernizing and securing the Department of Defense’s global IT infrastructure.
In this role, Skinner was at the forefront of defending the **DoD Information Network (DoDIN)** against cyber threats. His leadership was crucial in enabling command and control for combat operations, ensuring that the U.S. military could operate effectively in an era where cyber warfare is as critical as traditional battlefield tactics. Under his command, DISA underwent significant restructuring to enhance network protection, aligning with the broader trends in cyber resilience and digital transformation within the DoD.
Awards and Accolades: Recognition of Excellence
Skinner’s contributions to the U.S. military have not gone unnoticed. His decorated career includes prestigious awards such as the **Master Cyberspace Operator Badge**, a symbol of his expertise in cyber operations. He has also been awarded the **Armed Forces Expeditionary Medal**, the **Iraq Campaign Medal**, and the **Nuclear Deterrence Operations Service Medal**, each reflecting his diverse contributions to global operations, combat missions, and national security.
One of the most notable recognitions of his impact is his **three-time Wash100 Award**, an honor that highlights his influence in the federal IT and cybersecurity sectors. This award is a testament to his ability to drive innovation and lead transformative initiatives in an ever-changing digital landscape.
Transition to the Private Sector: A New Chapter
After retiring from the military in 2024, Skinner did not step away from the world of cybersecurity and IT modernization. Instead, he transitioned to the private sector, bringing his wealth of experience to **Axonius Federal Systems**. Joining the company’s board, Skinner is now focused on expanding Axonius’ presence within the federal government. His role is pivotal in helping the company meet the growing demands for network visibility and threat defense in an era where cyber threats are becoming increasingly sophisticated.
Skinner’s move to Axonius is a strategic one. The company specializes in cybersecurity asset management, providing organizations with the tools they need to gain visibility into their digital environments. With Skinner’s expertise, Axonius is well-positioned to support federal agencies in their efforts to modernize IT infrastructures and defend against cyber threats.
The Legacy of a Cyber Pioneer
Robert J. Skinner’s career is a blueprint for leadership in the digital age. From his early days as a second lieutenant to his role as a three-star general commanding global cyber operations, Skinner has consistently demonstrated an ability to adapt, innovate, and lead. His contributions to the U.S. military have not only strengthened national security but have also set a standard for how cyber operations should be integrated into modern defense strategies.
As he continues his work in the private sector, Skinner’s influence is far from over. His insights and leadership will undoubtedly shape the future of cybersecurity, ensuring that both government and private entities are equipped to face the challenges of an increasingly digital world.
Stay Tuned for More
This is just the beginning of Robert J. Skinner’s story. In the next part of this article, we’ll delve deeper into his strategic initiatives at DISA, his vision for the future of cybersecurity, and the lessons that young leaders can learn from his remarkable career. Stay tuned for an in-depth exploration of how Skinner’s leadership continues to impact the world of cyber defense.
Strategic Initiatives and Transformational Leadership at DISA
A Vision for Modernization
When Robert J. Skinner took the helm of the **Defense Information Systems Agency (DISA)** in 2021, he inherited an organization at the crossroads of a digital revolution. The DoD’s IT infrastructure, while robust, was facing unprecedented challenges—ranging from escalating cyber threats to the need for rapid digital transformation. Skinner’s leadership was defined by a clear vision: to modernize the DoD’s global IT network while ensuring it remained secure, resilient, and capable of supporting combat operations in real time.
One of Skinner’s first major initiatives was to **restructure DISA’s operations** to enhance network protection. This wasn’t just about bolting on new cybersecurity tools; it was about fundamentally rethinking how the DoD approached digital defense. Under his command, DISA adopted a **zero-trust architecture**, a model that assumes no user or system is inherently trustworthy, regardless of whether they are inside or outside the network perimeter. This shift was critical in an era where insider threats and sophisticated cyber-attacks from nation-state actors were becoming the norm.
Skinner also championed the **adoption of cloud-based solutions** across the DoD. Recognizing that legacy systems were no longer sufficient to meet the demands of modern warfare, he pushed for the integration of commercial cloud technologies. This move not only improved the scalability and flexibility of the DoD’s IT infrastructure but also enabled faster deployment of critical applications and services to troops in the field. His efforts aligned with the broader **DoD Cloud Strategy**, which aims to leverage cloud computing to enhance mission effectiveness and operational efficiency.
Defending the DoD Information Network (DoDIN)
The **DoD Information Network (DoDIN)** is the backbone of the U.S. military’s global operations. It connects commanders, troops, and assets across the world, enabling real-time communication, intelligence sharing, and command and control. Protecting this network from cyber threats was one of Skinner’s top priorities, and his approach was both proactive and adaptive.
Under Skinner’s leadership, DISA implemented **advanced threat detection and response capabilities**. This included the deployment of **artificial intelligence (AI) and machine learning (ML) tools** to identify and neutralize cyber threats before they could cause significant damage. These technologies allowed DISA to analyze vast amounts of data in real time, detecting anomalies that might indicate a cyber-attack. By automating threat detection, Skinner’s team could respond to incidents faster and more effectively, reducing the window of vulnerability.
Skinner also recognized the importance of **cyber hygiene**—the practice of maintaining basic security measures to prevent attacks. He launched initiatives to ensure that all personnel within the DoD adhered to best practices, such as regular software updates, strong password policies, and multi-factor authentication. While these measures might seem basic, they are often the first line of defense against cyber threats. By fostering a culture of cyber awareness, Skinner helped to minimize the risk of human error, which is a leading cause of security breaches.
Global Operations and the Human Element
One of the most impressive aspects of Skinner’s tenure at DISA was his ability to lead a **global workforce of approximately 19,000 personnel** spread across **42 countries**. Managing such a vast and diverse team required not only technical expertise but also exceptional leadership and communication skills. Skinner’s approach was rooted in **empowerment and collaboration**. He believed in giving his teams the tools, training, and autonomy they needed to succeed, while also fostering a sense of unity and shared purpose.
Skinner’s leadership style was particularly evident in his handling of **crisis situations**. Whether responding to a cyber-attack or ensuring uninterrupted communication during a military operation, he remained calm, decisive, and focused. His ability to maintain clarity under pressure was a key factor in DISA’s success during his tenure. He also placed a strong emphasis on **continuous learning and development**, ensuring that his teams were always equipped with the latest skills and knowledge to tackle emerging threats.
Bridging the Gap Between Military and Industry
Throughout his career, Skinner has been a strong advocate for **public-private partnerships**. He understands that the challenges of cybersecurity and IT modernization are too complex for any single entity to solve alone. By collaborating with industry leaders, the DoD can leverage cutting-edge technologies and best practices to stay ahead of adversaries.
During his time at DISA, Skinner worked closely with **tech giants, cybersecurity firms, and startups** to integrate innovative solutions into the DoD’s IT infrastructure. This included partnerships with companies specializing in **AI, cloud computing, and cybersecurity**, all of which played a crucial role in modernizing the DoD’s digital capabilities. Skinner’s ability to bridge the gap between the military and the private sector has been a defining feature of his career, and it’s a trend he continues to champion in his post-retirement role at Axonius.
The Transition to Axonius: A New Mission in the Private Sector
Why Axonius?
After retiring from the military in 2024, Skinner could have chosen any number of paths. However, his decision to join **Axonius Federal Systems** was a strategic one. Axonius is a leader in **cybersecurity asset management**, providing organizations with the visibility they need to understand and secure their digital environments. For Skinner, this was a natural fit. His decades of experience in cyber operations and IT modernization made him uniquely qualified to help Axonius expand its footprint within the federal government.
Axonius’ platform is designed to give organizations a **comprehensive view of all their assets**, including devices, users, and applications. This visibility is critical for identifying vulnerabilities, detecting threats, and ensuring compliance with security policies. In the federal sector, where cyber threats are a constant concern, Axonius’ solutions are in high demand. Skinner’s role on the board is to help the company navigate the complexities of the federal market, ensuring that its technologies are tailored to meet the unique needs of government agencies.
Expanding Federal Presence
Skinner’s appointment to the Axonius Federal Systems board is more than just a ceremonial role. He is actively involved in shaping the company’s strategy for engaging with federal clients. His deep understanding of the **DoD’s cybersecurity challenges** and his extensive network within the government make him an invaluable asset to Axonius.
One of Skinner’s key priorities is to **educate federal agencies** on the importance of asset visibility. Many organizations struggle with **shadow IT**—the use of unauthorized devices and applications that can introduce significant security risks. Axonius’ platform helps agencies identify and manage these hidden assets, reducing the attack surface and improving overall security posture. Skinner’s mission is to ensure that federal leaders understand the value of this approach and adopt it as part of their broader cybersecurity strategy.
A Focus on Cyber Resilience
In his new role, Skinner is also advocating for a **shift in how the federal government approaches cybersecurity**. Rather than simply reacting to threats, he believes agencies should focus on **building cyber resilience**—the ability to withstand, respond to, and recover from cyber-attacks. This requires a combination of **advanced technologies, robust policies, and a skilled workforce**.
Skinner’s vision aligns with the broader trends in federal cybersecurity. The **U.S. Cybersecurity and Infrastructure Security Agency (CISA)** has been pushing for a **zero-trust architecture** and **continuous monitoring** as part of its efforts to modernize federal IT systems. Axonius’ platform is a key enabler of these initiatives, providing the visibility and control needed to implement zero-trust principles effectively.
Lessons in Leadership: What Young Professionals Can Learn from Skinner
Adaptability in a Rapidly Changing Landscape
One of the most important lessons from Skinner’s career is the value of **adaptability**. The field of cybersecurity is constantly evolving, with new threats and technologies emerging at a rapid pace. Skinner’s ability to stay ahead of these changes—whether by adopting cloud computing, AI, or zero-trust architectures—has been a key factor in his success.
For young professionals entering the cybersecurity field, adaptability is non-negotiable. The skills and tools that are relevant today may be obsolete in a few years. Skinner’s career is a reminder that **continuous learning** is essential. Whether through formal education, certifications, or hands-on experience, staying updated with the latest trends is critical for long-term success.
The Importance of Collaboration
Another key takeaway from Skinner’s leadership is the power of **collaboration**. Cybersecurity is not a solo endeavor; it requires teamwork, both within organizations and across industries. Skinner’s ability to bring together military personnel, government agencies, and private-sector partners has been instrumental in his achievements.
Young professionals should seek out opportunities to **build networks** and **foster partnerships**. Whether it’s working with colleagues from different departments, engaging with industry experts, or participating in professional organizations, collaboration can open doors to new ideas and solutions. Skinner’s career demonstrates that the best outcomes often come from **diverse perspectives working toward a common goal**.
Leading with Integrity and Purpose
Finally, Skinner’s career is a testament to the importance of **leading with integrity and purpose**. Throughout his three decades of service, he has remained committed to the mission of protecting national security and enabling the success of the U.S. military. His leadership was never about personal glory but about **serving something greater than himself**.
For young leaders, this is a powerful lesson. True leadership is not about titles or authority; it’s about **making a positive impact** and **inspiring others to do the same**. Whether in the military, the private sector, or any other field, leading with integrity and purpose will always set you apart.
Looking Ahead: The Future of Cybersecurity and Skinner’s Continued Influence
As we look to the future, it’s clear that Robert J. Skinner’s influence on cybersecurity is far from over. His work at Axonius is just the latest chapter in a career defined by innovation, leadership, and a relentless commitment to excellence. The challenges of cybersecurity will only grow more complex, but with leaders like Skinner at the helm, the U.S. is well-positioned to meet them head-on.
In the final part of this article, we’ll explore Skinner’s vision for the future of cybersecurity, the emerging threats that keep him up at night, and the advice he has for the next generation of cyber leaders. Stay tuned for an in-depth look at how Skinner’s legacy continues to shape the digital battlefield.
The Future of Cybersecurity: Skinner’s Vision and Emerging Threats
A Shifting Cyber Landscape
The cybersecurity landscape is evolving at an unprecedented pace, and Robert J. Skinner is keenly aware of the challenges that lie ahead. In his view, the future of cybersecurity will be shaped by **three major trends* the rise of **quantum computing**, the increasing sophistication of **nation-state cyber threats**, and the growing importance of **AI-driven defense mechanisms**.
Skinner has often spoken about the potential impact of **quantum computing** on cybersecurity. While quantum computers hold the promise of revolutionary advancements in fields like medicine and logistics, they also pose a significant threat to current encryption standards. "The day quantum computers can break traditional encryption is not a question of *if* but *when*," Skinner has noted. His work at Axonius and his engagements with federal agencies emphasize the need for **post-quantum cryptography**—a new generation of encryption algorithms designed to resist attacks from quantum computers. For Skinner, preparing for this shift is not just a technical challenge but a strategic imperative.
Nation-State Threats and the New Battlefield
The threat posed by **nation-state actors** is another area of deep concern for Skinner. Over his career, he witnessed firsthand how cyber warfare has become a central component of geopolitical strategy. Countries like **Russia, China, Iran, and North Korea** have developed sophisticated cyber capabilities, using them to conduct espionage, disrupt critical infrastructure, and influence global events.
Skinner’s time at **U.S. Indo-Pacific Command** gave him a front-row seat to the cyber operations of adversarial nations. He has repeatedly stressed that cyber threats are no longer confined to the digital realm—they have **real-world consequences**. A cyber-attack on a power grid, for instance, can plunge entire cities into darkness, while an attack on financial systems can destabilize economies. His approach to countering these threats involves a combination of **proactive defense, international cooperation, and robust deterrence strategies**.
At Axonius, Skinner is advocating for **greater visibility and control** over federal networks to detect and mitigate these threats. "You can’t defend what you can’t see," he often says. By providing agencies with a comprehensive view of their digital assets, Axonius’ platform helps identify vulnerabilities before they can be exploited by adversaries.
AI and Automation: The Double-Edged Sword
Artificial intelligence is another double-edged sword in the cybersecurity arsenal. On one hand, **AI-driven tools** can enhance threat detection, automate responses, and analyze vast amounts of data in real time. On the other hand, adversaries are also leveraging AI to develop more sophisticated attacks, such as **deepfake phishing scams** and **automated hacking tools**.
Skinner believes that the future of cybersecurity will be defined by an **AI arms race**. "The side that can harness AI most effectively will have the upper hand," he has remarked. During his tenure at DISA, he championed the integration of AI into the DoD’s cyber defense strategies. Now, at Axonius, he is working to ensure that federal agencies have the tools they need to stay ahead in this race.
One of the key challenges is **balancing automation with human oversight**. While AI can process data faster than any human, it lacks the nuanced understanding and judgment that experienced cybersecurity professionals bring to the table. Skinner’s approach is to use AI as a **force multiplier**—augmenting human capabilities rather than replacing them. This means training the next generation of cyber defenders to work alongside AI tools, leveraging their strengths while mitigating their limitations.
Skinner’s Advice for the Next Generation of Cyber Leaders
Embrace Lifelong Learning
For young professionals entering the field of cybersecurity, Skinner’s first piece of advice is to **embrace lifelong learning**. "The moment you think you know everything is the moment you become obsolete," he warns. The cybersecurity landscape is constantly evolving, and staying relevant requires a commitment to continuous education.
Skinner recommends that young professionals **pursue certifications** in areas like **ethical hacking, cloud security, and AI-driven cyber defense**. He also encourages them to stay engaged with industry trends by attending conferences, participating in **capture-the-flag (CTF) competitions**, and joining professional organizations like **ISC²** and **ISACA**. "The best cybersecurity professionals are those who never stop learning," he says.
Develop Soft Skills Alongside Technical Expertise
While technical skills are essential, Skinner emphasizes that **soft skills** are equally important. "Cybersecurity is not just about writing code or configuring firewalls—it’s about communication, collaboration, and leadership," he explains. Effective cybersecurity professionals must be able to **articulate risks to non-technical stakeholders**, work in cross-functional teams, and lead initiatives that require buy-in from across an organization.
Skinner’s own career is a testament to the power of soft skills. His ability to **bridge the gap between military and civilian sectors**, as well as between government and industry, has been a key factor in his success. He advises young professionals to **hone their communication skills**, learn to **manage teams effectively**, and develop a **strategic mindset** that aligns cybersecurity with broader organizational goals.
Think Like an Adversary
One of the most valuable lessons Skinner has learned over his career is the importance of **thinking like an adversary**. "To defend a network, you have to understand how an attacker would try to breach it," he says. This mindset is at the core of **red teaming**—a practice where cybersecurity professionals simulate attacks to identify vulnerabilities.
Skinner encourages young cyber defenders to **adopt an offensive mindset**. This means staying updated on the latest **hacking techniques**, understanding the **tactics, techniques, and procedures (TTPs)** used by adversaries, and constantly challenging their own assumptions about security. "The best defense is a proactive one," he notes. By anticipating how attackers might exploit weaknesses, cybersecurity teams can stay one step ahead.
Build a Strong Professional Network
Networking is another area where Skinner sees tremendous value. "Cybersecurity is a team sport," he often says. Building relationships with peers, mentors, and industry leaders can open doors to new opportunities, provide access to valuable resources, and offer support during challenging times.
Skinner’s own network has been instrumental in his career. From his early days in the Air Force to his current role at Axonius, he has relied on **mentors, colleagues, and industry partners** to navigate complex challenges. He advises young professionals to **attend industry events**, join online communities, and seek out mentorship opportunities. "The relationships you build today will shape your career tomorrow," he emphasizes.
The Legacy of a Cyber Pioneer
A Career Defined by Service and Innovation
Robert J. Skinner’s career is a remarkable journey of **service, leadership, and innovation**. From his early days as a second lieutenant to his role as a three-star general commanding global cyber operations, he has consistently pushed the boundaries of what is possible in cybersecurity. His contributions to the U.S. military have not only strengthened national security but have also set a standard for how cyber operations should be integrated into modern defense strategies.
Skinner’s impact extends beyond his military service. His transition to the private sector at Axonius is a testament to his commitment to **continuing the fight against cyber threats**, this time from a different vantage point. By leveraging his expertise to help federal agencies modernize their IT infrastructures, he is ensuring that the lessons he learned in the military continue to benefit the nation.
A Vision for the Future
Looking ahead, Skinner’s vision for the future of cybersecurity is one of **resilience, adaptability, and collaboration**. He believes that the challenges of tomorrow will require a **unified approach**, bringing together government, industry, and academia to develop innovative solutions. His work at Axonius is just one example of how public-private partnerships can drive progress in cybersecurity.
Skinner is also a strong advocate for **investing in the next generation of cyber leaders**. He believes that the future of cybersecurity depends on **mentorship, education, and opportunity**. By sharing his knowledge and experience, he is helping to shape a new generation of professionals who are equipped to tackle the challenges of an increasingly digital world.
Final Thoughts: The Man Behind the Uniform
Beyond the titles, awards, and accolades, Robert J. Skinner is a leader who has always put **mission and people first**. His career is a reminder that true leadership is not about personal achievement but about **serving others and making a difference**. Whether in the military or the private sector, Skinner’s dedication to protecting national security and advancing cybersecurity has left an indelible mark.
As we reflect on his career, one thing is clear: Robert J. Skinner’s influence on cybersecurity will be felt for decades to come. His story is not just one of **technical expertise** but of **vision, perseverance, and an unwavering commitment to excellence**. For young professionals entering the field, his journey serves as both an inspiration and a roadmap for success.
The End of an Era, the Beginning of a New Chapter
Robert J. Skinner’s retirement from the military may have marked the end of one chapter, but his work is far from over. As he continues to shape the future of cybersecurity at Axonius and beyond, his legacy serves as a guiding light for those who follow in his footsteps. The digital battlefield is evolving, but with leaders like Skinner at the helm, the future of cybersecurity is in capable hands.
For those who aspire to make their mark in this critical field, Skinner’s career offers a powerful lesson: **success is not just about technical skills or strategic vision—it’s about leadership, adaptability, and an unyielding commitment to the mission**. As the cyber landscape continues to change, the principles that have guided Skinner’s career will remain as relevant as ever.
In the words of Skinner himself: *"Cybersecurity is not just a job—it’s a calling. And it’s a calling that requires us to be at our best, every single day."* For Robert J. Skinner, that calling is far from over. And for the rest of us, his journey is a reminder of the impact one leader can have on the world.


Quantum Cryptography: The Future of Secure Communication
Introduction to Quantum Cryptography
In an era where cybersecurity threats are becoming increasingly sophisticated, the demand for unbreakable encryption has never been greater. Traditional cryptographic methods, while effective, are vulnerable to advancements in computing power and clever hacking techniques. Enter quantum cryptography—a revolutionary approach to secure communication that leverages the principles of quantum mechanics to ensure unparalleled security. Unlike classical encryption, which relies on mathematical complexity, quantum cryptography is built on the inherent uncertainty and fundamental laws of physics, making it theoretically immune to hacking attempts.
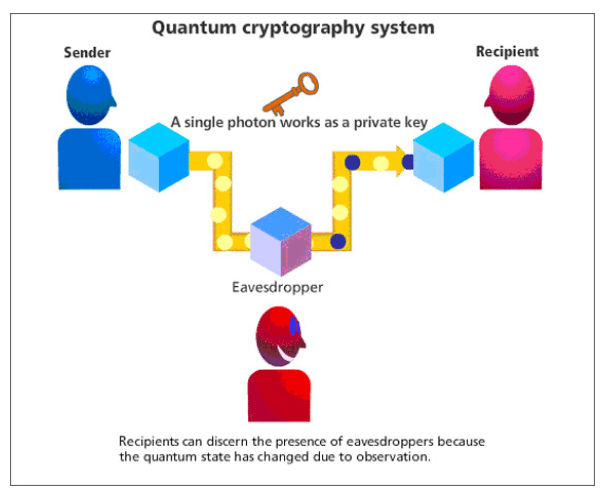
The foundation of quantum cryptography lies in quantum key distribution (QKD), a method that allows two parties to generate a shared secret key that can be used to encrypt and decrypt messages. What makes QKD unique is its reliance on the behavior of quantum particles, such as photons, which cannot be measured or copied without disturbing their state. This means any attempt to eavesdrop on the communication will inevitably leave traces, alerting the legitimate parties to the intrusion.
The Principles Behind Quantum Cryptography
At the heart of quantum cryptography are two key principles of quantum mechanics: the Heisenberg Uncertainty Principle and quantum entanglement.
Heisenberg Uncertainty Principle
The Heisenberg Uncertainty Principle states that it is impossible to simultaneously know both the position and momentum of a quantum particle with absolute precision. In the context of quantum cryptography, this principle ensures that any attempt to measure a quantum system (such as a photon used in QKD) will inevitably alter its state. Suppose an eavesdropper tries to intercept the quantum key during transmission. In that case, their measurement will introduce detectable disturbances, revealing their presence and preserving the key's secrecy.
Quantum Entanglement
Quantum entanglement is a phenomenon where two or more particles become linked in such a way that the state of one particle immediately influences the state of the other, regardless of the distance separating them. This property allows for the creation of highly secure cryptographic systems. For example, if entangled photons are used in QKD, any attempt to intercept one photon will disrupt the entanglement, providing a clear indication of tampering.
How Quantum Key Distribution (QKD) Works
QKD is the cornerstone of quantum cryptography and involves the exchange of cryptographic keys between two parties—traditionally referred to as Alice (the sender) and Bob (the receiver)—using quantum communication channels. Here's a simplified breakdown of the process:
Step 1: Transmission of Quantum States
Alice begins by generating a sequence of photons, each in a random quantum state (polarization or phase). She sends these photons to Bob over a quantum channel, such as an optical fiber or even through free space.
Step 2: Measurement of Quantum States
Upon receiving the photons, Bob measures each one using a randomly chosen basis (e.g., rectilinear or diagonal for polarization-based systems). Due to the probabilistic nature of quantum mechanics, Bob’s measurements will only be accurate if he chooses the same basis as Alice did when preparing the photon.
Step 3: Sifting and Key Formation
After the transmission, Alice and Bob publicly compare their choice of measurement bases (but not the actual results). They discard any instances where Bob measured the photon in the wrong basis, retaining only the cases where their bases matched. These remaining results form the raw key.
Step 4: Error Checking and Privacy Amplification
To ensure the key's integrity, Alice and Bob perform error checking by comparing a subset of their raw key. If discrepancies exceed a certain threshold, it indicates potential eavesdropping, and the key is discarded. If no significant errors are found, they apply privacy amplification techniques to distill a final, secure key.
Advantages of Quantum Cryptography
Quantum cryptography offers several compelling advantages over traditional encryption methods:
Unconditional Security
Unlike classical encryption, which depends on computational hardness assumptions (e.g., factoring large primes), quantum cryptography provides security based on the laws of physics. This means it remains secure even against adversaries with unlimited computational power.
Detection of Eavesdropping
Any attempt to intercept quantum-encoded information will disturb the system, making it immediately detectable. This feature ensures that compromised communications can be identified and discarded before sensitive data is exposed.
Future-Proof Against Quantum Computers
With the advent of quantum computers, classical cryptographic algorithms like RSA and ECC are at risk of being broken. Quantum cryptography, particularly QKD, remains resistant to such threats, making it a future-proof solution.
Current Applications and Challenges
While quantum cryptography holds immense promise, its practical implementation faces several hurdles. Currently, QKD is being used in limited scenarios, such as securing government communications and financial transactions. However, challenges like high implementation costs, limited transmission distances, and the need for specialized infrastructure hinder widespread adoption.
Despite these obstacles, research and development in quantum cryptography are advancing rapidly. Innovations in satellite-based QKD and integrated photonics are paving the way for more accessible and scalable solutions. As the technology matures, quantum cryptography could become a standard for securing critical communications in the near future.
Stay tuned for the next part of this article, where we will delve deeper into real-world implementations of quantum cryptography, its limitations, and the ongoing advancements in this groundbreaking field.
Real-World Implementations of Quantum Cryptography
The theoretical promise of quantum cryptography has begun translating into practical applications, albeit in niche and high-security environments. Governments, financial institutions, and research organizations are leading the charge in deploying quantum-secure communication networks, recognizing the urgent need for protection against both current and future cyber threats.
Government and Military Use Cases
National security agencies were among the first to recognize the potential of quantum cryptography. Countries like China, the United States, and Switzerland have implemented QKD-based secure communication networks to safeguard sensitive governmental and military data. In 2017, China’s Quantum Experiments at Space Scale (QUESS) satellite, also known as Micius, successfully demonstrated intercontinental QKD between Beijing and Vienna, marking a milestone in global quantum-secured communication.
Similarly, the U.S. government has invested in quantum-resistant encryption initiatives through collaborations involving the National Institute of Standards and Technology (NIST) and Defense Advanced Research Projects Agency (DARPA). These efforts aim to transition classified communications to quantum-safe protocols before large-scale quantum computers become a reality.
Financial Sector Adoption
Banks and financial enterprises handle vast amounts of sensitive data daily, making them prime targets for cyberattacks. Forward-thinking institutions like JPMorgan Chase and the European Central Bank have begun experimenting with QKD to protect high-frequency trading systems, interbank communications, and customer transactions.
In 2020, the Tokyo Quantum Secure Communication Network, a collaboration between Toshiba and major Japanese financial firms, established a quantum-secured link between data centers, ensuring tamper-proof financial transactions. Such implementations underscore the growing confidence in quantum cryptography as a viable defense against economic espionage and fraud.
Technical Limitations and Challenges
Despite its groundbreaking advantages, quantum cryptography is not without hurdles. Researchers and engineers must overcome several technical barriers before QKD can achieve mainstream adoption.
Distance Constraints
One of the biggest challenges in QKD is signal loss over long distances. Photons used in quantum communication degrade when traveling through optical fibers or free space, limiting the effective range of current systems. While terrestrial QKD networks rarely exceed 300 kilometers, researchers are exploring quantum repeaters and satellite relays to extend reach. China’s Micius satellite has achieved intercontinental key distribution, but ground-based infrastructure remains constrained by physical losses.
Key Rate Limitations
Quantum key distribution is also bottlenecked by the speed at which secure keys can be generated. Traditional QKD systems produce keys at rates of a few kilobits per second—sufficient for encrypting voice calls or small data packets but impractical for high-bandwidth applications like video streaming. Advances in superconducting detectors and high-speed modulators aim to improve key rates, but further innovation is needed to match classical encryption speeds.
Cost and Infrastructure
The specialized hardware required for QKD—such as single-photon detectors, quantum light sources, and ultra-low-noise optical fibers—makes deployment expensive. For instance, commercial QKD systems can cost hundreds of thousands of dollars, putting them out of reach for most enterprises. Additionally, integrating quantum-secured links into existing telecommunication networks demands significant infrastructure upgrades, further complicating widespread adoption.
The Quantum vs. Post-Quantum Debate
Quantum cryptography often overlaps with discussions about post-quantum cryptography (PQC), leading to some confusion. While both address quantum threats, their approaches differ fundamentally.
QKD vs. Post-Quantum Algorithms
Quantum key distribution relies on the principles of quantum mechanics to secure communications inherently, whereas post-quantum cryptography involves developing new mathematical algorithms resistant to attacks from quantum computers. PQC solutions, currently being standardized by NIST, aim to replace vulnerable classical algorithms without requiring quantum hardware. However, QKD offers a unique advantage: information-theoretic security, meaning its safety doesn’t depend on unproven mathematical assumptions.
Hybrid Solutions Emerging
Recognizing the complementary strengths of both approaches, organizations are increasingly adopting hybrid systems combining QKD with post-quantum algorithms. This dual-layer encryption strategy ensures resilience even if one layer is compromised, providing a balanced transition path toward a quantum-safe future.
Breakthroughs in Quantum Networking
The push toward a quantum internet—a global network interconnected via quantum entanglement—has accelerated breakthroughs in quantum repeaters, memory storage, and entanglement swapping. These innovations address critical challenges in scaling quantum cryptography beyond point-to-point links.
Quantum Repeaters
Traditional signal amplifiers cannot be used in quantum communications without destroying the quantum states of photons. Quantum repeaters, still in experimental stages, aim to overcome this by leveraging entanglement swapping to extend the reach of QKD without measurement. Companies like Quantum Xchange in the U.S. and ID Quantique in Switzerland are pioneering modular repeater technologies to enable continental-scale quantum networks.
Quantum Memory
Storing quantum information is essential for synchronizing transmissions in large networks. Recent advances in atomic ensembles and rare-earth-doped crystals have demonstrated millisecond-long quantum memory retention—a critical step toward buffering entangled光子 for on-demand retrieval in complex networks.
Commercial and Open-Source Initiatives
The quantum cryptography market is witnessing a surge in private-sector involvement, with startups and tech giants alike racing to commercialize the technology.
Industry Leaders and Innovators
Companies like Toshiba, IBM, and QuintessenceLabs are offering enterprise-grade QKD solutions tailored for specific industries. Meanwhile, open-source projects such as the OpenQKD initiative by the European Union are fostering collaboration between academia and industry to standardize protocols and drive down costs.
Cloud-Based Quantum Security
Cloud providers are exploring quantum-secure services, such as AWS’s hybrid post-quantum TLS and Azure’s Quantum Network, allowing businesses to test quantum-resistant encryption without major infrastructure investments. These platforms serve as bridges for organizations transitioning toward full quantum readiness.
Looking Ahead
Quantum cryptography is transitioning from lab experiments to real-world deployments, but obstacles remain. The next decade will likely see breakthroughs in scalable QKD, affordable quantum hardware, and international standards—key enablers for a quantum-secured global infrastructure. In the final part of this series, we will explore speculative future applications, ethical considerations, and the role of policy in shaping quantum security’s trajectory.
Stay tuned for the concluding installment, where we examine how quantum cryptography could redefine privacy, governance, and trust in the digital age.
The Future of Quantum Cryptography: Ethical and Societal Implications
As quantum cryptography moves from theoretical research to practical implementation, it raises profound questions about its impact on society, governance, and individual privacy. The technology’s potential to revolutionize secure communication is undeniable, but it also introduces new challenges that must be addressed to ensure responsible adoption.
Privacy in the Quantum Era
Quantum cryptography promises unbreakable encryption, but it also poses ethical dilemmas. Governments and corporations could use quantum-secure networks to protect sensitive data, but the same technology might enable mass surveillance if misused. The balance between security and privacy will be a critical issue as quantum encryption becomes mainstream. Policymakers must establish clear regulations to prevent abuse while fostering innovation.
Global Security and Cyber Warfare
The advent of quantum computing and cryptography could shift the balance of power in cyber warfare. Nations with advanced quantum capabilities may gain an advantage in intelligence gathering and secure communications, potentially destabilizing international relations. The risk of a "quantum arms race" is real, with countries competing to develop quantum-resistant encryption and decryption tools. International cooperation will be essential to prevent an escalation of cyber conflicts.
Accessibility and Digital Divide
Quantum cryptography is currently expensive and complex, limiting its availability to wealthy nations and large corporations. If left unchecked, this could exacerbate the digital divide, leaving smaller businesses and developing nations vulnerable to cyberattacks. Efforts to democratize quantum-secure technologies—through open-source projects, subsidies, or international partnerships—will be crucial to ensuring equitable access.
Quantum Cryptography and Artificial Intelligence
The intersection of quantum computing and artificial intelligence (AI) presents both opportunities and risks. Quantum algorithms could enhance AI’s ability to analyze encrypted data, potentially breaking classical encryption methods. Conversely, AI could be used to optimize quantum cryptographic protocols, making them more efficient and secure. The synergy between these two fields will shape the future of cybersecurity.
AI-Powered Quantum Attacks
AI-driven cyberattacks are already a growing threat, and quantum computing could amplify their effectiveness. Machine learning models trained on quantum algorithms might identify vulnerabilities in classical encryption faster than human hackers. Defending against such threats will require AI-powered quantum defenses, creating a continuous arms race between attackers and defenders.
Quantum Machine Learning for Security
On the defensive side, quantum machine learning could revolutionize threat detection. Quantum-enhanced AI models could analyze vast datasets in real time, identifying anomalies and potential breaches with unprecedented accuracy. This could lead to proactive cybersecurity measures, where threats are neutralized before they cause harm.
The Role of Policy and Regulation
Governments and international organizations must play a proactive role in shaping the future of quantum cryptography. Without proper oversight, the technology could be weaponized or monopolized, leading to unintended consequences.
Standardization and Certification
Establishing global standards for quantum encryption is essential to ensure interoperability and security. Organizations like NIST and the International Telecommunication Union (ITU) are already working on post-quantum cryptographic standards, but more collaboration is needed to address emerging quantum threats. Certification programs for quantum-secure products will also be necessary to build trust among users.
Ethical Guidelines for Quantum Research
As quantum technology advances, ethical guidelines must be developed to govern its use. Researchers and policymakers should collaborate to address concerns such as data sovereignty, surveillance, and the militarization of quantum encryption. Transparency and public discourse will be key to ensuring that quantum cryptography benefits society as a whole.
Speculative Applications of Quantum Cryptography
Beyond cybersecurity, quantum cryptography could enable groundbreaking applications in various fields, from healthcare to space exploration.
Quantum-Secure Medical Data
Healthcare systems handle vast amounts of sensitive patient data, making them prime targets for cyberattacks. Quantum-secure encryption could protect medical records, ensuring patient confidentiality while enabling secure sharing of research data. This could accelerate medical breakthroughs while safeguarding privacy.
Interplanetary Communication
As humanity expands into space, secure communication between Earth and distant colonies or spacecraft will be critical. Quantum cryptography could enable unhackable communication links across vast distances, ensuring the integrity of mission-critical data. NASA and other space agencies are already exploring quantum communication for future Mars missions.
Quantum Voting Systems
Election security is a growing concern worldwide. Quantum-secure voting systems could prevent tampering and ensure the integrity of democratic processes. By leveraging quantum encryption, governments could create verifiable and tamper-proof digital voting mechanisms, restoring public trust in elections.
Conclusion: The Quantum Security Revolution
Quantum cryptography is poised to redefine the future of secure communication, offering unparalleled protection against cyber threats. However, its widespread adoption will require overcoming technical, ethical, and regulatory challenges. As we stand on the brink of a quantum revolution, collaboration between scientists, policymakers, and industry leaders will be essential to harness the technology’s potential while mitigating its risks.
The next decade will be pivotal in determining how quantum cryptography shapes our digital world. By addressing accessibility, ethical concerns, and global cooperation, we can ensure that this revolutionary technology serves as a force for good, safeguarding privacy and security in an increasingly connected world.
As quantum cryptography evolves, one thing is certain: the future of cybersecurity will be quantum, and the time to prepare is now.

Alexis Alford: A Young Traveler's Journey to Exploring the World
Introduction
Alexis Alford, also known as Lexie, is a young adventurer who has captured the hearts of many with her passion for travel and exploration. Born in California, Lexie developed a love for discovering new cultures and places at an incredibly young age. By the time she was 21, she had already visited all 196 countries in the world, making her one of the youngest people to achieve this remarkable feat. Her story is not just about ticking off destinations but about embracing diversity, overcoming challenges, and inspiring others to step out of their comfort zones.
Early Life and the Spark of Wanderlust
Lexie’s journey began in a small town in California, where she was raised in a supportive family that encouraged curiosity and learning. Her parents played a significant role in nurturing her love for travel, taking her on trips to different states and countries from a young age. By the time she was 10, Lexie had already visited several countries, including Mexico and Canada. These early experiences ignited a deep passion for exploring the world and understanding different cultures.
Unlike many teenagers who spend their high school years focused on local activities, Lexie was already dreaming of global adventures. She saved money from part-time jobs and researched extensively about different countries, planning her future travels. Her determination was evident even then—she wasn’t just waiting for opportunities; she was actively creating them.
The Decision to Travel the World
At 18, Lexie made a bold decision: she would travel to every country in the world before turning 21. This was no small goal, considering the logistical, financial, and personal challenges it entailed. However, Lexie was undeterred. She understood that this journey would require sacrifices, including postponing traditional college plans and finding unconventional ways to fund her travels.
Lexie’s approach was strategic. She combined personal savings, sponsorships, and freelance work to finance her trips. She also leveraged social media to document her adventures, sharing her experiences with a growing audience. Her authenticity and enthusiasm resonated with people, and soon, she gained a following that supported her mission.
Challenges and Triumphs on the Road
Traveling to every country in the world is no easy feat, and Lexie faced numerous obstacles along the way. From visa issues to language barriers, cultural misunderstandings to health scares, her journey was far from smooth. However, each challenge only strengthened her resolve.
One of the most difficult aspects of her travels was navigating countries with political instability or limited infrastructure. Lexie visited places like Syria, Yemen, and South Sudan, where safety was a constant concern. Yet, she approached these destinations with respect and an open mind, learning invaluable lessons about resilience and humanity.
Another challenge was the emotional toll of constant travel. Being away from family and friends for extended periods was tough, and there were moments when Lexie questioned her decision. However, the connections she made with people around the world kept her going. She often stayed with local families, immersing herself in their way of life and forming bonds that transcended borders.
Cultural Immersion and Personal Growth
For Lexie, travel was never just about collecting passport stamps—it was about understanding the world on a deeper level. She made a conscious effort to immerse herself in local cultures, whether by learning basic phrases in different languages, participating in traditional ceremonies, or trying regional cuisines.
These experiences shaped her worldview in profound ways. Lexie realized that despite cultural differences, people everywhere share common values—kindness, hospitality, and a desire for connection. She also became more adaptable, learning to thrive in unfamiliar environments and embrace uncertainty.
One of her most memorable experiences was in Bhutan, where she trekked through the Himalayas and learned about the country’s philosophy of Gross National Happiness. In Rwanda, she visited gorilla sanctuaries and witnessed the country’s incredible conservation efforts. Each destination left a lasting impression, contributing to her personal and intellectual growth.
Breaking Records and Gaining Recognition
In 2019, at the age of 21, Lexie achieved her goal of visiting all 196 countries. This accomplishment earned her a place in the record books as one of the youngest people to do so. Her story was featured in major media outlets, including Forbes, BBC, and National Geographic.
However, Lexie remained humble about her achievement. She emphasized that her journey was not about breaking records but about inspiring others to pursue their passions, no matter how unconventional they may seem. She encouraged young people, especially women, to embrace adventure and challenge societal expectations.
Life After the Journey
Completing her goal of visiting every country was just the beginning for Lexie. She continued to travel, focusing on deeper explorations of regions she had previously only briefly visited. She also began sharing her knowledge and experiences through public speaking, mentoring aspiring travelers, and collaborating with organizations promoting global citizenship.
Lexie’s story is a testament to the power of determination, curiosity, and an open heart. She proved that age is no barrier to achieving extraordinary dreams and that the world is far more accessible than many believe.
Conclusion
The first part of Lexie’s journey is a remarkable tale of ambition, courage, and cultural discovery. From her early travels with her family to her record-breaking achievement, she has shown that with passion and perseverance, anything is possible. Her story continues to inspire countless individuals to step out of their comfort zones and explore the world with an open mind.
Stay tuned for the second part of this article, where we’ll delve deeper into Lexie’s post-travel endeavors, her impact on the travel community, and her future aspirations.otec.
Lexie’s Impact on the Travel Community
Lexie Alford’s journey has not only been about personal achievement but also about inspiring a new generation of travelers. Through her social media platforms, blog, and public speaking engagements, she has shared invaluable insights into the realities of global travel. Her transparency about the challenges—such as budgeting, safety, and cultural adaptation—has made her a trusted voice in the travel community.
One of the most significant ways Lexie has influenced others is by debunking myths about travel. Many people assume that extensive travel is only for the wealthy or that certain destinations are too dangerous to visit. Lexie’s experiences prove otherwise. She has shown that with careful planning, resourcefulness, and respect for local cultures, anyone can explore the world. Her budget-friendly tips, such as leveraging travel rewards programs and staying with locals through homestays, have empowered many to take their first steps toward international travel.
Lexie also emphasizes the importance of responsible tourism. She advocates for sustainable travel practices, such as reducing plastic use, supporting local economies, and respecting wildlife. Her visits to conservation projects in countries like Rwanda and Costa Rica highlight how travelers can contribute positively to the places they visit.
Overcoming Stereotypes and Breaking Barriers
As a young woman traveling solo to every country, Lexie has faced her share of stereotypes and skepticism. Many questioned her ability to navigate complex destinations or assumed she was merely a privileged tourist. However, Lexie’s approach to travel—immersive, respectful, and deeply educational—silenced critics.
She has spoken openly about the challenges female travelers face, from safety concerns to cultural expectations in conservative regions. By sharing her strategies for staying safe—such as researching local customs, dressing appropriately, and trusting her instincts—Lexie has become a role model for women who aspire to explore the world independently.
Her journey also challenges the notion that travel is a luxury reserved for later in life. Lexie’s story proves that age should not limit one’s ambitions. Whether it’s backpacking through Southeast Asia at 18 or negotiating visas for conflict zones at 20, she has demonstrated that youth can be an asset in travel, offering energy, adaptability, and a fresh perspective.
Lessons from the Road
Lexie’s travels have taught her lessons that extend far beyond geography. One of the most profound realizations she shares is the universality of human kindness. Despite language barriers and cultural differences, she encountered countless strangers who offered help, hospitality, and friendship. From a family in Iran who invited her for dinner to a taxi driver in Nigeria who guided her through the city, these interactions reinforced her belief in the goodness of people.
Another key lesson is the value of discomfort. Lexie often says that growth happens outside one’s comfort zone, and her travels were full of moments that tested her resilience. Whether it was falling ill in a remote village or getting lost in a bustling metropolis, each challenge taught her problem-solving skills and self-reliance.
She also learned the importance of flexibility. Travel rarely goes as planned, and Lexie’s ability to adapt—whether it was changing itineraries due to political unrest or finding last-minute accommodations—was crucial to her success. This mindset is something she encourages in others, both in travel and in life.
Life Beyond the 196-Country Goal
After achieving her record-breaking feat, Lexie didn’t slow down. Instead, she shifted her focus to deeper exploration and advocacy. She revisited countries she had only skimmed during her initial journey, spending weeks or months in places like India, Brazil, and Japan to truly understand their cultures.
She also began collaborating with travel organizations and brands, using her platform to promote meaningful travel experiences. Lexie works with companies that prioritize sustainability and ethical tourism, ensuring her partnerships align with her values. Additionally, she mentors young travelers, offering advice on everything from packing lists to navigating cultural nuances.
Lexie has also ventured into content creation, producing documentaries and writing articles that highlight lesser-known destinations. Her work aims to showcase the diversity of the world and encourage travelers to look beyond tourist hotspots.
Future Aspirations
Looking ahead, Lexie’s ambitions are as bold as ever. She plans to continue exploring, with a focus on regions like Central Asia and the Pacific Islands, where she believes there’s much more to discover. She’s also working on a book that will delve deeper into her journey, offering readers a more intimate look at her experiences and the lessons she’s learned.
Beyond travel, Lexie is passionate about education. She hopes to develop programs that teach young people about global citizenship, encouraging them to think critically about the world and their place in it. Whether through workshops, online courses, or school partnerships, she wants to make travel and cultural exchange more accessible to everyone.
Final Thoughts
Lexie Alford’s story is a powerful reminder that the world is full of possibilities for those willing to pursue them. Her journey from a curious teenager to a globally recognized traveler is a testament to the transformative power of travel. By embracing challenges, fostering connections, and staying true to her values, Lexie has not only achieved an extraordinary goal but also inspired countless others to dream bigger.
As she continues to explore and share her adventures, one thing is clear: Lexie’s impact on the travel world is just beginning. Her story encourages us all to step outside our comfort zones, embrace the unknown, and discover the beauty of our diverse planet.
Stay tuned for the third and final part of this article, where we’ll explore Lexie’s most transformative travel moments, her advice for aspiring adventurers, and her vision for the future of travel.
Transformative Travel Moments That Shaped Lexie's Perspective
Among the hundreds of destinations Alexis Alford visited, certain experiences stood out as genuinely life-changing. One such moment occurred in Varanasi, India, where she witnessed the spiritual intensity of the Ganges River at dawn. "Seeing thousands of pilgrims bathing in sacred waters while funeral pyres burned nearby was humbling," she recalls. "It taught me how differently cultures approach life, death, and spirituality."
Her time with the Maasai community in Kenya proved equally profound. Living with a tribal family for two weeks, she participated in their daily routines - herding cattle, fetching water, and learning ancient survival skills. "They had so little materially, yet their community bonds were stronger than anything I'd seen in developed nations," Lexie reflects. This experience fundamentally altered her understanding of wealth and happiness.
Perhaps her most challenging moment came in Venezuela during the country's political crisis. Trapped in Caracas amid protests with dwindling cash (ATMs weren't functioning), Lexie had to rely on the kindness of locals who sheltered her and helped her escape to Colombia. "That experience stripped away any remaining naive ideas I had about travel," she admits. "But it also showed me humanity's incredible capacity for compassion in crisis."
Lexie's Top Advice for Aspiring World Travelers
Drawing from her unparalleled experience, Lexie has developed key principles for meaningful travel:
1. **Start Before You're "Ready"**
"The perfect time, budget, or itinerary doesn't exist. I visited my first solo destination with $500 and a vague plan. You learn by doing."
2. **Embrace Discomfort**
"Real growth happens when things go 'wrong.' Missed buses, language mishaps, and cultural faux pas make the best stories and lessons."
3. **Travel Slowly When Possible**
"After my 196-country sprint, I realized depth matters more than stamps. Spend a month in one country rather than a week in four."
4. **Let Locals Guide You**
"My best meals weren't in guidebook restaurants, but in homes where grandmothers taught me family recipes. Always say yes to local invitations."
5. **Document Thoughtfully**
"Balance capturing memories with being present. I designate camera-free days to fully immerse myself."
The Unexpected Challenges of Life After 196 Countries
Adjusting to stability after years of constant movement presented unique difficulties Lexie hadn't anticipated. "Reverse culture shock hit hard," she explains. "Simple things like grocery shopping felt overwhelming with so many choices. I'd gotten used to markets with just a few options."
She also struggled with the interrogative "What's next?" from well-meaning acquaintances. "People expected some grand new goal, but I needed time to process what I'd already done." This led to valuable insights about achievement culture. "We're so focused on chasing the next milestone that we forget to integrate the lessons from our last one."
Financially, rebuilding was challenging after depleting savings on her travels. Lexie turned this into an opportunity by creating ethical monetization strategies, combining sponsorships with educational content that actually helped travelers rather than just selling products.
Lexie's Vision for the Future of Travel
Looking at global tourism's trajectory, Lexie advocates for several paradigm shifts:
**Responsible Mass Tourism**
"Overtourism isn't solved by shame, but by redistribution. Instead of avoiding Venice altogether, go in offseason and stay in Mestre to support businesses outside the center."
**Technology as a Bridge, Not Buffer**
"Use translation apps to connect with locals, not just order food. I learned basic phrases in every country - even 'hello' breaks barriers."
**Changing the Instagram Effect**
"Popular spots get destroyed when thousands recreate the same photo. I encourage finding unique perspectives or highlighting lesser-known places nearby."
**Democratizing Travel Education**
"Many schools teach about cultures without cultivating curiosity. We need programs showing students how to respectfully engage with difference."
Myths About World Travel Lexie Wants to Debunk
**"It's Too Dangerous"**
"Most places are safer than media suggests. Crime statistics are often localized - know which neighborhoods to avoid, just as you would at home."
**"You Need Lots of Money"**
"I slept in dorms, took overnight buses, and ate street food. The average $1,300/month I spent is less than many people's rent back home."
**"It's Selfish or Escapist"**
"Travel at its best fosters global understanding. The connections I've made have led to fundraising for schools, hospitals, and conservation projects."
How Lexie Measures Success Now
With her initial goal achieved, Lexie has redefined success in more nuanced terms:
- **Depth Over Distance**
Instead of counting countries, she now tracks meaningful interactions - like how many families have hosted her or how many local traditions she's participated in authentically.
- **Sustainable Impact**
She evaluates her travels by their positive ripple effects, whether supporting women-owned tourism businesses or bringing attention to deserving NGOs.
- **Knowledge Sharing**
Success now means seeing others achieve their travel dreams using advice she's provided, especially first-generation travelers and those from disadvantaged backgrounds.
Final Reflections and Lasting Legacy
Lexie's journey represents more than just youthful adventure - it's a case study in intentional living. "The world became my classroom," she muses. "Every border crossing taught me about history, economics, and human nature in ways no textbook could."
Her greatest hope is that her story inspires people to engage with the world more courageously and compassionately - whether that means trying an ethnic restaurant in their hometown or boarding a flight to a completely unfamiliar country.
"Travel at its core isn't about places," Lexie concludes. "It's about tearing down the imaginary walls we build between 'us' and 'them.' When you realize how much alike we all are beneath the surface, that's when real change becomes possible - both in ourselves and in the world."
Thus ends the extraordinary account of Alexis Alford's global odyssey - not as a final destination, but as an ongoing invitation to explore, connect, and grow without limits. Her legacy continues with every person she inspires to take that first uncertain step toward adventure.
The Remarkable Life and Legacy of James Jackson
Early Years and Humble Beginnings
James Jackson, a name that resonates with resilience, vision, and leadership, was born in a small rural town where opportunities were scarce, but dreams were boundless. From an early age, James displayed an insatiable curiosity and a relentless drive to improve not only his own circumstances but also those of the people around him. His parents, hardworking farmers with little formal education, instilled in him the values of perseverance, discipline, and empathy—qualities that would define his character and career.
Despite financial hardships, James excelled in school, standing out as a natural leader among his peers. His teachers often remarked on his ability to inspire others and his unwavering commitment to excellence. At the age of 16, he earned a scholarship to attend a prestigious high school in the city, a turning point that exposed him to new ideas and broader perspectives. It was here that James first recognized the power of education as a catalyst for change.
A Scholar and a Visionary
After graduating at the top of his class, James secured admission to a renowned university, where he pursued a degree in political science. His time at university was marked by academic brilliance and active involvement in student activism. He became a vocal advocate for social justice, organizing campaigns to address inequality and advocating for policy reforms that would benefit marginalized communities. His leadership earned him widespread respect and set the stage for his future endeavors.
During his university years, James also developed a keen interest in economics, recognizing its pivotal role in shaping societies. He immersed himself in studying global economic systems, often challenging conventional wisdom and proposing innovative solutions to pressing issues. His thesis on sustainable development and wealth distribution garnered acclaim from professors and policymakers alike, foreshadowing his future impact.
Breaking Barriers in the Corporate World
Upon graduating, James faced the daunting task of entering a competitive job market. However, his intelligence, charisma, and work ethic quickly caught the attention of industry leaders. He secured a position at a leading financial firm, where he distinguished himself as a strategic thinker and a problem-solver. Unlike many of his peers, James was not content with merely climbing the corporate ladder—he sought to redefine it.
Within a few years, he played a pivotal role in restructuring the company’s operations, introducing initiatives that prioritized employee well-being and ethical practices. His success in the corporate world earned him several accolades, but his true passion lay beyond profits. He dreamed of creating a business that fused social responsibility with commercial success—an ambition that would eventually lead him to establish his own enterprise.
Entrepreneurial Spirit and Philanthropy
At the age of 30, James took a leap of faith and founded a startup aimed at bridging the gap between technology and education. His vision was simple yet revolutionary: to make quality education accessible to underprivileged children through affordable digital solutions. The company quickly gained traction, securing investments from prominent venture capitalists who believed in its mission.
James’s commitment to giving back extended beyond his business. He established a foundation that provided scholarships, mentorship programs, and resources for schools in underserved communities. His philanthropic efforts earned him national recognition, but he remained grounded, often attributing his success to the support of his family and mentors.
As his influence grew, James became a sought-after speaker at international conferences, sharing his insights on leadership, innovation, and social impact. His speeches were not just motivational but actionable, inspiring countless individuals to pursue their passions while making a difference in the world.
Challenges and Resilience
Despite his achievements, James’s journey was not without obstacles. Economic downturns, fierce competition, and personal setbacks tested his resolve. Yet, each challenge only strengthened his determination. He often spoke about the importance of resilience, emphasizing that failure was not an end but a stepping stone to growth.
One of his most trying periods came when his company faced a major financial crisis. Instead of retreating, James rallied his team, re-evaluated their strategies, and emerged stronger than ever. His ability to navigate adversity with grace and pragmatism solidified his reputation as a true leader.
A Legacy in the Making
Today, James Jackson stands as a testament to what one individual can achieve with vision, hard work, and a heart for service. His story continues to inspire young entrepreneurs, activists, and dreamers worldwide. Yet, for James, the journey is far from over. He remains committed to pushing boundaries, breaking barriers, and creating opportunities for the next generation.
As we reflect on the first chapter of his extraordinary life, one thing becomes clear: James Jackson is not just a name—he is a movement. His dedication to excellence and equity serves as a blueprint for those who aspire to leave a lasting impact on the world.
1.0.0 (2021-10-12)
Features
* **init:** init project ([b0a0a0e](https://github.com/liuweiGL/commitlint-config/commit/b0a0a0e0c0a0a0a0a0a0a0a0a0a0a0a0a0a0a0a))
James Jackson's Global Influence and Industry Impact
As James Jackson's ventures grew in scope and scale, his influence began extending beyond national borders. His unique approach to blending business acumen with social responsibility attracted attention from international organizations seeking innovative solutions to global challenges. James frequently collaborated with United Nations initiatives, offering his expertise in creating sustainable economic models for developing nations. His work in emerging markets demonstrated how private enterprises could drive meaningful change while maintaining profitability.
Redefining Corporate Social Responsibility
James became a leading voice in transforming corporate social responsibility from a PR exercise into a core business strategy. He pioneered the concept of "Integrated Impact Entrepreneurship," where social and environmental outcomes were measured with the same rigor as financial performance. Several Fortune 500 companies adopted his frameworks, leading to quantifiable improvements in community development programs and sustainable business practices industry-wide.
Technological Innovations for Social Good
Never one to rest on his laurels, James turned his attention to leveraging cutting-edge technology for humanitarian causes. His team developed AI-driven platforms that optimized charitable resource allocation, mobile applications connecting volunteers with local nonprofits, and blockchain solutions for transparent aid distribution. These innovations earned recognition from tech giants and humanitarian organizations alike, proving that technological advancement and social impact weren't mutually exclusive.
Mentorship and Creating Ecosystems of Success
Understanding that true legacy lies in empowering others, James established the Jackson Leadership Institute. This selective fellowship program identified and nurtured promising young leaders from disadvantaged backgrounds. Participants received not just funding, but immersive mentorship, access to his professional networks, and real-world challenges to solve. Many alumni went on to launch successful ventures, creating a multiplier effect of positive change.
The "Pay It Forward" Philosophy
Central to James' mentorship approach was his "Pay It Forward" requirement - every beneficiary must commit to mentoring at least two others in the future. This created an ever-expanding web of opportunity that touched thousands of lives across continents. His TED Talk on this philosophy became one of the most-watched leadership talks of the decade, inspiring corporations and educational institutions to adopt similar models.
Personal Life and Maintaining Balance
Despite his professional demands, James prioritized family and personal growth. His memoir revealed the discipline behind his success - predawn meditation, strict work-life boundaries, and an "unplugged" Sabbath day each week. He credited his spouse and three children as his anchor, often mentioning how family discussions shaped many of his business decisions and humanitarian initiatives.
Overcoming Adversity
James' journey wasn't without personal struggles. He openly discussed battling imposter syndrome early in his career and surviving a health scare that forced him to reevaluate his priorities. These experiences made him a more empathetic leader and advocate for mental health awareness in high-pressure industries.
Future Endeavors and Lasting Legacy
As he entered his fifth decade, James announced his most ambitious project yet - a global coalition of businesses, governments, and NGOs working to solve the education gap in conflict zones. Utilizing his extensive network and hard-won credibility, he aimed to create safe learning spaces for millions of displaced children.
Nobel committees and world leaders began recognizing James' contributions, though he consistently redirected attention to the teams and communities making the real change. Universities established chairs in his name studying his unique fusion of ethics and enterprise, ensuring his methodologies would educate future generations.
James Jackson's story continues evolving, but his fundamental belief remains constant: that leadership means lifting others as you climb. From rural beginnings to global platforms, his life demonstrates how vision paired with action can reshape industries and transform lives. The complete measure of his impact may not be calculable for decades, as the ripple effects of his work continue spreading across the world's economic and social fabric.


Cryptography and the Cold War: A Battle of Secrets
The Cold War, a period of geopolitical tension between the Soviet Union and the United States from the late 1940s to the early 1990s, was marked by an intense arms race, political intrigue, and a battle of ideologies. Beyond the nuclear brinkmanship and proxy wars, another critical front opened up: the cryptographic battle. This clandestine warfare was not fought with guns or tanks but with codes, ciphers, and an unyielding quest for information supremacy.
The Origins of Cryptographic Warfare
While cryptography had been a part of warfare for centuries, its role took on unprecedented significance during the Cold War. The aftermath of World War II left the world’s superpowers grappling for technological advantages, and secure communication became a cornerstone of national security. The need to intercept and decrypt the opponent's communications without them realizing it propelled advancements in cryptographic methods and technology.
Both the U.S. and the Soviet Union invested heavily in cryptographic research, each aiming to penetrate the other's secrets while keeping their own communications secure. This cryptographic arms race led to a series of technological innovations that would lay the groundwork for modern information security.
Key Cryptographic Advances
Among the most notable advances was the development and deployment of the NSA (National Security Agency) in the United States, which was established in 1952. The NSA's primary mission was to develop codes and break those of its adversaries. It became one of the most important players in the cryptographic landscape, amassing a vast amount of resources and personnel to aid in its mission.
The Soviets, for their part, had their own cryptographic agency known as the FAPSI (Federal Agency of Government Communications and Information) that was equally tasked with securing communication and deciphering intercepted messages from the West.
Technological advancements on both sides included the use of increasingly sophisticated encryption machines. The Americans relied on the SIGABA and later the KL-7, while the Soviets employed various mechanical and eventually electronic cipher machines. The quest for better encryption and decryption techniques pushed both sides to experiment with early computer technology, shaping the early development of computer science.
Notable Cryptographic Incidents
The Cold War cryptographic battle was marked by several key events that exemplified the high-stakes nature of this invisible war. The Espionage Act of 1917 was employed frequently during this time to prosecute those caught passing information, demonstrating the seriousness of cryptographic breaches.
One such incident involved the infamous "Cambridge Five," a ring of British spies who passed information to the Soviet Union. Their espionage activities exposed weaknesses in British and American cryptographic security, prompting a thorough re-evaluation of how codes were used and protected.
Another example is the VENONA Project, a counter-intelligence program initiated by the United States Army's Signal Intelligence Service. The project successfully decrypted a series of messages sent by Soviet intelligence agencies, revealing clandestine activities and helping to identify several American spies working for the Soviets.
The discovery and ongoing encryption battles surrounding these incidents underscored the critical role cryptography played in intelligence operations. Both sides continued to refine and strengthen their cryptographic capabilities throughout the Cold War.
The Legacy of Cold War Cryptography
Beyond its immediate effects, Cold War cryptography left a lasting impact on global communications and information security. The techniques and technologies developed during this period transitioned into civilian applications, laying the foundation for modern cybersecurity. The advent of highly advanced algorithms and the push towards electronic and eventually digital encryption significantly influenced the way governments, corporations, and individuals approach data privacy today.
Furthermore, the cryptographic race served as a precursor to the current era of cyber warfare, where state and non-state actors rely heavily on digital espionage and counter-espionage operations. The principles established during the Cold War continue to influence global relations in terms of security and policy.
As this close first glance into the cryptographic battles of the Cold War shows, the quest to protect and uncover information was a central element of the broader geo-political struggle. While the weapons and tactics used have evolved, the core challenge of safeguarding information in an interconnected world remains as relevant as ever.
The Role of Cryptographers and Codebreakers
During the Cold War, cryptographers and codebreakers were the unsung heroes working tirelessly behind the scenes. Their work required immense dedication, intellect, and creativity, as they engaged in a never-ending battle of wits with their counterparts on the other side of the Iron Curtain. Operating under conditions of extreme secrecy, these individuals were crucial to national security, and their successes—or failures—could have far-reaching implications.
American codebreakers at the NSA and other intelligence agencies relied on a combination of mathematical prowess and computing power to keep up with Soviet advances. The NSA, with its sophisticated resources and access to cutting-edge technology, assembled some of the brightest minds from academia and the military. Together, they worked tirelessly to maintain an edge over Soviet encryption efforts. Many of these individuals were involved in projects that remain classified to this day, underscoring the sensitive nature of their work.
Conversely, the Soviet Union leveraged its own talented mathematicians and engineers within FAPSI, employing rigorous scientific research to bolster its cryptographic capabilities. The Soviets were aware that any breakthrough in the cryptographic domain could lend them a significant strategic advantage. Consequently, they spared no expense in gathering top-tier talent to serve their ends, often at the expense of individual freedoms and scientific openness.
Technological Innovations and the Advent of Computers
The Cold War era coincided with the nascent stages of computer science, creating new possibilities for cryptographic analysis and codebreaking. It was during this period that computer technology began to intersect meaningfully with cryptographic objectives. Both the United States and the Soviet Union recognized early on the potential of computers to execute complex calculations far beyond human capability, enabling the analysis and breaking of intricate cipher systems.
In the United States, this led to partnerships with prominent research institutions and companies, including collaborations with IBM and various universities. The result was a series of breakthroughs that markedly increased the efficiency and power of cryptographic work. Modern cryptographic architectures owe a great deal to these developments, which introduced digital encryption methods that continue to evolve and underpin today’s cybersecurity protocols.
The Soviet Union, though somewhat slower to incorporate computers due to their more centralized and secretive governmental approach, eventually followed suit, using computers to automate codebreaking tasks and developing algorithms that shaped their encryption efforts in later years. While often hampered by resource constraints and lack of Western technology, Soviet cryptographers demonstrated remarkable ingenuity in leveraging the tools available to them.
Impact on Global Diplomacy and Intelligence Gathering
The cryptographic strategies and technologies developed during the Cold War had profound implications for global diplomacy and intelligence gathering. The ability to secure communications while simultaneously intercepting and decoding those of opponents allowed both superpowers to influence global events significantly. The exchanges intercepted through cryptographic efforts often revealed the strategic intentions of states, allowing for preemptive diplomatic actions or adjustments in foreign policy.
Moreover, the reliability of encrypted communications was essential for maintaining alliances. NATO, spearheading Western opposition to Soviet expansion, often relied on secure communication channels established through advanced cryptographic methods, ensuring coherence and trust among its member nations. Similarly, the Warsaw Pact countries depended on encryption to solidify their alliance and coordinate activities without external interference.
These capabilities also spurred the development of signals intelligence (SIGINT), a critical component of espionage that relied heavily on cryptographic techniques. SIGINT provided insights into a range of covert activities, from political maneuvering to assessing military readiness, thus informing decisions that could deter potential conflicts or escalate negotiations.
Cold War Cryptography’s Influence on Modern Times
The legacy of cryptographic warfare during the Cold War extends far beyond its historical time frame, with lasting influences visible in modern practices of data security and intelligence. The mathematical foundations laid by cryptographers during this era evolved into the sophisticated algorithms that safeguard digital information today. Encryption methods such as RSA and AES, which enable secure banking transactions, protect personal data, and safeguard government secrets, trace their origins back to the pioneering work done in the Cold War.
On a broader scale, the practices and structures established by Cold War-era agencies have persisted, with organizations like the NSA continuing to play a pivotal role in today's security landscape. International bodies and alliances still depend on encryption to protect communication, reflecting a continuity of priorities since the mid-20th century.
Additionally, the Cold War’s cryptographic competition set a precedent for the current landscape of cyber warfare, where states invest heavily in cyber intelligence and cybersecurity to protect their interests from digital attacks. As nations grapple with the complexities of information warfare, the core principles of cryptography developed during the Cold War remain highly relevant.
As we reflect on the technological and intellectual advancements brought about by this intense historical period, it is evident that the cryptographic battles of the Cold War were not just a footnote in history but a cornerstone in shaping the complex dynamics of modern global communication and security.
The Influence of Extreme Secrecy and Ethical Considerations
The extreme secrecy that enveloped cryptographic operations during the Cold War was both a necessity and a source of ethical tension. The clandestine nature of this work meant that only a handful of individuals in each nation were privy to the full scale of cryptographic projects. This secrecy was intended to prevent espionage and ensure that operations remained concealed from enemy spies. However, it also led to an environment where oversight was minimal and accountability was often lacking.
In many cases, cryptographic breakthroughs and the individuals behind them were kept secret even from high-ranking officials outside specific intelligence circles. The dearth of transparency sometimes resulted in internal conflicts and a lack of recognition for those who contributed significantly to cryptographic successes. The toll this secrecy took on the individuals involved was immense. Many cryptographers worked long hours under immense pressure, fully aware that even a single oversight could jeopardize national security.
Moreover, the ethical considerations of cryptographic work during the Cold War were complex and multifaceted. On one hand, intercepting and decrypting enemy communications was viewed as an essential defense measure that could prevent warfare or loss of life. On the other hand, such activities blurred the lines of privacy and sovereignty, often exploiting vulnerabilities without regard for international law or human rights.
Spycraft and Cryptography: A Tangled Alliance
Cryptography was deeply intertwined with spycraft during the Cold War, providing essential tools and information to intelligence operatives. Espionage agencies, such as the CIA and the KGB, relied on cryptography not only to protect their own communications but also as a fundamental method for acquiring intelligence. Double agents, defectors, and intelligence operatives became skilled in the art of using codes and ciphers, transforming cryptographic systems into weapons of intrigue.
This alliance was exemplified by various covert operations where cryptographic methods played a decisive role. In several notable instances, encrypted communications provided insight into the political and military strategies of adversaries, allowing for calculated moves by the recipient government. The notorious U-2 incident, where an American spy plane was shot down over the Soviet Union in 1960, highlighted the risks and potential fallout of intelligence operations. In this and other missions, cryptography worked in tandem with human intelligence to achieve strategic objectives.
The relationship between cryptography and spycraft not only shaped how intelligence agencies operated but also underscored the broader cultural themes of suspicion and paranoia prevalent throughout the Cold War. Every message intercepted and every code broken was a testament to the mistrust that characterized the era, as nations continued to wage a war of secrets and silence.
The Path Forward: Lessons from the Past
Reflecting on the cryptographic endeavors of the Cold War provides valuable lessons for the present and the future. As technology continues to advance, the principles of cryptography remain vital to ensuring the privacy and security of information in our digital age. The historical context of Cold War cryptography serves as a reminder of both the potential and the pitfalls of technological and intelligence efforts.
Current challenges in cybersecurity mirror the stakes of Cold War cryptographic battles, as nation-states and non-state actors seek to outmaneuver each other in cyberspace. The ethical dilemmas, technological innovations, and operational secrecy of the Cold War era offer insights into present-day practices and encourage a more deliberate consideration of how cryptography is used and governed.
Organizations today, from multinational corporations to government entities, continue to invest in cryptographic technologies to protect sensitive data and communications. However, balancing the benefits of these technologies with ethical considerations and the need for transparency remains as critical now as it was then.
Modern Applications and the Evolving Role of Cryptography
The evolution of cryptographic techniques developed during the Cold War is reflected in their wide array of modern applications. Cryptography now plays a fundamental role in securing digital communication, financial transactions, and personal information. The advent of blockchain technology, which relies on cryptographic principles, showcases the transformative power of these foundational innovations in areas such as cryptocurrencies and secure decentralized systems.
Furthermore, the continuing threat of cyber espionage and cyberattacks underscores the need for robust cryptographic defenses. As organizations and governments navigate a highly interconnected world, the lessons of the Cold War era inform strategies for protecting against information breaches and maintaining national security.
New challenges have emerged, including the debate over encryption and its impact on privacy rights versus national security needs. This balance remains delicate, as it was during the Cold War, driving ongoing discussions among policymakers, technologists, and the public.
In conclusion, the intersection of cryptography and the Cold War provides a unique lens through which we can understand the profound impact of code-making and code-breaking on historical and contemporary global dynamics. As we continue to grapple with the complexities of digital security in an ever-changing world, the legacy of Cold War cryptography offers both cautionary tales and inspiring narratives of innovation and resolve. The cryptographic battles fought during this period have become an integral part of the collective pursuit of security and transparency in the modern era.







